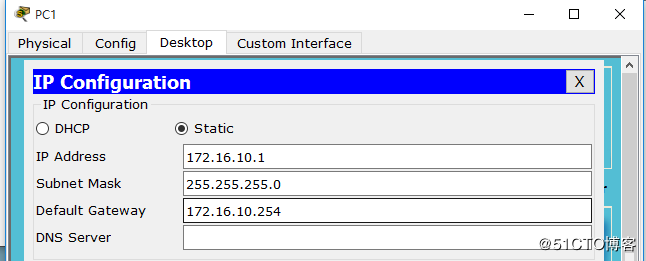
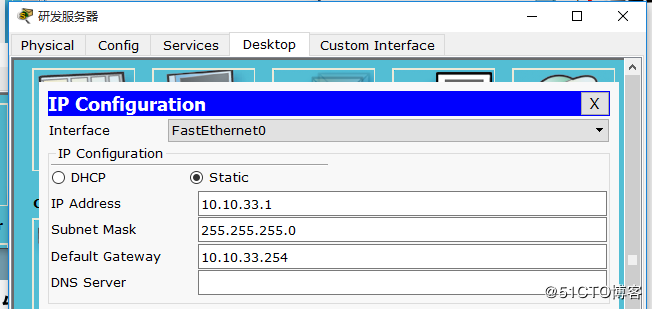
要求:
1. 研发小组可以通过×××访问总公司研发服务器,但不能访问internet
2. 分公司的其他客户端可以访问internet实验topo构想:
终端配置:
ip地址配置:
R0配置:
Router>enable
Router#conf t
Router(config)#no ip domain lookup
Router(config)#line console 0
Router(config-line)#exec-timeout 0
Router(config-line)#^Z
Router#conf t
Router(config)#hostname R0
R0(config)#inter f0/0
R0(config-if)#no shutdown
R0(config-if)#ip add 176.16.10.254 255.255.255.0
R0(config-if)#inter f0/1
R0(config-if)#no shutdown
R0(config-if)#ip address 172.16.20.254 255.255.255.0
R0(config)#inter f1/0
R0(config-if)#no shut
R0(config-if)#ip add 192.168.1.1 255.255.255.252
R0(config-if)#^Z
测试连通性:
R0#ping 172.16.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.10.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/3 ms
R0#ping 172.16.20.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.20.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
R1配置:
Router>en
Router#conf t
Router(config)#hostname R1
Router(config)#no ip domain lookup
R1(config)#line console 0
R1(config-line)#exec-timeout 0
R1(config-line)#exit
R1(config)#inter f0/1
R1(config-if)#no shutdown
R1(config-if)#ip add 192.168.1.2 255.255.255.252
R1(config-if)#inter f0/0
R1(config-if)#no shutdown
R1(config-if)#ip add 100.0.0.1 255.255.255.252
R1(config-if)#^Z
测试连通性:
R1#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
ISP配置:
Router>enable
Router#conf t
Router(config)#no ip domain lookup
Router(config)#hostname ISP
ISP(config)#line console 0
ISP(config-line)#exec-timeout 0
ISP(config-line)#^Z
ISP#conf t
ISP(config)#inter f0/1
ISP(config-if)#no shutdown
ISP(config-if)#ip address 100.0.0.2 255.255.255.252
ISP(config-if)#inter f0/0
ISP(config-if)#no shutdown
ISP(config-if)#ip add 200.0.0.1 255.255.255.252
ISP(config-if)#^Z
测试连通性:
ISP#ping 100.0.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 100.0.0.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
R2配置:
Router>enable
Router#conf t
Router(config)#hostname R2
R2(config)#no ip domain lookup
R2(config)#line console 0
R2(config-line)#exec-timeout 0
R2(config-line)#exit
R2(config)#inter f0/1
R2(config-if)#no shutdown
R2(config-if)#ip add 200.0.0.2 255.255.255.252
R2(config-if)#inter f0/0
R2(config-if)#no shutdown
R2(config-if)#ip add 10.10.33.254 255.255.255.0
R2(config-if)#^Z
测试连通性:
R2#ping 200.0.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.0.0.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
R2#ping 10.10.33.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.33.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/1/5 ms
配置路由:
R0#conf t
R0(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.2
