centos6.7下snort2.9.9.0+base+barnyard2的安装
0x01 YUM源准备
阿里云Linux安装镜像源地址:http://mirrors.aliyun.com/
第一步:备份原镜像文件
mv /etc/yum.repos.d/CentOS-Base.repo /etc/yum.repos.d/CentOS-Base.repo.bak
第二步:下载CentOS-Base.repo 到/etc/yum.repos.d/
CentOS 5
wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-5.repo
CentOS 6
wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-6.repo第三步:运行yum makecache生成缓存并更新yum
yum clean all
yum makecache
yum -y update0x02开始安装我们的IDS
0x02.1依赖包部分
使用PUT 上传我们的所需要的安装包,以下是本次安装涉及到
的
安装包。
- snortrules-snapshot-2990.tar.gz----snort规则库
- snort-2.9.9.0.tar.gz-----snort主程序
- libpcap-1.8.1.tar.gz
- libdnet-1.12.tgz
- daq-2.0.6.tar.gz
- base-1.4.5.tar.gz
- barnyard2-1.9.tar.gz
- adodb-5.20.9.zip
开始安装依赖包
yum install -y epel-release
yum install -y gcc gcc-c++ flex bison zlib* libxml2 libpcap* pcre* tcpdump git libtool curl man make第一步:先开始安装libdnet
cd centos6.7-snort
tar zxvf libdnet-1.12.tgz
cd libdnet-1.12
./configure
make && make install第二步:安装libpcap
tar -zxvf libpcap-1.8.1.tar.gz
cd libpcap-1.8.1
./configure
make && make install第三步:安装daq
tar zxvf daq-2.0.6.tar.gz
cd daq-2.0.6
./configure
make && make install0x02.2开始安装snort
与上文相同。
tar zxvf snort-2.9.9.0.tar.gz
cd snort-2.9.9.0
./configure
make && make install第一步:先创建配置文件目录,复制配置文件
mkdir /etc/snort
cp /root/centos6.7-snort/snort-2.9.9.0/etc/* /etc/snort/第二步:复制规则库至配置文件目录
cd /etc/snort/
cd /root/centos6.7-snort
tar zxvf snortrules-snapshot-2990.tar.gz
mv so_rules/ /etc/snort/
mv rules/ /etc/snort/
mv preproc_rules/ /etc/snort/
mv etc/ /etc/snort/
cd /etc/snort/
touch /etc/snort/rules/white_list.rules /etc/snort/rules/black_list.rules第三步:创建snort运行用户
groupadd -g 4000 snort
useradd snort -u 4000 -d /var/log/snort -s /sbin/nologin -c SNORT_IDS -g snort
chown -R snort:snort /etc/snort/*
chown -R snort:snort /var/log/snort第四步:配置snort.conf文件
(一)、修改rules的路径
var RULE_PATH ../rules ---> var RULE_PATH /etc/snort/rules
var SO_RULE_PATH ../so_rules ---> var SO_RULE_PATH /etc/snort/so_rules
var PREPROC_RULE_PATH ../preproc_rules ---> var PREPROC_RULE_PATH /etc/snort/preproc_rules
var WHITE_LIST_PATH ../rules ---> var WHITE_LIST_PATH /etc/snort/rules
var BLACK_LIST_PATH ../rules ---> var BLACK_LIST_PATH /etc/snort/rules(二)、修改log目录
# config logdir: ---> config logdir:/var/log/snort(三)、修改输出配置
# output unified2: filename merged.log, limit 128, nostamp, mpls_event_types, vlan_event_types ---> output unified2: filename snort.log, limit 128第五步:创建链接文件,并赋予权限
cd /usr/bin/
ln -s /usr/local/bin/snort snort
mkdir /usr/local/lib/snort_dynamicrules
chown snort:snort /usr/local/lib/snort_dynamicrules/
chown -R snort:snort /usr/local/lib/snort_dynamicrules/
chmod -R 755 /usr/local/lib/snort_dynamicrules/第六步:创建测试数据规则
vi /etc/snort/rules/local.rules
alert icmp any any -> $HOME_NET any (msg:”Ping”;sid:1000003;rev:1;)snort -u snort -g snort -c /etc/snort/snort.conf -i eth0 -A console0x02.2barnyard2部分
由于barnyard2的主要功能是将snort的事件写入数据库,所以我们这一块分两部分,一个是数据库的安装配置,还有一个就是barnyard2的安装配置。
0x02.2.1安装数据库
第一步:安装数据库,并设置数据库的状态和密码
yum -y install mysql-server mysql-devel php-mysql php-adodb php-pear php-gd libtool php-imap php-ldap php-mbstring php-odbc php-pear php-xml php-pecl-apc
chkconfig --levels 235 mysqld on
service mysqld start
/usr/bin/mysqladmin -u root password 'root'第二步:创建数据库及操作用户
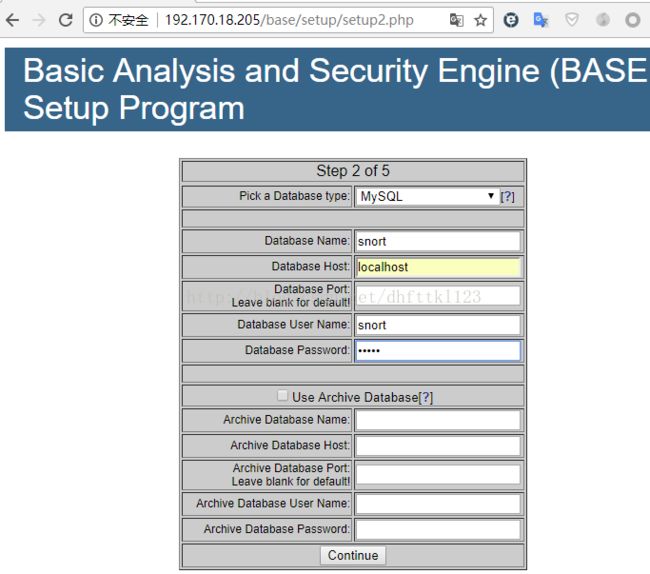
create database snort;
create user 'snort'@'localhost' identified by 'snort';
grant create,select,update,insert,delete on snort.* to snort@localhost identified by 'snort';
set password for snort@localhost=password('snort');
source /root/centos6.7-snort/barnyard2-1.9/schemas/create_mysql;
flush privileges;0x02.2.2安装barnyard2
第一步:开始安装barnyard2,并复制配置文件
./configure --with-mysql --with-mysql-libraries=/usr/lib64/mysql
make && make install
