网络介绍
1、TCP三次握手四次端口
2、网络连接状态
3、netstat 和ss命令之间的比较
4、netstat命令详解
5、netstat命令使用场景
6、ss令详解
7、ss令使用场景
一、TCP三次握手四次断开详情过程
A、建立连接
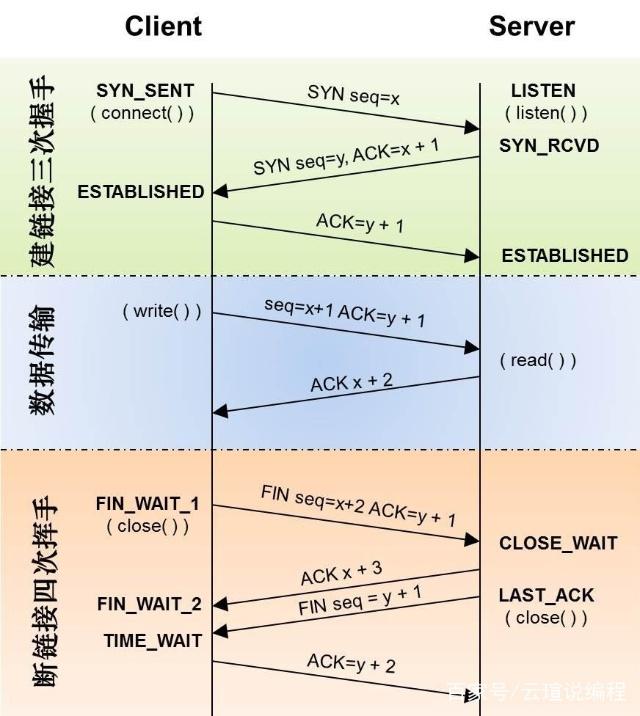
在TCP/IP协议中,TCP协议提供可靠的连接服务,采用三次握手建立一个连接,如图1所示。
(1)第一次握手:建立连接时,Client发送SYN包(SYN=j)到Server,并进入SYN_SEND状态,等待Server确认。
(2)第二次握手: Server收到SYN包,必须确认Client的SYN(ACK=j+1),同时自己也发送一个SYN包(SYN=k),即SYN+ACK包,此时Server进入SYN_RECV状态。
(3)第三次握手:Client收到Server的SYN+ACK包,向Server发送确认包ACK(ACK=k+1),此包发送完毕,Client和Server进入ESTABLISHED状态,完成三次握手。
完成三次握手,Clinet与Server开始传送数据.
B、数据传输
(1).超时重传超时重传机制用来保证TCP传输的可靠性。每次发送数据包时,发送的数据报都有seq号,接收端收到数据后,会回复ack进行确认,表示某一seq 号数据已经收到。发送方在发送了某个seq包后,等待一段时间,如果没有收到对应的ack回复,就会认为报文丢失,会重传这个数据包。
(2).快速重传接受数据一方发现有数据包丢掉了。就会发送ack报文告诉发送端重传丢失的报文。如果发送端连续收到标号相同的ack包,则会触发客户端的快速重 传。比较超时重传和快速重传,可以发现超时重传是发送端在傻等超时,然后触发重传;而快速重传则是接收端主动告诉发送端数据没收到,然后触发发送端重传。
(3).流量控制这里主要说TCP滑动窗流量控制。TCP头里有一个字段叫Window,又叫Advertised-Window,这个字段是接收端告诉发送端自己 还有多少缓冲区可以接收数据。于是发送端就可以根据这个接收端的处理能力来发送数据,而不会导致接收端处理不过来。 滑动窗可以是提高TCP传输效率的一种机制。
(4).拥塞控制滑动窗用来做流量控制。流量控制只关注发送端和接受端自身的状况,而没有考虑整个网络的通信情况。拥塞控制,则是基于整个网络来考虑的。考虑一下这 样的场景:某一时刻网络上的延时突然增加,那么,TCP对这个事做出的应对只有重传数据,但是,重传会导致网络的负担更重,于是会导致更大的延迟以及更多 的丢包,于是,这个情况就会进入恶性循环被不断地放大。试想一下,如果一个网络内有成千上万的TCP连接都这么行事,那么马上就会形成“网络风 暴”,TCP这个协议就会拖垮整个网络。为此,TCP引入了拥塞控制策略。拥塞策略算法主要包括:慢启动,拥塞避免,拥塞发生,快速恢复。
C、断开连接
由于TCP连接是全双工的,因此每个方向都必须单独进行关闭。这个原则是当一方完成它的数据发送任务后就能发送一个FIN来终止这个方向的连接。收到一个 FIN只意味着这一方向上没有数据流动,一个TCP连接在收到一个FIN后仍能发送数据。首先进行关闭的一方将执行主动关闭,而另一方执行被动关闭。
(1)Clinet发送一个FIN,用来关闭Client到Server的数据传送(报文段4)。
(2)Server收到这个FIN,它发回一个ACK,确认序号为收到的序号加1(报文段5)。和SYN一样,一个FIN将占用一个序号。
(3)Server关闭与Clinet的连接,发送一个FIN给Client(报文段6)。
(4)Client发回ACK报文确认,并将确认序号设置为收到序号加1(报文段7)。
二、网络连接状态
CLOSED 初始(无连接)状态。
LISTEN 侦听状态,等待远程机器的连接请求。
SYN_SEND 在TCP三次握手期间,主动连接端发送了SYN包后,进入SYN_SEND状态,等待对方的ACK包。
SYN_RECV 在TCP三次握手期间,主动连接端收到SYN包后,进入SYN_RECV状态。
ESTABLISHED 完成TCP三次握手后,主动连接端进入ESTABLISHED状态。此时,TCP连接已经建立,可以进行通信。
FIN_WAIT_1 在TCP四次挥手时,主动关闭端发送FIN包后,进入FIN_WAIT_1状态。
FIN_WAIT_2 在TCP四次挥手时,主动关闭端收到ACK包后,进入FIN_WAIT_2状态。
TIME_WAIT 在TCP四次挥手时,主动关闭端发送了ACK包之后,进入TIME_WAIT状态,等待最多MSL时间,让被动关闭端收到ACK包。
CLOSING 在TCP四次挥手期间,主动关闭端发送了FIN包后,没有收到对应的ACK包,却收到对方的FIN包,此时,进入CLOSING状态。
CLOSE_WAIT 在TCP四次挥手期间,被动关闭端收到FIN包后,进入CLOSE_WAIT状态。
LAST_ACK 在TCP四次挥手时,被动关闭端发送FIN包后,进入LAST_ACK状态,等待对方的ACK包。
主动连接端可能的状态有: CLOSED SYN_SEND ESTABLISHED
主动关闭端可能的状态有: FIN_WAIT_1 FIN_WAIT_2 TIME_WAIT
被动连接端可能的状态有: LISTEN SYN_RECV ESTABLISHED
被动关闭端可能的状态有: CLOSE_WAIT LAST_ACK CLOSED
三、netstat 和ss命令之间的比较
查看服务器连接数一般都会用netstat命令。其实,有一个命令比netstat更高效,那就是ss(Socket Statistics)命令!
ss命令可以用来获取socket统计信息,它可以显示和netstat类似的内容。
ss的优势在于它能够显示更多更详细的有关TCP和连接状态的信息,而且比netstat更快速更高效。原因如下:
A、当服务器的socket连接数量变得非常大时,无论是使用netstat命令还是直接cat /proc/net/tcp,执行速度都会很慢。可能你不会有切身的感受,但请相信我,当服务器维持的连接达到上万个的时候,使用 netstat等于浪费 生命,而用ss才是节省时间。
B、而ss快的秘诀在于它利用到了TCP协议栈中tcp_diag。tcp_diag是一个用于分析统计的模块,可以获得Linux内核中第一手的信息,这就确保了ss的快捷高效。当然,如果你的系统中没有tcp_diag,ss也可 以正常运行,只是效率会变得稍慢(但仍然比 netstat要快)。
四、netstat命令详解
- netstat 命令:用于显示各种网络相关信息,如网络连接,路由表,接口状态,无效连接,组播成员 等等。
- netstat命令是net-tools软件包中的一员
netstat五大作用:显示网络详情、显示路由详情、显示接口统计信息、显示无效连接信息、显示组播成员信息