R0(config)#^Z
R1#conf t
R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.1
R1(config)#ip route 0.0.0.0 0.0.0.0 100.0.0.2
R2#conf t
R2(config)#ip route 0.0.0.0 0.0.0.0 200.0.0.1
配置ISAKMP策略:
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encryption 3des
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
R1(config-isakmp)#exit
R1(config)#crypto isakmp key hahui address 200.0.0.2
R2#conf t
R2(config)#crypto isakmp policy 1
R2(config-isakmp)#encryption 3des
R2(config-isakmp)#hash sha
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#group 2
R2(config)#crypto isakmp key hahui address 100.0.0.1
配置ACL:
R1(config)#access-list 100 permit ip 172.16.10.0 0.0.0.255 10.10.33.0 0.0.0.255
R1(config)#ip nat inside source list 1 interface f0/0 overload
R1(config)#inter f0/0
R1(config-if)#ip nat outside
R1(config-if)#inter f0/1
R1(config-if)#ip nat inside
R1(config-if)#exit
R2(config)#access-list 100 permit ip 10.10.33.0 0.0.0.255 172.16.10.0 0.0.0.255
配置 IPSec 策略(转换集)
R1(config)#crypto ipsec transform-set hh-set ah-sha-hmac esp-des
R2(config)#crypto ipsec transform-set hh-set ah-sha-hmac esp-des
配置加密映射集
R1(config)#crypto map hh-map 1 ipsec-isakmp
R1(config-crypto-map)#set peer 200.0.0.2
R1(config-crypto-map)#set transform-set hh-set
R1(config-crypto-map)#match address 100
R2(config)#crypto map hh-map 1 ipsec-isakmp
R2(config-crypto-map)#set peer 100.0.0.1
R2(config-crypto-map)#set transform-set hh-set
R2(config-crypto-map)#match address 100
将映射集应用到接口
R1(config)#inter f0/0
R1(config-if)#crypto map hh-map
R2(config)#inter f0/1
R2(config-if)#crypto map hh-map
查看第一阶段状态:
首先要用 流量触发IPSec
R1#show crypto isakmp sa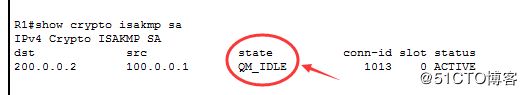
R2#show crypto isakmp sa
测试:

- 研发小组访问不了internet,可以访问研发服务器。
其他客户端就可以访问internet,就没有权限访问研发服务器了。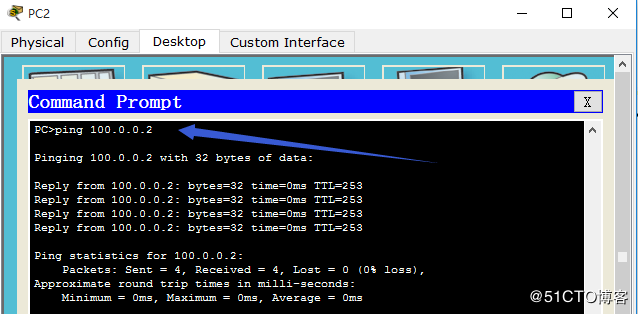
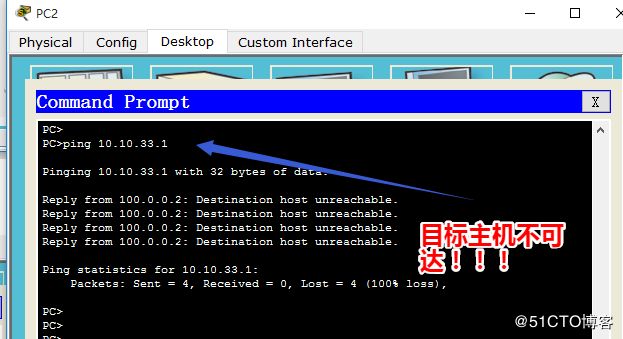
开启debug ip nat 查看地址是否转换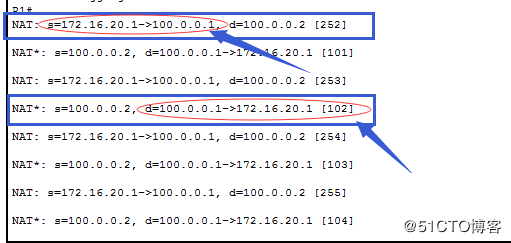
在R2上开启debug ip packet,观察包的信息,看看地址是否转换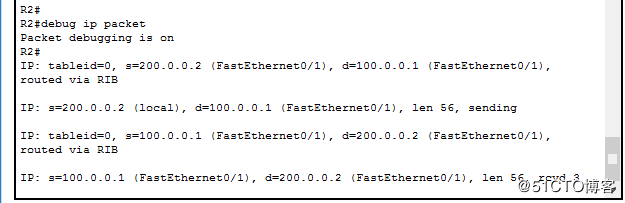
要求二:
1. 研发小组的流量走PAT,不走×××
2. 研发小组流量可以走PAT,也可以走×××具体配置步骤:
1. 研发小组的流量走PAT,不走×××(意思就是可以上网,不能访问研发服务器)在R1上添加配置:
R1(config)#access-list 1 permit 172.16.10.0 0.0.0.255
R1(config)#ip nat inside source list 1 interface f0/0 overload
测试:
查看地址转换
- 研发小组流量可以走PAT,也可以走×××(意思就是既可以上internet,还可以访问研发服务器:实际中,个人觉得很少有公司会这么做,因为要考虑到信息的安全性;通常就是只通过×××访问,如果还可以通过internet,那么***就可以在internet上轻松的截取信息)
R1添加配置:
要删除access-list 1 permit 172.16.10.0 0.0.0.255这条命令
R1(config)#no access-list 1 permit 172.16.10.0 0.0.0.255
R1(config)#access-list 110 deny ip 172.16.10.0 0.0.0.255 10.10.33.0 0.0.0.255
R1(config)#access-list 110 permit ip any any
R1(config)#ip nat inside source list 110 interface f0/0 overload
测试: