使用httpd-2.2和httpd-2.4实现
> 1.建立httpd服务,要求:
> 1) 提供两个基于名称的虚拟主机www1, www2;要求每个虚拟主机都有单独的错误日志和访问日志;
> 2) 通过www1的/server-status提供状态信息,且仅允许172.16.0.1主机访问;
> 3) www2不允许192.168.1.0/24网络中任意主机访问;
> 2.为上面的第2)个虚拟主机提供https服务。
>
使用httpd-2.2实现基于主机名的虚拟主机服务,并提供https服务:
1.准备:(1)在VMwareWorkstation平台下的CentOS6.9一枚;(2)真实机客户端一个;
2.环境:(1)CentOS6.9系统中安装httpd应用程序并启动httpd服务;(2)关闭防火墙;(3)设置SELinux;
(1) [root@chenliang ~]# yum -y install httpd
[root@chenliang ~]# service httpd start
正在启动 httpd:
(2) [root@chenliang ~]# iptables -F
(3) [root@chenliang ~]# setenforce 0
3.操作步骤:
[root@chenliang ~]# cd /etc/httpd/conf
[root@chenliang conf]# vim httpd.conf
NameVirtualHost 172.16.69.1:80 //在httpd.conf配置文件中添加这一行,IP地址要和下面设置的虚拟机文件保持一致
[root@chenliang conf]# cd ../conf.d //在配置虚拟主机时,我们在/etc/httpd/conf.d片段配置文件中设置
[root@chenliang conf.d]# ls
manual.conf mod_dnssd.conf README ssl.conf welcome.conf
[root@chenliang conf.d]# vim www1.conf //设置虚拟主机www1
>
> DocumentRoot /var/www/www1 //www1站点的资源路径映射
> ServerName www1.cl.com //这就是基于主机名设置虚拟主机
> ErrorLog logs/www1-error_log //每个虚拟主机都有单独的错误日志
> CustomLog logs/www1-access_log combined //每个虚拟主机都有单独访问日志
>
>
> SetHandler server-status
> Order deny,allow
> Deny from all
> Allow from 172.16.0.1 //通过www1的/server-status提供状态信息,且仅允许172.16.0.1主机访问
>
>
>
[root@chenliang conf.d]# vim www2.conf
>
> DocumentRoot /var/www/www2 //www2站点的资源路径映射
> ServerName www2.cl.com
> ErrorLog logs/www2-error_log //每个虚拟主机都有单独的错误日志
> CustomLog logs/www2-access_log combined //每个虚拟主机都有单独访问日志
>
>
> Options None
> AllowOverride None
> Order deny,allow
> Deny from 192.168.1.0/24 //www2不允许192.168.1.0/24网络中任意主机访问
>
>
>
[root@chenliang conf.d]# mkdir -pv /var/www/www{1,2} //为web站点的资源提供路径映射
mkdir: 已创建目录 "/var/www/www1"
mkdir: 已创建目录 "/var/www/www2"
[root@chenliang conf.d]# echo "WWW1's web site~~" >> //var/www/www1/index.html //创建web站点首页文件并添加内容
[root@chenliang conf.d]# echo "WWW2's web site~~" >> //var/www/www2/index.html
[root@chenliang conf.d]# httpd -t //检查编写的虚拟主机语法有没有错误
httpd: apr_sockaddr_info_get() failed for chenliang
httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1 for ServerName
Syntax OK //语法OK
[root@chenliang conf.d]# service httpd restart //在每一次配置好httpd服务后要重新启动服务
停止 httpd: [确定]
正在启动 httpd:httpd: apr_sockaddr_info_get() failed for chenliang
httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1 for ServerName
[确定]
4.测试:
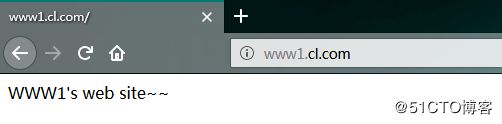
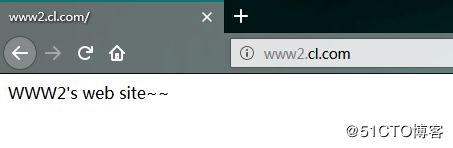
创建的虚拟主机web站点:
打开主机的真实主机进行测试,首先更改一下系统C盘下\Windows\System32\drivers\etc\hosts文件,在最下面添加配置的虚拟主机web站点:172.16.69.1 www1.cl.com www2.cl.com
结果:
5.提供https服务:
1)建立私有CA:
创建CA的私钥文件:
[root@chenliang CA]# (umask 077; openssl genrsa -out private/cakey.pem 4096)
Generating RSA private key, 4096 bit long modulus
...............................................................................................................................................................................................................++
......................................................++
e is 65537 (0x10001)
生成自签证书:
[root@chenliang CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HeBei
Locality Name (eg, city) [Default City]:Handan
Organization Name (eg, company) [Default Company Ltd]:CL
Organizational Unit Name (eg, section) []:Tech
Common Name (eg, your name or your server's hostname) []:chenliang
Email Address []:
[root@chenliang CA]# ls //查看创建的证书文件
cacert.pem certs crl newcerts private
[root@chenliang CA]# touch /etc/pki/CA/index.txt //完善CA所必需目录级文件要求和文本文件级文件要求
[root@chenliang CA]# echo 01 > /etc/pki/CA/serial
2)创建https站点:{有个前提要安装httpd模块列表中的mod_ssl模块}
[root@chenliang ~]# mkdir /etc/httpd/ssl
[root@chenliang ~]# cd /etc/httpd/ssl
[root@chenliang ssl]# (umask 077;openssl genrsa -out httpd.key 4096)
Generating RSA private key, 4096 bit long modulus
.....................................................................................++
.......................................................................................................................................................................................................................................................................................................................................................................................................................................................++
e is 65537 (0x10001)
[root@chenliang ssl]# openssl req -new -key httpd.key -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HeBei
Locality Name (eg, city) [Default City]:Handan
Organization Name (eg, company) [Default Company Ltd]:CL
Organizational Unit Name (eg, section) []:Tech
Common Name (eg, your name or your server's hostname) []:chenliang
Email Address []:
A challenge password []:123456
An optional company name []:chenliang
将证书请求发送到CA:~]# scp httpd.csr CA_SERVER:/tmp //因为这里是创建的私有CA,所以不使用此命令,跳过
在CA上为此次请求签发证书:
[root@chenliang ssl]# cd /etc/pki/CA
[root@chenliang CA]# ls
cacert.pem certs crl index.txt newcerts private serial
[root@chenliang CA]# openssl ca -in /etc/httpd/ssl/httpd.csr -out certs/httpd.crt
[root@chenliang CA]# ls certs/
httpd.crt
在httpd服务器上,删除证书请求文件:
[root@chenliang CA]# cp certs/httpd.crt /etc/httpd/ssl/
[root@chenliang CA]# cd -
/etc/httpd/ssl
[root@chenliang ssl]# ls
httpd.crt httpd.csr httpd.key
[root@chenliang ssl]# rm -f httpd.csr
[root@chenliang ssl]# ls
httpd.crt httpd.key
在httpd服务器上配置ssl支持:
1) 保证mod_ssl模块被正确装载;如果没有,则需要单独安装:yum install -y mod_ssl
2) 配置https的虚拟主机:
[root@chenliang conf.d]# vim ssl.conf
DocumentRoot "/var/www/www2"
ServerName www2.cl.com:443
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
测试https建立是否成功:
重启服务:
[root@chenliang conf.d]# service httpd restart
停止 httpd: [确定]
正在启动 httpd:httpd: apr_sockaddr_info_get() failed for chenliang
httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1 for ServerName
[确定]
在真实主机上(因为我们是私有证书是不受信任的):
添加例外后:
至此,httpd-2.2基于主机名建立虚拟主机并实现web站点的https服务完成。