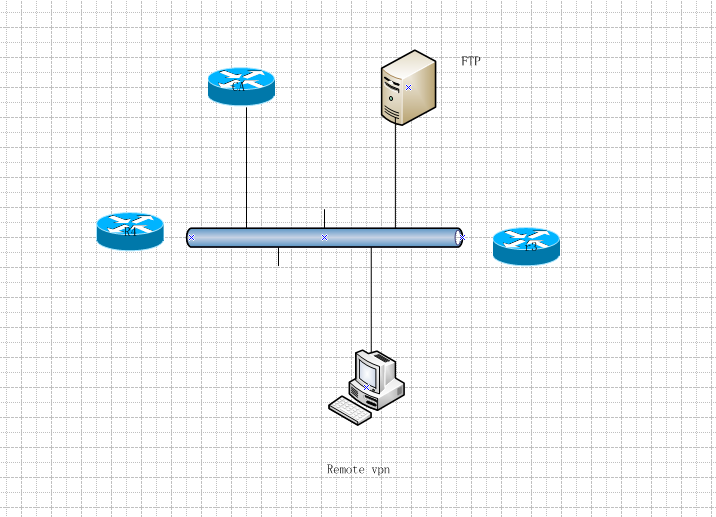
要求:
1.要求使用证书验证
2.site-to-site ***使用SCEP证书申请方式
3.remote-***使用pkcs10证书申请方式
前提:
1.在***环境中实现证书的验证,必须要求时间同步!CA服务器开启http server
2.使用FTP做为CA证书的存放地点,防止大量证书占用NV
3.CA有个FTP账号必须可写的权限
搭建:
我是使用server U搭建的FTP服务器,内建一个username cisco password cisco可写的权限账号。
搭建CA
clock timezone GMT 8
clock set
ntp mster
ip domain name laoliang.com
crypto pki server ca
database level complete
database url ftp://202.1.100.24 证书存放的地点
database username cisco password 7 094F471A1A0A 一个对FTP可写的账号
database archive pem 压缩方式
issuer-name cn=laoliang o=nongda i=zhengzhou CA的账户信息
cdp-url ftp://202.1.100.24 吊销列表
no sh
ca#SHOW crypto pki certificates 根证书
CA Certificate
Status: Available
Certificate Serial Number: 01
Certificate Usage: Signature
Issuer:
cn=laoliang o\=nongda i\=zhengzhou
Subject:
cn=laoliang o\=nongda i\=zhengzhou
Validity Date:
start date: 21:09:09 GMT May 17 2011
end date: 21:09:09 GMT May 16 2014
Associated Trustpoints: ca
R3搭建:
crypto key generate rsa usage-keys
crypto pki trustpoint ca 定义远程CA
enrollment url http://202.1.100.20:80
serial-number
ip-address 202.1.100.30
subject-name cn=r3 o=nongda i=zhengzhou
revocation-check crl none
crypto pki authen ca 获取CA的公钥
crypto pki enroll ca 把个人信息及其自己的公钥提交给CA
CA:当r3提交信息后查看CA的请求
ca#crypto pki server ca info requests
Enrollment Request Database:
Subordinate CA certificate requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
RA certificate requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
Router certificates requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
2 pending A5892D5B4CDC72DF67F212A225B73D11 ipaddress=202.1.100.30+hostname=r3.laoliang.com,cn=r3 o\=nongda i\=zhengzhou
1 pending 5EB2C274199A03844B6DE6F3A2330E57 ipaddress=202.1.100.30+hostname=r3.laoliang.com,cn=r3 o\=nongda i\=zhengzhou
ca#crypto pki server ca gr 颁发证书给R3
ca#crypto pki server ca grant 1
Writing 2.crt !
Writing 2.cnm !
Writing ca.ser !
ca#crypto pki server ca grant 2
Writing 3.crt !
Writing 3.cnm !
Writing ca.ser !
R4同理
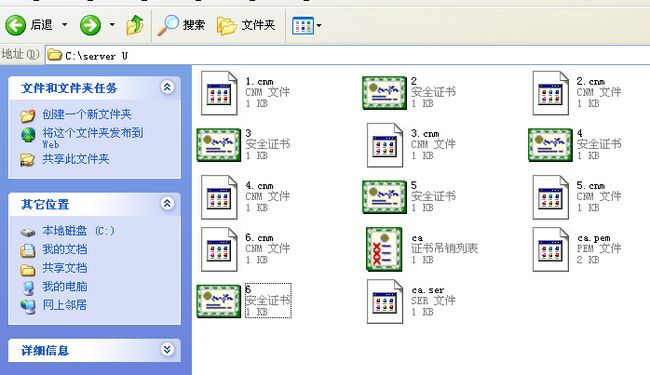
这是我们在FTP服务器看下证书
这里注意一点:crypto key generate rsa usage-keys 产生2对密钥一份用于签名一份用于加密,
r4(config)#crypto key generate rsa ?
general-keys Generate a general purpose RSA key pair for signing and
encryption
usage-keys Generate separate RSA key pairs for signing and encryption
配置好后R4的show run信息
r4#show run
Building configuration...
Current configuration : 5306 bytes
Last configuration change at 14:29:08 UTC Tue May 17 2011
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
hostname r4
boot-start-marker
boot-end-marker
no aaa new-model
memory-size iomem 5
ip cef
no ip domain lookup
ip domain name laoliang.com
crypto pki trustpoint ca
enrollment url http://202.1.100.20:80
serial-number
subject-name cn=r4 ou=nongda i=zhengzhou
revocation-check crl none
crypto pki certificate chain ca
certificate 05
30820212 3082017B A0030201 02020105 300D0609 2A864886 F70D0101 04050030
29312730 25060355 0403131E 6C616F6C 69616E67 20206F3D 6E6F6E67 64612069
3D7A6865 6E677A68 6F75301E 170D3131 30353137 31333138 34305A17 0D313230
35313631 33313834 305A3043 3121301F 06035504 03131872 34206F75 3D6E6F6E
67646120 693D7A68 656E677A 686F7531 1E301C06 092A8648 86F70D01 0902160F
72342E6C 616F6C69 616E672E 636F6D30 5C300D06 092A8648 86F70D01 01010500
034B0030 48024100 C3A11EC2 DFB7A349 F8E09D68 28E57490 7A6883DD EB434574
520C366B 09AB41D7 F1BE7363 52F88593 85AB63E3 D1F66F6D 67205B20 F19454BA
077885D6 A2D50E59 02030100 01A37430 72302306 03551D1F 041C301A 3018A016
A0148612 6674703A 2F2F3230 322E312E 3130302E 3234300B 0603551D 0F040403
02052030 1F060355 1D230418 30168014 366F45DC 405B228E EBE72399 C6893FFD
13899A38 301D0603 551D0E04 16041457 35CF6AFD 0DA86962 CD7C8A34 7D287E79
ADDF4E30 0D06092A 864886F7 0D010104 05000381 810062A2 EDBF3263 76B0E6BF
B63B8FE6 5F04556D 23691944 EBB8641E A5A02892 0C31B336 EF7B0A6F FFC92430
F16F71DB 1DE49F83 C34EA5C5 4E425C62 1D12BAD8 A4CF9198 EC84F72E FC15D2B8
FD7B4FBA B9A3BEF3 F3A7A237 D9DEA9FB C2FFD5F1 24827EB8 2180F9C9 923E07C2
6CC34DE2 0B1DD9F1 9EE63306 2825D038 00909D74 56E7
quit
certificate 04
30820212 3082017B A0030201 02020104 300D0609 2A864886 F70D0101 04050030
29312730 25060355 0403131E 6C616F6C 69616E67 20206F3D 6E6F6E67 64612069
3D7A6865 6E677A68 6F75301E 170D3131 30353137 31333138 33355A17 0D313230
35313631 33313833 355A3043 3121301F 06035504 03131872 34206F75 3D6E6F6E
67646120 693D7A68 656E677A 686F7531 1E301C06 092A8648 86F70D01 0902160F
72342E6C 616F6C69 616E672E 636F6D30 5C300D06 092A8648 86F70D01 01010500
034B0030 48024100 BCFAD0A9 191FAD30 2B1B51E8 260EFD40 39F68D68 11B78909
B56ACC30 236988E3 E5E9B21E 0C3F904E C7A447E9 D683EB85 3E8DFA99 5CF9C41A
22618115 0150B9F3 02030100 01A37430 72302306 03551D1F 041C301A 3018A016
A0148612 6674703A 2F2F3230 322E312E 3130302E 3234300B 0603551D 0F040403
02078030 1F060355 1D230418 30168014 366F45DC 405B228E EBE72399 C6893FFD
13899A38 301D0603 551D0E04 16041445 0AA4084B 09BFAEC3 0272C638 C7DE747C
A47B6930 0D06092A 864886F7 0D010104 05000381 8100922E 7289C55B 50716AA0
0A165B75 4A38A293 9C8E3C75 AA2117CA 39C29EC3 2BD9AE62 38447BE7 9D65E4D5
5DAD74C0 8D9F8F73 841883A7 57CEF4FB 5DD41093 B89EB20A 55F10C33 BB159D3F
9DC9F5FB 8048E70A 9D885C03 0A1E306E 324B5F6B 52B46D5A E286192B 7EF9B89A
45C9E51C 89071CD4 C68D694B 5977C001 9B868E22 3124
quit
certificate ca 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
29312730 25060355 0403131E 6C616F6C 69616E67 20206F3D 6E6F6E67 64612069
3D7A6865 6E677A68 6F75301E 170D3131 30353137 31333039 30395A17 0D313430
35313631 33303930 395A3029 31273025 06035504 03131E6C 616F6C69 616E6720
206F3D6E 6F6E6764 6120693D 7A68656E 677A686F 7530819F 300D0609 2A864886
F70D0101 01050003 818D0030 81890281 8100BD5F 93A6D7F9 A53B2F54 CE3C2F03
C40C158B BF43BB17 B5821732 57DAF284 9BB239F6 89349A84 C343EF58 B6D3A4E7
894A2553 24DD2DE4 3CA5FEE4 6A6E73F3 CF10660F 07BF4130 E4912CC2 AFB3E9A8
0F84C75D 35907E2F F3416EAE 9C5FB761 7EAA25C0 93A4EA00 592FB485 F15E0E62
EB132B32 8173DB92 AC008FA9 11489414 07150203 010001A3 63306130 0F060355
1D130101 FF040530 030101FF 300E0603 551D0F01 01FF0404 03020186 301F0603
551D2304 18301680 14366F45 DC405B22 8EEBE723 99C6893F FD13899A 38301D06
03551D0E 04160414 366F45DC 405B228E EBE72399 C6893FFD 13899A38 300D0609
2A864886 F70D0101 04050003 81810053 18A811BB 0BDABF83 6D528194 B5E107DE
EE518F07 C70E1FE6 DFE0FBA2 6E87BB91 4D56FC8A 7AFA91AD 275BF120 DAEBCE6B
87A51EFD ECA0677E 8844F915 A499A8C3 71F7F9C6 CE3089DF 67221387 516D1B51
35DA49D3 23E32858 06709738 8C753D33 D2C2CFFF 8E9B962C C0EBB1AA 96663F20
8B442A05 2FBF5E2B 0E9F63DC 024590
quit
crypto isakmp policy 10
crypto ipsec transform-set *** esp-des esp-md5-hmac
crypto map mymap 65000 ipsec-isakmp
set peer 202.1.100.30
set transform-set ***
match address ***
interface Loopback0
ip address 4.4.4.4 255.255.255.255
interface Ethernet0/0
ip address 202.1.100.40 255.255.255.0
full-duplex
crypto map mymap
ip http server
no ip http secure-server
ip route 3.3.3.3 255.255.255.255 202.1.100.30
ip access-list extended ***
permit ip host 4.4.4.4 host 3.3.3.3
在R3上开启debug cry isa
r3#debug cry isa
Crypto ISAKMP debugging is on
r3#ping 4.4.4.4 sou
r3#ping 4.4.4.4 source 3.3.3.3 re
r3#ping 4.4.4.4 source 3.3.3.3 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 3.3.3.3
May 17 13:28:32.811: ISAKMP: received ke message (1/1)
May 17 13:28:32.815: ISAKMP:(0:0:N/A:0): SA request profile is (NULL)
May 17 13:28:32.815: ISAKMP: Created a peer struct for 202.1.100.40, peer port 500
May 17 13:28:32.815: ISAKMP: New peer created peer = 0x6457345C peer_handle = 0x80000002
May 17 13:28:32.819: ISAKMP: Locking peer struct 0x6457345C, IKE refcount 1 for isakmp_initiator
May 17 13:28:32.819: ISAKMP: local port 500, remote port 500
May 17 13:28:32.819: ISAKMP: set new node 0 to QM_IDLE
May 17 13:28:32.819: insert sa successfully sa = 64572D70
May 17 13:28:32.823: ISAKMP:(0:0:N/A:0):Can not start Aggressive mode, trying Main mode.
