ASA入门实验之failover Active/Active
ASA failover
ASA的failover和普通的交换机一样。A/S模式:一主一备,主有问题切换到备机,做起来比较简单。A/A模式,双Active,将物理墙虚成不同的逻辑墙。
实验拓扑
| VLAN | 作用 | 地址 |
|---|---|---|
| vlan2 | inside1 | 10.1.1.0 |
| vlan3 | inside2 | 20.1.1.0 |
| vlan4 | failover | 1.1.1.0/2.2.2.0 |
| vlan5 | SP1 | 192.168.1.0 |
| vlan6 | SP2 | 192.168.2.0 |
| cloud | 111.111.111.111 |
ASA e0 为failover,e1口为failover 。e2为inside,e3为outside。

配置
3725
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/0.2 #配置子接口
encapsulation dot1Q 2
ip address 10.1.1.1 255.255.255.0
!
interface FastEthernet0/0.3
encapsulation dot1Q 3
ip address 20.1.1.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.1.1.254 #两条默认路由,默认走左边
ip route 0.0.0.0 0.0.0.0 20.1.1.254 20
SW
vlan 2-6
!
interface Ethernet0/0
switchport access vlan 4
switchport mode access
duplex auto
!
interface Ethernet0/1
switchport access vlan 4
switchport mode access
duplex auto
!
interface Ethernet0/2
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2,3,5,6
switchport mode trunk
duplex auto
!
interface Ethernet0/3
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2,3,5,6
switchport mode trunk
duplex auto
!
interface Ethernet1/0
switchport access vlan 4
switchport mode access
duplex auto
!
interface Ethernet1/1
switchport access vlan 4
switchport mode access
duplex auto
!
interface Ethernet1/2
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2,3,5,6
switchport mode trunk
duplex auto
!
interface Ethernet1/3
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2,3,5,6
switchport mode trunk
duplex auto
!
interface Ethernet2/0
switchport access vlan 5
switchport mode access
duplex auto
!
interface Ethernet2/1
switchport access vlan 6
switchport mode access
duplex auto
!
interface Ethernet2/2
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2,3
switchport mode trunk
duplex auto
!
SP1
interface Ethernet0/0 #TO ASA
no switchport
ip address 192.168.1.1 255.255.255.0
duplex auto
!
interface Ethernet0/2 #TO CLOUD
no switchport
ip address 11.11.11.11 255.255.255.0
duplex auto
!
ip route 0.0.0.0 0.0.0.0 11.11.11.12
ip route 10.1.1.0 255.255.255.0 192.168.1.254
ip route 20.1.1.0 255.255.255.0 192.168.2.254
SP2
interface Ethernet0/0
no switchport
ip address 192.168.2.1 255.255.255.0
duplex auto
!
interface Ethernet0/1
duplex auto
!
interface Ethernet0/2
no switchport
ip address 22.22.22.22 255.255.255.0
duplex auto
!
ip route 0.0.0.0 0.0.0.0 22.22.22.23
ip route 10.1.1.0 255.255.255.0 192.168.1.254
ip route 20.1.1.0 255.255.255.0 192.168.2.254
CLOUD
interface Loopback0 ##公网口
ip address 111.111.111.111 255.255.255.255
!
interface Ethernet0/0 ##SP1
no switchport
ip address 11.11.11.12 255.255.255.0
duplex auto
!
interface Ethernet0/1 #SP2
no switchport
ip address 22.22.22.23 255.255.255.0
duplex auto
!
ip route 10.1.1.0 255.255.255.0 11.11.11.11
ip route 20.1.1.0 255.255.255.0 22.22.22.22
ip route 192.168.1.0 255.255.255.0 11.11.11.11
ip route 192.168.2.0 255.255.255.0 22.22.22.22
line vty 0 4 #用于测试
password cisco
login
transport input all
ASA
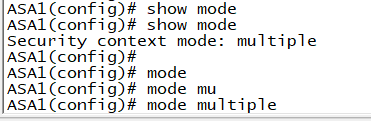
配置前检查:两个防火墙模式都必须为multiple模式和router模式,如果不是请转换。
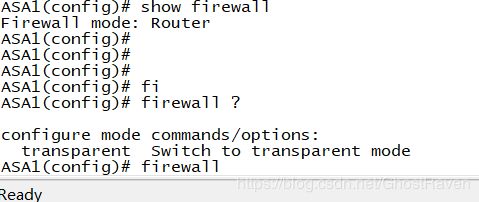
####### 主墙配置
#配置相应接口
interface Ethernet2.1
vlan 2
!
interface Ethernet2.2
vlan 3
!
interface Ethernet3
!
interface Ethernet3.1
vlan 5
!
interface Ethernet3.2
vlan 6
#配置failover
failover lan unit primary
failover lan interface fo-control Ethernet0
failover link fo-status Ethernet1
failover interface ip fo-control 1.1.1.1 255.255.255.0 standby 1.1.1.2
failover interface ip fo-status 2.2.2.2 255.255.255.0 standby 2.2.2.3
failover group 1
preempt
failover group 2
secondary
preempt
#配置虚墙
admin-context admin
context admin
config-url disk0:/admin.cfg
!
context A
allocate-interface Ethernet2.1
allocate-interface Ethernet3.1
config-url disk0:/A.cfg
join-failover-group 1
!
context B
allocate-interface Ethernet2.2
allocate-interface Ethernet3.2
config-url disk0:/B.cfg
!
#配置虚墙A
changeto context A
conf t
interface Ethernet2.1
nameif inside_1
security-level 100
ip address 10.1.1.254 255.255.255.0 standby 10.1.1.253
!
interface Ethernet3.1
nameif outside_1
security-level 0
ip address 192.168.1.254 255.255.255.0 standby 192.168.1.253
!
access-list icmp-ping extended permit icmp any 10.1.1.0 255.255.255.0
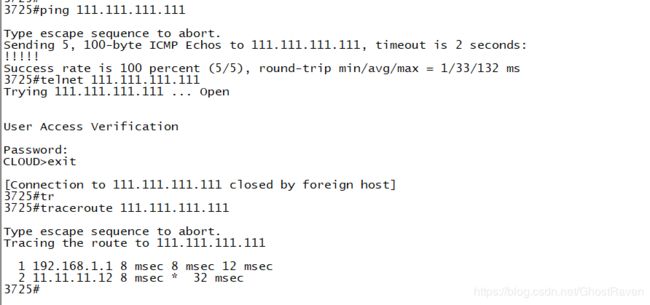
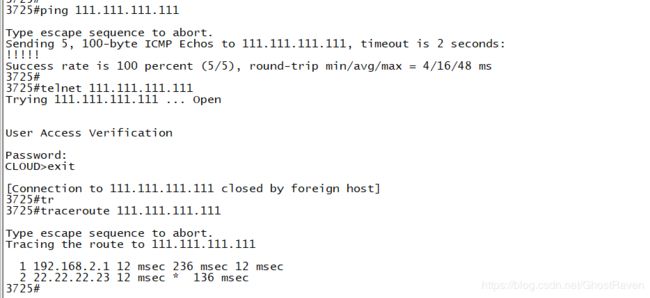
access-group icmp-ping in interface outside_1 #外访内放开icmp。如果不放开,你会发现inside可以telnet 111.111.111.111 但是不能ping通。因为ASA默认只放开了inside到outside,回报被拒。
route outside_1 0.0.0.0 0.0.0.0 192.168.1.1 1 #默认路由往上
#配置虚墙B
changeto context B
conf t
interface Ethernet2.2
nameif inside_2
security-level 100
ip address 20.1.1.254 255.255.255.0 standby 20.1.1.253
!
interface Ethernet3.2
nameif outside_2
security-level 0
ip address 192.168.2.254 255.255.255.0 standby 192.168.2.253
!
access-list icmp-ping extended permit icmp any 20.1.1.0 255.255.255.0
access-group icmp-ping in interface outside_2
route outside_2 0.0.0.0 0.0.0.0 192.168.2.1 1
备墙配置
#配置相应接口
interface Ethernet2.1
vlan 2
!
interface Ethernet2.2
vlan 3
!
interface Ethernet3
!
interface Ethernet3.1
vlan 5
!
interface Ethernet3.2
vlan 6
#配置failover
failover lan unit secondary
failover lan interface fo-control Ethernet0
failover link fo-status Ethernet1
failover interface ip fo-control 1.1.1.1 255.255.255.0 standby 1.1.1.2
failover interface ip fo-status 2.2.2.2 255.255.255.0 standby 2.2.2.3
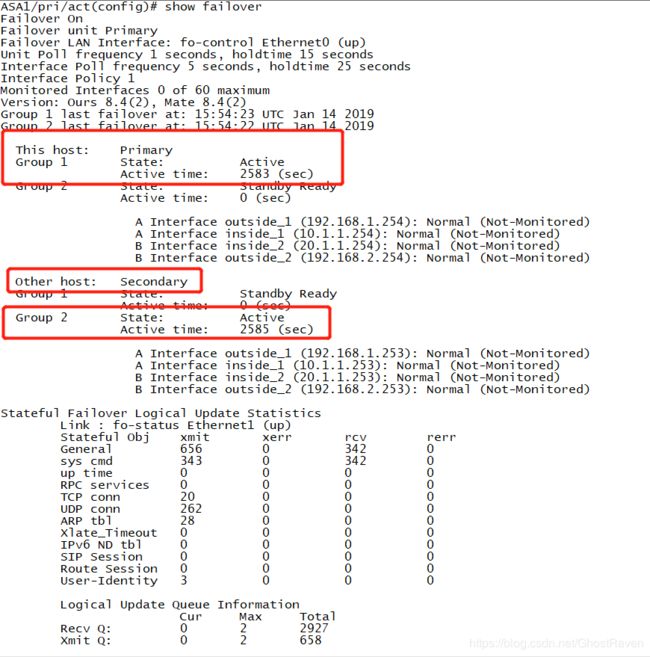
配置完成后,两个ASA都启用failover(直接输入failover就行),然后A墙的信息会被同步到B墙。可以prompt hostname context priority state 来查看所在墙的详细信息。