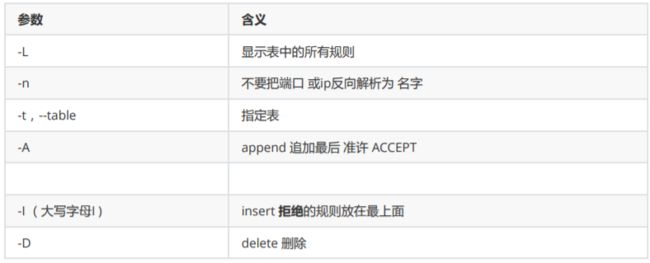
一、防火墙种类及使用说明
硬件:
三层路由: 华为 H3C(华三)
深信服
Juniper
软件:
iptables
firewalld
云防火墙:
阿里云:安全组(默认的是白名单 防火墙默认规则是拒绝)
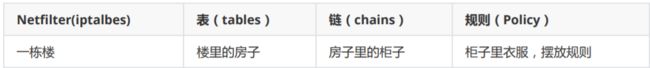
二、必须熟悉的名词
容器: 瓶子 罐子 存放东西
表(table): 存放链的容器
链(chain): 存放规则的容器
规则(policy): 准许或拒绝规则 ACCPT DROP
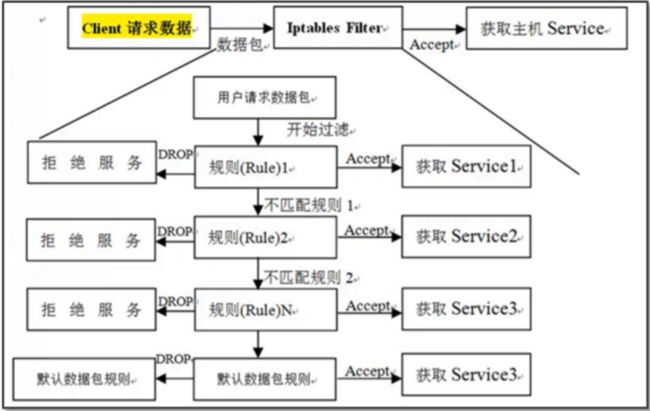
三、 iptables 执行过程※※※※※
工作流程小结:※※※※※
1. 防火墙是层层过滤的,实际是按照配置规则的顺序从上到下,从前到后进行过滤的。
2. 匹配 表示 阻止还是通过,数据包就不再向下匹配新的规则 。
3. 如果规则中没有明确表明是阻止还是通过的,也就是没有匹配规则,向下进行匹配,直到匹配默认规则得到明
确的阻止还是通过。
4. 防火墙的默认规则是所有规则执行完才执行的。
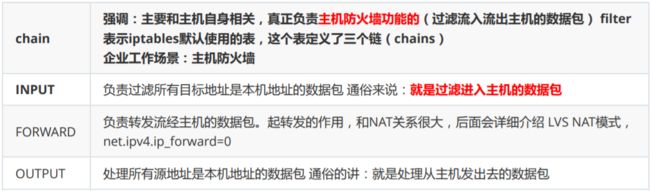
四、表与链※※※※※
4表伍链
表:
filter: (默认,防火墙功能 准许 拒绝)
nat:表 nat功能
内网服务器上外网(共享上网)
端口映射
mangle
raw
filter表:
nat(Network Address Translation)表:
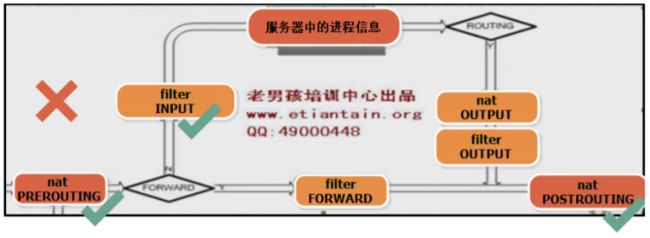
五、4表五链流程
六、环境准备及命令
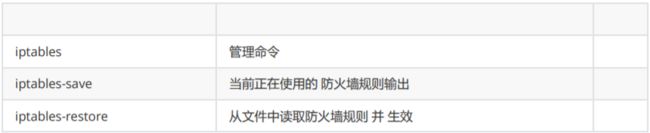
iptables iptables启动或关闭的命令
yum install -y iptables-services
[root@m01 ~]# rpm -ql iptables
/usr/sbin/iptables #iptables管理命令
[root@m01 ~]# rpm -ql iptables-services
/etc/sysconfig/ip6tables
/etc/sysconfig/iptables #防火墙的配置文件
/usr/lib/systemd/system/ip6tables.service
/usr/lib/systemd/system/iptables.service #防火墙服务配置文件(命令)
#防火墙相关模块 加载到内核中
#加载防火墙的内核模块
modprobe ip_tables
modprobe iptable_filter
modprobe iptable_nat
modprobe ip_conntrack
modprobe ip_conntrack_ftp
modprobe ip_nat_ftp
modprobe ipt_state
[root@m01 ~]# lsmod |egrep 'filter|nat|ipt'
nf_nat_ftp 12770 0
nf_conntrack_ftp 18638 1 nf_nat_ftp
iptable_nat 12875 0
nf_nat_ipv4 14115 1 iptable_nat
nf_nat 26787 2 nf_nat_ftp,nf_nat_ipv4
nf_conntrack 133053 6
nf_nat_ftp,nf_nat,xt_state,nf_nat_ipv4,nf_conntrack_ftp,nf_conntrack_ipv4
