DDCTF2019-Misc Write up
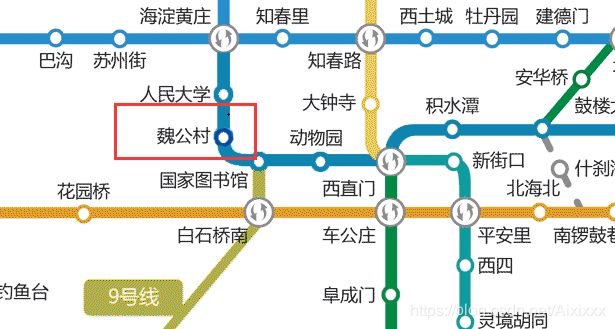
Misc 1 - 北京地铁
Color Threshold
提示:AES ECB密钥为小写字母
提示2:密钥不足位用\0补全
提示3:不要光记得隐写不看图片本身啊…
蠢死了= =_(:з」∠)_密钥找了一天发现真在图片里。。以为是提示挖坑。
去取图片RGB通道的最低位就能看见AES ECB加密的密文通过长度判断密钥因为16位
weigongcun为10位
weigongcun\0\0\0\0\0\0这就是密钥= =(:з」∠)
Misc 2 -MulTzor
原文为英语,请破解
12ce98ec4c4d79e38bf9454a71fecafa5a196ce58fb5795771ea87f41c5a71fd82f04e5076eacae6454a6ce887b5595779ef86f058196ce58fb54b5c6bf98fe7521959e186fc594a38e484b56b566ae18eb56b586aada3dc1c4d77ad98f05d5d38fe9ff74f4d79e39efc5d5538ec87fa49576cfecafa5a1955e298e659147be28ef058196aec8efc53197be287f8495771ee8be1555676fecafa5a196ce58fb57d4171fecae5534e7dff99b5485179f9cafd5d5d38ef8ff052197de389fc4c517dff8ff11c4c6be484f21c7c76e48df85d1975ec89fd55577dfec4b5685171fecaec555c74e98ff11c5471e183e15d4b61ad83fb485c74e183f259577be8cae254507be5c6b55d5577e38db54b506ce5cae154586cad8ce7535438e29efd594b38e98ff64e4068f98ff11c7860e499b54e587ce485b55d577cad9ef0505c68ff83fb485c6aad9ee75d576be083e64f5077e399b91c4e79fecaf2554f7de3cae1545c38ee85f1595779e08fb569556cff8bbb1c6d70e499b54b586bad89fa524a71e98fe7595d38ef93b54b5c6bf98fe752194bf89ae759547dadabf950507de9cad6535475ec84f1594b38c99dfc5b516cadaebb1c7c71fe8ffb54566fe898b5485638e58be359197ae88ffb1c1b7ce889fc4f506ee8c8b5485638f982f01c7874e183f058196ee489e1534b61a3e09f68517dadaffb555e75eccaf85d5a70e484f04f196fe898f01c5838eb8bf8555561ad85f31c4977ff9ef45e557dad89fc4c517dffcaf85d5a70e484f04f196fe49efd1c4b77f985e71c4a7bff8bf85e557dff99bb1c7e77e28eb553497dff8be155577fad9ae7535a7de99fe7594a34ad9ae753497dff86ec1c5c76eb85e75f5c7ca1cae2534c74e9cafd5d4f7dad87f4585c38f982f01c4974f88df753586ae9cad052507fe08bb551587be583fb59196de388e7595873ec88f9591738c585e2594f7dffc6b551566bf9cafa5a196ce58fb57b5c6ae08bfb1c5471e183e15d4b61ad8cfa4e5a7dfec6b54f5c7bff8fe11c4a7dff9cfc5f5c6bad8bfb58197be49cfc505079e3caf45b5c76ee83f04f196ce58be11c4c6be88eb5795771ea87f41c5c75fd86fa455c7cad9afa534b38e29af04e586ce484f21c496ae289f0584c6ae899b91c5876e9cafc48196fec99b548517dfe8fb54c5677ffcae54e567be88ee04e5c6bad9efd5d4d38ec86f9534e7de9cae1545c38c884fc5b5479ad87f45f5171e38fe61c4d77ad88f01c4b7dfb8fe74f5c35e884f255577de898f0581979e38eb548517dad89fc4c517dff99b5485638ef8fb54e5c79e9c49f366d70e8cad2594b75ec84b54c556dea88fa5d4b7ca08fe4495068fd8ff11c7c76e48df85d197ae889f4515c38c38bef55195fe898f85d5761aa99b54c4b71e389fc4c5874ad89e745496ce2c7e6454a6ce887bb1c706cad9df44f197aff85fe595738ef93b548517dadbafa50506be5cad259577dff8bf91c6a6cec8cf31b4a38ce83e5545c6aada8e04e5c79f8cafc52195ce889f0515b7dffcaa4050a2aa1cae2554d70ad9efd591979e48eb5535f38cb98f0525a70a099e04c4974e48ff11c5076f98ff950507fe884f6591975ec9ef04e5079e1cafa5e4d79e484f058197eff85f81c5838ca8fe7515876ad99e5451738cccaf853576ce5caf7595f77ff8fb548517dad85e0485b6ae88bfe1c567eadbdfa4e557cadbdf44e1951c4c6b55d4d38eccaf653577ee898f0525a7dad82f0505d38e38ff44e194fec98e65d4e34ad9efd591948e286fc4f5138ce83e5545c6aada8e04e5c79f8cae654586ae88eb5554d6badaffb555e75ecc7f74e5c79e683fb5b196ce889fd525069f88fe61c5876e9cae1595a70e385f9535e61ad9dfc485138f982f01c7f6ae884f6541979e38eb57e4b71f983e6541738c99fe755577fad9efd59195fe898f85d5738e484e35d4a71e284b5535f38dd85f95d577ca1caf6534b7dadbafa50506be5cad6554970e898b57e4c6ae88be01c497dff99fa52577de1cae2594b7dad8fe35d5a6dec9ef0581538fb83f41c6b77e08bfb555834ad9efa1c7f6aec84f659196fe58fe759196ce58fec1c5c6bf98bf750506be58ff11c4d70e8cac57f195aff9ffb53196be48dfb5d556bad83fb485c74e183f259577be8cae648586ce485fb1c4e71f982b57a4b7de389fd1c5f79ee83f9554d71e899b54f4c68fd85e7481738de9ff65f5c6bfe8ce050197be285e5594b79f983fa521979e085fb5b196ce58fb56c5674e899b91c4d70e8cad34e5c76ee82b91c5876e9cae1545c38cf98fc48506be5caf448195ae18fe15f5174e893b56c586ae6caf653576ce484e0595d38f884e1555538c79ffb591929b4dea510196fe58ffb1c7f6aec84f659196bf898e759577ce898f058196ce2cae1545c38ca8fe7515876fec49f367f6ae287b5485171fecaf7595e71e384fc525e34ad9efd59195aff83e1554a70adadfa4a5c6ae387f0524d38ce85f1591979e38eb57f4068e58fe71c6a7be585fa501930caa9b37f6a31ad8be11c7b74e89ef654557df4cac55d4b73ad88e055556cad9fe51c5876ad8fed485c76fe83e359197bff93e5485876ec86ec48507bad89f44c587ae486fc484036ada3fb554d71ec86f9451538f982f01c5d7dee98ec4c4d71e284b54b586bad87f4555774f4cafa5a1954f88ce14b587eeb8fb5147e7dff87f4521979e498b55a566aee8fbc1c5876e9caf41c5f7dfacadd595c6aadc2d2594b75ec84b55d4b75f4c3b5515c6bfe8bf2594a34ad8be61c4d70e8cade4e507dea99f85d4b71e38fb5147e7dff87f4521976ec9cec15197de09af953407de9caf8495a70ad87fa4e5c38fe8ff6494b7dad9ae7535a7de99fe7594a38eb85e71c4c6be484f21c7c76e48df85d1738cc86f452194cf898fc525e34ad8bb57f5875ef98fc585e7dadbffb554f7dff99fc484038e08be1545c75ec9efc5f5079e3caf4525d38e185f2555a71ec84b91c496ae29cfc585c7cad87e05f5138e28cb548517dad85e7555e71e38bf91c4d70e484fe55577fad9efd5d4d38e18ff11c4d77ad9efd59197ce899fc5b5738e28cb548517dad89e745496cec84f450406ce489f450197ae287f7591975ec89fd55577dfecae154586cad9df04e5c38e484e6484b6de08ffb485874ad83fb1c5c6ee884e1495874e193b55e4b7dec81fc525e38f982f01c5779fb8bf91c7c76e48df85d1738c585e2594f7dffc6b548517dada1e7555c7ffe87f44e5076e8cafc524d6ae28ee05f5c7cad8bfb1c7c76e48df85d196ee898e6555676ad9dfc485138eccaf3534c6af982b54e566ce298b55a566aad83e14f194da088fa5d4d6ba1cae7594a6de19efc525e38e484b55d1968ff85f953577fe88eb54c5c6ae485f11c4e70e884b548517dfe8fb5515c6bfe8bf2594a38ee85e0505d38e385e11c5b7dad8ef05f4b61fd9ef0581738da83e154196ce58fb55f5868f99fe7591977ebcae759557dfb8bfb48197be49afd594b38e68fec4f1979e38eb548517dad9fe6591977ebcaf8495a70ad8cf44f4d7dffcac06f1956ec9cec1c5b77e088f04f1538ff8ff2495579ffc6b54e5868e48eb54e5c79e983fb5b1977ebcac0115b77ec9eb5515c6bfe8bf2594a38ff8fe649547de9c49f366d70e8caf350587fad83e606195cc9a9c17a427ab88ca1055c2abcdaa30a0b2bbddbf45f097ebb8ca65d0f2dbfdca40c0f7ebc97