May 17 13:28:32.823: ISAKMP:(0:0:N/A:0):No pre-shared key with 202.1.100.40!
May 17 13:28:32.823: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-07 ID
May 17 13:28:32.827: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-03 ID
May 17 13:28:32.827: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-02 ID
May 17 13:28:32.827: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
May 17 13:28:32.827: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_I_MM1
May 17 13:28:32.831: ISAKMP:(0:0:N/A:0): beginning Main Mode exchange
May 17 13:28:32.831: ISAKMP:(0:0:N/A:0): sending packet to 202.1.100.40 my_port 500 peer_port 500 (I) MM_NO_STATE
May 17 13:28:33.263: ISAKMP (0:0): received packet from 202.1.100.40 dport 500 sport 500 Global (I) MM_NO_STATE
May 17 13:28:33.275: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
May 17 13:28:33.275: ISAKMP:(0:0:N/A:0):Old State = IKE_I_MM1 New State = IKE_I_MM2
May 17 13:28:33.279: ISAKMP:(0:0:N/A:0): processing SA pay.load. message ID = 0
May 17 13:28:33.283: ISAKMP:(0:0:N/A:0): processing vendor id payload
May 17 13:28:33.283: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
May 17 13:28:33.283: ISAKMP (0:0): vendor ID is NAT-T v7
May 17 13:28:33.283: ISAKMP : Scanning profiles for xauth ...
May 17 13:28:33.283: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 10 policy
May 17 13:28:33.287: ISAKMP: encryption DES-CBC
May 17 13:28:33.287: ISAKMP: hash SHA
May 17 13:28:33.287: ISAKMP: default group 1
May 17 13:28:33.287: ISAKMP: auth RSA sig
May 17 13:28:33.287: ISAKMP: life type in seconds
May 17 13:28:33.287: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
May 17 13:28:33.291: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
May 17 13:28:33.343: ISAKMP:(0:1:SW:1): processing vendor id payload
May 17 13:28:33.343: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
May 17 13:28:33.343: ISAKMP (0:134217729): vendor ID is NAT-T v7
May 17 13:28:33.343: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
May 17 13:28:33.343: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM2
May 17 13:28:33.343: ISAKMP (0:134217729): constructing CERT_REQ for issuer cn=laoliang o\=nongda i\=zhengzhou
May 17 13:28:33.343: ISAKMP:(0:1:SW:1): sending packet to 202.1.100.40 my_port 500 peer_port 500 (I) MM_SA_SETUP
May 17 13:28:33.343: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
May 17 13:28:33.343: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM2 New State = IKE_I_MM3
May 17 13:28:33.587: ISAKMP (0:134217729): received packet from 202.1.100.40 dport 500 sport 500 Global (I) MM_SA_SETUP
May 17 13:28:33.591: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
May 17 13:28:33.595: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM3 New State = IKE_I_MM4
May 17 13:28:33.595: ISAKMP:(0:1:SW:1): processing KE payload. message ID = 0
May 17 13:28:.33.659: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = 0
May 17 13:28:33.663: ISAKMP:(0:1:SW:1):SKEYID state generated
May 17 13:28:33.667: ISAKMP:(0:1:SW:1): processing CERT_REQ payload. message ID = 0
May 17 13:28:33.667: ISAKMP:(0:1:SW:1): peer wants a CT_X509_SIGNATURE cert
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): peer want cert issued by
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): Choosing trustpoint ca as issuer
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): processing vendor id payload
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): vendor ID is Unity
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): processing vendor id payload
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): vendor ID is DPD
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): processing vendor id payload
May 17 13:28:33.671: ISAKMP:(0:1:SW:1): speaking to another IOS box!
May 17 13:28:33.671: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
May 17 13:28:33.671: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM4
May 17 13:28:33.671: ISAKMP:(0:1:SW:1):Send initial contact
May 17 13:28:33.715: ISAKMP:(0:1:SW:1):SA is doing RSA signature authentication using id type ID_IPV4_ADDR
May 17 13:28:33.715: ISAKMP (0:134217729): ID payload
next-payload : 6
type : 1
address : 202.1.100.30
protocol : 17
port : 500
length : 12
May 17 13:28:33.715: ISAKMP:(0:1:SW:1):Total payload length: 12
May 17 13:28:33.715: ISAKMP (0:134217729): constructing CERT payload for ipaddress=202.1.100.30+hostname=r3.laoliang.com,cn=r3 o\=nongda i\=zhengzhou
May 17 13:28:33.715: ISAKMP:(0:1:SW:1): using the ca trustpoint's keypair to sign
May 17 13:28:33.831: ISAKMP:(0:1:SW:1): sending packet to 202.1.100.40 my_port 500 peer_port 500 (I) MM_KEY_EXCH
May 17 13:28:33.831: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
May 17 13:28:33.831: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM4 New State = IKE_I_MM5
.
May 17 13:28:38.140: ISAKMP (0:134217729): received packet from 202.1.100.40 dport 500 sport 500 Global (I) MM_KEY_EXCH
May 17 13:28:38.148: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 0
May 17 13:28:38.148: ISAKMP (0:134217729): ID payload
next-payload : 6
type : 2
FQDN name : r4.laoliang.com
protocol : 17
port : 500
length : 23
May 17 13:28:38.148: ISAKMP:(0:1:SW:1):: peer matches *none* of the profiles
May 17 13:28:38.152: ISAKMP:(0:1:SW:1): processing CERT payload. message ID = 0
May 17 13:28:38.152: ISAKMP:(0:1:SW:1): processing a CT_X509_SIGNATURE cert
May 17 13:28:38.188: ISAKMP:(0:1:SW:1): peer's pubkey isn't cached.
May 17 13:28:41.016: ISAKMP:(0:1:SW:1): Unable to get DN from certificate!
May 17 13:28:41.020: ISAKMP:(0:1:SW:1): Cert presented by peer contains no OU field.
May 17 13:28:41.024: ISAKMP (134217729): adding peer's pubkey to cache
May 17 13:28:41.024: ISAKMP:(0:1:SW:1): processing SIG payload. message ID = 0
May 17 13:28:41.048: ISAKMP:(0:1:SW:1):SA authentication status:
authenticated
May 17 13:28:41.048: ISAKMP:(0:1:SW:1):SA has been authenticated with 202.1.100.40
May 17 13:28:41.048: ISAKMP: Trying to insert a peer 202.1.100.30/202.1.100.40/500/, and inserted successfully 6457345C.