mkdir /var/log/barnyard2
touch /var/log/snort/barnyard2.waldo
chown -R snort:snort /var/log/snort/barnyard2.waldo
cp /root/centos6.7-snort/barnyard2-1.9/etc/barnyard2.conf /etc/snort/第二步:修改配置文件
#config logdir: /tmp ---> config logdir: /var/log/barnyard2
#config hostname: thor ---> config hostname: localhost
#config interface: eth0 ---> config interface: eth0
#config waldo_file: /tmp/waldo ---> config waldo_file: /var/log/snort/barnyard2.waldo
# output database: log, mysql, user=root password=test dbname=db host=localhost --->
output database: log, mysql, user=snort password=snort dbname=snort host=localhost
以上就是我们barnyard2的安装部分
0x03联合运行snort和barnyard2
这里需要有一个地方注意,就是我们最好先运行barnyard2,然后再运行snort,因为barnyard2会先监听有没有新数据产生。
第一步:先运行barnyard2
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snortsnort -q -u snort -g snort -c /etc/snort/snort.conf -i eth0 -D0x03.1查看barnyard2结果
[root@snort centos6.7-snort]# barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snort
Running in Continuous mode
--== Initializing Barnyard2 ==--
Initializing Input Plugins!
Initializing Output Plugins!
Parsing config file "/etc/snort/barnyard2.conf"
ERROR: Unable to open SID file '/etc/snort/sid-msg.map' (No such file or directory)
Log directory = /var/log/barnyard2
database: compiled support for (mysql)
database: configured to use mysql
database: schema version = 107
database: host = localhost
database: user = snort
database: database name = snort
database: sensor name = localhost:eth0
database: sensor id = 1
database: sensor cid = 1
database: data encoding = hex
database: detail level = full
database: ignore_bpf = no
database: using the "log" facility
--== Initialization Complete ==--
______ -*> Barnyard2 <*-
/ ,,_ \ Version 2.1.9 (Build 263)
|o" )~| By the SecurixLive.com Team: http://www.securixlive.com/about.php
+ '''' + (C) Copyright 2008-2010 SecurixLive.
Snort by Martin Roesch & The Snort Team: http://www.snort.org/team.html
(C) Copyright 1998-2007 Sourcefire Inc., et al.
WARNING: Ignoring corrupt/truncated waldofile '/var/log/snort/barnyard2.waldo'
Opened spool file '/var/log/snort/snort.log.1500636770'
07/21-19:32:50.946642 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
Waiting for new data
Closing spool file '/var/log/snort/snort.log.1500636770'. Read 2 records
Opened spool file '/var/log/snort/snort.log.1500636807'
07/21-19:33:27.973221 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
Waiting for new data
07/21-19:33:28.960111 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:29.967876 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:30.899934 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.81.229.151 -> 192.170.40.52
07/21-19:33:30.957175 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:31.965832 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:32.958331 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:33.965026 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:34.956528 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:35.965217 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:36.901655 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 222.72.118.69 -> 192.170.40.52
07/21-19:33:36.971852 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:37.978949 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:38.859376 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {UDP} 157.56.106.184:3544 -> 192.170.40.30:55941
07/21-19:33:38.986988 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
0x03.2查看数据库的情况
[root@snort centos6.7-snort]# barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -g snort -u snort
Running in Continuous mode
--== Initializing Barnyard2 ==--
Initializing Input Plugins!