iptable_filter 12810 0
ip_tables 27126 2 iptable_filter,iptable_nat
libcrc32c 12644 3 xfs,nf_nat,nf_conntrack
[root@m01 ~]# systemctl stop firewalld
[root@m01 ~]# systemctl disable firewalld
[root@m01 ~]# systemctl is-active firewalld.service
unknown
[root@m01 ~]# systemctl is-enabled firewalld.service
disabled
[root@m01 ~]# systemctl start iptables.service
[root@m01 ~]# systemctl enable iptables.service
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to
/usr/lib/systemd/system/iptables.service.
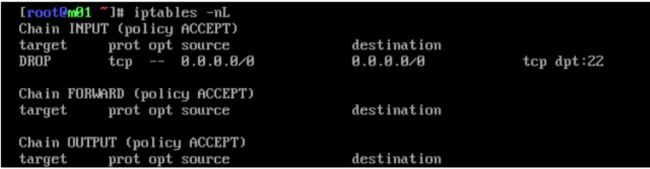
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state
RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-hostprohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-hostprohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
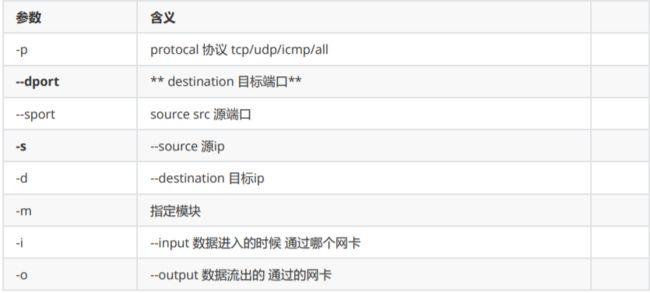
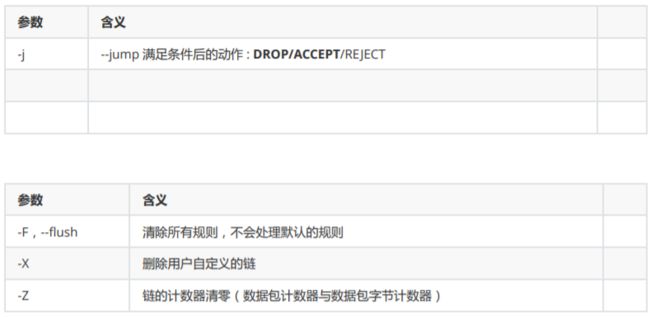
七、iptables命令参数
八、配置filter表规则※※※※※
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -X
[root@m01 ~]# iptables -Z
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
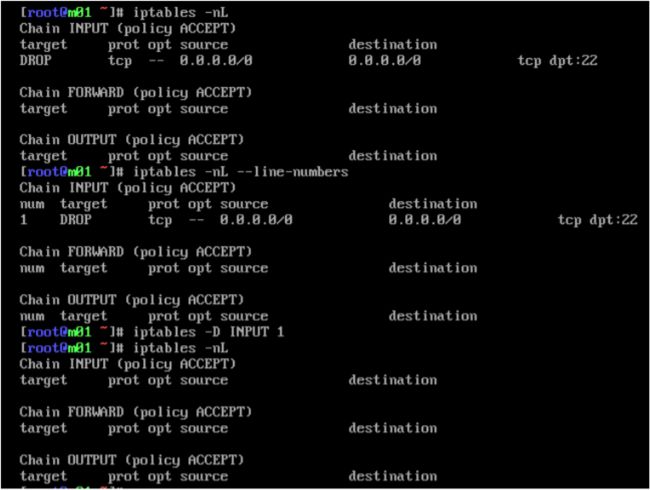
九、 禁止访问22端口
iptables -t filter -A INPUT -p tcp --dport 22 -j DROP
删除 规则 -D
十、禁止ip和端口访问
[root@m01 ~]# iptables -I INPUT -s 10.0.0.7 -p tcp --dport 22 -j DROP
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 10.0.0.7 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
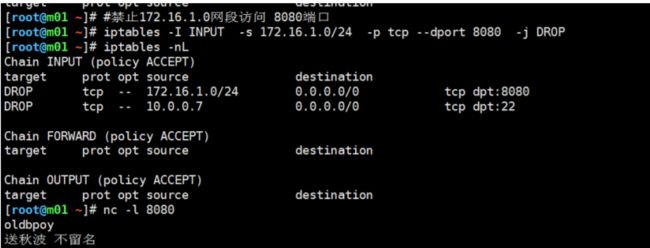
十一、禁止网段连入(禁止10.0.0.0网段访问 8080端口)
nc ncat netcat
nc -l
telnet
[root@m01 ~]# yum provides nc
已加载插件:fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
2:nmap-ncat-6.40-16.el7.x86_64 : Nmap's Netcat replacement
