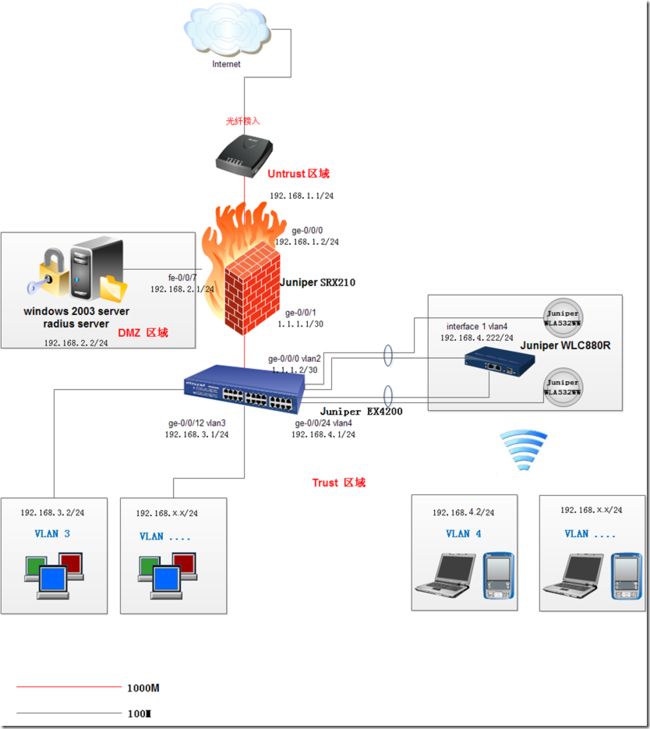
Hi,本文是一个测试环境,模拟中小型企业广泛使用安全稳定的juniper产品来管理公司网络。从安全,到网关,到无线均是juniper产品,本次主要是讲解这些产品的配置,具体设备的性能和可扩展性请根据客户实际需求配置。谢谢
首先是SRX210上面的配置:
步骤:
root@juniperSrx210# load factory-default //清除所有配置
root@juniperSrx210# set system root-authentication plain-text-password
commit
delete interfaces //清除所有默认接口
delete security zones //清除所有默认zones
root@juniperSrx210# show |display set
set version 12.1X44.5
set system root-authentication encrypted-password "$1$okkrnGtM$PoUGILVvgQ5TL4LHNxeMO."
------------系统配置------------
set system name-server 202.96.134.133
set system name-server 8.8.8.8
set system services ssh
set system services telnet
set system services xnm-clear-text
set system services web-management http interface fe-0/0/7.0
set system services web-management http interface ge-0/0/1.0
set system services web-management https system-generated-certificate
set system services web-management https interface ge-0/0/0.0
------------日志服务器配置------------
set system syslog archive size 100k
set system syslog archive files 3
set system syslog user * any emergency
set system syslog file messages any critical
set system syslog file messages authorization info
set system syslog file interactive-commands interactive-commands error
set system max-configurations-on-flash 5
set system max-configuration-rollbacks 5
set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval
------------接口配置------------
set interfaces ge-0/0/0 unit 0 family inet address 192.168.1.2/24
set interfaces ge-0/0/1 unit 0 family inet address 1.1.1.1/30
set interfaces fe-0/0/7 unit 0 family inet address 192.168.2.1/24
set interfaces vlan unit 0
------------路由配置------------
set routing-options static route 0.0.0.0/0 next-hop 192.168.1.1
set protocols ospf area 0.0.0.0 interface fe-0/0/7.0
set protocols ospf area 0.0.0.0 interface ge-0/0/1.0
set protocols stp
------------防火墙默认配置------------
set security screen ids-option untrust-screen icmp ping-death
set security screen ids-option untrust-screen ip source-route-option
set security screen ids-option untrust-screen ip tear-drop
set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024
set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200
set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024
set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048
set security screen ids-option untrust-screen tcp syn-flood timeout 20
set security screen ids-option untrust-screen tcp land
------------策略配置------------
set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any
set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any
set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any
set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit
set security policies from-zone trust to-zone untrust policy trust-to-untrust then log session-init
set security policies from-zone trust to-zone untrust policy trust-to-untrust then log session-close
set security policies from-zone DMZ to-zone untrust policy DMZ-TO-untrust match source-address any
set security policies from-zone DMZ to-zone untrust policy DMZ-TO-untrust match destination-address any