发现是16进制。先制作成二进制文件发现UTF-8编码下
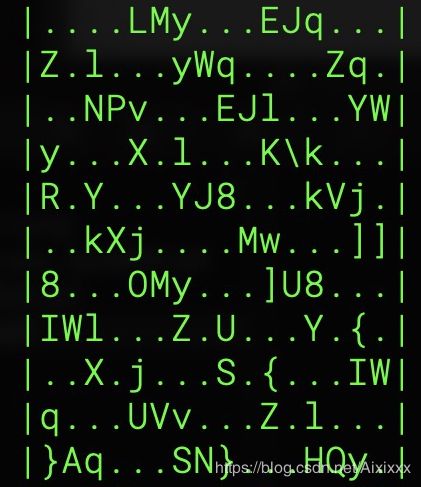
有可能是异或加密的如果是异或就需要异或的对象。有可能是跟题目异或发现不行。
通过搜寻资料看见这篇博客写的异或密钥如何爆破=。=贼强。
https://www.anquanke.com/post/id/161171
利用该脚本先进行密钥长度爆破再进行密钥爆破得到密钥
或者用xortools
Cryptanalysis of the Enigma ciphering system enabled the western Allies in World War II to read substantial amounts of Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio and teleprinter transmissions, was given the codename Ultra. This was considered by western Supreme Allied Commander Dwight D. Eisenhower to have been "decisive" to the Allied victory.
The Enigma machines were a family of portable cipher machines with rotor scramblers. Good operating procedures, properly enforced, would have made the plugboard Enigma machine unbreakable. However, most of the German military forces, secret services and civilian agencies that used Enigma employed poor operating procedures, and it was these poor procedures that allowed the Enigma machines to be reverse-engineered and the ciphers to be read.
The German plugboard-equipped Enigma became Nazi Germany's principal crypto-system. It was broken by the Polish General Staff's Cipher Bureau in December 1932, with the aid of French-supplied intelligence material obtained from a German spy. A month before the outbreak of World War II, at a conference held near Warsaw, the Polish Cipher Bureau shared its Enigma-breaking techniques and technology with the French and British. During the German invasion of Poland, core Polish Cipher Bureau personnel were evacuated, via Romania, to France where they established the PC Bruno signals intelligence station with French facilities support. Successful cooperation among the Poles, the French, and the British at Bletchley Park continued until June 1940, when France surrendered to the Germans.
From this beginning, the British Government Code and Cypher School (GC&CS) at Bletchley Park built up an extensive cryptanalytic capability. Initially, the decryption was mainly of Luftwaffe (German air force) and a few Heer (German army) messages, as the Kriegsmarine (German navy) employed much more secure procedures for using Enigma. Alan Turing, a Cambridge University mathematician and logician, provided much of the original thinking that led to the design of the cryptanalytical bombe machines that were instrumental in eventually breaking the naval Enigma. However, the Kriegsmarine introduced an Enigma version with a fourth rotor for its U-boats, resulting in a prolonged period when these messages could not be decrypted. With the capture of relevant cipher keys and the use of much faster US Navy bombes, regular, rapid reading of U-boat messages resumed.
The flag is: DDCTF{b5f49e210662301ac0f6f3a6526106f1}
Misc 4 -Wireshark
使用科来网络流量分析_(:з」∠)_发现存在负载。直接导出图片= =
Misc 5 -联盟决策大会
为了共同的利益,【组织1】和【组织2】成立了联盟,并遵守共同约定的协议。为了让协议的制定和修改更加公
平,组织1和组织2共同决定:当三位以上【组织1】成员和三位以上【组织2】成员同意时,才可以制定或修改协
议。为了实现这一功能,联盟的印章被锁在密码保险柜中,而保险柜的密码只通过Shamir秘密分享方案分享给【组织
1】和【组织2】的每一位成员。
现在,【组织1】的【成员1】、【成员2】、【成员4】,【组织2】的【成员3】、【成员4】、【成员5】一致同
意制定新的协议。请还原出这套方案的设计思路,按照这套方案的思路恢复出保险柜密码,取出印章吧!以下为使用到的7个十六进制常数:
p =
C45467BBF4C87D781F903249243DF8EE868EBF7B090203D2AB0EDA8EA48719ECE9B914F9F5D0795C23BF627
E3ED40FBDE968251984513ACC2B627B4A483A6533
组织1成员1 =
729FB38DB9E561487DCE6BC4FB18F4C7E1797E6B052AFAAF56B5C189D847EAFC4F29B4EB86F6E678E0EDB17
77357A0A33D24D3301FC9956FFBEA5EA6B6A3D50E
组织1成员2 =
478B973CC7111CD31547FC1BD1B2AAD19522420979200EBA772DECC1E2CFFCAE34771C49B5821E9C0DDED7C
24879484234C8BE8A0B607D8F7AF0AAAC7C7F19C6
组织1成员4 =
BFCFBAD74A23B3CC14AF1736C790A7BC11CD08141FB805BCD9227A6E9109A83924ADEEDBC343464D42663AB
5087AE26444A1E42B688A8ADCD7CF2BA7F75CD89D
组织2成员3 =
9D3D3DBDDA2445D0FE8C6DFBB84C2C30947029E912D7FB183C425C645A85041419B89E25DD8492826BD709A
0A494BE36CEF44ADE376317E7A0C70633E3091A61
组织2成员4 =
79F9F4454E84F32535AA25B8988C77283E4ECF72795014286707982E57E46004B946E42FB4BE9D22697393F
C7A6C33A27CE0D8BFC990A494C12934D61D8A2BA8 组织2成员5 =
2A074DA35B3111F1B593F869093E5D5548CCBB8C0ADA0EBBA936733A21C513ECF36B83B7119A6F5BEC6F472
444A3CE2368E5A6EBF96603B3CD10EAE858150510http://mslc.ctf.su/wp/plaidctf-2012-nuclear-launch-detected-150-password-guessing/
Google 到了关于Shamir的往年类似的题改改代码直接用=。=
思路就是根据题意
【组织1】的【成员1】、【成员2】、【成员4】
【组织2】的【成员3】、【成员4】、【成员5】
分为两组进行解密;再将两组的值再去解密就能出来flag值
运气比较好= =试了几次就出来了
from libnum import *
pairs = []
#pairs += [(1,6003337281407523367186816771601490940615500711557368761527360302854076376201665136290909859657023088320891142661937462474900250483078729090684999860213006)]
#pairs += [(2,3747130175520475798593821190976284432219291130357152221572952079224206973326877203344432331671696664831404861445127770767770666635355856062680429039131078)]
#pairs += [(4,10045980505979257143337507392043927450281026428477914992178874114132061426043166259133591648487756351929497979655653054589426269233341481936567926253213853)]
#pairs += [(3,8235286350623641980967511020663457162226759801127251615460201681119560827594899157212651541944611172396892864367839207456159782249492523947684435166042721)]
#pairs += [(4,6388421571481901983340861215304515629032100729076825501885182419338793283655773352752913154855701690876909137925569269658507279419501366808879368514448296)]
#pairs += [(5,2201212642761620893972666700430230313555397362506320152355413125034520665041564975704631086516207775042292075114322970550542048095265158192521779485148432)]
pairs += [(1,5008218469324545733723642682613512359732318262730008690839081007747593667553287238208851242799115274462488135174002821782864699383438870487674519605392385)]
pairs += [(2,10016436938649091467447285365227024719464636525460017381678159790509157807879462342444466019366040634129410798859979685203946007341755469910255396896570501)]
p=10282621148071476044049093185578805651346165275301962841221400519188324796517681207383861403658207623060366773379188832216705087567759783411470896041977139
res = 0
for i, pair in enumerate(pairs):
x, y = pair
top = 1
bottom = 1
for j, pair in enumerate(pairs):
if j == i:
continue
xj, yj = pair
top = (top * (-xj)) % p
bottom = (bottom * (x - xj)) % p
res += (y * top * invmod(bottom, p)) % p
res %= p
print res
print n2s(res)
不想写了_(:з」∠)_被ban了23333