Initializing Output Plugins!
Parsing config file "/etc/snort/barnyard2.conf"
ERROR: Unable to open SID file '/etc/snort/sid-msg.map' (No such file or directory)
Log directory = /var/log/barnyard2
database: compiled support for (mysql)
database: configured to use mysql
database: schema version = 107
database: host = localhost
database: user = snort
database: database name = snort
database: sensor name = localhost:eth0
database: sensor id = 1
database: sensor cid = 1
database: data encoding = hex
database: detail level = full
database: ignore_bpf = no
database: using the "log" facility
--== Initialization Complete ==--
______ -*> Barnyard2 <*-
/ ,,_ \ Version 2.1.9 (Build 263)
|o" )~| By the SecurixLive.com Team: http://www.securixlive.com/about.php
+ '''' + (C) Copyright 2008-2010 SecurixLive.
Snort by Martin Roesch & The Snort Team: http://www.snort.org/team.html
(C) Copyright 1998-2007 Sourcefire Inc., et al.
WARNING: Ignoring corrupt/truncated waldofile '/var/log/snort/barnyard2.waldo'
Opened spool file '/var/log/snort/snort.log.1500636770'
07/21-19:32:50.946642 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
Waiting for new data
Closing spool file '/var/log/snort/snort.log.1500636770'. Read 2 records
Opened spool file '/var/log/snort/snort.log.1500636807'
07/21-19:33:27.973221 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
Waiting for new data
07/21-19:33:28.960111 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:29.967876 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:30.899934 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.81.229.151 -> 192.170.40.52
07/21-19:33:30.957175 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:31.965832 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:32.958331 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:33.965026 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:34.956528 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:35.965217 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:36.901655 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 222.72.118.69 -> 192.170.40.52
07/21-19:33:36.971852 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:37.978949 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
07/21-19:33:38.859376 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {UDP} 157.56.106.184:3544 -> 192.170.40.30:55941