源 :base
匹配来源:
提供 :nc
2:nmap-ncat-6.40-16.el7.x86_64 : Nmap's Netcat replacement
源 :@base
匹配来源:
提供 :nc
[root@m01 ~]#
[root@m01 ~]#
[root@m01 ~]#
[root@m01 ~]#
[root@m01 ~]#
[root@m01 ~]# rpm -qf `which nc`
nmap-ncat-6.40-16.el7.x86_64
#nc使用指南:
## 实现telnet检查端口是否开启
nc 10.0.0.61 22
## 聊天 送秋波
[root@m01 ~]# nc -l 8080
送秋波
送香菜
[root@m01 ~]# ss -lntup |grep 8080
tcp LISTEN 0 10 *:8080 *:*
users:(("nc",pid=10661,fd=4))
tcp LISTEN 0 10 :::8080 :::*
users:(("nc",pid=10661,fd=3))
[root@web01 ~]# telnet 10.0.0.61 8080 #连接到 8080端口
Trying 10.0.0.61...
Connected to 10.0.0.61.
Escape character is '^]'. #按ctrl + 】 退出
送秋波
送香菜
^C^C^C^C^C^C^]
telnet> Connection closed.
## 通过nc传输文件
[root@m01 ~]# nc -l 8080 >/tmp/hosts.txt
[root@web01 ~]# cat /etc/hosts |nc 10.0.0.61 8080
[root@m01 ~]# cat /tmp/hosts.txt
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
172.16.1.61 m01
十二、禁止172.16.1.0网段访问 8080端口
iptables -I INPUT -s 10.0.0.0/24 -p tcp --dport 8080 -j DROP
十三、只允许指定网段连入(允许10.0.0.0网段)
location /status {
stub_status;
allow 10.0.0.0/24;
deny all;
}
iptables -I INPUT ! -s 10.0.0.0/24 -j DROP
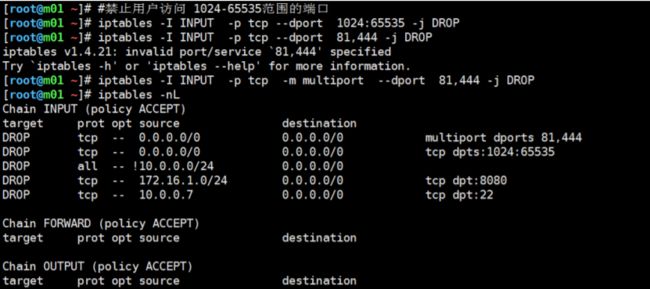
十四、 指定多个端口
[root@m01 ~]# iptables -I INPUT -p tcp -m multiport ! --dport 80,443 -j DROP
[root@m01 ~]# iptables -I INPUT -p tcp --dport 1024:65535 -j DROP
[root@m01 ~]# #禁止用户访问 1024-65535范围的端口
[root@m01 ~]# iptables -I INPUT -p tcp --dport 1024:65535 -j DROP
[root@m01 ~]# iptables -I INPUT -p tcp --dport 81,444 -j DROP
iptables v1.4.21: invalid port/service `81,444' specified
Try `iptables -h' or 'iptables --help' for more information.
[root@m01 ~]# iptables -I INPUT -p tcp -m multiport --dport 81,444 -j DROP
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 81,444
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:1024:65535
DROP all -- !10.0.0.0/24 0.0.0.0/0
DROP tcp -- 172.16.1.0/24 0.0.0.0/0 tcp dpt:8080
DROP tcp -- 10.0.0.7 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
十五、匹配ICMP 类型
ping
tracert(windows) traceroute (linux) 路由追踪
ICMP(Internet Control Message Protocol)Internet控制报文协议
通过内核参数 控制 禁止被ping
[root@m01 ~]# cat /etc/sysctl.conf
#/proc/sys/net/ipv4/icmp_echo_ignore_all
net.ipv4.icmp_echo_ignore_all = 1
[root@m01 ~]# sysctl -p
net.ipv4.icmp_echo_ignore_all = 1
通过防火墙规则 控制是否可以ping
[root@m01 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP
###iptables -I INPUT -p icmp --icmp-type any -j DROP
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
十六、 匹配网络状态(TCP/IP连接状态)
-m state --state
NEW:已经或将启动新的连接
ESTABLISHED:已建立的连接
RELATED:正在启动的新连接
INVALID:非法或无法识别的
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
十七、限制并发及速率
iptables -I INPUT -p icmp --icmp-type 8 -j ACCEPT
iptables -I INPUT -p icmp --icmp-type 8 -m limit --limit 6/min --limit-burst 5 -j
ACCEPT
-m limit --limit n/{second/minute/hour}:
解释:指定时间内的请求速率”n”为速率,后面为时间分别为:秒 分 时
--limit-burst [n]
解释:在同一时间内允许通过的请求”n”为数字,不指定默认为5
十八、防火墙规则的保存与恢复
[root@m01 ~]# cat /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
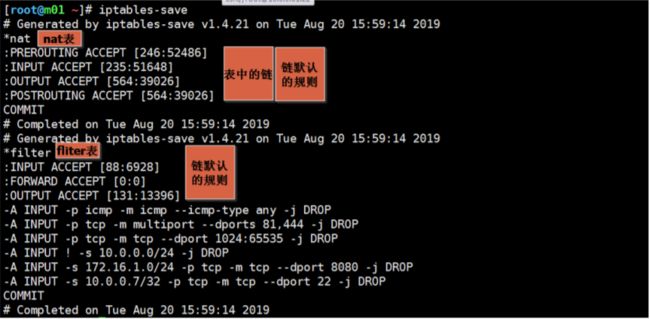
[root@m01 ~]# iptables-save > /etc/sysconfig/iptables
[root@m01 ~]#
[root@m01 ~]# cat /etc/sysconfig/iptables
# Generated by iptables-save v1.4.21 on Wed Jul 24 23:28:23 2019
*filter
:INPUT ACCEPT [341:28194]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [271:30712]
-A INPUT -p icmp -m icmp --icmp-type 8 -j DROP
COMMIT
# Completed on Wed Jul 24 23:28:23 2019
[root@m01 ~]# #恢复
[root@m01 ~]# #重启防火墙
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@m01 ~]#
[root@m01 ~]# iptables-restore 十九、实际生产用法
默认是拒绝 去电影院
逛公园
1. ssh可以连接进来
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -X
[root@m01 ~]# iptables -Z
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@m01 ~]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
2.设置允许本机lo**通讯规则**
# 允许本机回环lo接口数据流量流出与流入
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
3. 配置默认规则及 放行 80 443端口
[root@m01 ~]# iptables -P INPUT DROP
[root@m01 ~]# iptables -P FORWARD DROP
[root@m01 ~]# iptables -P OUTPUT ACCEPT
[root@m01 ~]# iptables -A INPUT -m multiport -p tcp --dport 443,80 -j ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
Chain FORWARD (policy DROP)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables -A INPUT -s 10.0.0.0/24 -j ACCEPT
[root@m01 ~]# iptables -A INPUT -s 172.16.1.0/24 -j ACCEPT
[root@m01 ~]#
[root@m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
ACCEPT all -- 172.16.1.0/24 0.0.0.0/0
Chain FORWARD (policy DROP)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables-save
# Generated by iptables-save v1.4.21 on Wed Jul 24 23:42:00 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [24:3008]
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m multiport --dports 443,80 -j ACCEPT
-A INPUT -s 10.0.0.0/24 -j ACCEPT
-A INPUT -s 172.16.1.0/24 -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
COMMIT
# Completed on Wed Jul 24 23:42:00 2019
[root@m01 ~]# iptables-save
# Generated by iptables-save v1.4.21 on Tue Aug 20 16:31:56 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [52:5728]
-A INPUT -p tcp -m multiport --dports 80,443 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -s 10.0.0.0/24 -j ACCEPT
-A INPUT -s 172.16.1.0/24 -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
COMMIT
# Completed on Tue Aug 20 16:31:56 2019
# Generated by iptables-save v1.4.21 on Tue Aug 20 16:31:56 2019
*nat
:PREROUTING ACCEPT [11:1542]
:INPUT ACCEPT [9:1220]
:OUTPUT ACCEPT [10:670]
:POSTROUTING ACCEPT [10:670]
COMMIT
# Completed on Tue Aug 20 16:31:56 2019
二十、nat表
[root@m01 ~]# iptables -P INPUT ACCEPT
[root@m01 ~]# iptables -P FORWARD ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
ACCEPT all -- 172.16.1.0/24 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
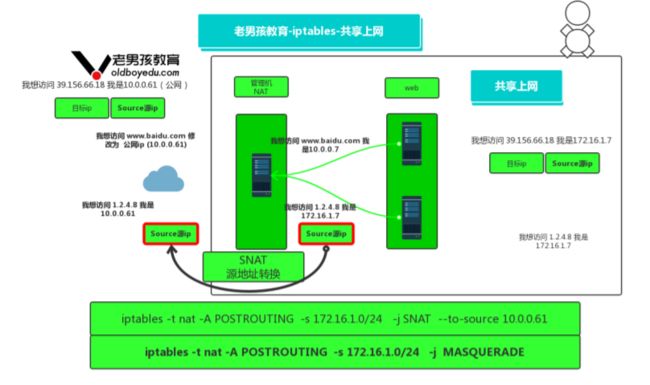
二十一、实现共享上网※※※※※
物理服务器/虚拟机
云服务器 :
- 防火墙配置
[root@m01 ~]# iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT --to-source
10.0.0.61
[root@m01 ~]# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf
[root@m01 ~]# sysctl -p
net.ipv4.icmp_echo_ignore_all = 0
net.ipv4.ip_forward = 1
注意事项: 公网ip不固定: iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j MASQUERADE
- web配置
[root@web01 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth0
TYPE=Ethernet
BOOTPROTO=none
NAME=eth0
DEVICE=eth0
ONBOOT=no
IPADDR=10.0.0.7
PREFIX=24
GATEWAY=10.0.0.254
DNS1=223.5.5.5
GATEWAY=10.0.0.254
[root@web01 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth1
TYPE=Ethernet
IPADDR=172.16.1.7
PREFIX=24
NAME=eth1
DEVICE=eth1
ONBOOT=yes
GATEWAY=172.16.1.61
DNS1=1.2.4.8
[root@web01 ~]# systemctl restart network
[root@m01 ~]# ssh 172.16.1.7
Last login: Wed Jul 24 23:06:58 2019 from 10.0.0.1
[root@web01 ~]# ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default
qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: mtu 1500 qdisc pfifo_fast state DOWN group default
qlen 1000
link/ether 00:0c:29:b2:e3:7e brd ff:ff:ff:ff:ff:ff
3: eth1: mtu 1500 qdisc pfifo_fast state UP group
default qlen 1000
link/ether 00:0c:29:b2:e3:88 brd ff:ff:ff:ff:ff:ff
inet 172.16.1.7/24 brd 172.16.1.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb2:e388/64 scope link
valid_lft forever preferred_lft forever
[root@web01 ~]# ping baidu.com
PING baidu.com (220.181.38.148) 56(84) bytes of data.
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=1 ttl=127 time=8.90 ms
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=2 ttl=127 time=7.52 ms
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=3 ttl=127 time=9.28 ms
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=4 ttl=127 time=9.36 ms
^C
--- baidu.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 7.528/8.769/9.364/0.746 ms
[root@web01 ~]# ping 1.2.4.8
PING 1.2.4.8 (1.2.4.8) 56(84) bytes of data.
64 bytes from 1.2.4.8: icmp_seq=1 ttl=127 time=76.4 ms
64 bytes from 1.2.4.8: icmp_seq=2 ttl=127 time=76.8 ms
^C
--- 1.2.4.8 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 76.440/76.637/76.834/0.197 ms
- 完成后 在web01 发出 ip r和ping 外网ip的结果
[root@web01 ~]# ip r
default via 172.16.1.61 dev eth1
169.254.0.0/16 dev eth1 scope link metric 1003
172.16.1.0/24 dev eth1 proto kernel scope link src 172.16.1.7
[root@web01 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 172.16.1.61 0.0.0.0 UG 0 0 0 eth1
169.254.0.0 0.0.0.0 255.255.0.0 U 1003 0 0 eth1
172.16.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
[root@web01 ~]# ping baidu.com
PING baidu.com (39.156.69.79) 56(84) bytes of data.
64 bytes from 39.156.69.79 (39.156.69.79): icmp_seq=1 ttl=127 time=21.7 ms
64 bytes from 39.156.69.79 (39.156.69.79): icmp_seq=2 ttl=127 time=32.6 ms
^C
--- baidu.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 21.781/27.214/32.647/5.433 ms
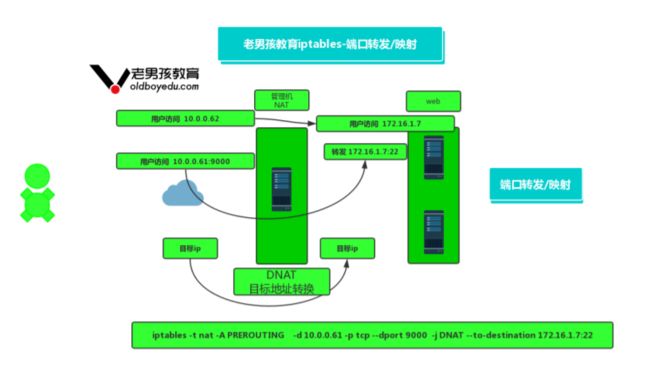
二十二、 实现端口转发※※※※※
[root@m01 ~]# iptables -t nat -A PREROUTING -d 10.0.0.61 -p tcp --dport 9000 -j
DNAT --to-destination 172.16.1.7:22
[root@m01 ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 10.0.0.61 tcp dpt:9000
to:172.16.1.7:22
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 172.16.1.0/24 0.0.0.0/0 to:10.0.0.61
测试与检查:
本地shell中
[d:\~]$ ssh [email protected] 9000
二十三、实现ip映射
ip a add 10.0.0.62/24 dev eth0 label eth0:0
[root@m01 ~]# iptables -t nat -A PREROUTING -d 10.0.0.62 -j DNAT --to-destination
172.16.1.7
[root@m01 ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 10.0.0.61 tcp dpt:9000
to:172.16.1.7:22
DNAT all -- 0.0.0.0/0 10.0.0.62 to:172.16.1.7
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 172.16.1.0/24 0.0.0.0/0 to:10.0.0.61
二十四、补充资料:
面试题:让1个服务开机自启动 有什么方法 https://www.jianshu.com/p/fc26d73fe050
【不会别做运维了】CentOS 6 VS 7 区别 https://www.jianshu.com/p/d6d9a49e95c9
二十五、总结
4表五链 及 执行过程
防火墙执行过程
案例:
企业防火墙实现:屏蔽
nat规则
共享上网
端口映射/转发
练习题:
【面试题】老男孩教育防火墙企业面试题iptalbes
https://www.jianshu.com/p/19422676b854
二十六、面试题
5、请写出查看iptables当前所有规则的命令。
iptables-save
iptables -nL
iptables -nL -t nat
6、禁止来自10.0.0.188 ip地址访问80端口的请求
iptables -I INPUT -s 10.0.0.188 -p tcp --dport 80 -j DROP
7、如何使在命令行执行的iptables规则永久生效?