set security policies from-zone DMZ to-zone untrust policy DMZ-TO-untrust match application any
set security policies from-zone DMZ to-zone untrust policy DMZ-TO-untrust then permit
set security policies from-zone trust to-zone DMZ policy trust-to-DMZ match source-address any
set security policies from-zone trust to-zone DMZ policy trust-to-DMZ match destination-address any
set security policies from-zone trust to-zone DMZ policy trust-to-DMZ match application any
set security policies from-zone trust to-zone DMZ policy trust-to-DMZ then permit
set security policies from-zone DMZ to-zone trust policy DMZ-to-trust match source-address any
set security policies from-zone DMZ to-zone trust policy DMZ-to-trust match destination-address any
set security policies from-zone DMZ to-zone trust policy DMZ-to-trust match application any
set security policies from-zone DMZ to-zone trust policy DMZ-to-trust then permit
set security policies from-zone untrust to-zone trust policy untrust-to-trust match source-address any
set security policies from-zone untrust to-zone trust policy untrust-to-trust match destination-address any
set security policies from-zone untrust to-zone trust policy untrust-to-trust match application any
set security policies from-zone untrust to-zone trust policy untrust-to-trust then permit
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ match source-address any
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ match destination-address any
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ match application any
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ then permit
------------ZONES配置------------
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic system-services all
set security zones security-zone trust interfaces ge-0/0/1.0 host-inbound-traffic protocols all
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services all
set security zones security-zone DMZ interfaces fe-0/0/7.0 host-inbound-traffic system-services all
set security zones security-zone DMZ interfaces fe-0/0/7.0 host-inbound-traffic protocols all
------------默认vlan配置------------
set vlans vlan-trust vlan-id 3
set vlans vlan-trust l3-interface vlan.0
交换机的配置:
admin# show |display set
set version 11.4R1.6
set system root-authentication encrypted-password "$1$pWh6yJUK$/ErngshQbpbEuuphoRn041"
set system login user admin uid 2000
set system login user admin class super-user
set system login user admin authentication encrypted-password "$1$pygG.dck$sYJPoTD.1JlCMUwlPgWGV1"
set system services ssh
set system services telnet
set system services dhcp pool 192.168.5.0/24 address-range low 192.168.5.2
set system services dhcp pool 192.168.5.0/24 address-range high 192.168.5.253
set system services dhcp pool 192.168.5.0/24 name-server 8.8.8.8
set system services dhcp pool 192.168.5.0/24 router 192.168.5.1
set system services dhcp pool 192.168.4.0/24 address-range low 192.168.4.2
set system services dhcp pool 192.168.4.0/24 address-range high 192.168.4.253
set system services dhcp pool 192.168.4.0/24 name-server 8.8.8.8
