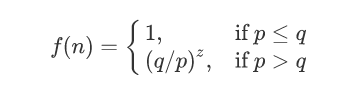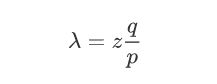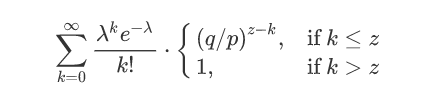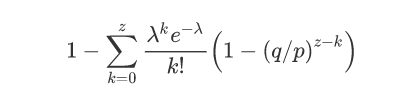Bitcoin: A Peer-to-Peer Electronic Cash System 比特币:一个点对点电子现金系统
Bitcoin: A Peer-to-Peer Electronic Cash System 比特币:一个点对点电子现金系统
Satoshi Nakamoto
[email protected]
www.bitcoin.org
英文版 https://bitcoin.org/bitcoin.pdf
中文版 http://www.8btc.com/wiki/bitcoin-a-peer-to-peer-electronic-cash-system
中文翻译有删改,侵删。中文翻译,我觉得翻译的不好,有些句子不通顺而且难以理解。很多我都做了修改,使之读起来通顺并且便于理解。当然,如果能直接读英文,当我没说。
每一句英文,我都跟了一句中文翻译,有的后面还有“解读”,咋啦,刚接触就不能解读啦…
Abstract. 摘要:
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution.
一个真正的点对点(p2p)电子现金系统,一方应当能够直接发起网络支付给另一方,而不需要经过任何金融机构。
真正的网络支付系统,必须能够直接由一方支付给另一方,不需要经过第三方,就像是我们现实生活中直接拿现金支付一样。这是我们的目标:1.一方给另一方;2.不要中介。
Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending.
虽然数字签名(Digital signatures)技术解决了一部分问题,但是如果仍然需要第三方的支持才能防止双重支付(double-spending)的话,那么这种系统是没有价值的。
这个数字签名技术,应该是有人已经发明的电子支付系统,不过这个系统无法解决双重支付的问题(或者说必须通过第三方机构才能防止双重支付),在中本聪眼里,这种系统的价值不大,可能是因为要求第三方机构介入了,后面会说到引入第三方机构存在的问题。
查了下,大卫·乔姆(David Chaum)提出过需要第三方中介的电子货币系统。估计中本聪批评的是这个系统。
We propose a solution to the double-spending problem using a peer-to-peer network.
我们(we)在此对点对点网络下的双重支付问题提出一种解决办法。
The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work.
该系统会对所有的交易加上时间戳(timestamps),并通过散列(hashing,哈希运算)的方式将这些交易并入一个不断延伸的、具有工作量证明(proof-of-work)的链。该工作量证明也是基于散列的。这样以来,除非重新完成全部的工作量证明,否则形成的交易记录将不可更改。
这句真的很难翻译,我反复读了有四十分钟,才翻译成这个样子,谁让我英语水平烂呢,不过区块链也的确不是一句话就能解释的啊,弄懂这句话,比特币就懂了大半了。
首先,不懂散列(哈希)运算的,先移步这里:
1. 百度百科 https://baike.baidu.com/item/Hash/390310?fr=aladdin
2. 知乎 https://www.zhihu.com/question/20507188
3. 看不懂 https://www.jianshu.com/p/08365ef027a3中本聪提出的方案就是做一个链,把所有交易按照时间排个序,那就不会有双重支付。说明几点:
1. 链公开,就没人可以作弊,因为大家一起监督。
2. 按时间排序,就可以得出每个人都多少钱,从头开始计算呗。
3. 防止双重支付,一笔钱不可能花两次,因为大家都知道这笔钱属不属于你,有没有被交易过,一旦交易过,就不再是你的了,第二次交易肯定会被大家否定的。为了保证不会有人随意修改这个链,又额外引入工作量证明(这个好像是中本聪首先提出的,我不是很确定,但这个设想真的很天才)
1. 为防止每个人的链不一样,或者有人更改链,大家都必须只承认一个链,那就是工作量最大的那个链。只有付出超过现有工作量才能修改链,实际上没人愿意提供那么大的工作量,因为会亏本,所以,工作量最大的那个链就是不可更改的链,就是大家都在里面交易的链。
2. 工作量怎么证明的?答案是随机产生的,按照概率的,基本上,越奇葩的散列,得到的概率就越低。所以区块链基本上就是,一堆奇葩的散列值在一起比较,到底谁更奇葩一些,谁更奇葩,谁就是下一个王者(块)。我已经耗在这句话快2个小时了,扛不住了,还看不懂的跳过吧,拜拜,看完全文可以回头再想想这句话。
The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power.
最长的链不仅可以视作是交易序列的证明,而且可以被认为是CPU计算能力最大的那一方(pool)认同的结果。
链的存在就说明存在这些交易,换个角度看,也是cpu计算力最大那些节点都承认的交易。像不像投票?少数服从多数?