语法: netstat [-acCeFghilMnNoprstuvVwx][-A<网络类型>][--ip] 选项: -a或--all 显示所有连线中的Socket。 -A<网络类型>或--<网络类型> 列出该网络类型连线中的相关地址。 -c或--continuous 持续列出网络状态。 -C或--cache 显示路由器配置的快取信息。 -e或--extend 显示网络其他相关信息。 -F或--fib 显示FIB。 -g或--groups 显示多重广播功能群组组员名单。 -h或--help 在线帮助。 -i或--interfaces 显示网络界面信息表单。 -l或--listening 显示监控中的服务器的Socket。 -M或--masquerade 显示伪装的网络连线。 -n或--numeric 直接使用IP地址,而不通过域名服务器。 -N或--netlink或--symbolic 显示网络硬件外围设备的符号连接名称。 -o或--timers 显示计时器。 -p或--programs 显示正在使用Socket的程序识别码和程序名称。 -r或--route 显示Routing Table。 -s或--statistice 显示网络工作信息统计表。 -t或--tcp 显示TCP传输协议的连线状况。 -u或--udp 显示UDP传输协议的连线状况。 -v或--verbose 显示指令执行过程。 -V或--version 显示版本信息。 -w或--raw 显示RAW传输协议的连线状况。 -x或--unix 此参数的效果和指定"-A unix"参数相同。 --ip或--inet 此参数的效果和指定"-A inet"参数相同。
五、使用场景
1、netstat -ant 显示所有的tcp连接,并以数字的方式显示。
[admin@AY130828191306Z ~]$ netstat -ant Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 127.0.0.1:32000 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN tcp 0 0 10.139.32.237:5667 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:970 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 10.139.32.237:10050 10.253.117.176:48461 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:64834 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:14458 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:61812 TIME_WAIT tcp 0 0 10.139.32.237:58553 10.253.164.85:4505 ESTABLISHED tcp 0 0 10.139.32.237:10050 10.253.117.176:45595 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:23838 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:62522 TIME_WAIT tcp 0 0 127.0.0.1:32000 127.0.0.1:31000 ESTABLISHED tcp 0 0 10.139.32.237:10050 10.253.117.176:11306 TIME_WAIT tcp 0 0 127.0.0.1:31000 127.0.0.1:32000 ESTABLISHED tcp 0 0 10.139.32.237:10050 10.253.117.176:46545 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:47821 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:22213 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:23015 TIME_WAIT tcp 0 0 10.139.32.237:37287 10.253.2.123:4505 ESTABLISHED tcp 0 2792 10.139.32.237:22 10.139.0.113:9321 ESTABLISHED tcp 0 0 10.139.32.237:10050 10.253.117.176:56509 TIME_WAIT tcp 0 0 10.139.32.237:10050 10.253.117.176:64177 TIME_WAIT tcp 0 0 10.139.32.237:55475 100.100.45.131:80 ESTABLISHED tcp 0 0 10.139.32.237:40416 10.139.32.238:22 TIME_WAIT
2、netstat -aun 显示所有udp连接信息
[admin@AY130828191306Z ~]$ netstat -aut Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 localhost:32000 *:* LISTEN tcp 0 0 *:zabbix-agent *:* LISTEN tcp 0 0 AY130828191306Z:5667 *:* LISTEN tcp 0 0 *:mysql *:* LISTEN tcp 0 0 *:970 *:* LISTEN tcp 0 0 *:sunrpc *:* LISTEN tcp 0 0 192.168.122.1:domain *:* LISTEN tcp 0 0 *:ssh *:* LISTEN tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:52061 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:29297 TIME_WAIT tcp 0 0 AY130828191306Z:58553 10.253.164.85:4505 ESTABLISHED tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:28773 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:48742 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:27151 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:43780 TIME_WAIT tcp 0 0 localhost:32000 localhost:31000 ESTABLISHED tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:57150 TIME_WAIT tcp 0 0 localhost:31000 localhost:32000 ESTABLISHED tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:10731 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:53731 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:51615 TIME_WAIT tcp 0 0 AY130828191306Z:37287 10.253.2.123:4505 ESTABLISHED tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:64397 TIME_WAIT tcp 0 2508 AY130828191306Z:ssh 10.139.0.113:guibase ESTABLISHED tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:49537 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:64898 TIME_WAIT tcp 0 0 AY130828191306:zabbix-agent 10.253.117.176:27835 TIME_WAIT tcp 0 0 AY130828191306Z:55475 100.100.45.131:http ESTABLISHED tcp 0 0 AY130828191306Z:40561 10.139.32.238:ssh TIME_WAIT tcp 32 0 AY130828191306Z:39544 100.100.98.18:squid CLOSE_WAIT udp 0 0 *:syslog *:* udp 0 0 192.168.122.1:domain *:*
3、netstat -tnl 显示处于监听状态的tcp连接。
[admin@AY130828191306Z ~]$ netstat -tnl Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 127.0.0.1:32000 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN tcp 0 0 10.139.32.237:5667 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:970 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
4、netstat -unl 显示处于监听状态的udp连接。
[admin@AY130828191306Z ~]$ netstat -unl Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State udp 0 0 0.0.0.0:514 0.0.0.0:* udp 0 0 192.168.122.1:53 0.0.0.0:* udp 0 0 0.0.0.0:67 0.0.0.0:* udp 0 0 0.0.0.0:964 0.0.0.0:* udp 0 0 0.0.0.0:967 0.0.0.0:* udp 0 0 0.0.0.0:57180 0.0.0.0:* udp 0 0 0.0.0.0:5353 0.0.0.0:* udp 0 0 0.0.0.0:111 0.0.0.0:* udp 0 0 121.199.131.204:123 0.0.0.0:* udp 0 0 10.139.32.237:123 0.0.0.0:* udp 0 0 127.0.0.1:123 0.0.0.0:* udp 0 0 0.0.0.0:123 0.0.0.0:*
5、netstat -tnle 列出所有tcp连接的信息,以扩展格式显示。
[admin@AY130828191306Z ~]$ netstat -tnle Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State User Inode tcp 0 0 127.0.0.1:32000 0.0.0.0:* LISTEN 0 4717 tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN 509 6250 tcp 0 0 10.139.32.237:5667 0.0.0.0:* LISTEN 500 6186 tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN 503 6655 tcp 0 0 0.0.0.0:970 0.0.0.0:* LISTEN 0 4460 tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 0 4222 tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 0 6572 tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 0 5936
6、netstat -tnlp 列出所有tcp连接的信息,并显示其相关的进行和PID(进程号)。
[root@OM-SERVER ~]# netstat -tnlp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:3690 0.0.0.0:* LISTEN 4513/svnserve tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN 1199/master tcp 0 0 0.0.0.0:5901 0.0.0.0:* LISTEN 1108/Xvnc tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 1/systemd tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 20208/nginx: master tcp 0 0 0.0.0.0:6001 0.0.0.0:* LISTEN 1108/Xvnc tcp 0 0 0.0.0.0:465 0.0.0.0:* LISTEN 1199/master tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 10821/sshd tcp 0 0 127.0.0.1:8182 0.0.0.0:* LISTEN 1222/DragoonAgent tcp 0 0 10.253.10.173:8182 0.0.0.0:* LISTEN 1222/DragoonAgent tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 1199/master tcp 0 0 0.0.0.0:41344 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:18082 0.0.0.0:* LISTEN 1093/java tcp 0 0 127.0.0.1:15778 0.0.0.0:* LISTEN 1221/DragoonAgent tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN 992/zabbix_agentd tcp6 0 0 :::3306 :::* LISTEN 2875/mysqld tcp6 0 0 :::587 :::* LISTEN 1199/master tcp6 0 0 :::5901 :::* LISTEN 1108/Xvnc tcp6 0 0 :::111 :::* LISTEN 11185/rpcbind tcp6 0 0 :::6001 :::* LISTEN 1108/Xvnc tcp6 0 0 :::465 :::* LISTEN 1199/master tcp6 0 0 :::3128 :::* LISTEN 16938/(squid-1) tcp6 0 0 :::3000 :::* LISTEN 2341/grafana-server tcp6 0 0 :::25 :::* LISTEN 1199/master tcp6 0 0 :::37950 :::* LISTEN - tcp6 0 0 :::10050 :::* LISTEN 992/zabbix_agentd tcp6 0 0 :::1988 :::* LISTEN 955/falcon-agent
7、netstat -tanc 持续显示tcp连接信息。
[root@OM-SERVER ~]# netstat -tanc Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:3690 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:587 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:5901 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:6001 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:465 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:8182 0.0.0.0:* LISTEN tcp 0 0 10.253.10.173:8182 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:41344 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:18082 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:15778 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN tcp 0 0 121.41.141.185:54808 106.11.61.112:443 TIME_WAIT tcp 0 0 10.253.10.173:54972 10.91.32.210:2049 ESTABLISHED tcp 0 0 121.41.141.185:56550 106.11.61.111:80 TIME_WAIT tcp 0 0 10.253.10.173:44912 10.157.220.10:80 TIME_WAIT tcp 0 0 10.253.10.173:50438 10.157.201.5:80 TIME_WAIT tcp 0 0 10.253.10.173:44964 10.157.220.10:80 ESTABLISHED tcp 0 0 10.253.10.173:34036 100.112.45.163:514 ESTABLISHED tcp 0 0 10.253.10.173:44954 10.157.220.10:80 TIME_WAIT tcp 0 0 10.253.10.173:38482 10.253.2.123:4505 ESTABLISHED tcp 0 52 10.253.10.173:22 10.139.0.113:9130 ESTABLISHED tcp 0 0 10.253.10.173:60058 100.112.17.225:8433 ESTABLISHED tcp 0 0 127.0.0.1:51136 127.0.0.1:1988 ESTABLISHED tcp 0 0 127.0.0.1:51084 127.0.0.1:1988 TIME_WAIT tcp 32 0 121.41.141.185:37642 52.74.223.119:443 CLOSE_WAIT tcp 0 0 121.41.141.185:37644 52.74.223.119:443 ESTABLISHED tcp 0 0 10.253.10.173:58342 10.253.10.173:3306 TIME_WAIT tcp 0 0 10.253.10.173:48284 100.100.45.131:80 ESTABLISHED tcp 0 0 10.253.10.173:44132 100.112.44.78:6030 ESTABLISHED tcp 0 0 10.253.10.173:44940 10.157.220.10:80 TIME_WAIT
8、netstat -nr 显示路由信息类似 route -n
![]() View Code
View Code
9、netsat -g 显示组播关系
[root@OM-SERVER ~]# netstat -s Ip: 1086524721 total packets received 598 with invalid addresses 0 forwarded 2 with unknown protocol 0 incoming packets discarded 1086524121 incoming packets delivered 481829682 requests sent out 824 dropped because of missing route Icmp: 19719 ICMP messages received 18 input ICMP message failed. ICMP input histogram: destination unreachable: 62 timeout in transit: 785 echo requests: 22 echo replies: 18837 timestamp reply: 13 49091 ICMP messages sent 0 ICMP messages failed ICMP output histogram: destination unreachable: 956 echo request: 47780 echo replies: 22 IcmpMsg: InType0: 18837 InType3: 62 InType8: 22 InType11: 785 InType14: 13 OutType0: 22 OutType3: 956 OutType8: 47780 OutType69: 333 Tcp: 5400368 active connections openings 285584395 passive connection openings 14750393 failed connection attempts 284829270 connection resets received 11 connections established 1079307801 segments received 614091658 segments send out 5999180 segments retransmited 498 bad segments received. 26355414 resets sent Udp: 7195631 packets received 947 packets to unknown port received. 0 packet receive errors 7200550 packets sent 0 receive buffer errors 0 send buffer errors UdpLite: TcpExt: 14232789 resets received for embryonic SYN_RECV sockets 127229 packets pruned from receive queue because of socket buffer overrun 7 ICMP packets dropped because socket was locked 2126326 TCP sockets finished time wait in fast timer 139 packets rejects in established connections because of timestamp 1435052 delayed acks sent 603 delayed acks further delayed because of locked socket Quick ack mode was activated 63629 times 5218729 packets directly queued to recvmsg prequeue. 75812785 bytes directly in process context from backlog 3504713219 bytes directly received in process context from prequeue 41750397 packet headers predicted 4465349 packets header predicted and directly queued to user 336853129 acknowledgments not containing data payload received 44778004 predicted acknowledgments 81042 times recovered from packet loss by selective acknowledgements Detected reordering 802 times using FACK Detected reordering 171024 times using SACK Detected reordering 200 times using time stamp 368 congestion windows fully recovered without slow start 345 congestion windows partially recovered using Hoe heuristic 9405 congestion windows recovered without slow start by DSACK 16542 congestion windows recovered without slow start after partial ack TCPLostRetransmit: 6256 2181 timeouts after SACK recovery 2269 timeouts in loss state 3697706 fast retransmits 182811 forward retransmits 1086390 retransmits in slow start 861638 other TCP timeouts TCPLossProbes: 88780 TCPLossProbeRecovery: 10722 18326 SACK retransmits failed 65960246 packets collapsed in receive queue due to low socket buffer 63758 DSACKs sent for old packets 60 DSACKs sent for out of order packets 197271 DSACKs received 1644 DSACKs for out of order packets received 9666 connections reset due to unexpected data 1213 connections reset due to early user close 7521 connections aborted due to timeout TCPDSACKIgnoredOld: 4700 TCPDSACKIgnoredNoUndo: 14000 TCPSpuriousRTOs: 281 TCPSackShifted: 3134190 TCPSackMerged: 9680004 TCPSackShiftFallback: 1366927 TCPBacklogDrop: 293 TCPRetransFail: 297 TCPRcvCoalesce: 17221483 TCPOFOQueue: 503601 TCPOFOMerge: 60 TCPChallengeACK: 601 TCPSYNChallenge: 507 TCPSpuriousRtxHostQueues: 352 TCPAutoCorking: 2559504 TCPFromZeroWindowAdv: 14888 TCPToZeroWindowAdv: 14888 TCPWantZeroWindowAdv: 209240 TCPSynRetrans: 863286 TCPOrigDataSent: 235904965 TCPHystartTrainDetect: 424092 TCPHystartTrainCwnd: 6938815 TCPHystartDelayDetect: 2392 TCPHystartDelayCwnd: 374902 TCPACKSkippedSynRecv: 39 TCPACKSkippedPAWS: 128 TCPACKSkippedSeq: 3036 TCPWinProbe: 547 TCPKeepAlive: 158556 IpExt: InOctets: 295672544761 OutOctets: 317805584636 InNoECTPkts: 1202642152 InECT1Pkts: 1 InECT0Pkts: 117401 InCEPkts: 2
10、netstat -ap显示程序所对应端口
[root@OM-SERVER ~]# netstat -ap Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:svn 0.0.0.0:* LISTEN 4513/svnserve tcp 0 0 0.0.0.0:submission 0.0.0.0:* LISTEN 1199/master tcp 0 0 0.0.0.0:5901 0.0.0.0:* LISTEN 1108/Xvnc tcp 0 0 0.0.0.0:sunrpc 0.0.0.0:* LISTEN 1/systemd tcp 0 0 0.0.0.0:http 0.0.0.0:* LISTEN 20208/nginx: master tcp 0 0 0.0.0.0:6001 0.0.0.0:* LISTEN 1108/Xvnc tcp 0 0 0.0.0.0:urd 0.0.0.0:* LISTEN 1199/master tcp 0 0 0.0.0.0:ssh 0.0.0.0:* LISTEN 10821/sshd tcp 0 0 localhost:vmware-fdm 0.0.0.0:* LISTEN 1222/DragoonAgent
11、netstat结合其他命令使用
查看所有80端口的连接数 netstat -nat|grep -i "80" |wc -l 对连接的IP按连接数量进行排序 netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n 查看TCP连接状态 netstat -nat |awk '{print $6}'|sort|uniq -c|sort -rn netstat -an | awk '/^tcp/ {++S[$NF]};END {for(a in S) print a, S[a]}' netstat -an | awk '/^tcp/ {++state[$NF]}; END {for(key in state) print key,"\t",state[key]}' netstat -an | awk '/^tcp/ {++arr[$NF]};END {for(k in arr) print k,"\t",arr[k]}' netstat -an |awk '/^tcp/ {print $NF}'|sort|uniq -c|sort -rn netstat -ant | awk '{print $NF}' | grep -v '[a-z]' | sort | uniq -c 查看80端口连接数最多的20个IP netstat -ant |awk '/:80/{split($5,ip,":");++A[ip[1]]}END{for(i in A) print A[i],i}' |sort -rn|head -n20 查找较多time_wait连接 netstat -n|grep TIME_WAIT|awk '{print $5}'|sort|uniq -c|sort -rn|head -n20 查找较多的SYN连接 netstat -an | grep SYN | awk '{print $5}' | awk -F: '{print $1}' | sort | uniq -c | sort -nr | more
六、ss命令详解
ss是Socket Statistics的缩写
- ss命令可以用来获取socket统计信息,它可以显示和netstat类似的内容。但是ss的优势在于它能够显示更详细的有关网络连接的状态信息,而比netstat更快速、更高效。
- ss命令是iproute2软件包中的一
- Usage: ss [ OPTIONS ] ss [ OPTIONS ] [ FILTER ]
- -h, --help this message #显示帮助菜单
- -V, --version output version information #输出版本信息
- -n, --numeric don't resolve service names #不解析服务名
- -r, --resolve resolve host names #解析主机名
- -a, --all display all sockets #显示所有的套接字
- -l, --listening display listening sockets #显示监听状态的socket
- -o, --options show timer information #显示计时器信息
- -e, --extended show detailed socket information #展示详细的socket信息
- -m, --memory show socket memory usage #展示socket的内存使用
- -p, --processes show process using socket #展示使用socket的进程
- -i, --info show internal TCP information #展示tcp内部信息
- -s, --summary show socket usage summary #展示socket使用汇总
- -4, --ipv4 display only IP version 4 sockets #只显示ipv4的sockets
- -6, --ipv6 display only IP version 6 sockets #只显示ipv6的sockets
- -0, --packet display PACKET sockets #显示包经过的网络接口
- -t, --tcp display only TCP sockets #显示tcp套接字
- -u, --udp display only UDP sockets #显示udp套接字
- -d, --dccp display only DCCP sockets #显示dccp套接字
- -w, --raw display only RAW sockets #显示raw套接字
- -x, --unix display only Unix domain sockets #显示unix套接字
- -f, --family=FAMILY display sockets of type FAMILY #显示指定类型的套接字
- -A, --query=QUERY, --socket=QUERY #查看某种类型 QUERY := {all|inet|tcp|udp|raw|unix|packet|netlink}[,QUERY]
- -D, --diag=FILE Dump raw information about TCP sockets to FILE #将关于TCP套接字的原始信息转储到文件中
- -F, --filter=FILE read filter information from FILE #使用此参数指定的过滤规则文件,过滤某种状态的连接
- FILTER := [ state STATE-FILTER ] [ EXPRESSION ]
- STATE-FILTER := {all|connected|synchronized|bucket|big|TCP-STATES}
- TCP-STATES := {established|syn-sent|syn-recv|fin-wait-{1,2}|time-wait|closed|close-wait|last-ack|listen|closing}
- connected := {established|syn-sent|syn-recv|fin-wait-{1,2}|time-wait|close-wait|last-ack|closing}
- synchronized := {established|syn-recv|fin-wait-{1,2}|time-wait|close-wait|last-ack|closing}
- bucket := {syn-recv|time-wait}
- big := {established|syn-sent|fin-wait-{1,2}|closed|close-wait|last-ack|listen|closing}
六、使用场景
1、ss -s 显示sockets简要信息
列出当前已经连接,关闭,等待的tcp连接
[root@iZbp10h3aahazrus0tk312Z ~]# ss -s Total: 2704 (kernel 2869) TCP: 2392 (estab 697, closed 72, orphaned 0, synrecv 0, timewait 71/0), ports 0 Transport Total IP IPv6 * 2869 - - RAW 5 5 0 UDP 3 2 1 TCP 2320 522 1798 INET 2328 529 1799 FRAG 0 0 0
2、ss -l 列出监听端口
[root@OM-SERVER ~]# ss -l | less Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port nl UNCONN 0 0 rtnl:ntpd/12548 * nl UNCONN 0 0 rtnl:firefox/1543 * nl UNCONN 0 0 rtnl:kernel * nl UNCONN 0 0 rtnl:ntpd/12548 * nl UNCONN 0 0 rtnl:firefox/1543 * nl UNCONN 0 0 tcpdiag:AliYunDun/26337 * nl UNCONN 768 0 tcpdiag:kernel * nl UNCONN 4352 0 tcpdiag:ss/25788 * nl UNCONN 0 0 xfrm:kernel * nl UNCONN 0 0 selinux:kernel * nl UNCONN 0 0 audit:kernel * nl UNCONN 0 0 audit:systemd/1 * nl UNCONN 0 0 fiblookup:kernel * nl UNCONN 164352 0 connector:1581 * nl UNCONN 0 0 connector:kernel * nl UNCONN 164352 0 connector:14635 * nl UNCONN 0 0 connector:AliYunDun/26337 * nl UNCONN 0 0 connector:AliYunDun/26337 * nl UNCONN 164352 0 connector:14635 * nl UNCONN 164352 0 connector:1581 * nl UNCONN 0 0 uevent:systemd-logind/525 * nl UNCONN 0 0 uevent:kernel * nl UNCONN 0 0 uevent:-1482169911 * nl UNCONN 0 0 uevent:-646189470 *
3、ss -pl 列出进程名和监听端口
[root@OM-SERVER ~]# ss -pl | less Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port nl UNCONN 0 0 rtnl:ntpd/12548 * nl UNCONN 0 0 rtnl:firefox/1543 * nl UNCONN 0 0 rtnl:kernel * nl UNCONN 0 0 rtnl:ntpd/12548 * nl UNCONN 0 0 rtnl:firefox/1543 * nl UNCONN 0 0 tcpdiag:AliYunDun/26337 * nl UNCONN 768 0 tcpdiag:kernel * nl UNCONN 4352 0 tcpdiag:ss/26710 * nl UNCONN 0 0 xfrm:kernel * nl UNCONN 0 0 selinux:kernel * nl UNCONN 0 0 audit:kernel * nl UNCONN 0 0 audit:systemd/1 * nl UNCONN 0 0 fiblookup:kernel * nl UNCONN 164352 0 connector:1581 * nl UNCONN 0 0 connector:kernel * nl UNCONN 164352 0 connector:14635 * nl UNCONN 0 0 connector:AliYunDun/26337 * nl UNCONN 0 0 connector:AliYunDun/26337 *
4、ss -at列所有的tcp sockets
5、ss -au列出所有udp sockets
6、ss使用的state状态
STATE-FILTER := {all|connected|synchronized|bucket|big|TCP-STATES}
TCP-STATES := {established|syn-sent|syn-recv|fin-wait-{1,2}|time-wait|closed|close-wait|last-ack|listen|closing}
connected := {established|syn-sent|syn-recv|fin-wait-{1,2}|time-wait|close-wait|last-ack|closing}
synchronized := {established|syn-recv|fin-wait-{1,2}|time-wait|close-wait|last-ack|closing}
bucket := {syn-recv|time-wait}
big := {established|syn-sent|fin-wait-{1,2}|closed|close-wait|last-ack|listen|closing}
7、ss -o state established '(dport= :http or sport= :http)' 列出所有http连接中的连接
8、ss -o state fin-wait-1 '(sport= :http or sport= :https)' 列出处在FIN-WAIT-1状态的http、https连接
9、ss使用IP地址筛选
ss
src:表示来源
dst: 表示目录
ADDRESS_PATTERN:表示地址规则
[root@AY130828191306Z ~]# hostname -i 10.139.32.237 [root@AY130828191306Z ~]# ss dst 10.253.10.173 State Recv-Q Send-Q Local Address:Port Peer Address:Port ESTAB 0 0 10.139.32.237:ssh 10.253.10.173:37244 [root@AY130828191306Z ~]# ss src 10.139.32.237 State Recv-Q Send-Q Local Address:Port Peer Address:Port ESTAB 0 0 10.139.32.237:58553 10.253.164.85:4505 ESTAB 0 0 10.139.32.237:ssh 10.253.10.173:37244 ESTAB 0 0 10.139.32.237:37287 10.253.2.123:4505 ESTAB 0 0 10.139.32.237:55475 100.100.45.131:http [root@AY130828191306Z ~]#
10、使用端口筛选
ss
OP:是运算符
sport:源端口
dport:目标端口
PORT: 表示端口
OP运算符如下
- <= or le 小于等于
- >= or ge 大于等于
- == or eq 等于
- != or ne 不等于
- < or lt 小于
- > or gt 大于
指定端口或者使用知名端口一样 [root@OM-SERVER ~]# ss dport = :80 Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port tcp ESTAB 0 0 10.253.10.173:48284 100.100.45.131:http tcp ESTAB 0 0 10.253.10.173:48140 10.157.220.10:http [root@OM-SERVER ~]# ss dport = :http Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port tcp ESTAB 0 0 10.253.10.173:48284 100.100.45.131:http tcp ESTAB 0 0 10.253.10.173:48140 10.157.220.10:http [root@OM-SERVER ~]# ss dport \< 1024 Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port u_str ESTAB 0 0 * 21191 * 0 udp ESTAB 0 0 10.253.10.173:44501 10.139.100.165:domain udp ESTAB 0 0 10.253.10.173:54934 10.139.32.152:domain udp ESTAB 0 0 10.253.10.173:45176 10.139.100.165:domain udp ESTAB 0 0 10.253.10.173:33386 10.139.100.165:domain udp ESTAB 0 0 10.253.10.173:56032 10.139.32.152:domain [root@OM-SERVER ~]# ss dport le 1024 Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port u_str ESTAB 0 0 * 21191 * 0 udp ESTAB 0 0 10.253.10.173:44501 10.139.100.165:domain udp ESTAB 0 0 10.253.10.173:54934 10.139.32.152:domain udp ESTAB 0 0 10.253.10.173:45176 10.139.100.165:domain udp ESTAB 0 0 10.253.10.173:33386 10.139.100.165:domain udp ESTAB 0 0 10.253.10.173:56032 10.139.32.152:domain
11、 显示目的端口是443或80的套接字
[root@OM-SERVER ~]# ss -at '( dst :443 or dst :80 )' 注意空格的使用 State Recv-Q Send-Q Local Address:Port Peer Address:Port TIME-WAIT 0 0 10.253.10.173:48648 10.157.220.10:http TIME-WAIT 0 0 10.253.10.173:48666 10.157.220.10:http ESTAB 0 0 10.253.10.173:48680 10.157.220.10:http TIME-WAIT 0 0 10.253.10.173:48636 10.157.220.10:http CLOSE-WAIT 32 0 121.41.141.185:37642 52.74.223.119:https ESTAB 0 0 121.41.141.185:37644 52.74.223.119:https ESTAB 0 0 10.253.10.173:48284 100.100.45.131:http ESTAB 0 0 121.41.141.185:45512 35.241.23.245:https
12、显示所有源端口或目的端口为 ssh 的套接字
[root@OM-SERVER ~]# ss -at '( dport = :ssh or sport = :ssh )' State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:ssh *:* ESTAB 0 52 10.253.10.173:ssh 10.139.0.113:18626 ESTAB 0 0 10.253.10.173:ssh 10.139.0.113:9130 ESTAB 0 0 10.253.10.173:49526 10.253.165.96:ssh ESTAB 0 0 10.253.10.173:ssh 10.139.0.118:55482