相关链接:
关于ATS参数:http://www.cnblogs.com/dahe007/p/6093874.html
ATS介绍官方文档:https://developer.apple.com/library/content/documentation/General/Reference/InfoPlistKeyReference/Articles/CocoaKeys.html
ATS审核问题:https://yq.aliyun.com/articles/62563
1.拿到后台人员给到的域名后 首先查看能否通过ATS验证
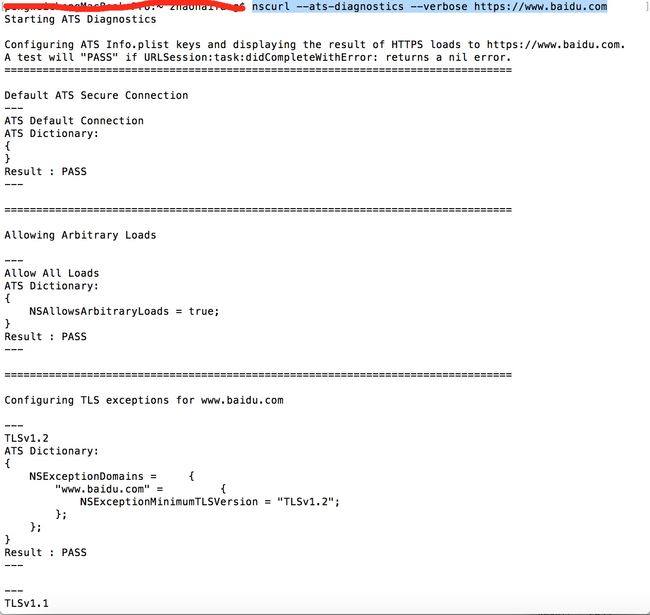
-》1.打开终端 输入命令 nscurl --ats-diagnostics --verbose 你的域名
例1:nscurl --ats-diagnostics --verbose https://www.baidu.com 查看百度的 部分打印结果
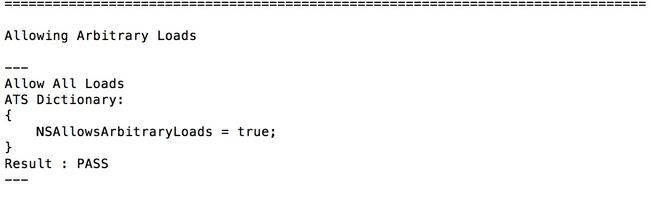
仔细观察 就是系统在做一系列测试 看在不同的ATS参数下 结果是什么 pass or fail
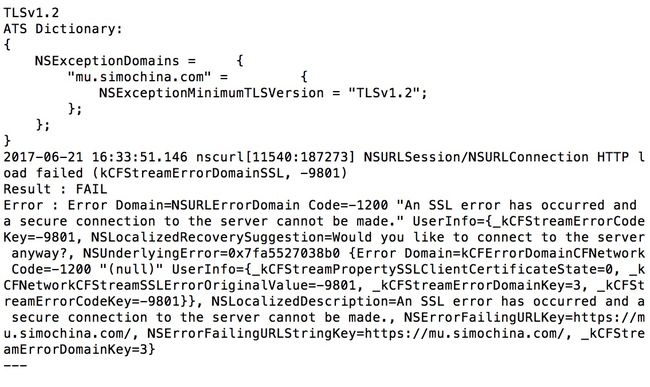
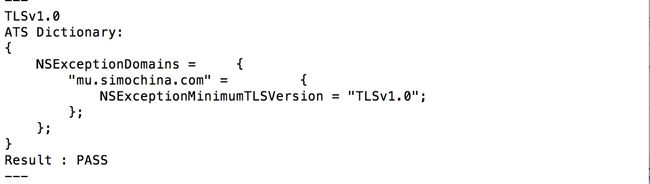
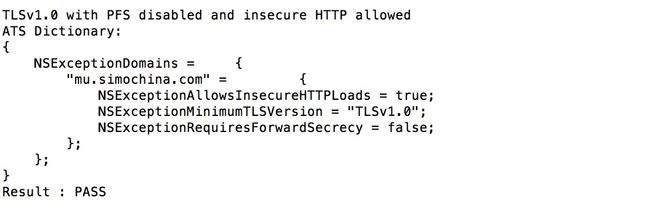
例2:nscurl --ats-diagnostics --verbose https://mu.simochina.com
2.拿到后台人员给到的 .crt证书 转成 .cer证书
->1. 终端命令
cd 到.crt证书 所在文件夹
然后输入命令 openssl x509 -in 后台给你的证书名.crt -out 转化的证书名.cer -outform der
例:
cd /Users/myfile/Desktop/certificate
openssl x509 -in certificate.crt -out certificate.cer -outform der
->2.双击后台给到的.crt证书 加入钥匙串 然后从钥匙串导出时选择.cer
->3.根据域名自己生成一个单向验证的证书 终端命令
openssl s_client -connect https://你的域名:443 /dev/null | openssl x509 -outform DER > 证书名.cer
例:openssl s_client -connect https://baidu.com:443 /dev/null | openssl x509 -outform DER > myCertificate.cer
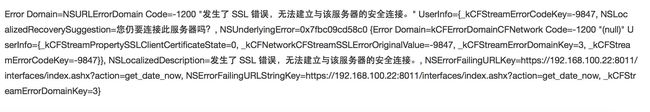
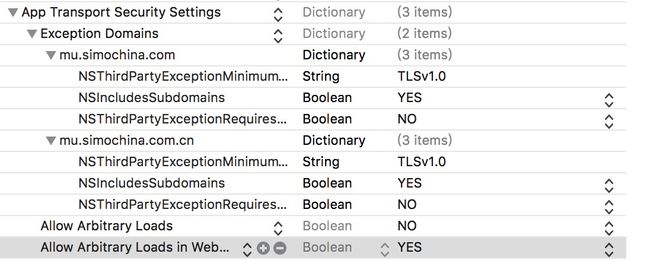
3.开始的错误是在AFN中报出来的错误 加入的证书无法进行验证 加入验证 但是不执行回调 后通过修改ATS参数获得解决
关于AFN中https的验证,如下
//https相关设置
AFHTTPSessionManager *manager = [AFHTTPSessionManager manager];
//安全策略
[manager setSecurityPolicy:[self customSecurityPolicy]];
//证书校验
[self checkCredential:manager];
//安全策略
+ (AFSecurityPolicy*)customSecurityPolicy {
AFSecurityPolicy *securityPolicy = [AFSecurityPolicy policyWithPinningMode:AFSSLPinningModeCertificate];
//获取证书路径
NSString * cerPath = [[NSBundle mainBundle] pathForResource:@"myCertificate" ofType:@"cer"];
NSData *certData = [NSData dataWithContentsOfFile:cerPath];
NSSet *dataSet = [NSSet setWithArray:@[certData]];
[securityPolicy setAllowInvalidCertificates:YES];//是否允许使用自签名证书
[securityPolicy setPinnedCertificates:dataSet];//设置去匹配服务端证书验证的证书
[securityPolicy setValidatesDomainName:NO];//是否需要验证域名,默认YES
return securityPolicy;
}
//校验证书
+ (void)checkCredential:(AFURLSessionManager *)manager
{
[manager setSessionDidBecomeInvalidBlock:^(NSURLSession * _Nonnull session, NSError * _Nonnull error) {
NSLog(@"policy-%@",error);
}];
__weak typeof(manager)weakManager = manager;
[manager setSessionDidReceiveAuthenticationChallengeBlock:^NSURLSessionAuthChallengeDisposition(NSURLSession*session, NSURLAuthenticationChallenge *challenge, NSURLCredential *__autoreleasing*_credential) {
NSURLSessionAuthChallengeDisposition disposition = NSURLSessionAuthChallengePerformDefaultHandling;
__autoreleasing NSURLCredential *credential =nil;
NSLog(@"pwc -- authenticationMethod= %@",challenge.protectionSpace.authenticationMethod);
//判断服务器要求客户端的接收认证挑战方式,如果是NSURLAuthenticationMethodServerTrust则表示去检验服务端证书是否合法,NSURLAuthenticationMethodClientCertificate则表示需要将客户端证书发送到服务端进行检验
if([challenge.protectionSpace.authenticationMethod isEqualToString:NSURLAuthenticationMethodServerTrust]) {
// 基于客户端的安全策略来决定是否信任该服务器,不信任的话,也就没必要响应挑战
if([weakManager.securityPolicy evaluateServerTrust:challenge.protectionSpace.serverTrust forDomain:challenge.protectionSpace.host]) {
// 创建挑战证书(注:挑战方式为UseCredential和PerformDefaultHandling都需要新建挑战证书)
credential = [NSURLCredential credentialForTrust:challenge.protectionSpace.serverTrust];
// 确定挑战的方式
if (credential) {
//证书挑战 设计policy,none,则跑到这里
disposition = NSURLSessionAuthChallengeUseCredential;
} else {
disposition = NSURLSessionAuthChallengePerformDefaultHandling;
}
} else {
disposition = NSURLSessionAuthChallengeCancelAuthenticationChallenge;
}
} else { //只有双向认证才会走这里
// client authentication
SecIdentityRef identity = NULL;
SecTrustRef trust = NULL;
//客户端证书路径
NSString *p12 = [[NSBundle mainBundle] pathForResource:@"client" ofType:@"p12"];
NSFileManager *fileManager =[NSFileManager defaultManager];
if(![fileManager fileExistsAtPath:p12])
{
NSLog(@"client.p12:not exist");
}
else
{
//生成证书二进制文件
NSData *PKCS12Data = [NSData dataWithContentsOfFile:p12];
if ([self extractIdentity:&identity andTrust:&trust fromPKCS12Data:PKCS12Data])
{
SecCertificateRef certificate = NULL;
SecIdentityCopyCertificate(identity, &certificate);
const void*certs[] = {certificate};
CFArrayRef certArray = CFArrayCreate(kCFAllocatorDefault, certs,1,NULL);
credential = [NSURLCredential credentialWithIdentity:identity certificates:(__bridge NSArray*)certArray persistence:NSURLCredentialPersistencePermanent];
// credential = [NSURLCredential credentialWithIdentity:identity certificates:nil persistence:NSURLCredentialPersistenceNone];
disposition =NSURLSessionAuthChallengeUseCredential;
if (certArray) {//释放资源
CFRelease(certArray);
}
}
}
}
*_credential = credential;
return disposition;
}];
}
//读取p12文件中的密码
+ (BOOL)extractIdentity:(SecIdentityRef*)outIdentity andTrust:(SecTrustRef *)outTrust fromPKCS12Data:(NSData *)inPKCS12Data {
OSStatus securityError = errSecSuccess;
//client certificate password
NSDictionary *optionsDictionary = [NSDictionary dictionaryWithObject:@"123456" forKey:(__bridge id)kSecImportExportPassphrase];
CFArrayRef items = CFArrayCreate(NULL, 0, 0, NULL);
securityError = SecPKCS12Import((__bridge CFDataRef)inPKCS12Data,(__bridge CFDictionaryRef)optionsDictionary,&items);
if(securityError == 0) {
CFDictionaryRef myIdentityAndTrust =CFArrayGetValueAtIndex(items,0);
const void*tempIdentity =NULL;
tempIdentity= CFDictionaryGetValue (myIdentityAndTrust,kSecImportItemIdentity);
*outIdentity = (SecIdentityRef)tempIdentity;
const void*tempTrust =NULL;
tempTrust = CFDictionaryGetValue(myIdentityAndTrust,kSecImportItemTrust);
*outTrust = (SecTrustRef)tempTrust;
} else {
NSLog(@"Failedwith error code %d",(int)securityError);
return NO;
}
return YES;
}
相关链接 资料参考:
http://www.jianshu.com/p/0109f45395e3
http://www.jianshu.com/p/a84237b07611
http://www.jianshu.com/p/36ddc5b009a7
http://www.jianshu.com/p/1f426385ba53