源NAT 和 目的 NAT 的区别:
Source Nat 业务场景:内网地址访问外部地址、资源时使用;源地址是转换前的内网地址,目标地址是转换后的公网地址。
方向【源/内网地址 ------转换为-------目的/公网地址】;
Destination Nat 业务场景:从公网访问内部特定IP或特定IP的特定端口时使用;源地址是转换前的公网地址,目的地址是转换后的内网IP或IP:port.
方向【源/公网地址 ------转换为-------目的/内网地址】;
一、定义 目的 NAT
== 创建Dnat pool
set security nat destination pool DP_TRUST_MQI_8088 address 172.22.201.19/32
set security nat destination pool DP_TRUST_MQI_8088 address port 8088
==创建DNAT规则
set security nat destination rule-set DNAT_FROM_ISP6 rule ISP6_TO_LIMS_BY_Owenli match destination-address-name WAN3006_172
set security nat destination rule-set DNAT_FROM_ISP6 rule ISP6_TO_LIMS_BY_Owenli match destination-port 8089
set security nat destination rule-set DNAT_FROM_ISP6 rule ISP6_TO_LIMS_BY_Owenli then destination-nat pool DP_TRUST_MQI_8088
备注:WAN3006_172 是ISP提供的公网IP,或接口地址或做了ARP_proxy
set security address-book global address WAN3006_172 210.X.X.172/32
==创建区域间的控制策略
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN match source-address any
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN match destination-address QI_PRIVATE
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN match application tcp-80
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN match application tcp-8888
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN match application tcp-8089
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN then permit
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN then log session-init
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN then log session-close
set security policies from-zone ISP6 to-zone trust policy ISP6_TO_TRUST_IMMQI_BY_KEVIN then count
二、定义源NAT【design NAT TO iplc 】
set security nat source rule-set SNAT_Design_TO_ISP1 from zone Design
set security nat source rule-set SNAT_Design_TO_ISP1 to zone ISP1
==定义Snat pool
set security nat source pool SP_ISP1_241 address 119.X.X.241/32
==定义Snat 规则
set security nat source rule-set SNAT_Design_TO_ISP1 rule Design_TO_ISP1_ANY match source-address design_team
set security nat source rule-set SNAT_Design_TO_ISP1 rule Design_TO_ISP1_ANY match destination-address 0.0.0.0/0
set security nat source rule-set SNAT_Design_TO_ISP1 rule Design_TO_ISP1_ANY then source-nat pool SP_ISP1_241
set security nat source rule-set SNAT_Design_TO_ISP1 rule Design_TO_ISP1_ANY match source-address cnspdc4
set security nat source rule-set SNAT_Design_TO_ISP1 rule Design_TO_ISP1_ANY match destination-address 0.0.0.0/0
set security nat source rule-set SNAT_Design_TO_ISP1 rule Design_TO_ISP1_ANY then source-nat pool SP_ISP1_241
===定义不同区间的控制策略
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 match source-address cnspdc4
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 match destination-address any
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 match application any
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 then permit
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 then log session-init
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 then log session-close
set security policies from-zone Design to-zone ISP1 policy LEGACY_YF_DE_TO_ISP1 then count
===如果你有N条策略,那么你可能需要调整你新增策略的顺序即优先级,具体视策略内容调整顺序;
===修改策略LIMS-XQ-TEST-OWEN-EDIT的顺序在策略DENY之前
insert security policies from-zone ISP6 to-zone trust policy LIMS-PY-OWEN-EDIT before policy DENY
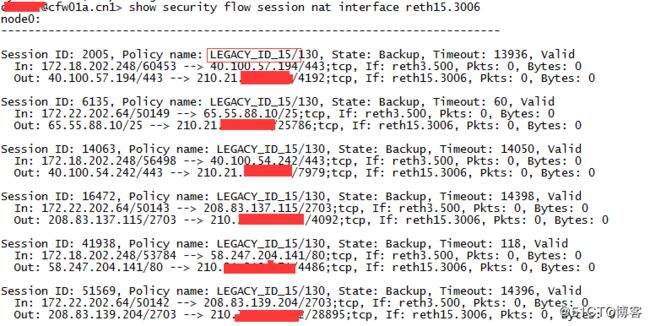
三、验证策略是否生效
show security flow session nat interface reth15.3006
注释:reth15.3006 属于ISP6.因此,查看reth15.3006的会话,从中查找是否出现定义的“区域间访问控制策略”。有,策略成功,没有,策略错误或策略优先顺序错误;
show security flow session nat interface reth15.3006 destination-port 443
注释:也可以用destination-port、source-port、source-prefix 、destination-prefix等参数对经过ISP6区域的数据流进行更精细的匹配,从结果中判断策略是否成功应用,加端口查询的方式尤其适用“内网服务器的业务,通过某个端口发布到外网,然后验证”