May 17 13:28:41.052: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
May 17 13:28:41.052: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM5 New State = IKE_I_MM6
May 17 13:28:41.052: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
May 17 13:28:41.056: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM6 New State = IKE_I_MM6
May 17 13:28:41.060: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
May 17 13:28:41.060: ISAKMP:(0:1:SW:1):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
May 17 13:28:41.064: ISAKMP:(0:1:SW:1):beginning Quick Mode exchange, M-ID of 1880679587
May 17 13:28:41.080: ISAKMP:(0:1:SW:1): sending packet to 202.1.100.40 my_port 500 peer_port 500 (I) QM_IDLE
May 17 13:28:41.084: ISAKMP:(0:1:SW:1):Node 1880679587, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
May 17 13:28:41.084: ISAKMP:(0:1:SW:1):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
May 17 13:28:41.084: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
May 17 13:28:41.088: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
May 17 13:28:41.516: ISAKMP (0:134217729): received packet from 202.1.100.40 dport 500 sport 500 Global (I) QM_IDLE
May 17 13:28:41.520: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = 1880679587
May 17 13:28:41.520: ISAKMP:(0:1:SW:1): processing SA payload. message ID.!! = 1880679587
May 17 13:28:41.520: ISAKMP:(0:1:SW:1):Checking IPSec proposal 1
May 17 13:28:41.524: ISAKMP: transform 1, ESP_DES
May 17 13:28:41.524: ISAKMP: attributes in transform:
May 17 13:28:41.524: ISAKMP: encaps is 1 (Tunnel)
May 17 13:28:41.524: ISAKMP: SA life type in seconds
May 17 13:28:41.524: ISAKMP: SA life duration (basic) of 3600
May 17 13:28:41.524: ISAKMP: SA life type in kilobytes
May 17 13:28:41.524: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
May 17 13:28:41.528: ISAKMP: authenticator is HMAC-MD5
May 17 13:28:41.528: ISAKMP:(0:1:SW:1):atts are acceptable.
May 17 13:28:41.532: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = 1880679587
May 17 13:28:41.532: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 1880679587
May 17 13:28:41.532: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 1880679587
May 17 13:28:41.540: ISAKMP: Locking peer struct 0x6457345C, IPSEC refcount 1 for for stuff_ke
!!!!!May 17 13:28:41.544: ISAKMP:(0:1:SW:1): Creating IPSec SAs
May 17 13:28:41.544: inbound SA from 202.1.100.40 to 202.1.100.30 (f/i) 0/ 0
(proxy 4.4.4.4 to 3.3.3.3)
May 17 13:28:41.544: has spi 0x3F85BFA4 and conn_id 0 and flags 2
May 17 13:28:41.544: lifetime of 3600 seconds
May 17 13:28:41.544: lifetime of 4608000 kilobytes
May 17 13:28:41.548: has client flags 0x0
May 17 13:28:41.548: outbound SA from 202.1.100.30 to 202.1.100.40 (f/i) 0/0
(proxy 3.3.3.3 to 4.4.4.4)
May 17 13:28:41.548: has spi 244258562 and conn_id 0 and flags A
May 17 13:28:41.548: lifetime of 3600 seconds
May 17 13:28:41.548: lifetime of 4608000 kilobytes
May 17 13:28:41.552: has client flags 0x0
May 17 13:28:41.552: ISAKMP:(0:1:SW:1): sending packet to 202.1.100.40 my_port 500 peer_port 500 (I) QM_IDLE
May 17 13:28:41.556: ISAKMP:(0:1:SW:1):deleting node 1880679587 error FALSE reason "No Error"
Ma!!!!!!y 17 13:28:41.556: ISAKMP:(0:1:SW:1):Node 1880679587, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
May 17 13:28:41.556: ISAKMP:(0:1:SW:1):Old State = IKE_QM_I_QM1 New State = IKE_QM_PHASE2_COMPLETE
May 17 13:28:41.560: ISAKMP: Locking peer struct 0x6457345C, IPSEC refcount 2 for from create_transforms
May 17 13:28:41.564: ISAKMP: Unlocking IPSEC struct 0x6457345C from create_transforms, count 1!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 95 percent (95/100), round-trip min/avg/max = 60/167/272 ms
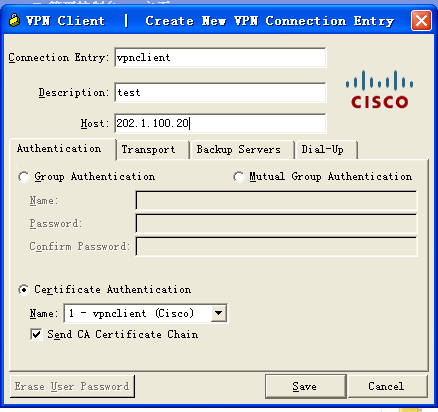
二:关于*** client 证书申请
点击enroll
department 名字必须给ipsecgroup定义的名字一致
进入这个目录用记事本打开复制
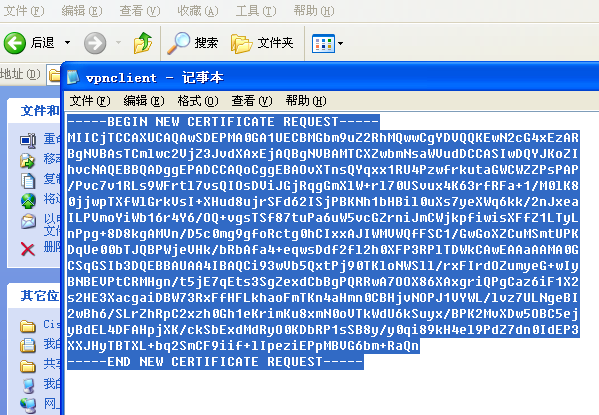
ca#crypto pki server ca request pkcs10 terminal 把内容粘贴到这
% Enter Base64 encoded or PEM formatted PKCS10 enrollment request.
% End with a blank line or "quit" on a line by itself.
-----BEGIN NEW CERTIFICATE REQUEST-----
MIICfzCCAWcCAQAwOjEPMA0GA1UEChMGbm9uZ2RhMRMwEQYDVQQLEwppcHNlY2dy
b3VwMRIwEAYDVQQDEwl2cG5jbGllbnQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAw
ggEKAoIBAQDpVSa+lcjqSZlhLlNdht9C5PcltYOFiyBMrgn8Bojp2sZwq45Efemu
PGnTvh1msXLICbU7shuAVzFsaHST26w0gZArEDR5FdOjSN/8Wqmby5NMJqRj/Mxi
241kmfFXjuw0CsizlGOsesB0LWg3SrZOHCKVdHF5P/bEicrDoAaqT9ZL3kSadFQQ
bWcP2IyIeb/8gZK0A0cZXK3oRVeGPiZdQixYVn7/K/V1zyrtJlPhkAcviVIPJsrj
ZNkRvHXjUcyUT8ZFEeg9w3AV7+VzCYrEsyndAqV+5HUYa8TSGDkMuXCCYn9P2TJa
+R1ekbPlVMEvrwmKQBNbpRHlTSpSh0I1AgMBAAGgADANBgkqhkiG9w0BAQQFAAOC
AQEATCR0s1FrX+UYQHYNKfVudG6b8A/KeBZ4pWV0KIeto86e2jNu8a8bHVqsSom3
UEIvWVuEB4KZCWFRCCrtebCvjhbpEAx8+dBccKjpswoeAR/wgEqY6WeaM+PIvgm2
e2Wss8lQf4rMj8Uxxc0Ubyfkidz/33t3Lu0GRrY+1/YCaBLP68uVzQq3BtzFbq6/
jAVvt1qDuftjCvZaFml4vw+asjo2o8g1mBwOEgxQ8wXa3ahR/4+SYS9joOJHif7L
ZTsTBgj00Z5qX5032aM38BvYib9mRpK2PHBy/wx2tAjSQ96xZ/jc4MD3GvPoKUvp
FnT8X43uf9gme3/qfvAPKjiySQ==
-----END NEW CERTIFICATE REQUEST-----
% Enrollment request pending, reqId=5
ca#crypto pki server ca info requests
Enrollment Request Database:
Subordinate CA certificate requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
RA certificate requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
Router certificates requests:
ReqID State Fingerprint SubjectName
--------------------------------------------------------------
5 pending 6F01A97C63E204788D48A9AAED8041FF cn=***client,ou=ipsecgroup,o=nongda
ca#crypto pki server ca grant 5 颁发证书
Writing 6.crt !
Writing 6.cnm !
Writing ca.ser !
% Granted certificate:
-----BEGIN CERTIFICATE-----
MIICxDCCAi2gAwIBAgIBBjANBgkqhkiG9w0BAQQFADApMScwJQYDVQQDEx5sYW9s
aWFuZyAgbz1ub25nZGEgaT16aGVuZ3pob3UwHhcNMTEwNTE3MTM1OTIyWhcNMTIw
NTE2MTM1OTIyWjA6MQ8wDQYDVQQKEwZub25nZGExEzARBgNVBAsTCmlwc2VjZ3Jv
dXAxEjAQBgNVBAMTCXZwbmNsaWVudDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBAOlVJr6VyOpJmWEuU12G30Lk9yW1g4WLIEyuCfwGiOnaxnCrjkR96a48
adO+HWaxcsgJtTuyG4BXMWxodJPbrDSBkCsQNHkV06NI3/xaqZvLk0wmpGP8zGLb
jWSZ8VeO7DQKyLOUY6x6wHQtaDdKtk4cIpV0cXk/9sSJysOgBqpP1kveRJp0VBBt
Zw/YjIh5v/yBkrQDRxlcrehFV4Y+Jl1CLFhWfv8r9XXPKu0mU+GQBy+JUg8myuNk
2RG8deNRzJRPxkUR6D3DcBXv5XMJisSzKd0CpX7kdRhrxNIYOQy5cIJif0/ZMlr5
HV6Rs+VUwS+vCYpAE1ulEeVNKlKHQjUCAwEAAaNnMGUwIwYDVR0fBBwwGjAYoBag
FIYSZnRwOi8vMjAyLjEuMTAwLjI0MB8GA1UdIwQYMBaAFDZvRdxAWyKO6+cjmcaJ
P/0TiZo4MB0GA1UdDgQWBBSHFWZCnsioo+C2zxx9W+3koBOptzANBgkqhkiG9w0B
AQQFAAOBgQAuo3LVgA2io1uwTq44cXA/RuLAN3aDyrFpvAP2yBWKmCCte+SH8Mb6
YXhSqE1YFCtWKZHsL7im+ocIiCUeg3uyoPdvfoKHuJswm3fJKnJO9ZV+kBHkdBoV
ClBDYJr1oWhhmc5/trC802QR2mCCx1RohB34l8UCH4fgCARO9p/rDA==
-----END CERTIFICATE-----
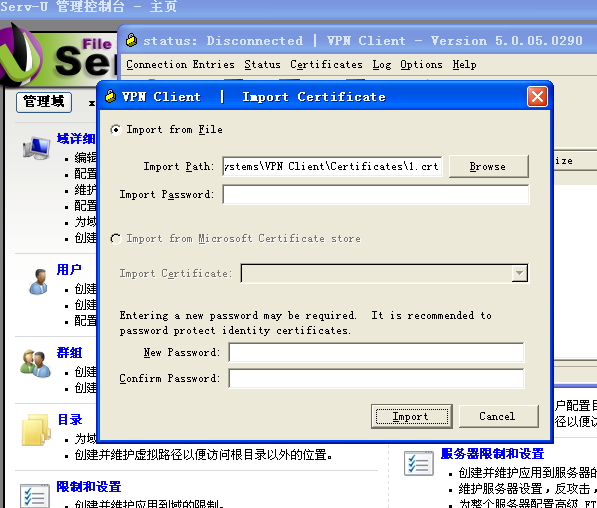
把证书从Server U中导出来放进下面的文件内(不能放在桌面)
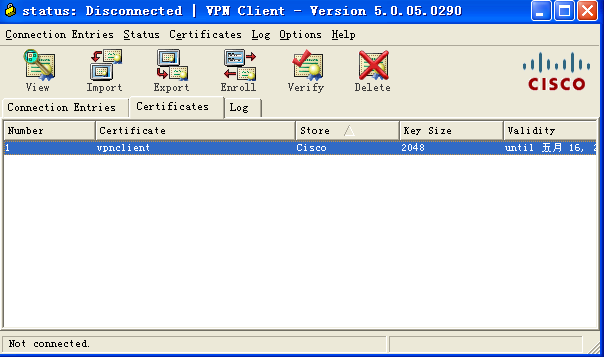
点击import导入证书,必须先导入 根证书,在导入***client证书,导入后如下图所示: