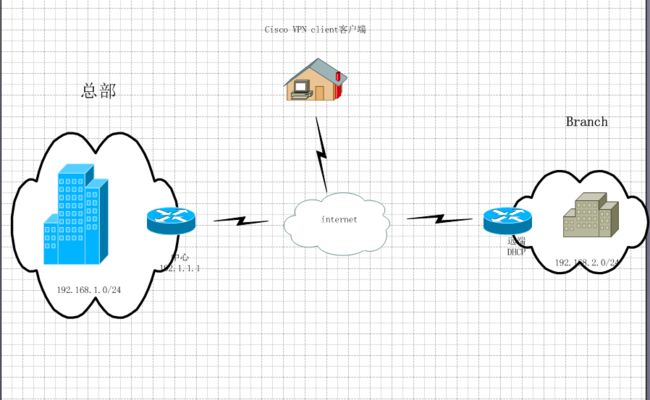
在实际工程中我们经常做***来实现远程访问的安全,假如现在一公司拥有一台路由器来实现L2L***,保证分部连接总部的数据安全。但随着业务的扩大,一些出差员工同样要访问总部内部的数据,来保证日常工作的进行,该公司已经有了一台高性能的路由,在不增加支出的情况下怎样保证远程访问的安全,难道再去买一台***3000,no no我们可以在一台路由器上做双重策略来达到我们的目的。我们来看案例
要求:
1.实现分部到总部的安全访问 192.168.2.0到192.168.1.0的安全访问
2.实现远程访问公司内部网络
3.在总部边界路由器做安全策略,保护总部内部网络安全
4.实现nat转换
总部:
interface Loopback0
ip address 192.168.1.1 255.255.255.255
ip nat inside
ip virtual-reassembly
interface Loopback1
ip address 1.1.1.1 255.255.255.255
interface Ethernet0/0
ip address 192.1.1.1 255.255.255.0
ip nat outside
username cisco password 0 cisco
username liang password 0 liang
crypto keyring l2l
pre-shared-key address 0.0.0.0 0.0.0.0 key cisco
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
crypto isakmp client configuration group remote
key cisco
dns 202.68.222.222
wins 192.168.1.100
domain liang.com
pool ippool
crypto isakmp profile remote
match identity group romote
match identity group remote
client authentication list remote
isakmp authorization list remote
client configuration address respond
crypto isakmp profile l2l
keyring l2l
match identity address 0.0.0.0
keepalive 20 retry 3
crypto ipsec transform-set liang esp-des esp-md5-hmac
crypto dynamic-map dymap 5
set transform-set liang
set isakmp-profile remote
crypto dynamic-map dymap 10
set transform-set liang
set isakmp-profile l2l
crypto map mymap 10 ipsec-isakmp dynamic dymap
ip local pool ippool 123.1.1.100 123.1.1.200
ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.1.1.2
ip route 200.100.1.1 255.255.255.255 192.1.1.2
ip nat inside source list nat interface Ethernet0/0 overload
ip access-list extended nat
deny ip host 192.168.1.1 host 192.168.2.3
permit ip any any
分支:
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
crypto isakmp key cisco address 192.1.1.1 no-xauth
crypto ipsec transform-set liang esp-des esp-md5-hmac
crypto map mymap 10 ipsec-isakmp
set peer 192.1.1.1
set transform-set liang
match address liang
interface Loopback0
ip address 192.168.2.3 255.255.255.255
ip nat inside
interface Ethernet0/1
ip address 88.88.8.3 255.255.255.0
ip nat outside
ip route 0.0.0.0 0.0.0.0 88.88.8.2
ip nat inside source list nat interface Ethernet0/1 overload
ip access-list extended liang
permit ip host 192.168.2.3 host 192.168.1.1
ip access-list extended nat
deny ip host 192.168.2.3 host 192.168.1.1
permit ip any any
我们看下
center#show crypto isakmp sa
dst src state conn-id slot status
192.1.1.1 200.100.1.1 QM_IDLE 2 0 ACTIVE
192.1.1.1 88.88.8.3 QM_IDLE 1 0 ACTIVE
center#show crypto ip sa
interface: Ethernet0/0
Crypto map tag: mymap, local addr 192.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.2.3/255.255.255.255/0/0)
current_peer 88.88.8.3 port 500
PERMIT, flags={}
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (123.1.1.100/255.255.255.255/0/0)
current_peer 200.100.1.1 port 1041
PERMIT, flags={}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 40, #pkts decrypt: 40, #pkts verify: 40
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 40
client#ping 192.168.1.1 source 192.168.2.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 112/149/184 ms