1.1、IPsec ×××
1.1.1、实验描述
在配制ipsec ***时一般按照以下几个频骤
第一.R1发送感兴流量到R2(设定感兴流量即ACL)
第二.R1和R2协商IKE 第一阶段(phase 1)
* 确定密钥分发方式
* 确定验证方式
* 对等方确定ISAKMP策略(加密算法、hash算法、IKE SA生存期)
第三.R1和R2协商IKE 第二阶段(phase 2)
第四.通过IPsec信道交互信息
第五.在无数据发送的时候自动关团信道
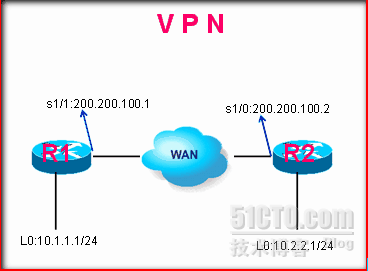
1.1.2、拓扑
如图所示,R1和R2为两个路由器,它们是通过internet连一起的,(但实验是通过串口直接连在一起),R1的loopback 0模拟R1这边的内网,R2的loopback 0模拟R2的内网,最后实现两边的loopback是通过×××实现互连的
1.1.3、基本配制
R1=========================
host R1
no ip domain-lookup
line con 0
logg sy
exec-time 0 0
!
int s1/1
ip add 200.200.100.1 255.255.255.252
no sh
int loopback 0
ip add 10.1.1.1 255.255.255.0
exit
R2=================================
host R2
no ip domain-lookup
line con 0
logg sy
exec-time 0 0
!
int s1/0
ip add 200.200.100.2 255.255.255.252
cl ra 56000
no sh
int loopback 0
ip add 10.2.2.1 255.255.255.0
exit
!
1.1.4、×××配制
R1=================================================
access-list 101 permit ip host 10.1.1.1 host 10.2.2.1
crypto isakmp policy 1
authentication pre-share
hash md5
exit
!
crypto isakmp key 0 cisco address 200.200.100.2 255.255.255.0
!
crypto ipsec transform-set shanghai esp-des esp-md5-hmac
!
crypto map ***_to_shanghai 10 ipsec-isakmp
match add 101
set peer 200.200.100.2
set transform shanghai
!
ip route 10.2.2.0 255.255.255.0 200.200.100.2
int s1/1
crypto map ***_to_shanghai
R2 ================================================
access-list 101 permit ip host 10.2.2.1 host 10.1.1.1
crypto isakmp policy 1
authentication pre-share
hash md5
exit
!
crypto isakmp key 0 cisco address 200.200.100.1 255.255.255.0
!
crypto ipsec transform-set shanghai esp-des esp-md5-hmac
!
crypto map ***_to_shanghai 10 ipsec-isakmp
match add 101
set peer 200.200.100.1
set transform shanghai
!
ip route 10.1.1.0 255.255.255.0 200.200.100.1
!
int s1/0
crypto map ***_to_shanghai
!
1.1.5、校验
在R1上扩展ping 10.2.2.1
R1#ping
Protocol [ip]:
Target IP address: 10.2.2.1
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: loo 0
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.2.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
..!!!
Success rate is 60 percent (3/5), round-trip min/avg/max = 172/238/288 ms
R1#show crypto map
Crypto Map "***_to_shanghai" 10 ipsec-isakmp
Peer = 200.200.100.2
Extended IP access list 101
access-list 101 permit ip host 10.1.1.1 host 10.2.2.1
Current peer: 200.200.100.2
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
shanghai,
}
Interfaces using crypto map ***_to_shanghai:
Serial1/1
R1#show crypto ipsec sa
interface: Serial1/1
Crypto map tag: ***_to_shanghai, local addr 200.200.100.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (10.2.2.1/255.255.255.255/0/0)
current_peer 200.200.100.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 2, #recv errors 0
local crypto endpt.: 200.200.100.1, remote crypto endpt.: 200.200.100.2
path mtu 1500, ip mtu 1500
current outbound spi: 0xC57F1ABD(3313441469)
inbound esp sas:
spi: 0x9C8542B5(2625979061)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: ***_to_shanghai
sa timing: remaining key lifetime (k/sec): (4416419/3493)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC57F1ABD(3313441469)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: ***_to_shanghai
sa timing: remaining key lifetime (k/sec): (4416419/3492)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R1#show crypto isakmp sa
dst src state conn-id slot status
200.200.100.2 200.200.100.1 QM_IDLE 1 0 ACTIVE