CISCO路由器NAT-T与IPSec ×××配置实验
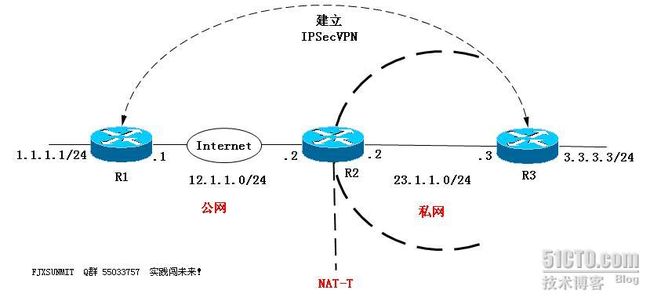
1.实验拓扑:
2.
基本原理:
A.R1上配加密图时,address为 12.1.1 .2 IP;【不是内网的23.1.1.3哦!】
B.R3上配加密图时,address为 12.1.1 .1 IP;
C.内网到远程时,因路由器自动开启NAT-T功能,所有可以ping通;
D.远程到内网时,要做UDP端口映射,即R2上静态映射端口500和4500;
3.基本配置:
R1:
R1#sh run
hostname R1
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 12.1.1 .2
!
crypto ipsec transform-set myset esp-3des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1 .2
set transform-set myset
match address 100
!
interface Loopback0
ip address 1.1.1 .1 255.255.255.0
!
interface FastEthernet0/0
ip address 12.1.1 .1 255.255.255.0
duplex half
crypto map cisco
ip route 0.0.0 .0 0.0.0.0 FastEthernet0/0
access-list 100 permit i p 1.1.1 .0 0.0.0.255 3.3.3.0 0.0.0.255
!
!
R2:
R2#sh run
hostname R2
!
interface FastEthernet0/0
ip address 12.1.1 .2 255.255.255.0
ip nat outside
duplex half
!
interface FastEthernet3/0
ip address 23.1.1 .2 255.255.255.0
ip nat inside
duplex half
!
ip nat inside source list 101 interface FastEthernet0/0 overload
ip nat inside source static es p 23.1.1 .3 interface FastEthernet0/0
ip nat inside source static ud p 23.1.1 .3 4500 interface FastEthernet0/0 4500
ip nat inside source static ud p 23.1.1 .3 500 interface FastEthernet0/0 500
ip route 0.0.0 .0 0.0.0.0 FastEthernet0/0
ip route 3.3.3 .0 255.255.255.0 FastEthernet3/0
access-list 101 permit i p 3.3.0 .0 0.0.255.255 any
!
R3:
R3#sh run
hostname R3
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 12.1.1 .1
!
crypto ipsec transform-set myset esp-3des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1 .1
set transform-set myset
match address 100
!
interface Loopback0
ip address 3.3.3 .3 255.255.255.0
!
interface FastEthernet3/0
ip address 23.1.1 .3 255.255.255.0
duplex half
crypto map cisco
ip route 0.0.0 .0 0.0.0.0 FastEthernet3/0
access-list 100 permit i p 3.3.3 .0 0.0.0.255 1.1.1.0 0.0.0.255
!
4.实验测试结果
R3#ping 1.1.1 .1 sou 3.3.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1 .1, timeout is 2 seconds:
Packet sent with a source address of 3.3.3 .3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 120/212/452 ms
R3#
R2#
*Mar 18 17:00:51.415: NAT: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [160]
*Mar 18 17:00:51.763: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [167]
*Mar 18 17:00:51.903: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [163]
*Mar 18 17:00:51.975: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [170]
*Mar 18 17:00:52.111: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [166]
*Mar 18 17:00:52.159: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [173]
*Mar 18 17:00:52.231: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [169]
*Mar 18 17:00:52.319: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [176]
*Mar 18 17:00:52.343: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [172]
*Mar 18 17:00:52.407: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [179]
R1#ping 3.3.3 .3 sou 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3 .3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1 .1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/144/220 ms
R1#
R2#
*Mar 18 17:01:37.355: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [182]
*Mar 18 17:01:37.547: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [175]
*Mar 18 17:01:37.667: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [185]
*Mar 18 17:01:37.787: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [178]
*Mar 18 17:01:37.835: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [188]
*Mar 18 17:01:37.875: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [181]
*Mar 18 17:01:37.947: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [191]
*Mar 18 17:01:37.955: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [184]
*Mar 18 17:01:37.999: NAT*: s= 12.1.1 .1, d=12.1.1.2->23.1.1.3 [194]
*Mar 18 17:01:38.015: NAT*: s= 23.1.1 .3->12.1.1.2, d=12.1.1.1 [187]
R2#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
es p 12.1.1 .2:0 23.1.1 .3:0 --- ---
ud p 12.1.1 .2:500 23.1.1 .3:500 --- ---
ud p 12.1.1 .2:4500 23.1.1 .3:4500 --- ---
ud p 12.1.1 .2:4500 23.1.1 .3:4500 12.1.1 .1:4500 12.1.1 .1:4500
R2#
5.实验总结:
A:NAT-T实施:
1.是否支持NAT-T;
2.是否有NAT/PAT;
3.是否应该实施NAT-T;
B:防火墙默认不开启 NAT-T穿透功能的哦!【配置时要注意咯!】