As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they’ll generate the longest chain and outpace attackers.
只要大多数的CPU计算力没有打算合作起来对系统进行攻击,那么这些节点生成的链将会是最长的,而且会超过攻击者的链。
情况是这样,整个系统工作必须依靠一个交易链(账簿),如果大家都不承认这个链,那么一定是个没有用处的链。怎么才能作弊呢?只要你的cpu计算力占优势,那就可以类似投票一样,把那些正常的不作弊的给比下去,那你就是正统了!这就是传说中的51%攻击,如果你的计算力占优势,那么你就可以干坏事了。
The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.
这个系统只要的很小的基础设施:信息尽最大努力在全网传播;节点(nodes)可以随时离开或重新加入,只要承认最长的工作量证明的链即可。
系统结构确实很简单,尽可能地传播信息,每个节点都很自由(条件是承认最长的链)
- Bitcoin: A Peer-to-Peer Electronic Cash System 比特币:一个点对点电子现金系统
-
-
- 1. Introduction 绪论
- 2. Transactions 交易(最小单位,每笔交易的产生)
- 3. Timestamp Server 时间戳服务器 (把交易组合起来成一个接一个的块)
- 4. Proof-of-Work 工作量证明 (一重保证历史交易不可更改的方式)
- 5. Network 网络 (点对点网络)
- 6. Incentive 激励 (最初的货币来源和工作奖励)
- 7. Reclaiming Disk Space 回收硬盘空间(很早的数据可以不用存储)
- 8. Simplified Payment Verification 简化的支付确认
- 9. Combining and Splitting Value 价值的合并与分割 (货币的合并和分割)
- 10. Privacy 隐私 (公钥匿名)
- 11. Calculations 相关计算 (证明)
- 12. Conclusion 结论
- References 参考文献
-
-
1. Introduction 绪论
Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments.
互联网上的贸易,几乎都需要借助金融机构作为可资信赖的第三方来处理电子支付信息。
While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model.
虽然这类系统在绝大多数情况下都运作良好,但是这类系统仍然受限于“基于信用模式”(trust based model)固有的弱点。
Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes.
由于无法实现完全不可逆的交易,因此,金融机构总是不可避免地会协调争端。
The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for nonreversible services.
调停损失会增加交易成本,限制了最小交易规模,进而无法实现日常小额交易,并且,在缺乏信任的环境下实现不可逆交易需要付出更大的成本。
With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable.
由于交易存在取消的可能,实现交易就需要交易双方互相信任。商家会向客户索取完全不必要的个人信息以预防消费者蓄意破坏交易,然而在实际的商业行为中,一定比例的欺诈性客户是不可避免的。
These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party.
这些费用和支付的不确定性在使用物理现金情况下是可以避免的,并且完全无需第三方信用中介的参与。
主要说明当前的网上交易系统的弊端,和我们理想中的现实现金支付进行比较:
1. 因为网上交易可以取消,所以双方需要信任才会进行交易,进而需要中介(金融机构)进行协调
2. 有了中介之后,整个交易就会有中介的成本,就让交易有了很多限制(每次交易有固定成本、交易金额不能太小、交易次数也不能很多)问题是,在现实现金支付的情况下,上面两点问题是不存在的,所以,比特币就是要在网上建立一个尽量现实现金交易一样的系统,这里说尽量,因为,比特币也是要交易费用的。
What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party.
我们需要这样一种电子支付系统,只基于密码学原理而不是信用,就能使得任何达成一致的双方直接进行支付交易,同时不需要第三方中介的参与。
Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers.
杜绝取消(reverse)交易,就可以保护卖方免于欺诈;也很容易实现常规的托管机制来保护买方的利益。
In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions.
在这篇论文中,我们(we)将提出一种通过点对点分布式的时间戳服务器来生成依照时间前后排列并的交易证明(交易链),从而解决双重支付问题。
The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.
只要诚实的节点所控制的计算能力大于任何一个合作(cooperating)攻击者的计算能力,该系统就是安全的。
- 基于密码学,不基于信用,就可以不要中介。
- 交易记录不可逆,就无法取消交易,那么,卖方就一定能收到钱。
说实话没看懂怎么保证买方的利益?为什么又要托管呢?虽然这个托管机构和前面信用模式的第三方金融机构是不一样的,但是为啥还要第三方呢!!谁懂,能给我解释下么。- 交易按时间排序可以防止双重支付。
- 只要诚实工作的节点的计算力占优势,那么系统就是安全的。
2. Transactions 交易(最小单位,每笔交易的产生)
We define an electronic coin as a chain of digital signatures.
我们定义,一枚电子货币(an electronic coin)是这样的一串数字签名:
Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin.
