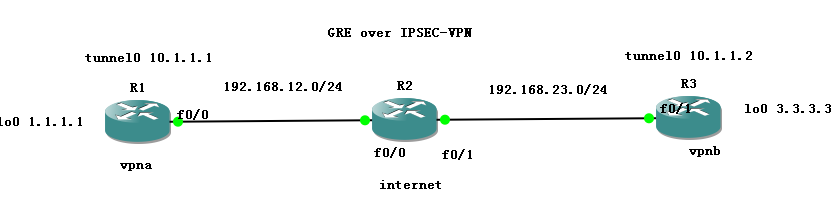
GRE over IPSEC-×××
GRE over IPSEC-×××则是通过
GRE通用路由封装协议来建立一个非安全的隧道去传递私网路由,而且GRE支持组播协议,所以也就支持动态路由协议。但GRE的安全性就需要IPSEC去保证了,而IPSEC可悲的是又不支持组播,除非用到其它诸如VTI的一些技术了。所以自然而然,人们就想到GRE overIPSEC的×××去安全的传递内网数据。
Top:
配置:
解法:首先呢,配置好
GRE隧道,然后再配置IPSEC-×××,隧道模式选传输模式就可以了,因为GRE已经封装了公网的IP了,就不需要再新添IP报头了,因为我们的GRE隧道的建立是通过默认路由来建立的,所以对于×××路由器如何建立好IPSEC-×××可以有两种配置:1,静态路由,2,动态路由。
一:利用静态路由指向
***b/***a出口为gre tunnel0口。
R1:
R1#show run
hostname R1
ip cef
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 192.168.23.2
!
!
crypto ipsec transform-set myset esp-3des esp-sha-hmac
mode transport//指明为IPSEC-×××模式为传输模式。
!
crypto map map 1 ipsec-isakmp
set peer 192.168.23.2
set transform-set myset
match address 101
interface Loopback0//模拟×××内网
ip address 1.1.1.1 255.255.255.0
!
interface Tunnel0
ip address 10.1.1.1 255.255.255.0//指明隧道地址与对端的IP同处于一个网络里
tunnel source FastEthernet0/0//指明隧道源
tunnel destination 192.168.23.2/指明隧道目的
tunnel key 520 //用来验证GRE隧道
!
interface FastEthernet0/0
ip address 192.168.12.1 255.255.255.0
crypto map map
!
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0 /默认路由可以用来建立GRE tunnel,而后续组播的应用也是基于它的如动态路由协议。
ip route 3.3.3.3 255.255.255.255 Tunnel0 //指定×××流量的出口
logging alarm informational
access-list 101 permit gre host 192.168.12.1 host 192.168.23.2//定义感兴趣流,由于×××流量需要经过GRE tunnel0之后再经过实际物理口FA0/0出去,显然到fa0/0时,GRE封装已完成,且IP地址也为192.168.12.1,192.168.23.2故×××隧道模式为传输模式。
R2:
interface FastEthernet0/0
ip address 192.168.12.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.23.1 255.255.255.0
duplex auto
speed auto
R3:
R3#show run
hostname R3
!
ip cef
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 192.168.12.1
!
!
crypto ipsec transform-set myset esp-3des esp-sha-hmac
mode transport
!
crypto map map 1 ipsec-isakmp
set peer 192.168.12.1
set transform-set myset
match address 101
!
interface Loopback0
ip address 3.3.3.3 255.255.255.0
!
interface Tunnel0
ip address 10.1.1.2 255.255.255.0
tunnel source FastEthernet0/1
tunnel destination 192.168.12.1
tunnel key 520
!
!
interface FastEthernet0/1
ip address 192.168.23.2 255.255.255.0
crypto map map
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/1
ip route 1.1.1.1 255.255.255.255 Tunnel0
access-list 101 permit gre host 192.168.23.2 host 192.168.12.1
2,动态路由协议:
注意:
不要把公网也就是GRE tunnel源,目地地址放入动态路由协议里面宣告,否则会出现tunnel与动态路由时up,时down的情况。因为gre tunnel的建立是靠默认路由,而动态路由又是通过GRE隧道学到的,如果把静态默认路由宣告后,那么R1学到192.168.23.0是从tunnel0口出去了,gre tunnel的建立原本是从默认路由走fa0/0出去的而现在却是去tunne0(路由表最长匹配原则),然后默认路由失效,这显然是矛盾的,路由器会找不到方向,,这样gre tunnel会导致tunnel建立超时,会down掉,那么自然而然基于gre tunnel的动态路由协议也会down掉,这时动态路由还没起来,而GRE tunnel隧道的建立使用的
默认路由又可以匹配了,此时tunnel 又建立,动态路由也起来了,这样会一直up &down下去。
配置:
R1
ß-
àR2:
去掉静态路由ip route 3.3.3.3 255.255.255.255 tunnel 0
用动态路由来学习对端的路由,以便从正确的tunnel口出去。
Router eigrp 1
Network 10.1.1.0
Network 1.1.1.0
No au
Exit
即可。
如果加入net 192.168.12.0
出现的现象:
R1#
*Jun 20 12:12:49.399: %ADJ-5-PARENT: Midchain parent maintenance for IP midchain out of Tunnel0 66AFF7A0 - looped chain attempting to stack
*Jun 20 12:12:50.395: %TUN-5-RECURDOWN: Tunnel0 temporarily disabled due to recursive routing
R1#
*Jun 20 12:12:51.391: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to down
*Jun 20 12:12:51.527: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 10.1.1.2 (Tunnel0) is down: interface down
R1#
*Jun 20 12:13:52.563: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to up
R1#
去掉就正常了。
R1#ping 3.3.3.3 source lo 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 392/424/480 ms
R1#
IPSEC SA:
R3#show crypto ipsec sa
PFS (Y/N): N, DH group: none
interface: FastEthernet0/1
Crypto map tag: map, local addr 192.168.23.2
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.23.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (192.168.12.1/255.255.255.255/47/0)
current_peer 192.168.12.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 390, #pkts encrypt: 390, #pkts digest: 390
#pkts decaps: 354, #pkts decrypt: 354, #pkts verify: 354
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 2, #recv errors 0
local crypto endpt.: 192.168.23.2, remote crypto endpt.: 192.168.12.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/1
current outbound spi: 0xAD8D7319(2911728409)
inbound esp sas:
spi: 0xE7F2ED71(3891457393)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 3, flow_id: SW:3, sibling_flags 80000006, crypto map: map
sa timing: remaining key lifetime (k/sec): (4378759/3439)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAD8D7319(2911728409)
transform: esp-3des esp-sha-hmac ,
in use settings ={Transport, }
conn id: 4, flow_id: SW:4, sibling_flags 80000006, crypto map: map
sa timing: remaining key lifetime (k/sec): (4378759/3439)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R3#show cry