07/21-19:33:38.986988 [**] [1:1000003:1] Snort Alert [1:1000003:0] [**] [Classification ID: (null)] [Priority ID: 0] {ICMP} 218.109.1.233 -> 192.170.40.52
mysql> use snort;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> select * from e
edit encoding encoding.encoding_type encoding_type event.cid event.signature exit
ego encoding.encoding_text encoding_text event event.sid event.timestamp
mysql> select * from event;
+-----+-----+-----------+---------------------+
| sid | cid | signature | timestamp |
+-----+-----+-----------+---------------------+
| 1 | 1 | 1 | 2017-07-21 19:32:50 |
| 1 | 2 | 1 | 2017-07-21 19:33:27 |
| 1 | 3 | 1 | 2017-07-21 19:33:28 |
| 1 | 4 | 1 | 2017-07-21 19:33:29 |
| 1 | 5 | 1 | 2017-07-21 19:33:30 |
| 1 | 6 | 1 | 2017-07-21 19:33:30 |
| 1 | 7 | 1 | 2017-07-21 19:33:31 |
| 1 | 8 | 1 | 2017-07-21 19:33:32 |
| 1 | 9 | 1 | 2017-07-21 19:33:33 |
| 1 | 10 | 1 | 2017-07-21 19:33:34 |
| 1 | 11 | 1 | 2017-07-21 19:33:35 |
| 1 | 12 | 1 | 2017-07-21 19:33:36 |
| 1 | 13 | 1 | 2017-07-21 19:33:36 |
| 1 | 14 | 1 | 2017-07-21 19:33:37 |
| 1 | 15 | 1 | 2017-07-21 19:33:38 |
| 1 | 16 | 1 | 2017-07-21 19:33:38 |
| 1 | 17 | 1 | 2017-07-21 19:33:39 |
| 1 | 18 | 1 | 2017-07-21 19:33:40 |
+-----+-----+-----------+---------------------+0x04安装base
第一步:先安装LMAP环境
yum install -y httpd mysql-server php php-mysql php-mbstring php-mcrypt mysql-devel php-gd第二步:安装pear插件
yum install -y php-pear
pear upgrade pear
pear channel-update pear.php.net
pear install mail
pear install Image_Graph-alpha Image_Canvas-alpha Image_Color Numbers_Roman
pear install mail_mime第三步:安装adodb
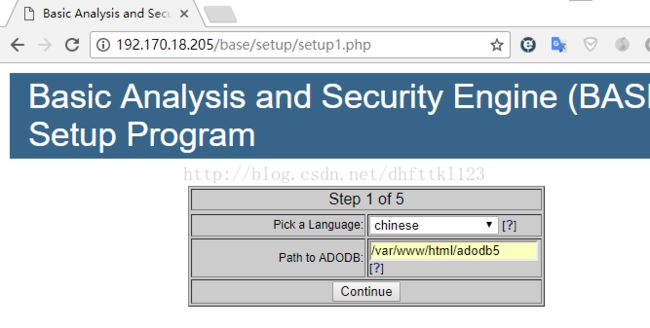
unzip adodb-5.20.9.zip
mv ./adodb5 /var/www/html/第四步:安装base
tar zxvf base-1.4.5.tar.gz
mv base-1.4.5 /var/www/html/base第五步:配置PHP错误信息,并赋予权限
vi /etc/php.ini
修改error_reporting 为 E_ALL & ~E_NOTICE
chown -R apache:apache /var/www/html
chmod 755 /var/www/html
第六步:开启服务,并关闭防火墙
service mysqld restart
service httpd resatrt
service iptables stop第七步:关闭selinux(这步不做很可能造成无法打开页面)
setenforce 0
vi /etc/selinux/config
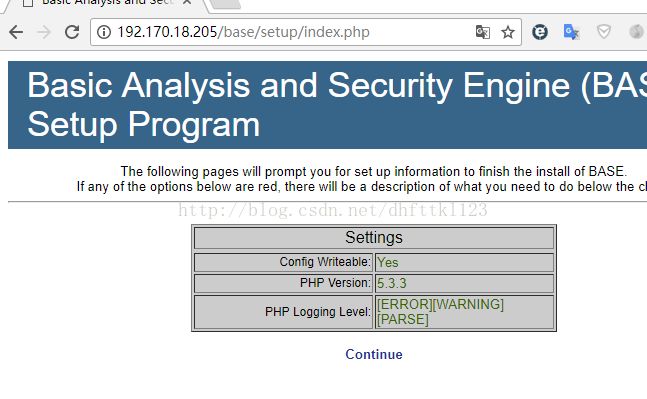
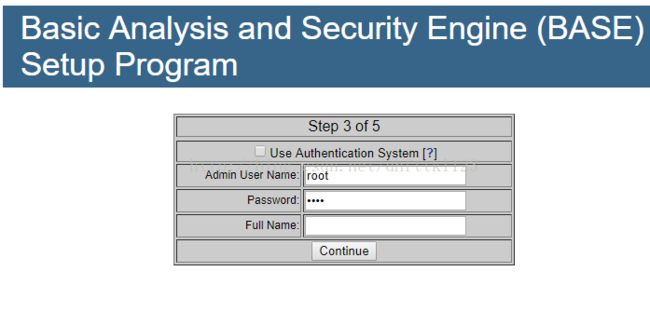
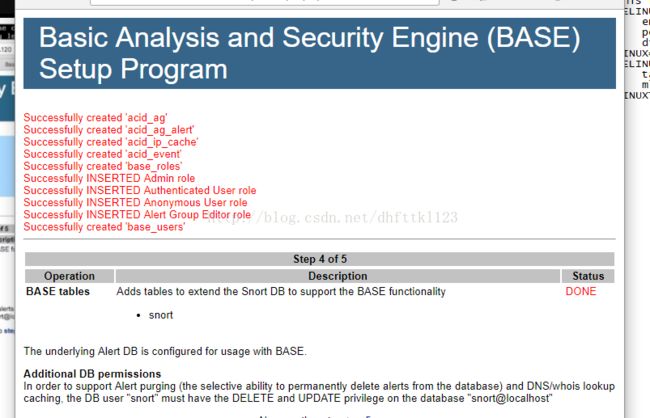
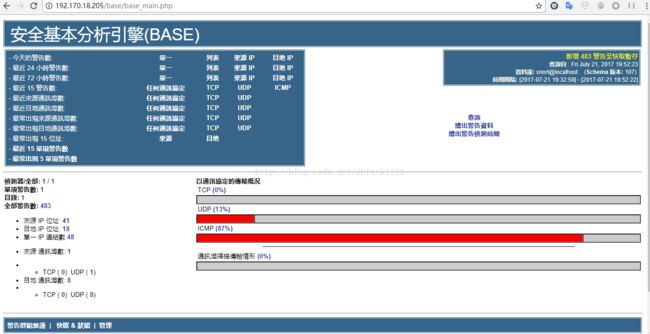
将SELINUX=enforcing改为SELINUX=disabled第八步:打开base页面,并进行配置
安装完成