每一位所有者通过对前一次交易的位置和下一位拥有者的公钥(Public key)的散列值签署一个数字签名,并将这个签名附加在这枚电子货币的末尾,电子货币就发送给了下一位所有者。
A payee can verify the signatures to verify the chain of ownership.
收款人通过对签名进行检验,就能够验证该链的所有者。
首先解释一下公钥和私钥,这是密码学里的东西了。公钥和私钥是一对,可以实现这样的功能:
1. 公钥对文件加密,私钥可以把加密后的文件进行解密还原回来,不是一对的话是无法做到的
2. 私钥对文件签名,公钥可以验证这个签名对不对,就是私钥是不是和它匹配的那个私钥
比方说,私钥对abcd…进行签名生成一串efgh…,然后对待验证的公钥说:我俩是一对,你看,我对abcd…进行签名得到的结果是efgh…,你验证一下。公钥就对efgh…进行验证,然后发现的确是abcd…,就算是验证通过了。如果私钥和公钥不是一对的话,是无法做到这一点下面解释交易是怎么生成的,其实图示已经很形象啦,看中间那个,1号想把他的货币支付给2号,就生成这样一个东西:
被支付货币的位置(1号在哪一次交易收到这个货币的)+收款人的公钥–>进行散列(散列值是abcd…)–>1号对这个散列值进行签名(签名结果是efgh…),把生成的签名放到散列值的后面
2号如何验证他收到了这个货币呢?
从上一次位置获取1号的公钥,对这个交易的签名efgh…进行验证得到abcd…,说明这个1号的确拥有这个公钥对应的私钥,说明1号的确拥有过这个货币。如果这个交易信息(位置+2号公钥->散列值->签名)能够加入交易链,这个货币就是2号的了,然后2号可以通过相同的方式支付给3号
The problem of course is the payee can’t verify that one of the owners did not double-spend the coin.
该过程的问题在于,收款人难以检验,付款人是否对这枚电子货币进行了双重支付。
A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending.
通常的解决方案是引入信得过的第三方权威,或者类似于造币厂(mint)的机构,来对每一笔交易进行防止双重支付的检验。
After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent.
在每一笔交易结束后,这枚电子货币就要被造币厂回收,同时造币厂将发行一枚新的电子货币;并且只有造币厂直接发行的电子货币,才算作有效,这样就能够有效防止双重支付。
The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank.
可是该解决方案的问题在于,每一笔交易都要经过该造币厂的确认,因此整个货币系统的命运完全依赖于运作造币厂的公司,造币厂就好比是一家银行。
这一段说明了第三方金融机构是如何防止电子货币的双重支付的
We need a way for the payee to know that the previous owners did not sign any earlier transactions.
我们需要收款人有某种方法,能够确保付款人在本次交易之前没有对该电子货币进行交易签名。
For our purposes, the earliest transaction is the one that counts, so we don’t care about later attempts to double-spend.
为了实现这个目的,我们只需要关注本交易之前是否进行过支付,而不需要关注本次交易之后有没有进行双重支付。
The only way to confirm the absence of a transaction is to be aware of all transactions.
为了确认一次交易是不存在的,那么唯一的方法就是查看之前发生过的所有交易。
In the mint based model, the mint was aware of all transactions and decided which arrived first.
在造币厂模型里面,造币厂获悉所有的交易,并且决定交易完成的先后顺序。
To accomplish this without a trusted party, transactions must be publicly announced [1], and we need a system for participants to agree on a single history of the order in which they were received.
如果想要在电子现金系统中排除第三方信任机构,那么交易信息就应当被公开(publicly announced)[1] ,并且我们需要一个包含所有参与者都承认的历史交易序列的系统。
The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received.
收款人在交易期间需要验证是否绝大多数的节点都认同该交易是首次出现。
本文的解决方案是,不要第三方验证是佛双重支付,把交易记录公开,每个人都可以验证。
对于本节开始那个交易,2号其实并不知道1号有没有把这个货币支付给其他人。如果有了交易链,我们就知道所有的交易,要想知道这个货币有没有被支付给其他人,就按时间顺序检查一下喽
或者说,2号不想检查,让其他人检查,这就是后文矿工的作用了,检查不通过的是不允许加入交易链的,所以2号只要等这个交易有没有进入交易链就可以了
3. Timestamp Server 时间戳服务器 (把交易组合起来成一个接一个的块)
The solution we propose begins with a timestamp server.
我们提出的解决方案从一个“时间戳服务器”开始的。
A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post [2-5].
时间戳服务器会对由一组数据和时间戳组成的区块(block)进行散列,并将该散列进行广播,就像报纸或全球新闻网(Usenet)的传播一样 [2-5]。
The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash.
显然,该时间戳能够证明该组数据在这个时间是确实存在的,因为只有加入了该时间戳才能得到相应的散列值。
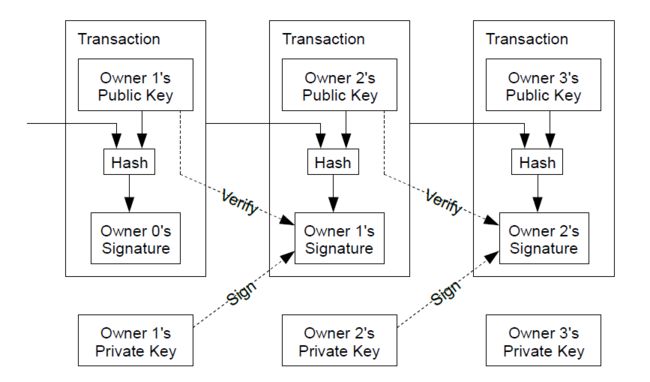
Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.
每个时间戳应当将前一个时间戳纳入其散列值中,像这样,每一个后面的时间戳都对之前的一个时间戳进行增强(reinforcing),这样就形成了一个链(Chain)。

最后一句话莫名其妙啊,明明是散列值,看图看图,时间戳服务器是干啥的呢?
1. 把许多交易(验证通过没有问题的交易)组成一个块数据+前一个块的散列值–>进行散列得到散列值
2. 下一个块也像这样产生,这样就一个接一个形成一个链
4. Proof-of-Work 工作量证明 (一重保证历史交易不可更改的方式)
To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back’s Hashcash [6], rather than newspaper or Usenet posts.
为了在点对点的基础上实现一组分布式的时间戳服务器,仅仅像报纸或全球新闻网一样是不够的,我们还需要使用一个类似于亚当•柏克(Adam Back)提出的哈希现金(Hashcash)[6] 的工作量证明系统。
The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits.
在进行散列运算时,工作量证明机制会对某一个特定值进行检测,比方说采用SHA-256算法进行散列,要求散列值以一个或多个0开始。
The average work required is exponential in the number of zero bits required and can be verified by executing a single hash.
那么随着0的数目的上升, 找到这个解所需要的平均工作量将呈指数增长,但是对结果进行检验则仅需要一次散列运算。
确实需要个工作量证明啊,否则,每个人想生成有一个块就生成一个块,那还有什么不可更改可言啊。
这个hash值是随机的,必须通过一次次尝试才能得出,所以可以改交易啊,付出海量的计算力就可以啦
有意思的是,写这篇论文时,中本聪还说比较的是cpu计算力,但是后来发展成gpu(显卡)计算力,再后来有专门的矿机(什么都不会,只会算hash),,简直无法想象,为了钱,人会做些什么设计
For our timestamp network, we implement the proof-of-work by incrementing a nonce in the block until a value is found that gives the block’s hash the required zero bits.
在我们的时间戳服务器组成的网络中,区块中会放置一个随机数(Nonce),通过不断地调整这个随机数来使得该区块的散列值满足所要求个数的0。
Once the CPU effort has been expended to make it satisfy the proof-of-work, the block cannot be changed without redoing the work.
一旦耗费的CPU计算力满足了所要求的工作量,那么除非重新完成相同的工作量,否则该区块的信息就是不可更改的。
As later blocks are chained after it, the work to change the block would include redoing all the blocks after it.
由于之后的区块是链接在该区块之后的,所以想要更改该区块中的信息,就必须重新完成之后所有区块要求的全部工作量。
由于散列值和数据具有很强的关联,改动哪怕一个字,都会生成不同的散列值,所以越早生成的块越不可能更改,一旦更改,后面的就都不对了,这样就保证了不可更改的特性
所以实现不可更改的方式真的很妙,每个块都是付出代价得到的,改动之前的块,必须把后面的块都重新生成一遍,没有人会有这么大的计算力的,,所以大家都只能承认最长的链,延长它,不要想着更改
感觉有点像博弈论里面的囚徒困境,这个博弈中本聪胜出,也是多数人的胜出。
The proof-of-work also solves the problem of determining representation in majority decision making.
同时,该工作量证明机制还解决了在集体投票表决时,谁是多数的问题。
If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs.
如果决定多数的方式是基于一IP地址一票的,那么一旦有人能够分配大量IP地址,该表决机制就会被破坏。
Proof-of-work is essentially one-CPU-one-vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it.
工作量证明机制的本质则是一CPU一票。“多数”的决定表现为最长的链,因为最长的链包含了最大的工作量。
If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains.
如果多数的CPU为诚实的节点控制,那么诚实的链将以最快的速度延长,并超越其他的竞争链。
To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes.
如果想要对早已生成的区块进行修改,攻击者必须付出完成该区块及其之后所有区块的工作量,并最终赶上并超越诚实节点提供的工作量。
We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.
我们将在后文证明,一个较慢的攻击者试图超过随后所有的区块,其成功概率将呈指数化减小。
“布尔什维主义”的胜利
To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour.
为了解决高速增长的硬件运算速度和参与节点数量的变动带来的实际工作量提供能力的差异,工作量证明的难度(the proof-of-work difficulty)将采用移动平均方法来确定,即每小时生成区块的速度为某一个预定的平均数的难度大小。
If they’re generated too fast, the difficulty increases.
如果区块生成的速度过快,那么难度就会提高。
中本聪连这个问题都想到了
1. 如果整体计算力低,为了保证交易(入块)的速度,就要求工作量低一点
2. 如果计算力变高,就要求工作量高一点,这时候担心的不是交易速度,而是每个人都能很轻易的生成块,那不可更改性就可能受到挑战,总之就要攫取最大的计算力!!!
5. Network 网络 (点对点网络)
The steps to run the network are as follows: 运行该网络的步骤如下:
- New transactions are broadcast to all nodes.
新的交易向全网进行广播 - Each node collects new transactions into a block.
每一个节点都将收到的交易信息纳入一个区块中 - Each node works on finding a difficult proof-of-work for its block.
每个节点都尝试在自己的区块中找到一个具有足够难度的工作量证明 - When a node finds a proof-of-work, it broadcasts the block to all nodes.
当一个节点找到了一个工作量证明,它就向全网进行广播 - Nodes accept the block only if all transactions in it are valid and not already spent.
当且仅当包含在该区块中的所有交易都是有效的且之前未消费过,其他节点才认同该区块的有效性 - Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
其他节点若接受该区块,则会在该区块的末尾,使用该区块的散列值制造新的区块延长该链
Nodes always consider the longest chain to be the correct one and will keep working on extending it.
节点始终都将最长的链视为正确的链,并持续工作和延长它。
If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first.
如果有两个节点同时广播不同版本的新区块,那么其他节点在接收到两个区块的时间上将存在先后差别。
In that case, they work on the first one they received, but save the other branch in case it becomes longer.
在此情形下,他们将在率先收到区块的基础上进行工作,但也会保留另外一个区块,以防后者变成最长的链。
The tie will be broken when the next proof-of- work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one.
该僵局(tie)会在下一个工作量证明时打破,而其中的一条链会被证明是较长的一条,那么在另一条分支链上工作的节点将转换阵营,开始在这条较长的链上进行工作。
不断延长链
New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, they will get into a block before long.Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one.
新的交易并不需要广播至全部的节点。只要交易信息能够广播至足够多的节点,这些交易信息就会很快被整合进一个区块中。区块的广播对被丢弃的信息是有容错能力的。如果一个节点没有收到某特定区块,那么该节点将会发现缺失了某个区块,就会向其他节点提出下载该区块的请求。
6. Incentive 激励 (最初的货币来源和工作奖励)
By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block.
我们约定:每个区块的第一个交易都是一笔特殊的交易,该交易产生一枚由该区块创造者拥有的新的电子货币。
This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them.
这样就为了节点支持该网络的进行了激励,在没有中央集权机构发行货币的情况下,这种方式提供了一种将电子货币分配到流通领域的方法。
The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended.
这种将一定数量新货币持续增添到货币系统中的方法,非常类似于耗费资源去挖掘金矿并将黄金注入到流通领域。在我们的系统中,CPU的运算时间和电力就是消耗的资源。
货币来源和矿工激励
The incentive can also be funded with transaction fees.
另外一个激励的来源则是交易费(transaction fees)。
If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction.
如果某笔交易的输出值小于输入值,那么差额就是交易费,该交易费将被增加到该区块的激励中。
Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free.
只要既定数量的电子货币已经进入流通,那么激励机制就可以逐渐转换为完全依靠交易费,并且该货币系统能够免于通货膨胀。
交易费用的激励
The incentive may help encourage nodes to stay honest.
激励系统也有助于鼓励节点保持诚实。
If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins.
如果有一个贪婪的攻击者能够调集比所有诚实节点加起来还要多的CPU计算力,那么他就面临一个选择:要么将其用于诚实工作产生新的电子货币,或者将其用于进行双重支付攻击。
He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.
那么他就会发现,按照规则行事、诚实工作是更有利可图的。因为该规则使得他能够拥有更多的电子货币,而不是破坏这个系统使得其自身财富的有效性受损。
节点为什么要验证交易的正确病情合并入块延长链?
1. 初期每个块可以把第一笔交易设置成收款人是自己,付款人是系统,(这就能凭空得到货币,当然这也是前期货币的来源)
2. 后期,每个区块不奖励货币了,就会收交易费,付出交易费的交易会更优先入块。
7. Reclaiming Disk Space 回收硬盘空间(很早的数据可以不用存储)
Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space.
如果最近的交易已经被纳入了足够多的区块之中,那么就可以丢弃该交易之前的数据,以回收硬盘空间。
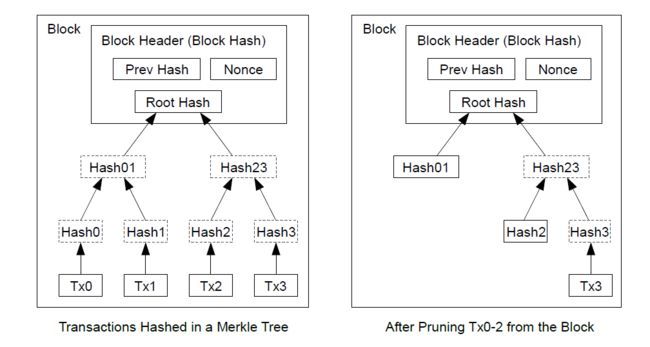
To facilitate this without breaking the block’s hash, transactions are hashed in a Merkle Tree [7], with only the root included in the block’s hash.
为了确保不破坏区块的散列值,交易信息在被散列时,会构建成一种Merkle树(Merkle tree)[7] 的形态,使得只有根(root)被纳入了区块。
Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored.
通过将该树(tree)的分支拔除(stubbing)的方法,老区块就能被压缩。区块内部的散列值是不必保存的。
对于用不到的交易信息可以删除保存空间。
比如上面1号、2号和3号,2号都已经把货币支付给3号了,1号给2号的交易信息怕是连散列值都不用保存了。
A block header with no transactions would be about 80 bytes.If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year.
不含交易信息的区块头(Block header)仅有80字节。如果我们设定区块生成的速率为每10分钟一个,那么每一年产生数据的大小为4.2MB(80 bytes * 6 * 24 * 365 = 4.2MB)。
With computer systems typically selling with 2GB of RAM as of 2008, and Moore’s Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory.
2008年,PC系统通常的内存容量为2GB,按照摩尔定律的预言,即使将全部的区块头存储于内存之中都不是问题。
8. Simplified Payment Verification 简化的支付确认
It is possible to verify payments without running a full network node.
在不运行完整网络节点的情况下,也能够对支付进行检验。
A user only needs to keep copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he’s convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it’s timestamped in.
一个用户需要保留最长工作量证明链区块头的拷贝(通过不断向网络发起询问,直到能确认拥有最长的链),得到能连接交易及包含该交易的块的merkle分支。
He can’t check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it.
节点想要自行检验交易的有效性是不可能的,但通过检查该交易在链上的位置,就能确认某个节点已经接受了交易,并且于其后追加的区块都会进一步证明全网已经接受了该交易。

一旦能确认该交易已经入块,就表明该交易已经被其他节点接受,不出意外应该是交易成功了。
As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker.
只要诚实的节点控制了网络,检验机制就是可靠的。但是,当攻击者的计算力占优时,该验证机制会变得较为脆弱。
While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker’s fabricated transactions for as long as the attacker can continue to overpower the network.
在网络节点能够自行确认交易的有效性时,只要攻击者能够持续地保持计算力优势,简化的验证机制会被攻击者伪造的(fabricated)交易欺骗。
One strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user’s software to download the full block and alerted transactions to confirm the inconsistency.
一个可行的策略是,一旦发现了一个无效的区块,就立刻发出警报,收到警报的用户将立刻开始下载被警告有问题的区块,以便确认信息的不一致性。
Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification.
对于会发生大量日常交易的商业机构,可能会希望运行他们自己的完整节点,以保持较大的独立安全和更快的校验速度。
没看懂这一段,怎么进行攻击?求讲解。
9. Combining and Splitting Value 价值的合并与分割 (货币的合并和分割)
Although it would be possible to handle coins individually, it would be unwieldy to make a separate transaction for every cent in a transfer.
虽然可以单独的对电子货币进行交易,但是将交易分割然后一枚一枚进行是笨拙的办法。
To allow value to be split and combined, transactions contain multiple inputs and outputs.
为了使得货币易于合并或分割,交易被设计为允许多个输入和输出。
Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender.
一般而言之前某次金额较大的交易构成的单一输入,或者由几次金额较小的交易共同构成的并行输入,但是输出最多只有两个:一个用于支付,另一个用于找零(如有)。

It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here.
需要指出的是,当一笔交易依赖于之前的多笔交易时,这些交易又各自依赖于多笔交易,这是正常的。
There is never the need to extract a complete standalone copy of a transaction’s history.
这些交易依赖并不意味着需要从交易记录中抽取个副本出来。
一个或多个输入,至多2个输出,电子货币就可以任意合并或分割了。
10. Privacy 隐私 (公钥匿名)
The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party.
传统的银行模型为交易的参与者提供了一定程度的隐私保护,因为试图向可信任的第三方索取交易信息是受限制的。
The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous.
如果将交易信息向全网进行广播,那么就无法通过这个方法来保护隐私。但是通过隐藏交易信息的某个环节——公钥匿名化,隐私就仍然是可以得到保护的。
The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone.