cp /etc/sysconfig/iptables{,.bak.$(date +%F)}
iptables-save >/etc/sysconfig/iptables
/etc/sysconfig/iptables
8、实现把访问10.0.0.3:80的请求转到172.16.1.17:80
iptables -t nat -A PREROUTING -d 10.0.0.3 -p tcp --dport 80 -j DNAT --todestination 172.16.1.17:80
9、实现172.16.1.0/24段所有主机通过124.32.54.26外网IP共享上网。
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT --to-source
123.32.54.26
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT MASQUERADE
防火墙 笔试题 www.jianshu.com/p/2180face8381
封掉/通过:ip或端口
下次:nat表
共享上网
端口转发
二十七、lnmt环境
java简介
JAVA: LNMT(tomcat)
tomcat
resin
weblogic( 配合oracle)
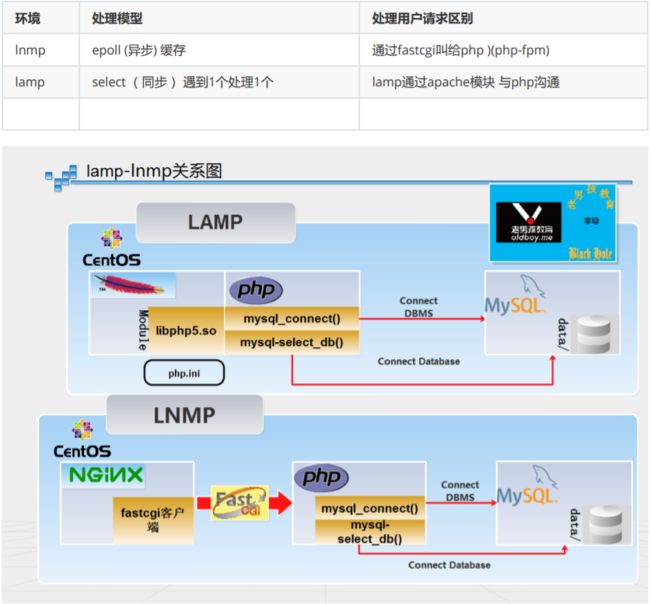
PHP: LNMP LAMP
tomcat必备姿势
tomcat apache-tomcat
jvm java virtual machine java虚拟机
代码的可移植性 1份代码 处处使用
占用内存
jdk java development kit java开发环境
java命令
jvm
jdk
Oracle jdk
openjdk
二十八、 tomcat环境搭建
web01 eth0
1. jdk
#man bash
#PATH 存放命令的路径
## ls
cat >>/etc/profile <<'EOF'
export JAVA_HOME=/application/jdk
export PATH=$JAVA_HOME/bin:$JAVA_HOME/jre/bin:$PATH
export CLASSPATH=.:$JAVA_HOME/lib:$JAVA_HOME/jre/lib:$JAVA_HOME/lib/tools.jar
EOF
. /etc/profile
[root@web01 ~]# mkdir -p /application
[root@web01 application]# tar xf jdk-8u60-linux-x64.tar.gz -C /application/
[root@web01 application]# ln -s /application/jdk1.8.0_60/ /application/jdk
[root@web01 application]# java -version
java version "1.8.0_60"
Java(TM) SE Runtime Environment (build 1.8.0_60-b27)
Java HotSpot(TM) 64-Bit Server VM (build 25.60-b23, mixed mode)
2. tomcat
[root@web01 application]# tar xf apache-tomcat-8.0.27.tar.gz
[root@web01 application]# ll
总用量 185908
drwxr-xr-x 9 root root 160 8月 20 19:16 apache-tomcat-8.0.27
-rw-r--r-- 1 root root 9128610 10月 5 2015 apache-tomcat-8.0.27.tar.gz
lrwxrwxrwx 1 root root 25 8月 20 19:11 jdk -> /application/jdk1.8.0_60/
drwxr-xr-x 8 10 143 255 8月 5 2015 jdk1.8.0_60
-rw-r--r-- 1 root root 181238643 10月 5 2015 jdk-8u60-linux-x64.tar.gz
[root@web01 application]# ln -s /application/apache-tomcat-8.0.27
/application/tomcat
[root@web01 application]# ll /application/
总用量 185908
drwxr-xr-x 9 root root 160 8月 20 19:16 apache-tomcat-8.0.27
-rw-r--r-- 1 root root 9128610 10月 5 2015 apache-tomcat-8.0.27.tar.gz
lrwxrwxrwx 1 root root 25 8月 20 19:11 jdk -> /application/jdk1.8.0_60/
drwxr-xr-x 8 10 143 255 8月 5 2015 jdk1.8.0_60
-rw-r--r-- 1 root root 181238643 10月 5 2015 jdk-8u60-linux-x64.tar.gz
lrwxrwxrwx 1 root root 33 8月 20 19:16 tomcat -> /application/apache-tomcat8.0.27
[root@web01 application]# mv *.tar.gz /tmp/
[root@web01 application]# ll
总用量 0
drwxr-xr-x 9 root root 160 8月 20 19:16 apache-tomcat-8.0.27
lrwxrwxrwx 1 root root 25 8月 20 19:11 jdk -> /application/jdk1.8.0_60/
drwxr-xr-x 8 10 143 255 8月 5 2015 jdk1.8.0_60
lrwxrwxrwx 1 root root 33 8月 20 19:16 tomcat -> /application/apache-tomcat-8.0.27
[root@web01 application]# /application/tomcat/bin/version.sh
Using CATALINA_BASE: /application/tomcat
Using CATALINA_HOME: /application/tomcat
Using CATALINA_TMPDIR: /application/tomcat/temp
Using JRE_HOME: /application/jdk
Using CLASSPATH:
/application/tomcat/bin/bootstrap.jar:/application/tomcat/bin/tomcat-juli.jar
Server version: Apache Tomcat/8.0.27
Server built: Sep 28 2015 08:17:25 UTC
Server number: 8.0.27.0
OS Name: Linux
OS Version: 3.10.0-957.5.1.el7.x86_64
Architecture: amd64
JVM Version: 1.8.0_60-b27
JVM Vendor: Oracle Corporation
[root@web01 application]# #9.x 8.5 8.0
3. 启动与管理
startup.sh 启动
shutdown.sh 关闭
catalina.sh 核心脚本
PRG="$0"
PRGDIR=`dirname "$PRG"` #dirname 路径
#[root@web01 ~]# dirname /etc/sysconfig/iptables-config
#/etc/sysconfig
#[root@web01 ~]# basename /etc/sysconfig/iptables-config
#iptables-config
EXECUTABLE=catalina.sh
exec "$PRGDIR"/"$EXECUTABLE" start "$@"
#/application/tomcat/bin/catalina.sh start
[root@web01 bin]# /application/tomcat/bin/startup.sh
Using CATALINA_BASE: /application/tomcat
Using CATALINA_HOME: /application/tomcat
Using CATALINA_TMPDIR: /application/tomcat/temp
Using JRE_HOME: /application/jdk
Using CLASSPATH:
/application/tomcat/bin/bootstrap.jar:/application/tomcat/bin/tomcat-juli.jar
Tomcat started.
[root@web01 bin]# ss -lntup |grep tomcat
[root@web01 bin]# ss -lntup |grep java
tcp LISTEN 0 100 :::8009 :::*
users:(("java",pid=12137,fd=51))
tcp LISTEN 0 100 :::8080 :::*
users:(("java",pid=12137,fd=46))
tcp LISTEN 0 1 ::ffff:127.0.0.1:8005 :::*
users:(("java",pid=12137,fd=68))
[root@web01 bin]# ps -ef |grep java
root 12137 1 5 19:26 pts/2 00:00:03 /application/jdk/bin/java -
Djava.util.logging.config.file=/application/tomcat/conf/logging.properties -
Djava.util.logging.manager=org.apache.juli.ClassLoaderLogManager -
Djava.endorsed.dirs=/application/tomcat/endorsed -classpath
/application/tomcat/bin/bootstrap.jar:/application/tomcat/bin/tomcat-juli.jar -
Dcatalina.base=/application/tomcat -Dcatalina.home=/application/tomcat -
Djava.io.tmpdir=/application/tomcat/temp org.apache.catalina.startup.Bootstrap start
root 12182 11916 0 19:27 pts/2 00:00:00 grep --color=auto java
/application/jdk/bin/java
-Djava.util.logging.config.file=/application/tomcat/conf/logging.properties
-Djava.util.logging.manager=org.apache.juli.ClassLoaderLogManager
-Djava.endorsed.dirs=/application/tomcat/endorsed
-classpath /application/tomcat/bin/bootstrap.jar:/application/tomcat/bin/tomcat
-juli.jar
-Dcatalina.base=/application/tomcat
-Dcatalina.home=/application/tomcat
-Djava.io.tmpdir=/application/tomcat/temp org.apache.catalina.startup.Bootstrap
start
二十九、测试