*** ike 模式的配置
分别在路由和防火墙上配置***实现不同网段的通信。
26-1
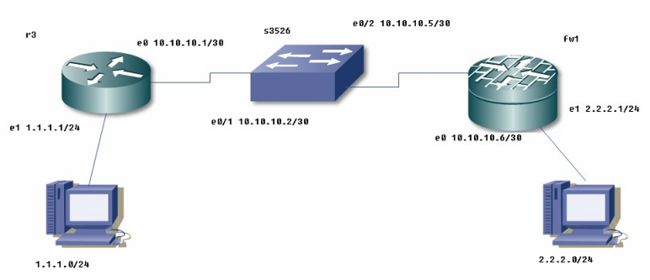
通过创建*** 实现不同网段的网络通过广域网使用可以通信。
R3.fw1上分别配置通道
三层交换机上划分vlan ,构造一个不同区域的网络模拟广域网。
配置交换机
Vlan 10
Port e 0/1
Int vlan 10
Ip add 10.10.10 .2 30
Vlan 20
Int vlan 20
Ip add 10.10.10 .5 30
Port access vlan 20
[sw12-Vlan-interface20]dis vlan 10
VLAN ID: 10
VLAN Type: static
ARP proxy disabled.
Route Interface: configured
IP Address: 10.10.10 .2
Subnet Mask: 255.255.255.252
Description: VLAN 0010
Name: VLAN 0010
Tagged Ports: none
Untagged Ports:
Ethernet0/1
[sw12-Vlan-interface20]dis vlan 20
VLAN ID: 20
VLAN Type: static
ARP proxy disabled.
Route Interface: configured
IP Address: 10.10.10 .5
Subnet Mask: 255.255.255.252
Description: VLAN 0020
Name: VLAN 0020
Tagged Ports: none
Untagged Ports:
Ethernet0/2
[sw12-Vlan-interface20]
配置***1
在路由r3的E0接口配置***
1.配置ip和默认路由
[R3-Ethernet0]ip add 10.10.10 .1 30 sub
[R3]int e 1
[R3-Ethernet1]ip add 1.1.1 .1 24
[R3]ip route-static 0.0.0 .0 0 10.10.10.2
2.配置acl
[R3]acl 3000
[R3-acl-3000]rule permit ip source 1.1.1 .0 0.0.0.255 destination 2.2.2.0 0.0.0.255
[R3-acl-3000]rule deny ip source any dest any
3.配置安全提议
[R3]ipsec proposal tran1
[R3-ipsec-proposal-tran1]encap tunnel
[R3-ipsec-proposal-tran1]esp-new authentication- md5 --指定ESP使用的验证算法
[R3-ipsec-proposal-tran1]esp enc des 指定ESP使用的加密算法
4.策略
[R3]ipsec policy p1 10 isakmp 说明使用IKE协商建立安全联盟
[R3-ipsec-policy-p1-10]security acl 3000指定对符合规则条件的报文进行保护
[R3-ipsec-policy-p1-10]pro tran1
[R3-ipsec-policy-p1-10]tunnel local 10.10.10 .1
[R3-ipsec-policy-p1-10]tunnel remote 10.10.10 .6
[R3]ike pre-shared-key 123456 remote 10.10.10 .6
5.应用
[R3-ipsec-policy-p1-10]int e0
[R3-Ethernet0]ipsec policy p1
[R3]dis cu
Now create configuration...
Current configuration!
version 1.74
local-user user1 service-type administrator password simple 123
sysname R3
undo pos-server addr-switch
firewall enable
aaa-enable
aaa accounting-scheme optional
!
ike pre-shared-key 123456 remote 10.10.10 .6
!
acl 3000 match-order auto
rule normal permit ip source 1.1.1 .0 0.0.0.255 destination 2.2.2.0 0.0.0.255
rule normal deny ip source any destination any
!
ipsec proposal tran1
!
ipsec policy p1 10 isakmp
security acl 3000
tunnel local 10.10.10 .1
tunnel remote 10.10.10 .6
!
controller e1 0
!
interface Aux0
async mode flow
link-protocol ppp
!
interface Ethernet0
ip address 192.168.100.3 255.255.255.0
ip address 10.10.10 .1 255.255.255.252 sub
ipsec policy p1
!
interface Ethernet1
ip address 1.1.1 .1 255.255.255.0
!
interface Serial0
link-protocol ppp
!
interface Serial1
link-protocol ppp
!
quit
ip route-static 0.0.0 .0 0.0.0.0 10.10.10.2 preference 60
!
return
[R3]
[R3]dis ipsec sa all
interface name: Ethernet0
path MTU: 1500
ipsec policy name: p1
ipsec policy sequence: 10
negotiation mode: isakmp
in use settings = {tunnel}
local address: 10.10.10 .1
remote address: 10.10.10 .6
esp SAs(inbound):
spi: 237707733 (0xe2b21d5)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa timing: remaining key duration (bytes/sec): (1887412028/3040)
max received sequence-number: 1
esp SAs(outbound):
spi: 2736644835 (0xa31de2e3)
proposal: ESP-ENCRYPT-DES ESP-AUTH-MD5
sa timing: remaining key duration (bytes/sec): (1887403020/3040)
max sent sequence-number: 564
[R3]
配置***2
1. 配置ip
[fw-1]int Ethernet 0/0
[fw-1-Ethernet0/0]ip add 10.10.10.6 30 sub
[fw-1]interface Ethernet0/1
[fw-1-Ethernet0/1]ip add 2.2.2.1 24
[fw-1]ip route-static 0.0.0.0 0 10.10.10.5
2. 配置acl
[fw-1]acl number 3000
[fw-1-acl-adv-3000]rule permit ip source 2.2.2.0 0.0.0.255 dest 1.1.1.0 0.0.0.255
[fw-1-acl-adv-3000]rule deny ip sour any dest any
3. 配置安全提议
[fw-1]ipsec proposal tran2
[fw-1-ipsec-proposal-tran2]encap tunnel -- 指定对整个IP报文进行加密或验证
[fw-1-ipsec-proposal-tran2]esp authentication-algorithm md5 --指定ESP使用HMAC-MD5的验证算
[fw-1-ipsec-proposal-tran2]esp encryption-algorithm des -- 指定ESP使用des的加密算法
4. 配置策略
[fw-1]ike peer hh
[fw-1-ike-peer-hh]local-address 10.10.10.6
[fw-1-ike-peer-hh]remote-address 10.10.10.1
[fw-1-ike-peer-hh]pre-shared-key 123456
--在isakmp中引用hh
[fw-1]ipsec policy p2 20 isakmp
[fw-1-ipsec-policy-isakmp-p2-20]securityacl
[fw-1-ipsec-policy-isakmp-p2-20]security acl 3000
[fw-1-ipsec-policy-isakmp-p2-20]proposal tran2
[fw-1-ipsec-policy-isakmp-p2-20]ike-peer hh
--等待对端建立共同的密钥才能建立成功。
5. 应用
[fw-1]interface Ethernet0/0
[fw-1-Ethernet0/0]ips
[fw-1-Ethernet0/0]ipsec p
[fw-1-Ethernet0/0]ipsec policy p2
[fw-1]
[fw-1]dis cu
ike peer hh
pre-shared-key 123456
remote-address 10.10.10.1
local-address 10.10.10.6
#
ipsec proposal tran2
ipsec policy p2 20 isakmp
security acl 3000
ike-peer hh
proposal tran2
acl number 3000
rule 0 permit ip source 2.2.2.0 0.0.0.255 destination 1.1.1.0 0.0.0.255
rule 1 deny ip
interface Ethernet0/0
ip address 192.168.100.41 255.255.255.0
ip address 10.10.10.6 255.255.255.252 sub
ipsec policy p2
interface Ethernet0/1
ip address 2.2.2.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 10.10.10.5 preference 60
[fw-1]
[R3-ipsec-policy-p1-10]dis ips po all
ipsec policy name: p1
ipsec policy sequence: 10
negotiation mode: isakmp
security acl: 3000
remote address 0: 10.10.10 .6
Proposal name:
ipsec sa duration: 3600 seconds
ipsec sa duration: 1843200 kilobytes
OutBound SA has NOT been established.
InBound SA has NOT been established.
[R3-ipsec-policy-p1-10]dis ips po p1
--硬件反应太慢了,等很久才出现下面的结果
[R3]dis ips po all
ipsec policy name: p1
ipsec policy sequence: 10
negotiation mode: isakmp
security acl: 3000
remote address 0: 10.10.10 .6
Proposal name: tran1
ipsec sa duration: 3600 seconds
ipsec sa duration: 1843200 kilobytes
OutBound SA has been established.
InBound SA has been established.
在两段网络里测试:
C:\Documents and Settings\Administrator>ipconfig
Windows IP Configuration
Ethernet adapter 本地连接:
Connection-specific DNS Suffix . :
IP Address. . . . . . . . . . . . : 1.1.1 .2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 1.1.1 .1
C:\Documents and Settings\Administrator>ping 2.2.2 .1
Pinging 2.2.2 .1 with 32 bytes of data:
Reply from 2.2.2 .1: bytes=32 time=5ms TTL=254
Reply from 2.2.2 .1: bytes=32 time=5ms TTL=254
Reply from 2.2.2 .1: bytes=32 time=5ms TTL=254
Reply from 2.2.2 .1: bytes=32 time=5ms TTL=254
Ping statistics for 2.2.2 .1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 5ms, Maximum = 5ms, Average = 5ms
C:\Documents and Settings\Administrator>ping 2.2.2 .2
Pinging 2.2.2 .2 with 32 bytes of data:
Reply from 2.2.2 .2: bytes=32 time=9ms TTL=126
Reply from 2.2.2 .2: bytes=32 time=9ms TTL=126
Reply from 2.2.2 .2: bytes=32 time=8ms TTL=126
Reply from 2.2.2 .2: bytes=32 time=8ms TTL=126
Ping statistics for 2.2.2 .2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 8ms, Maximum = 9ms, Average = 8ms
C:\Documents and Settings\Administrator>