题目描述:
下载附件得到
server.py打开得到如下代码:
#!/usr/bin/python
# -*- coding: utf-8 -*-
from Crypto.Cipher import AES
from Crypto.Util.strxor import strxor
from Crypto.Random import get_random_bytes
from FLAG import flag
class MAC:
def __init__(self):
self.key = get_random_bytes(16) #私钥
self.iv = get_random_bytes(16) #AES 加密向量
def pad(self, msg):#填充算法 注意向量长度最少16字节。如果长度不够,请填充"\0"。建议随机生成,然后base64后传给前端。
pad_length = 16 - len(msg) % 16
return msg + chr(pad_length) * pad_length
def unpad(self, msg):#反填充
return msg[:-ord(msg[-1])]
def code(self, msg):
res = chr(0)*16
for i in range(len(msg)/16):
res = strxor(msg[i*16:(i+1)*16], res)
aes = AES.new(self.key, AES.MODE_CBC, self.iv)
return aes.encrypt(res).encode('hex')
def identity(self, msg, code):
if self.code(msg) == code:
msg = self.unpad(msg)
if msg == 'please send me your flag':
print 'remote: ok, here is your flag:%s' % flag
else:
print 'remote: I got it'
else:
print 'remote: hacker!'
if __name__ == '__main__':
mac = MAC()
message = 'see you at three o\'clock tomorrow'
print 'you seem to have intercepted something:{%s:%s}' %(mac.pad(message).encode('hex'), mac.code(mac.pad(message)))
print 'so send your message:'
msg = raw_input() #输入字符,不用加‘’
print 'and your code:'
code = raw_input()
mac.identity(msg.decode('hex'), code)
exit()
分析:
self.key和self.iv随机不可获得。但是我们知道一组明文-密文对,identity()加密后才check字符串,所以利用unpad()函数,构造合适的字符串绕过。
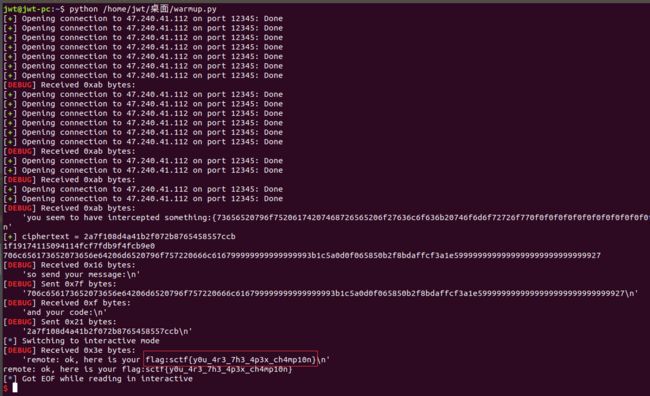
图片.png
附脚本如下:
from pwn import *
from Crypto.Util.strxor import strxor
p=remote('47.240.41.112',12345)
p.recvuntil('0f:')
c = p.recv(32)
msg=('706c656173652073656e64206d6520796f757220666c6167'+'8'*16).decode('hex')
print c1
res = chr(0)*16
for i in range(len(msg)/16):
res = strxor(msg[i*16:(i+1)*16], res)
res1 = chr(0)*16
msg1=('73656520796f75206174207468726565206f27636c6f636b20746f6d6f72726f77'+'0f'*15).decode('hex')
for i in range(len(msg1)/16):
res1 = strxor(msg1[i*16:(i+1)*16], res1)
last_res = strxor(res1, res).encode('hex')
payload = (msg.encode('hex')+last_res).ljust(124,"a")+'27'
print payload
p.recvuntil("so send your message:\n")
p.sendline(payload)
p.recvuntil("and your code:\n")
p.sendline(c)
p.interactive()