公众得知的信息仅仅是有某个人将一定数量的货币支付给了另外一个人,但是难以将该交易同特定的人联系在一起。
This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the “tape”, is made public, but without telling who the parties were.
这和股票交易发布的信息是类似的,股票交易的时间和数量是可供查询的,但是无法获知具体是“谁”在进行交易。

As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner.
作为额外的保护措施,使用者可以让每次交易都生成一个新的地址,以确保这些交易不被追溯到一个共同的所有者。
Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner.
由于并行输入的存在,一定程度上的追溯还是不可避免的,因为并行输入表明这些货币属于同一个所有者。
The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner.
此时的风险在于,如果某人的公钥暴露了,那么就可以借此公钥追溯出此人的其它交易。
11. Calculations 相关计算 (证明)
We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain.
设想如下场景:一个攻击者拥有更快的计算力并且试图生成另一条链来代替诚实节点生成的链。
Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker.
即便它达到了这一目的,也不意味着整个系统就能被攻击者完全控制,比方说凭空创造价值(货币),或者使用任何不属于攻击者的货币。
Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them.
这是因为节点不会接受无效的交易,并且诚实的节点也永远不会接受一个包含无效信息的区块。
An attacker can only try to change one of his own transactions to take back money he recently spent.
一个攻击者能做的,最多是更改他自己的交易信息,例如拿回他刚刚付给别人的钱。
The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk.
诚实链和攻击链之间的竞赛,可以用二叉随机漫步(Binomial Random Walk)来描述。
The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker’s chain being extended by one block, reducing the gap by -1.
成功事件定义为诚实的链延长了一个区块,其领先性+1,而失败事件则是攻击者的链被延长了一个区块,使得差距-1。
The probability of an attacker catching up from a given deficit is analogous to a Gambler’s Ruin problem.
攻击者弥补某一既定差距的概率,可以近似地看做赌徒破产问题(Gambler’s Ruin problem)。
Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven.
假定一个赌徒拥有无限的透支信用,然后开始进行可能无数次的赌博,直到填补上自己的亏损。
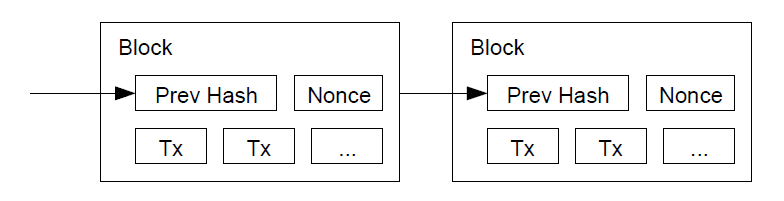
We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows [8]:
那么我们可以计算赌徒填补上亏损的概率,也就是攻击者赶上诚实节点链的概率,如下所示[8] :
p = probability an honest node finds the next block 诚实节点发现下一个块的概率
q = probability the attacker finds the next block 攻击者发现下一个块的概率
q_z = probability the attacker will ever catch up from z blocks behind 攻击者消除z个块差距的概率
Given our assumption that p > q, the probability drops exponentially as the number of blocks the attacker has to catch up with increases.
假定p>q,那么攻击成功的概率就因为区块数z的增长而呈现指数化下降。
With the odds against him, if he doesn’t make a lucky lunge forward early on, his chances become vanishingly small as he falls further behind.
由于攻击者找到下一个块的概率小,倘若攻击者不能幸运且快速地获得成功,那么他获得成功的机会随着时间的流逝就变得越来越小。
We now consider how long the recipient of a new transaction needs to wait before being sufficiently certain the sender can’t change the transaction.
现在讨论一个收款人究竟需要等待多长时间,才能确信付款人已经难以改变交易。
We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed.
我们假设付款人是一个攻击者,他希望能够让收款人在一段时间内相信他已经付过款了,然后建立新的分支块将支付的款项重新支付给自己。
The receiver will be alerted when that happens, but the sender hopes it will be too late.
虽然收款人之后会发现这一点,但等到发现时收款人已经什么都做不了了。
The receiver generates a new key pair and gives the public key to the sender shortly before signing.
收款人生成了一个新的密钥对,然后在签名之前快速地将公钥发给付款人。
This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment.
这样可以防止以下情况:付款人预先准备好一个区块然后不断地对此区块进行运算,直到运气让他的区块链超越了诚实的链,然后付款人才执行支付。
Once the transaction is sent, the dishonest sender starts working in secret on a parallel chain containing an alternate version of his transaction.
在此情形下,只要交易一旦发出,攻击者就开始秘密地准备一条包含了他自己交易的平行链来替代刚刚支付出去的链。
The recipient waits until the transaction has been added to a block and z blocks have been linked after it.
收款人会等待交易出现在一个区块中,并且紧随其后有z个区块。
He doesn’t know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker’s potential progress will be a Poisson distribution with expected value:
此时,收款人仍然不能确切知道攻击者已经进展了多少个区块,假设诚实区块将耗费平均预期时间以产生一个区块,那么攻击者的潜在进展服从泊松分布,期期望值为:
To get the probability the attacker could still catch up now, we multiply the Poisson density for each amount of progress he could have made by the probability he could catch up from that point:
攻击者追赶上的概率为,一定进展区块数量下的泊松概率密度,乘以在该数量下依然能够追赶上的概率。
Rearranging to avoid summing the infinite tail of the distribution…
化为如下形式,避免对无限数列求和:
Converting to C code…
写为如下C语言代码:
double AttackerSuccessProbability(double q, int z)
{
double p = 1.0 - q;
double lambda = z * (q / p);
double sum = 1.0;
int i, k;
for (k = 0; k <= z; k++)
{
double poisson = exp(-lambda);
for (i = 1; i <= k; i++)
poisson *= lambda / i;
sum -= poisson * (1 - pow(q / p, z - k));
}
return sum;
}Running some results, we can see the probability drop off exponentially with z.
对其进行运算,我们可以得到如下的结果,发现概率对z值呈指数下降。
q=0.1
z=0 P=1.0000000
z=1 P=0.2045873
z=2 P=0.0509779
z=3 P=0.0131722
z=4 P=0.0034552
z=5 P=0.0009137
z=6 P=0.0002428
z=7 P=0.0000647
z=8 P=0.0000173
z=9 P=0.0000046
z=10 P=0.0000012
q=0.3
z=0 P=1.0000000
z=5 P=0.1773523
z=10 P=0.0416605
z=15 P=0.0101008
z=20 P=0.0024804
z=25 P=0.0006132
z=30 P=0.0001522
z=35 P=0.0000379
z=40 P=0.0000095
z=45 P=0.0000024
z=50 P=0.0000006
Solving for P less than 0.1%… 求解令P<0.1%时,z的值:
P < 0.001
q=0.10 z=5
q=0.15 z=8
q=0.20 z=11
q=0.25 z=15
q=0.30 z=24
q=0.35 z=41
q=0.40 z=89
q=0.45 z=340
12. Conclusion 结论
We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending.
我们提出了一种不需要信用中介的电子支付系统。首先讨论了通常的电子货币的电子签名原理,虽然这种系统为所有权提供了强有力的控制,但是不足以防止双重支付。
To solve this, we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power.
为了解决这个问题,我们提出了一种采用工作量证明机制的点对点网络来记录公开的交易信息,只要诚实的节点能够控制绝大多数的CPU计算力,就能使得攻击者难以改变交易记录。
The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis.
该网络的强健之处在于它非结构化简洁性。节点的工作大部分是彼此独立的,只需要很少的协同。每个节点都不需要明确自己的身份,由于交易信息的流动路径并无任何要求,所以只需要尽其最大努力传播即可。
Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them.
节点可以随时离开网络,而想重新加入网络也非常容易,只需要接受离开期间的工作量证明链即可。节点通过自己的CPU计算力进行投票,它们不断延长有效的区块链来表达自己的确认,并拒绝在无效的区块之后延长区块以表示拒绝。
Any needed rules and incentives can be enforced with this consensus mechanism.
这套交易系统共识机制包含所有需要的规则和激励措施。
References 参考文献
[1] W. Dai, a scheme for a group of untraceable digital pseudonyms to pay each other with money and to enforce contracts amongst themselves without outside help(一种能够借助电子假名在群体内部相互支付并迫使个体遵守规则且不需要外界协助的电子现金机制),”b-money,” http://www.weidai.com/bmoney.txt, 1998.
[2] H. Massias, X.S. Avila, and J.-J. Quisquater, “Design of a secure timestamping service with minimal trust requirements(在最小化信任的基础上设计一种时间戳服务器),” In 20th Symposium on Information Theory in the Benelux, May 1999.
[3] S. Haber, W.S. Stornetta, “How to time-stamp a digital document(怎样为电子文件添加时间戳),” In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991.
[4] D. Bayer, S. Haber, W.S. Stornetta, “Improving the efficiency and reliability of digital time-stamping(提升电子时间戳的效率和可靠性),” In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[5] S. Haber, W.S. Stornetta, “Secure names for bit-strings(比特字串的安全命名),” In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997.
[6] A. Back, “Hashcash - a denial of service counter-measure(哈希现金——拒绝服务式攻击的克制方法),” http://www.hashcash.org/papers/hashcash.pdf, 2002.
[7] R.C. Merkle, “Protocols for public key cryptosystems(公钥密码系统的协议),” In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980.
[8] W. Feller, “An introduction to probability theory and its applications(概率论与应用导论),” 1957.