JACTF misc wp
0x00 该死的温柔
查看属性,guess,呃呃,看了大佬博客,才知道是guess隐写,在kali上用outguess还原即可。
先安装一下outguess, kail终端命令输入git clone https://github.com/crorvick/outguess,
安装包随即下载到文件夹。双击打开文件夹,右键点击空白区域选终端打开。随后输入以下命令./configure && make && make install 进行安装。
用outguess -help查看命令参数,之后用outguess -k ‘guess’ -r flag.jpg flag.txt,将jpg里面隐藏的flag信息写到flag.txt文件中,打开即可得到jactf{jactf_guess_steganography}。
题目之外来说一说outguess图片隐写软件:
加密:
outguess -k “my secret key” -d flag.txt demo.jpg out.jpg
加密之后,demo.jpg会覆盖out.jpg,
flag.txt中的内容是要隐藏的东西
解密:
outguess -k “my secret key” -r flag.jpg flag.txt
解密之后,解密内容放在flag.txt中
0x01 这是什么玩意儿
打开txt文件,真的想说什么玩意儿,2333
大佬博客说这是quoted-printable 编码,解码网站解码一下,得到

是与佛论禅,苦笑,同样解码,

发现是核心价值观编码,直接解码,得到jactf{hexin_yufo_qp}。
PS:这道题真的让我大开眼界,什么码都有,
0x02 so_easy
是一个exe文件但不能打开,用记事本打开(或者用strings命令)得到一串码,
Kf3kAFJMri71zQLADjAuHAPwXtTCSwRrcF9oeig4tZwqpur8i88LoJU1v8LcaKt2WutLqtRp988veY5FfyMwqs3zZiNvhqb6zFTHpn3fSmFuaogagzdqEuq5GiynnGfL7hQC9fbEKJV4MxqLYd9F6LvweLJ3cEaRfMjde2bvZUfgvgXDkCx8g7DwHrH7Mp4usUdB1YmgeuyKP1Z6GARYaWBDzunJ6dePDtddCkD2G11eF9E9vJooAPrZ7U3s1xeW1UYabFmLazHs5QkvthXeJqZewHDXEUCrBnnoYXZCbHBHfP9sD6NAgS3Gr6ZT6h4HNK9qkttjxk6SVF1ABfPmRsLCQXr6C6vnWq9YR1fk9hHCiW4sFiKPe2QR24h9dFFfjV4Pk3h6LawqT8me4rE1vJTBnMnhm4caXqGNhxz74GY1WmzUfWyrXmN3K1PvkhzARnFytP8ot5FsNzL3uHvJguE3mbKBuGdPQuCBk27D2CwXDtBdhcHXc9mATg89xtnmk2Wjro9PVvZqaxtWzMWsi1d91fu7RFRRJcJQ61ScaxyX9bop485xMszPSDVL1sxDHk5aCzJ6isswjntmqdix4WogfDQwRHwQyj6cBhkwdo52aV76t9Yw6sqGgi6ra6FyPp2ygPtoJrcpgJCXm9P23VoE9XEopJfr7MEpfoVvLon9xuSQ1JnyHKYSFcJoU5RX7erNWhY3bp4wUACr9JGRcGXrcGs9JjKqVnVGamNUc97xtrsbTYmMJYXp9HwPMFT7YQww9R8d3gE39JmhM214fr9ESZWzWac1nbhYdvbPS9edLe5wkjzNvGrmzctSfXU7ciGgMF8gAjsrMwBXQ9Kj9oLqVCfSXZHwBXcNthyjQt5hYAaRZnfxZLdoFXRmSByPSZjKrWa7K8sKNebbQTu1cEQ4f3rEuPFgpunELkrm8j7gcJyJmARdkiD5fqmgW9R2vNB9kXPNBMJqCham2kkfYe2NwteGzpiB3EsNhJiEk4GSQXEJ43FSW23rwYUaaq9E3LSL2jcBhndTbdcAvp3HZufRtvVKHxYL3tgnLHKZtPKRgZez7WGUR2LgJwQJ48dA8zcoyWovcDq2Mkz43JPJLkAXhtaFaAdvXpV3YMRNcGwCy6BftzA2vewJNroERmNHgLzJFa4LqnKB91iN2wcm6vF28YFwZjepujaZiEMqdUcEdiyG6M7cC2Pot9SXJB6Hzd16H9WhSE9Qs8RFy6AMFbxvvTpW6CYhNMdSr4kBzCB1iTb8jPHK6vU4aMscD14kamgYnsKdxqpiR9AFSwzWmDQnXLWPumWAwpbX7STv8pGWMD9uKxEJ9VUaFYwM9iZsZj7ifo8qdvvqqakA4paZrjaM2mXk2iHH3tpJ1gWLVQ4ttkSBqrcVPvoCRwa7WETN2eYWLMYsvdzMJUC5yPitV6TJmYuJv5CWY4Vd4xXe38itZmDAthPupY7fF61ATgmxmMbpJU7bHZdNwC5kN2GS5BC6TKqTfjtE4GvUYUeueGtRpgMJJvJHrika7r389EcRWmnibj3iyxyWRED4Pe7EUYBQdpXZ5Qz9U3hJyEXTjtFh5884rgNZci8trShxHkXR3pny1VgTVnGKZ2FKJKK6iHWyLZtpuGkTybkUJq2nxAPPg5mSeuGEfxhzf8qq6jSSgCPRrLXcHJdn7werTv4jprM6Yc8SxCuUe7TX8bqMeYYaYpKnRrN84k4S4TBtRN8hv2CLbANkVGXMXxt3gi8Y6WXnHqbPigW1qbe2YhVArsHkx8MPyAnU9g1WddhRZSkNdpuvwgKk1A6jDaS3DXpG7eLFmLX2M8Lwn7UUmafwUKC3G18j2yitnjTDZLQUjdaxkQB2nev9DDKgXkxGpBexJpCTHhicsLfnTYsXUZ13b3k3sZyULsRJ4J4M4Fff4q1B6a1dTCBSKA4ftKyArVRTXMJCN7B93X74V6hwAYtuayjtv4evTLhuM2EpR8waQy6L3fDoFAZbdgjCUuuf2spd8eriBBCCentpeDH5B18BcbTwjF93HmBHehBCD59cdZECibfojGheM8nyGnLnGNKp3MUkLtrBQvefWJkK64BUZoy9Hrvp5SxbSgigzkfn9BWVZASNHpUHoY2LwFYqyKCGrE9mzESb2e8iNfGcrxntHU2eVSANCNqQhF4Cyjt1ce82vL5rDyeH2ZJtTrsxWBKKNnMhkGxsQyUWxrHQKp5qpow7sotSN8WxyVKYfyZefhj94ct7pQTmNxwTySesMXhbLfXyC4t56iuZGsSL4Ekhk1tAa3vCeBBRmhfHf8eFBK946YSpARtkn6drbyCBJDqaHsZULx4YyHij3JYiDtREQwHZVZX1cc5btqjYqYKpiu126GHLRHxLxWEgbNZHBc54s6JGLP4dgJUJDdF9uL865bkQ8yvydzhv2DEHUshL5esRBsHWJfgE9hNyZ46FjpUm5A9NtPVYnzSg698gWxRc4MW3yxhQ4t3SmmTxcXWhkE5Az5AuDsb3ZzLRnhZr7vGUwz8p5Nz7wpkdPBL1s7GZKfrJjQAuq1VTy6xXQ5j4aQZvmN1oTNx1bofo3ghDKWYi5JNkiePKu7RuHfw2Ee2uYAd1BEhiTTuRvEm8VGVVNzirhJxW7sV61utZzQHyqbE91MxNqfmHYWZLCics8pbsXyE5iqSvhCm8CTjkknmuiRqNYcUknNnK4bM33cdk9rSpG3v91RWdjC7fAqS8Jh9WipcLTsjBEd89rzg7TShaRnzbQAi5YcEL2oJ16L4knoo2iPv63MCuYPMNjUtCCbZe6uPvVNkRfXCCusXNe5YYms1KarSC7LfcDqAdoXEfu835kYrrrxx9yX1B86GewP1ACBwJcJwkHJKdN7athAkoZAcjjkoQdUxvwTn111GYUgHAkgn3oeFbz6RiWVG5afkd6LpNVoPpzLWBRrhoFXoTPwrj31S2Y1SmnGeC35FuHCrh1Fb2TmH4GaD2DfzKwwvTWTwHPDzffDh2p39C9K7w1XQ19Nx73EXuMRU4gFHXtZkt1ddmpz3kB5Kw91dWVh1QySLHJLSyA3NXxGGCeFRZ5AnpxyqAbVQMjqSZjttWZ9jrnC3J9SMHio9QqcxdSCMdZK4HQjJPMrTb8UvT3BHFPJsDvZZcbyv1RSAA92ixvDWo4JF42CSHuPS1RNpRh5MdT29A37urWPB4Qvc5zbPdhrenf2joKFxm4MXc16bWG7Z1fbjbDVqnHRZX4VUeTdLesYsjfmFm7HGLBH7nMrtuU9iEE7xDmCG4Ycg8PAEftDS9iNKqQgDL5Rb4JaANtJJezAyUupo4k2FNPPJk55gbLc8KT6EPZWXdY7BCtf6AJBRXb3bFYQW7u91ysEzD53ToXD4w4zr2YdPotnqo7fTMxoZDE3Tdcd6meejFLLz7NmYddkhvKX9RovXqmrTNLLyu3M3V1vnJ6TAnEHdKjMgW9qsnyUpBZLorv1eG32ij9ELXd7YscMiXxL7HbXukBZ47BKDknQ7a1JhWMgtvkoFd6jtMrKmLDfSEbrMancxb4aFHBWi8PuwaEWePbCvZsgzD9qjLcRMj1PVMwSzwpgijX88J5reEh6prYjg5BnSnf7eP7trkW1uvbVuCsbbwazMartTRVa3dTqV8ELcLqwrjpEPxWMSM3yBCxETGeqnJBLTjvvC8WUP97H8xpE3w7kNLHxqZs8xX6ADM9DbkCzHfvnzbgt4kZsPe3oTUnRiGnnwHAV5mqUfy2A4CCL8dPYh3B96HZK63YqzgZJuXH2Mmwvthd6pqkF6mi7rvJyjJm3pMjiRyo7VvsKuNR2ShASgECtXNo2N2WL1VkKNfH7usYJfH9UQPtYwngaBUvsaqaJSmqFF35bqm1sXi4JZSjXSp3z9BsD92xZm2gHnhy1EECakPH38WXTcaf6G1kM2ErVW2FDJxkKGV3tejaFaNfxvUdqaQtLUDKZc7qyiGU4bdLLinuDYsfXMTpPiPxJUiJMLVn5kqUcXVtgU6xZ4zu63AmAD3XeDXf67q5TUCXQp1HGpQX3kZqwxeq2psusi1PRWKQJ35QgrE7c3Rco1mgRYvXK4TfLQqRUPyhNu5tRuJDZQxFQVydjuqym97jZj6TkjQvQE86nyntSZPKwgVcLFkKFnFt3mdQk2PMB14jB4H2t99oFX1SoeFUFrVpjitqFp9yWkTe1WCGP9pCtvB7s235rfosio96yLaL3dR8MDVcKfoB9CF2ot4oXQaz5RYxrwrK3rwM2MmFBgd7ZGwsgViASTYh8qbsQjRTCwr5Ln3NvHH3rHPULCG3qSvAeKfeb2LRFFiQUgkrmPHCeT5XFWLidQEwk7FPQ1QeL7Vvn1Q7v2AcJxoS28min2GytYPbQLubqczy9T6CZhLbBGJqzqa7vR3GbR2fMcWtyH1riFtEPssa7JC3UZYRwPoEcRR341ck3py7GTB7ADRhWNSX1Cgkm5y9s5kgjje1pwoMeXcqdzcaFQ4mcrPV1A96qWBzZ9s4TinT6tq6vJLqn63vyJS2oGFMJziEcdNHDtCrJpKoFt5Bw62kTigs7Ck8jAT5zMTgr6zgdwqpCrhftxS8H53hj9LqHDMz3J7WCKH3w1GCrHrwfYDpQXPyawCrV3MZxyajF6i5qHcWumsq1yubM1Y5pvU6cALL7iN6CKK9y135u1h8SfcoRqhJhzqLMLtUHaHLMiHRdXeVBrE9XhpXEE92xKLTyAzEHdWPU4RrpxBVqeQnyScRXKmWKd9WipCsdQMFq6R7d5B2QV4axNyRgHBDGEYU2csx5YqG9ZW37gGw2ov26DKMdi63LuBhtYcbXAXWErxgMyJaU1vyy2w3pvLEeuA3qVBikfpAgkbPEHTLE7Pkc11zLGWw99MtRsVJ6SL4ZneVu8xGt86iQcigtGuQQdV3BdhePMvvhQH7YmPfjVGR4uesxRmdW596nJbutbGK5bLtN7Cao7jagU6RkxWHFGYHqpcKGmVxQD3gUKTiAoxx53u3cRpxUeZeAi4QDYjMSk1Jq8ieDBuFTyEUEaMc45E8YHxm4VUfAto736znUX8Aptooh7V9rVdddqxQhvAtR52z2Ke9CNPEuSPtVQFz6GfPnGzdZwXBeKmp453eMMegqShP9RvhnYupthkbjUcLDZoLKgKbhL9FyG9dXffbSacqkyrNEWBeEmBeRb6VMj6W4F8U62a5Z4HYnbCs6HcUSWjoQZkX7iaG61mowqk3Ky4DMqkPMizg4Rjf2oZLFkTFrsPA3aUtKR5gUepdY6tDqQcGrdtL7CYosPysWoWQxLu2puohtPj8Rf3e3NZkfjrFNQ8BLxTqJ69fXGKgKmxMFKE5DonnPKvMFytzcDGbtoE39z4GeYKboQyY5oZNE8ZWc3MZH9ugQZFTAi5eZ8ZZb5A2nUYYEuvkweph6y96fD9wnH7ifP8a74WoJwFnoZTLYskCZRePEw1cm3Ymx1kXT78rgPMvDgvuhuQP52DmVDFKBfX4X3UYMKGe9zgAfnXmN3eMQmZCWzvo3yJ5TciDAATm1v78zgWZewDvohMpsBGHdmYb5kvzRRHkEb81mbg1zhqAtNQyYuHCrtJ4E2SAHaBTx4qCNRB1Deri5S7tvc2A2taWtLopzfmAT7oevmtoBorXbNkv8uTCxBHfw3n6fq9SJVWM5M1ptTxHNwZBVN5fWShAYxURMf7ahhe1GDFNQwJs8X4nDdRTT7FBXiHzqVxTEiPBAEucLM68WQ3ipASGTEA4qoYSgKSF1Y1LjPCFQbhEVag5eozfp5EjZEsLaWRr43VqP4vLaqasMrM8WK32kuXAtStG8G5ecxxDwHfiPh3TtQB8BUayqjf2zWRRT9d34uJiuQ1ijUiRJW2mKMeDDTW2MSxKJU7V7CF6JhAZWE3hVrSb2JVmAwAaucneEr6RUdP7SHjnxhgXLvacjA9TEouD6TYPCo8ho6kLF7Ef2sZiurvE6yXHgPd5kMfrmrRr3BKvdMySy7BBrRYvQa1Ppi6eEJyoh5ZvRMBAwgNVVFohD2dQUc2P4xfwhjEG1X4juen8nu4TakeijuB8mmUgg5cj2sQ7WTHTiuekEhkppVWAruRdZBSPSkZudYuMvWnQxJD3tVghnQxz3Tt284wkyzzc8vPSSeQTM49KrpUL8bJ6biujc6jb4W7d6FBi5tzrB4Hczz7iJwn7Wzpwd1rSkNVMx8XC7VhYJyusJ6o83ZmVKk1TV9TrNm7eKdncwU4kCx6ZYP1PJKJFympNkG3UMbWjgei4ASyU5YrDAymA6y93tpw7eonKC57A9nJDiHb5tRhsjAUB5aLB4d7iJfownJvhcZJiCLFtzM3yWsXreX1w3fibsTb1BTU7cTK6dDFWSuFz5vZHMRfMSnzxfXNQ8cbBmo4CAAwdf28KEqm7o4zyBfqjZo3zndgmrQAnfRpmX3joqGB7XCjTm1B3U5xox12p9P3uhQxjVbVdbKps8VYdNaSQ258L5uPLLnP6aQjS7eumACbVGRB6aVqLPcmKQURaP8yVMPLzQ3CKuVAz6Q8aQRFMWvbbJ9MSPnbgnQFC2w4G5CCjd3e7bPiuhLcC8LJoSL5MjGpHdsh7kysE6JBsm8psopY1x45Hhf9eHMR8YDC6cTBnEgAs4eKenmN6WjmH79MxbEFyzd5yLoLLTzAT5viazQbC87ky1Efox3HiGCj4BcLCzy8RXBEAzcWccKHTFZCgz5FsPM1mkub2hWdv9ctBHJk4u7W62eZHj9Te2JpHjde3LvPPbPU19SjKMuu7DGnCV7pC8HFhRpQ4y7622mxogu3dBSyNjryn9dkBf5L35hTbDbxF5JjEZFaCJFzNaeGYL16YEZLC6EouckjzBFBJrYGyQsh1RKVXNmHXGbcKz84J8zTD2TSGGrbAZXVBYJuMjUbrd59dvH4NeTSN1bEAw9Zzu2ygQTPvLrLRycrpPw9jw5vnxbDh5QXMnNGkWcsie7QtLoQnyXhfVqK5SVDKShQDk6DxzWAJM6EAAaf9oyg4QkRDSy8RA4NYeJPpVAPy5K3PJyHjFvJmRXJLQJKnU5RkRkSmF1SjhdoKZKSNMTrzCXVLGFCG67KSRcmR9mCeqQ37w1nMHVWW9RzMNBchSL2tX72Ms8AXPuG8zZC4N38pudRciCowkcS1AAz1ofvXZk49AtftYfhPbMJs3agh53VWKGwx2dHrgPvA7XPWoUKFzPi4zEzHZeL59CcXRoL4q38kXGGuAnG8S8gdkB8AXWGWQwkFbhKJLtGcSHXh9Ev13yfB1GP78QYxbiWc7iCYNVQJkUJd4yY8XentoyvL4mAde4T7mbn7KJhd8fQjMug2N148NiWz9zotaF9APx9VfXYLAfwNN8UZnLdcNDG7Tx3Hr1YcSCLLFVJcJQNQWewicBqtRwxNYpu7MyjLUB34jpS8LM4L5xaKEi4617FpegAehsNoPJK4mpiCAP7CotYSxEMFqeBuxCtCfLapGNw9gzAbUfy1MGRsQB5ZkgsbatW4iaXFq54ozeguejVHyVr71pZGqxa6mVXFsZGZBuVA6DEXomdSNwBpgywpRGLStZkHNhYcn4EpVXPCRw39Syx8a36dk3B9AZCv8rAjXgGJ7qNkHeNr6DMrmjPMagwM7RSZThkQGu6ZgnjqfhvtUta7qqzhYt4eu49HDeeiAsq5uRtRVjyucdA31MxNi7tC1DAHT1cMW7mJbxjKT22STt6y84TEQiLr3cUZytPJQLsC8WQyatDWSRutsdrqgAhV5tMztBz9nsTa73mpjaWdxyRrY2RHUDcCRvBies2d8kEXvn9mMoxErkyM2gXEXH4rJ1Jd5jFKW5gnQbgjjNTQRm8jHDmGywB3cHmJ6LUWcqErmWC6sLnfrcQw1t4PBHPEhiAnskFViXPPAHkAbLMksBq8Sf67Uc1mEuVovEESozmViKvBGnuZCvBcgG8h5SuWaU1MPzeFNPMRjEk2qw2NWCCw3LUJRyyF5sjSWSsq5Q6kSAa9Z4VqLPQuDwqe9myw9N
是base58码,解码网站(https://www.jisuan.mobi/pbHzbBHbzHB6uSJx.html),得到

大佬说这是bmp图片,用base64与图片转换网站,转换一下,得到二维码:
扫一扫得到jactf{base58_base64_flag_very_easy}
0x03 小梳子,我永远只爱你一个人
下载文件下来,发现是wifi握手包,而且提示很明显是手机号当字典,直接使用kali生成字典:
root@kali:~# crunch 11 11 -t 138364%%%%% -o /root/桌面/dict.txt
Crunch will now generate the following amount of data: 1200000 bytes
1 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 100000
crunch: 100% completed generating output
具体crunch命令的用法见博客
生成字典之后爆破,
root@kali:~/桌面# aircrack-ng -w /root/桌面/dict.txt dict.cap
Opening dict.cap please wait...
Read 45880 packets.
# BSSID ESSID Encryption
1 0A:69:6C:9D:2D:97 CMCC-WEB None (0.0.0.0)
2 0C:D8:6C:15:5D:AE 喔雄帅 No data - WEP or WPA
3 0C:D8:6C:93:D0:82 FAST_D082 No data - WEP or WPA
4 0E:69:6C:9D:3B:BF None (100.177.92.91)
5 0E:69:6C:9D:47:2B None (100.177.92.112)
6 12:69:6C:9D:2D:97 CMCC-FJ None (0.0.0.0)
7 20:6B:E7:15:DD:5D is you dad No data - WEP or WPA
8 20:6B:E7:78:3B:42 Necros No data - WEP or WPA
9 50:BD:5F:8C:A6:E4 MERCURY_A6E4 WPA (0 handshake)
10 60:EE:5C:46:C8:F0 爱睡觉的夜猫子~ No data - WEP or WPA
11 60:EE:5C:4E:98:76 皮皮王 No data - WEP or WPA
12 B4:0F:3B:D0:7D:90 Tenda_D07D90 WPA (1 handshake)
13 C8:3A:35:D5:24:78 T216私用 No data - WEP or WPA
14 D8:32:14:47:7E:C8 mbd No data - WEP or WPA
15 D8:FE:E3:CF:69:55 D-Link_DIR-613 No data - WEP or WPA
Index number of target network ? 12
Opening dict.cap please wait...
Read 45880 packets.
1 potential targets
Aircrack-ng 1.5.2
[00:00:30] 91408/99999 keys tested (2809.52 k/s)
Time left: 3 seconds 91.41%
KEY FOUND! [ 13836458932 ]
Master Key : 2D D3 02 39 5D 05 89 2C 45 3B B8 A2 53 B0 05 65
30 C8 E7 B8 C2 5D DC A5 80 2A 48 72 4F 3C 38 01
Transient Key : FC CA E5 00 59 A9 B7 53 3F CE 43 5C 7A 1A 89 84
F1 35 FC 52 12 51 63 55 B4 74 E2 E0 2A CB 3F 22
CF 6A EC 11 30 35 52 34 8C 41 A3 E3 AC FE 02 EC
E0 E6 64 C5 16 B1 42 C9 82 65 D8 CA 7D 2F 16 EC
EAPOL HMAC : F9 96 8E 4E AF 7C 57 27 89 3E EC 06 7E FF 91 42
密码就找到了,jactf{13836458932}提交。
0x04 隐写术
题目给的是一个hello.exe,很明显肯定不能打开,到kali里面,用strings命令看一下,发现里面有一个ciphertxt,
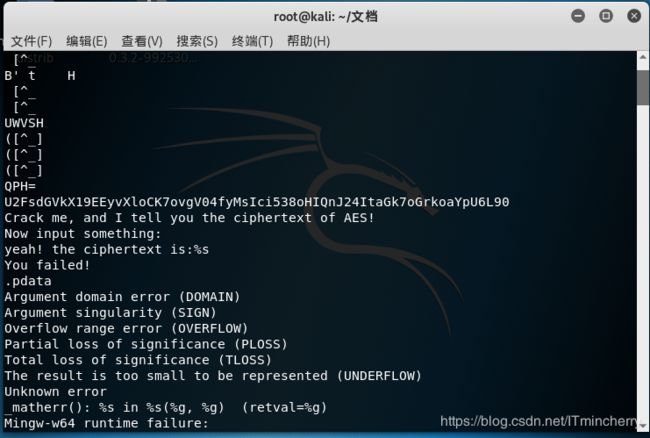
大致看出里面意思是要把
U2FsdGVkX19EEyvXloCK7ovgV04fyMsIci538oHIQnJ24ItaGk7oGrkoaYpU6L90
这一串密文进行AES解密,关键的密码就在ciphertxt里面。
对hello.exe binwalk一下,

可以发现里面有个png文件,用命令
foremost hello.exe
将其分离出来在output文件夹里面,然后将其高度04 89修改为05 89,可以看到

0xA是10,所以密码就是10,解密一下,得到jactf{hey_y0u_are_right}
0x05 真的不是图片
题目给的是一张png图片,binwalk一下,先分析下有没有隐藏文件,发现有个zip:
root@cat:~/ctf# binwalk misc.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 824 x 639, 8-bit/color RGB, non-interlaced
91 0x5B Zlib compressed data, compressed
140598 0x22536 End of Zip archive
root@cat:~/ctf# file misc.png
misc.png: PNG image data, 824 x 639, 8-bit/color RGB, non-interlaced
用010editor分离出png和zip,前八个字节89 50 4E 47 0D 0A 1A 0A为png的文件头,该段格式是固定的,文件尾是42 60 82,后面自然就是zip了。但是因为zip文件头是50 4B 03 04,这里的6A 61 36 36(16进制)对应于ASCII的ja66,修改为50 4B 03 04,另存为zip。打开zip需要密码,猜测就是ja66,发现解压成功。
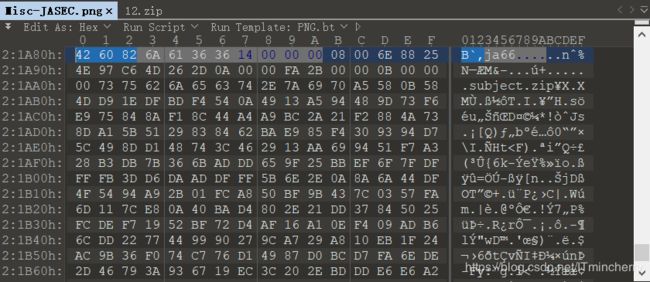
将0-31个txt文件里面的内容综合起来,再base64解码得到flag(下面的脚本直接解决):
jactf{64se64_1s_50_c001}
import base64
flag=''
for i in range(32):
f=open('./subject/'+str(i)+'/'+str(i)+'.txt','r')
flag+=f.read()
print(base64.b64decode(flag))
zip
压缩源文件数据区:
50 4B 03 04:这是头文件标记(0x04034b50)
14 00:解压文件所需 pkware 版本
00 00:全局方式位标记(有无加密)
08 00:压缩方式
5A 7E:最后修改文件时间
F7 46:最后修改文件日期
16 B5 80 14:CRC-32校验(1480B516)
19 00 00 00:压缩后尺寸(25)
17 00 00 00:未压缩尺寸(23)
07 00:文件名长度
00 00:扩展记录长度
6B65792E7478740BCECC750E71ABCE48CDC9C95728CECC2DC849AD284DAD0500
压缩源文件目录区:
50 4B 01 02:目录中文件文件头标记(0x02014b50)
3F 00:压缩使用的 pkware 版本
14 00:解压文件所需 pkware 版本
00 00:全局方式位标记(有无加密,这个更改这里进行伪加密,改为09 00打开就会提示有密码了)
08 00:压缩方式
5A 7E:最后修改文件时间
F7 46:最后修改文件日期
16 B5 80 14:CRC-32校验(1480B516)
19 00 00 00:压缩后尺寸(25)
17 00 00 00:未压缩尺寸(23)
07 00:文件名长度
24 00:扩展字段长度
00 00:文件注释长度
00 00:磁盘开始号
00 00:内部文件属性
20 00 00 00:外部文件属性
00 00 00 00:局部头部偏移量
6B65792E7478740A00200000000000010018006558F04A1CC5D001BDEBDD3B1CC5D001BDEBDD3B1CC5D001
压缩源文件目录结束标志:
50 4B 05 06:目录结束标记
00 00:当前磁盘编号
00 00:目录区开始磁盘编号
01 00:本磁盘上纪录总数
01 00:目录区中纪录总数
59 00 00 00:目录区尺寸大小
3E 00 00 00:目录区对第一张磁盘的偏移量
00 00:ZIP 文件注释长度
这儿可以引出zip伪加密 只要00 0X (X为奇数就是加密)
python库之base64用法
import base64
if __name__ == '__main__':
s = 'plain text'
# base64编码
t = base64.b64encode(s.encode('UTF-8'))
print(t)
# base64解码
t = base64.b64decode(t)
print(t)
# base32编码
t = base64.b32encode(s.encode('UTF-8'))
print(t)
# base32解码
t = base64.b32decode(t)
print(t)
# base16编码
t = base64.b16encode(s.encode('UTF-8'))
print(t)
# base16解码
t = base64.b16decode(t)
print(t)
base64.bxxencode接受一个字节数组bytes用于加密,返回一个bytes存储加密之后的内容。
base64.bxxdecode接受一个存放着密文的bytes,返回一个bytes存放着解密后的内容。
对url进行编码
编码之后的+和/在请求中传输的时候可能会出问题,使用urlsafe_b64encode会自动将+映射为-,/映射为_,这样加密之后传输就安全了。
import base64
if __name__ == '__main__':
s = 'hello, world'
t = base64.urlsafe_b64encode(s.encode('UTF-8'))//base64.b64encode(s.encode('UTF-8'), b'-_')等效
print(t)
t = base64.urlsafe_b64decode(t)
print(t)
使用urlsafe_b64encode相当于是base64.b64encode(s.encode(‘UTF-8’), b’-_’),第二个参数指定了使用哪两个字符来替换掉+和/。