nginx虚拟主机,重定向 ,反向代理
nginx
1.nginx配置文件板块介绍:
1、全局块:配置影响nginx全局的指令。一般有运行nginx服务器的用户组,nginx进程pid存放路径,日志存放路径,配置文件引入,允许生成worker process数等。
2、events块:配置影响nginx服务器或与用户的网络连接。有每个进程的最大连接数,选取哪种事件驱动模型处理连接请求,是否允许同时接受多个网路连接,开启多个网络连接序列化等。
3、http块:可以嵌套多个server,配置代理,缓存,日志定义等绝大多数功能和第三方模块的配置。如文件引入,mime-type定义,日志自定义,是否使用sendfile传输文件,连接超时时间,单连接请求数等。
4、server块:配置虚拟主机的相关参数,一个http中可以有多个server。
5、location块:配置请求的路由,以及各种页面的处理情况。
详细参数:
#user administrator administrators; #配置用户或者组,默认为nobody nobody。
#worker_processes 2; #允许生成的进程数,默认为1
#pid /nginx/pid/nginx.pid; #指定nginx进程运行文件存放地址
error_log log/error.log debug; #制定日志路径,级别。这个设置可以放入全局块,http块,server块,级别以此为:debug|info|notice|warn|error|crit|alert|emerg
events {
accept_mutex on; #设置网路连接序列化,防止惊群现象发生,默认为on
multi_accept on; #设置一个进程是否同时接受多个网络连接,默认为off
#use epoll; #事件驱动模型,select|poll|kqueue|epoll|resig|/dev/poll|eventport
worker_connections 1024; #最大连接数,默认为512
}
http {
include mime.types; #文件扩展名与文件类型映射表
default_type application/octet-stream; #默认文件类型,默认为text/plain
#access_log off; #取消服务日志
log_format myFormat '$remote_addr–$remote_user [$time_local] $request $status $body_bytes_sent $http_referer $http_user_agent $http_x_forwarded_for'; #自定义格式
access_log log/access.log myFormat; #combined为日志格式的默认值
sendfile on; #允许sendfile方式传输文件,默认为off,可以在http块,server块,location块。
sendfile_max_chunk 100k; #每个进程每次调用传输数量不能大于设定的值,默认为0,即不设上限。
keepalive_timeout 65; #连接超时时间,默认为75s,可以在http,server,location块。
upstream mys {
server 127.0.0.1:7878;
server 172.25.30.4:3333 backup; #热备
}
error_page 404 https://www.baidu.com; #错误页
server {
keepalive_requests 120; #单连接请求上限次数。
listen 80; #监听端口
server_name 127.0.0.1; #监听地址
location ~*^.+$ { #请求的url过滤,正则匹配,~为区分大小写,~*为不区分大小写。
#root path; #根目录
#index vv.txt; #设置默认页
proxy_pass http://mysvr; #请求转向mysvr 定义的服务器列表
deny 127.0.0.1; #拒绝的ip
allow 172.25.30.250; #允许的ip
}
}
}
注意:
1.$remote_addr 与$http_x_forwarded_for 用以记录客户端的ip地址; 2.$remote_user :用来记录客户端用户名称;
3.$time_local : 用来记录访问时间与时区;.$request : 用来记录请求的url与http协议;
5.$status : 用来记录请求状态;成功是200,
6.$body_bytes_s ent :记录发送给客户端文件主体内容大小;
7.$http_referer :用来记录从那个页面链接访问过来的;
8.$http_user_agent :记录客户端浏览器的相关信息;
2、惊群现象:一个网路连接到来,多个睡眠的进程被同事叫醒,但只有一个进程能获得链接,这样会影响系统性能。
3、每个指令必须有分号结束。1.nginx实现多个虚拟主机:
[root@server1 ~]# mkdir /www1
[root@server1 ~]# mkdir /www2
[root@server1 ~]# vim /www1/index.html
[root@server1 ~]# vim /www2/index.html
[root@server1 ~]# cat /www1/index.html
www.westos.org
[root@server1 ~]# cat /www2/index.html
www.linux.org
[root@foundation30 ~]# cat /etc/hosts
172.25.30.1 www.westos.org www.linux.orgnginx配置文件
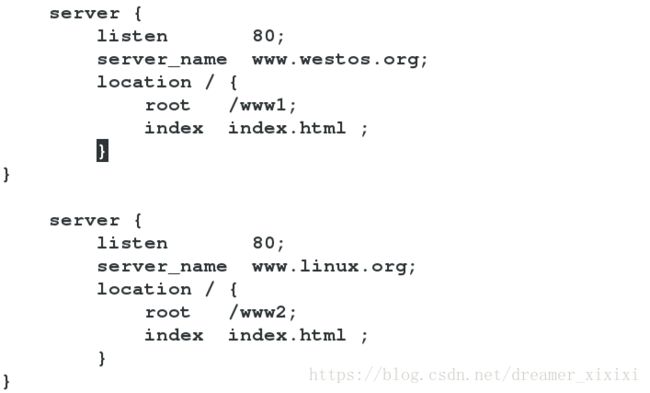
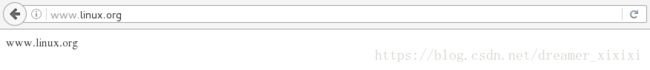
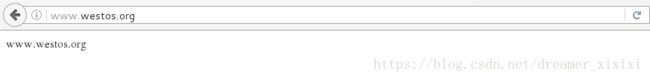
访问www.westos.org

访问www.linux.org
2.添加加密认证:
[root@server1 ~]# vim /usr/local/nginx/conf/nginx.conf
server {
listen 443 ssl;
server_name www.westos.org;
ssl_certificate cert.pem;
ssl_certificate_key cert.pem;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}
[root@server1 ~]# nginx -t
nginx: [emerg] BIO_new_file("/usr/local/nginx/conf/cert.pem") failed (SSL: error:02001002:system library:fopen:No such file or directory:fopen('/usr/local/nginx/conf/cert.pem','r') error:2006D080:BIO routines:BIO_new_file:no such file)
nginx: configuration file /usr/local/nginx/conf/nginx.conf test failedvim /usr/local/nginx/conf/nginx.conf#开启加密认证:

重新加载失败我们需要制作安全证书:
制作安全证书
[root@server1 pki]# cd /etc/pki/tls/certs/
[root@server1 certs]# make cert.pem
umask 77 ; \
PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
/usr/bin/openssl req -utf8 -newkey rsa:2048 -keyout $PEM1 -nodes -x509 -days 365 -out $PEM2 -set_serial 0 ; \
cat $PEM1 > cert.pem ; \
echo "" >> cert.pem ; \
cat $PEM2 >> cert.pem ; \
rm -f $PEM1 $PEM2
Generating a 2048 bit RSA private key
..................................+++
..........................+++
writing new private key to '/tmp/openssl.1V00AV'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:shannxi
Locality Name (eg, city) [Default City]:xi'an
Organization Name (eg, company) [Default Company Ltd]:westos
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:server1
Email Address []:root@localhost
[root@server1 certs]# cp cert.pem /usr/local/nginx/conf/
[root@server1 certs]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@server1 certs]# ll cert.pem
-rw------- 1 root root 3088 Aug 7 08:14 cert.pem加密式访问:
下载证书后:
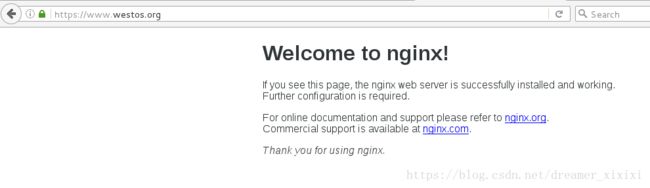
4.端口重定向
无论我们访问www.westos.org还是westos.org都可以访问到相同的界面返回200–>OK
[root@server1 certs]# vim /usrl/local/nginx/conf/nginx.conf

访问结果:
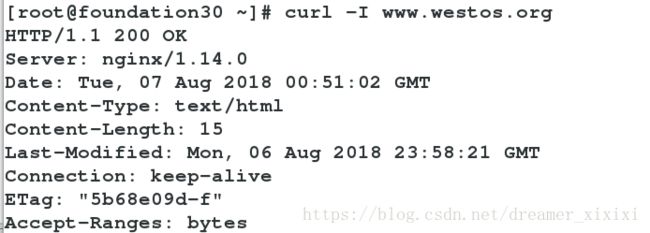
重定向:server_name www.westos.org westos.org;
rewrite ^(.*) https://www.westos.org h t t p s : / / w w w . w e s t o s . o r g 1 permanent;#当访问www.westos.org或者westos.org都转发到www.westos.org访问界面;永久转发返回301;临时转发返回302;错误返回404;permanent为永久转发,redirect为临时转发


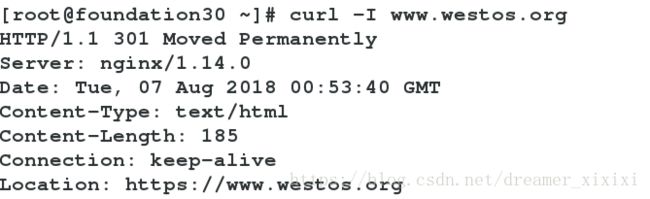
访问重定向到域名后面所根的第二串字符文件
rewrite ^(.*) https://www.westos.org h t t p s : / / w w w . w e s t o s . o r g 1 permanent;

访问www.westos.org进入该server端后如果后面以bbs结尾重定向—->bbs.westos.org
server {
listen 80;
server_name www.westos.org westos.org bbs.westos.org;
rewrite ^/bbs$ https://bbs.westos.org permanent;

[root@server1 certs]# mkdir /www1/bbs
[root@server1 certs]# vim /www1/bbs/index.html
[root@server1 certs]# cat /www1/bbs/index.html
www.westos.org—–bbs
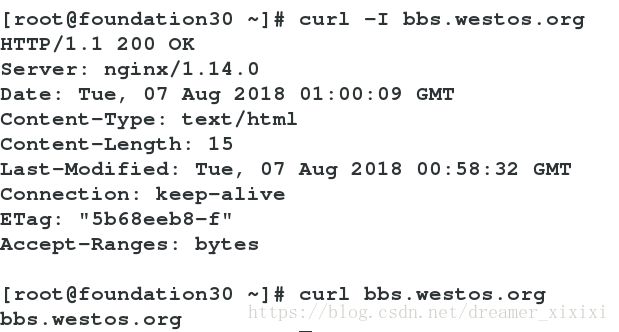
rewrite ^/bbs$ https://bbs.westos.org permanent;以bbs开头的任意字符访问都会重定向到bbs.westos.org
rewrite ^/bbs/(.*) http://bbs.westos.org/ h t t p : / / b b s . w e s t o s . o r g / 1 permanent;以bbs结尾的任意字符访问都会重定向到bbs.westos.org
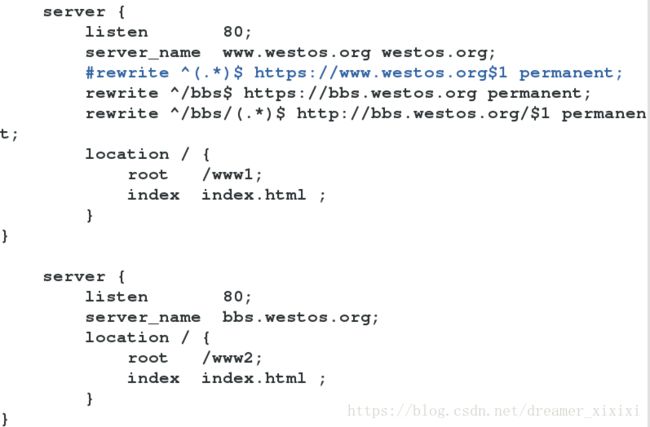

访问www.westos.org/bbs/index.html转发—–>bbs.westos.org/index.html
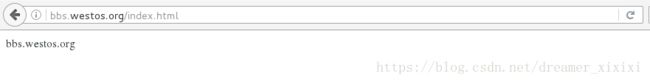
5.逆向转发:

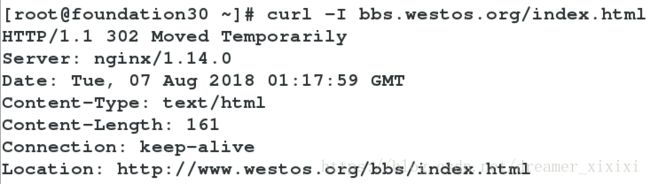

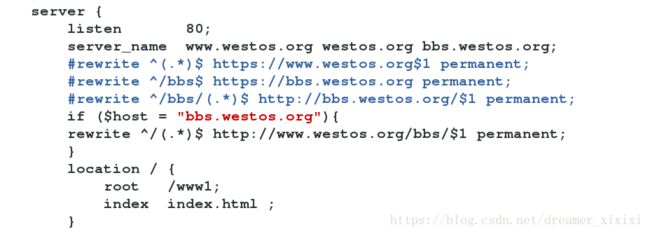
有时候我们回绝这样太繁琐因此我们可以用条件判断把他们写在一个模块中
server {
listen 80;
server_name www.westos.org westos.org bbs.westos.org;
#rewrite ^(.*)$ https://www.westos.org$1 permanent;
#rewrite ^/bbs$ https://bbs.westos.org permanent;
#rewrite ^/bbs/(.*)$ http://bbs.westos.org/$1 permanent;
if ($host = "bbs.westos.org"){
rewrite ^/(.*)$ http://www.westos.org/bbs/$1 permanent;
}
location / {
root /www1;
index index.html ;
}
}
# server {
# listen 80;
# server_name bbs.westos.org;
# rewrite ^/(.*)$ http://www.westos.org/bbs/$1;
# #location / {
# # root /www2;
# # index index.html ;
# #}
# }
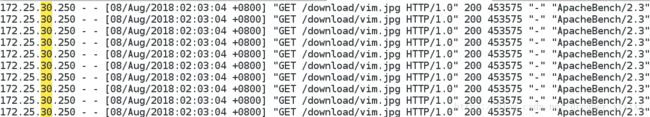
}[root@foundation30 ~]# curl -I http://172.25.30.1/download/vim.jpg
HTTP/1.1 200 OK
Server: nginx/1.14.0
Date: Tue, 07 Aug 2018 17:58:17 GMT
Content-Type: image/jpeg
Content-Length: 453575
Last-Modified: Fri, 20 May 2016 03:53:06 GMT
Connection: keep-alive
ETag: "573e8a22-6ebc7"
Accept-Ranges: bytes一次访问一个访问10次——>每次处理处理一个每次都ok
[root@foundation30 ~]# ab -c1 -n 10 http://172.25.30.1/download/vim.jpg
Benchmarking 172.25.30.1 (be patient).....done
Server Software: nginx/1.14.0
Server Hostname: 172.25.30.1
Server Port: 80
Document Path: /download/vim.jpg
Document Length: 453575 bytes
Concurrency Level: 1
Time taken for tests: 0.013 seconds
Complete requests: 10
Failed requests: 0
Write errors: 0
Total transferred: 4538140 bytes
HTML transferred: 4535750 bytes
Requests per second: 745.49 [#/sec] (mean)
Time per request: 1.341 [ms] (mean)
Time per request: 1.341 [ms] (mean, across all concurrent requests)
Transfer rate: 330384.47 [Kbytes/sec] received
Connection Times (ms)
min mean[+/-sd] median max
Connect: 0 0 0.3 0 1
Processing: 1 1 0.4 1 2
Waiting: 0 0 0.1 0 0
Total: 1 1 0.7 1 3
Percentage of the requests served within a certain time (ms)
50% 1
66% 1
访问生成日至在:/usr/local/nginx/logs/access.log #200--->0k一次访问10个并发处理一个所以有九个失败一个成功
[root@foundation30 ~]# ab -c10 -n 10 http://172.25.30.1/download/vim.jpg
Benchmarking 172.25.30.1 (be patient).....done
Server Software: nginx/1.14.0
Server Hostname: 172.25.30.1
Server Port: 80
Document Path: /download/vim.jpg
Document Length: 537 bytes
Concurrency Level: 10
Time taken for tests: 0.027 seconds
Complete requests: 10
Failed requests: 1
(Connect: 0, Receive: 0, Length: 1, Exceptions: 0)
Write errors: 0
Non-2xx responses: 9
Total transferred: 460393 bytes
HTML transferred: 458408 bytes
Requests per second: 367.69 [#/sec] (mean)
Time per request: 27.197 [ms] (mean)
Time per request: 2.720 [ms] (mean, across all concurrent requests)
Transfer rate: 16531.33 [Kbytes/sec] received
Connection Times (ms)
min mean[+/-sd] median max
Connect: 0 0 0.0 0 0
Processing: 25 26 0.5 26 27
Waiting: 0 21 10.7 26 26
Total: 25 26 0.5 26 27 limit_conn_zone $binary_remote_addr zone=addr:10m;
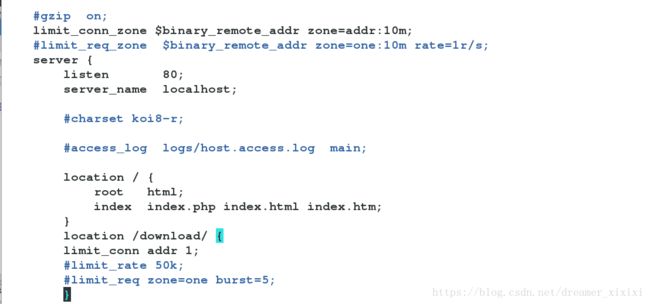
limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s;6.控制限速;控制带宽
limit_conn_zone $binary_remote_addr zone=addr:10m;
limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s; #zone域命名为one;rate=1r/s # 每秒处理一次
location /download/ {
limit_conn addr 1; #并发数c1-->200c10测试-->503
limit_rate 50k; #下载速度为50k每秒;
limit_req zone=one burst=5; #burst=5带宽只处理五个再处理别的测试下载传输速度:
time wget http://172.25.30.1/download/mysql-boost-5.7.17.tar.gz
[root@foundation30 ~]# ab -c10 -n 10 http://172.25.30.1/download/vim.jpg
7.访问控制
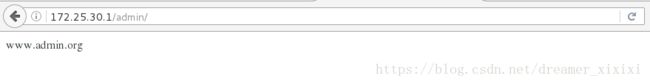
location /admin/{
allow 172.25.30.250;
deny all;
}
#访问读取顺序先读上面一行再读下面后面不会覆盖前一句即使deny all但是当172.25.30.250访问admin时是先读allow的
[root@server1 html]# mkdir admin
[root@server1 html]# vim admin/index.html
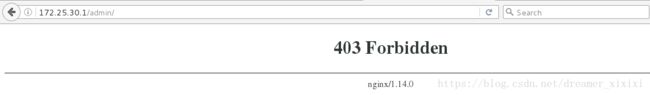
www.admin.orglocation /admin/{
deny all;
allow 172.25.30.250;
}
这个设置172.25.30.250访问是被拒绝的:location /admin/{
allow 172.25.30.0/24;
deny all;
}
允许30网段访问
location ~ .*\.(gif|jpg|png)$ {
expires 30d;
}
所有的网页格式为gif|jpg|png格式保存30天
防止恶意解析---->所有的服务解析到你的访问域,
引流:根据访问匹配;重定向
server {
listen 80;
server_name _;
return 500;
所有 访问都返回500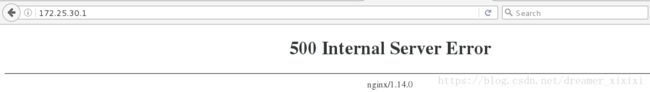
这样好像也不太好我们可以把它重定向到别的界面:

8.访问乱码:
[root@server1 conf]# vim /www1/index.html
[root@server1 conf]# cat /www1/index.html
www.westos.org —-小仙女

server {
listen 80;
server_name www.westos.org westos.org bbs.westos.org;
charset utf-8;
location / {
root /www1;
index index.html ;
}
9.防盗链:
盗链即当客户段把我们伪装成一个服务器去访问我们网站的东西。
Client–访问—>http1()—–>nginx
有时候是client 想要盗链有时候是有些网站恶意耗费我们的资源
实验:
Server2:
[root@server2 ~]# yum install httpd
[root@server2 ~]# /etc/init.d/httpd start
Starting httpd: httpd: Could not reliably determine the server's fully qualified domain name, using 172.25.30.2 for ServerName
[ OK ]
[root@server2 ~]# vim /var/www/html/
[root@server2 ~]# vim /var/www/html/index.html #盗用www.westos.org网站的网页
浏览器访问解析:
172.25.30.2 server2 daolian.westos.com
Nginx------>/www1/images/iso7gif
location / {
root /www1;
index index.html ;
}
}
表面访问server2其实是伪装成了server2去server1上的nginx:
当然我们是可以看到的:
[root@server1 logs]# cat access.log
172.25.30.250 - - [08/Aug/2018:06:48:40 +0800] "GET /images/iso7.gif HTTP/1.1" 200 225325 "http://daolian.westos.com/" "Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0"因此我们需要作的就是防盗链:
设置访问控制和重定向如果访问格式是以后缀格式为.jpg/png/jif结尾我们可以给他回复403
server {
listen 80;
server_name www.westos.org westos.org bbs.westos.org;
location / {
root /www1;
index index.html ;
}
location ~ \.(gif|jpg|png)$ {
root /www1;
valid_referers none blocked www.westos.org;
if ($invalid_referer) {
return 403;
# 除了自己访问自己以这种格式被允许其他的都回复403
# 我们可以给他们返回盗链的页面: valid_referers none blocked www.westos.org;
if ($invalid_referer) {
#return 403;
rewrite ^/ http://bbs.westos.org/daolian.jpg
}
}
}
server {
listen 80;
server_name bbs.westos.org;
#rewrite ^/(.*)$ http://www.westos.org/bbs/$1;
location / {
root /www2;
index index.php index.html ;
}
}