set system services dhcp pool 192.168.4.0/24 router 192.168.4.1
set system services dhcp pool 192.168.6.0/24 address-range low 192.168.6.2
set system services dhcp pool 192.168.6.0/24 address-range high 192.168.6.253
set system services dhcp pool 192.168.6.0/24 name-server 8.8.8.8
set system services dhcp pool 192.168.6.0/24 router 192.168.6.1
set system syslog user * any emergency
set system syslog file messages any notice
set system syslog file messages authorization info
set system syslog file interactive-commands interactive-commands any
set interfaces interface-range IT12-23 member-range ge-0/0/12 to ge-0/0/23
set interfaces interface-range IT12-23 unit 0 family ethernet-switching vlan members vlan5
set interfaces interface-range IT1-11 member-range ge-0/0/0 to ge-0/0/11
set interfaces interface-range IT1-11 unit 0 family ethernet-switching vlan members vlan2
set interfaces interface-range IT24-35 member-range ge-0/0/24 to ge-0/0/35
set interfaces interface-range IT24-35 unit 0 family ethernet-switching port-mode access
set interfaces interface-range IT24-35 unit 0 family ethernet-switching vlan members vlan4
set interfaces interface-range IT36-47 member-range ge-0/0/36 to ge-0/0/47
set interfaces interface-range IT36-47 unit 0 family ethernet-switching vlan members vlan6
set interfaces ge-0/0/0 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members vlan2
set interfaces ge-0/0/12 unit 0 family ethernet-switching
set interfaces ge-0/0/24 unit 0 family ethernet-switching vlan members vlan4
set interfaces vlan unit 2 family inet address 1.1.1.2/30
set interfaces vlan unit 4 family inet address 192.168.4.1/24
set interfaces vlan unit 5 family inet address 192.168.5.1/24
set interfaces vlan unit 6 family inet address 192.168.6.1/24
set routing-options static route 0.0.0.0/0 next-hop 1.1.1.1
set protocols ospf area 0.0.0.0 interface vlan.2
set protocols ospf area 0.0.0.0 interface vlan.4 passive
set protocols ospf area 0.0.0.0 interface vlan.5 passive
set protocols ospf area 0.0.0.0 interface vlan.6 passive
set protocols igmp-snooping vlan all
set protocols rstp
set protocols lldp interface all
set protocols lldp-med interface all
set ethernet-switching-options storm-control interface all
set vlans vlan2 vlan-id 2
set vlans vlan2 interface ge-0/0/0.0
set vlans vlan2 l3-interface vlan.2
set vlans vlan4 vlan-id 4
set vlans vlan4 l3-interface vlan.4
set vlans vlan5 vlan-id 5
set vlans vlan5 l3-interface vlan.5
set vlans vlan6 vlan-id 6
set vlans vlan6 l3-interface vlan.6
set poe interface all
无线控制台WLC880R的配置
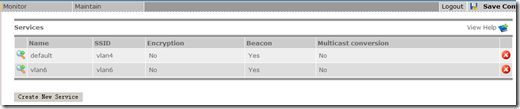
划了两个vlan
分别建了两个不同的SSID
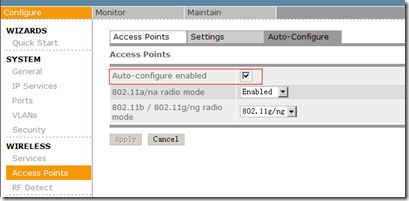
自动学习AP
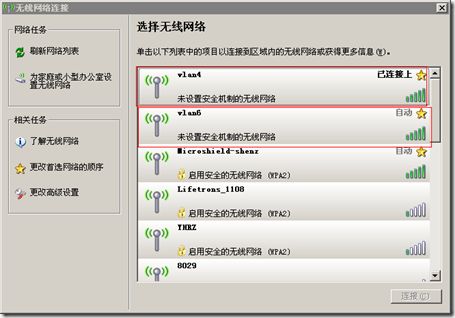
配置完成后,控制台自动搜索到以下AP:
无线显示:
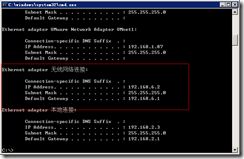
连接后,自动获取交换机上下发的IP
连接到VLAN4
连接到VLAN6
最后测试一下无线用户登陆需要经过Radius认证。
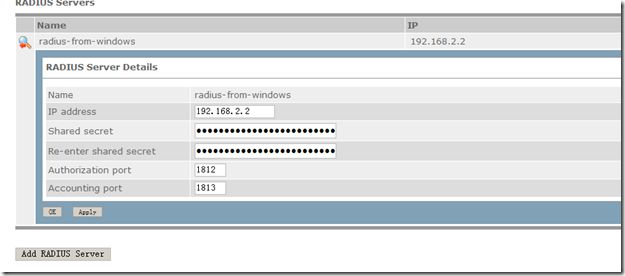
控制台上配置Radius认证:
服务器配置
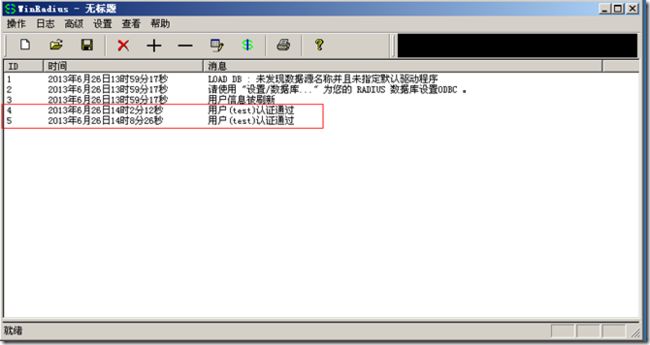
使用winradius做测试:
连接无线后不能拼外网:
打开任意网站,需要进行验证:
验证成功后显示:
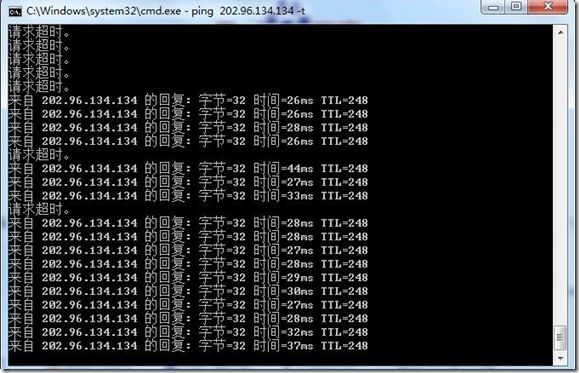
外网拼通:
radius服务器显示认证成功: