Snort是一个网络***检测系统,它可以分析网络上的数据包,用以决定一个系统是否被远程***了。多数Linux发行版本都有Snort程序,因此通过urpmi、apt-get、yum等安装Snort是一件很轻松的事情。Snort可以将其收集的信息写到多种不同的存储位置以便于日后的分析。此外,Snort可被用作一个简单的数据包记录器、嗅探器,当然它主要是一个成熟的NDIS(网络***检测系统)。
实验环境
centos6.8_x64
snort_master 192.168.1.101
windows_slave 192.168.1.102
测试 windows_slave ping 192.168.1.101 -t 不断发ping包
实验软件
adodb519.tar.gz
base-1.4.5.tar.gz
barnyard2-1.9.tar.gz
daq-2.0.4.tar.gz
libdnet-1.12.tgz
snort-2.9.7.0.tar.gz
snortrules-snapshot-2983.tar.gz
软件安装
yum install -y httpd mysql-server
yum install -y mcrypt libmcrypt libmcrypt-devel libpcap libpcap-devel
yum install -y gcc flex bison zlib libpcap tcpdump gcc-c++ pcre* zlib* libdnet libdnet-devel
yum install -y php php-mysql php-mbstring php-mcrypt mysql-devel php-gd php-pear
sed -i.bak "s/#ServerName www.example.com:80/ServerName *:80/g" /etc/httpd/conf/httpd.conf sed.bak为修改备份
ll /etc/httpd/conf/httpd.conf
httpd.conf httpd.conf.bak
tar zxvf libdnet-1.12.tgz
cd libdnet-1.12
./configure && make && make install
tar zxvf daq-2.0.4.tar.gz
cd daq-2.0.4
./configure && make && make install
tar zxvf barnyard2-1.9.tar.gz
service mysqld start
mysqladmin -uroot password mysqlroot密码
mysql -uroot -pmysqlroot密码
create database snort;
grant create,select,update,insert,delete on snort.* to snort@localhost identified by 'snort';
mysql -usnort -psnort
mysql>
mysql -usnort -psnort -Dsnort < /root/barnyard2-1.9/schemas/create_mysql
cd barnyard2-1.9
./configure --with-mysql --with-mysql-libraries=/usr/lib64/mysql/
make && make install
mkdir -pv /var/log/barnyard2
mkdir -pv /var/log/snort
mkdir -pv /etc/snort
touch /var/log/snort/barnyard2.waldo
cp -pv /root/barnyard2-1.9/etc/barnyard2.conf /etc/snort/
cp -pv /etc/snort/barnyard2.conf /etc/snort/barnyard2.conf.bak
vim /etc/snort/barnyard2.conf
config logdir:/var/log/barnyard2
config hostname: localhost
config interface: eth0 监听网卡
config waldo_file:/var/log/snort/barnyard2.waldo
output database: log, mysql, user=snort password=snort dbname=snort host=localhost
tar zxvf snort-2.9.7.0.tar.gz
cd snort-2.9.7.0
./configure && make && make install
mkdir -pv /etc/snort
mkdir -pv /var/log/snort
mkdir -pv /usr/local/lib/snort_dynamicrules
mkdir -pv /etc/snort/rules
mkdir -pv /etc/snort/so_rules
mkdir -pv /etc/snort/preproc_rules
touch /etc/snort/rules/white_list.rules /etc/snort/rules/black_list.rules
cp -pv /root/snort-2.9.7.0/etc/gen-msg.map /etc/snort/
cp -pv /root/snort-2.9.7.0/etc/threshold.conf /etc/snort/
cp -pv /root/snort-2.9.7.0/etc/classification.config /etc/snort/
cp -pv /root/snort-2.9.7.0/etc/reference.config /etc/snort/
cp -pv /root/snort-2.9.7.0/etc/unicode.map /etc/snort/
cp -pv /root/snort-2.9.7.0/etc/snort.conf /etc/snort/
vim /etc/snort/snort.conf
var RULE_PATH /etc/snort/rules/
var SO_RULE_PATH /etc/snort/so_rules
var PREPROC_RULE_PATH /etc/snort/preproc_rules
var WHITE_LIST_PATH /etc/snort/rules
var BLACK_LIST_PATH /etc/snort/rules
config logdir: /var/log/snort
# output unified2: filename merged.log, limit 128, nostamp, mpls_event_types, vlan_event_types
output unified2: filename snort.log,limit 128
tar zxvf snortrules-snapshot-2983.tar.gz -C /etc/snort/
cp -pv /etc/snort/etc/sid-msg.map /etc/snort/
snort -T -i eth0 -c /etc/snort/snort.conf &
Snort successfully validated the configuration!
Snort exiting
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo &
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D &
snort -c /etc/snort/snort.conf -i eth0 -D &
killall -9 snort
killall -9 barnyard2 杀死进程
tar zxvf adodb519.tar.gz
tar zxvf base-1.4.5.tar.gz
mv /root/adodb5 /var/www/html/adodb
mv /root/base-1.4.5 /var/www/html/base
chown -R apache:apache /var/www/html/
chmod 755 /var/www/html/adodb/
touch /var/www/html/test.html
echo welcome to server > /var/www/html/test.html 建立apache测试页
sed -i 's/#AddType application/AddType application/g' /etc/httpd/conf/httpd.conf 配置apahce/php 结合
sed -i '765 aAddType application/x-httpd-php .php' /etc/httpd/conf/httpd.conf
765行插入AddType application/x-httpd-php .php配置 a为插入配置内容
netstat -tuplna | grep mysql
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN 28424/mysqld
netstat -tuplna | grep httpd
tcp 0 0 :::80 :::* LISTEN 28460/httpd
ps -ef | grep snort
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D
snort -c /etc/snort/snort.conf -i eth0 -D
service mysqld restart
service httpd restart
chkconfig --level 35 httpd on
chkconfig --level 35 mysqld on
cp -pv /etc/snort/rules/local.rules /etc/snort/rules/local.rules.bak 添加测试规则
echo "alert icmp any any -> any any (msg: "IcmP Packet detected";sid:1000001;)" >> /etc/snort/rules/local.rules
cat /etc/snort/rules/local.rules | grep alert
alert icmp any any -> any any (msg: IcmP Packet detected;sid:1000001;)
touch /var/www/html/test.php php测试页,测试完毕最好即可删除
echo "" > /var/www/html/test.php
curl http://localhost/index.html
welcome to server
http://serverip/test.php
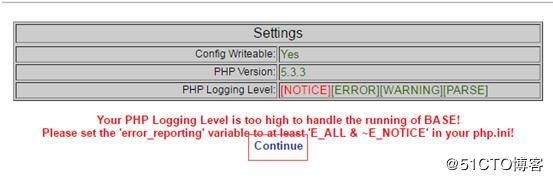
http://serviceip/base/setup/index.php
cp -pv /etc/rc.d/rc.local /etc/rc.d/rc.local.bak 设置服务开机启动
echo "snort -T -i eth0 -c /etc/snort/snort.conf &" >> /etc/rc.d/rc.local
echo "barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo &" >> /etc/rc.d/rc.local
echo "barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D &" >> /etc/rc.d/rc.local
echo "snort -c /etc/snort/snort.conf -i eth0 -D &" >> /etc/rc.d/rc.local
cat /etc/rc.d/rc.local
snort -T -i eth0 -c /etc/snort/snort.conf &
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo &
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D &
snort -c /etc/snort/snort.conf -i eth0 -D &