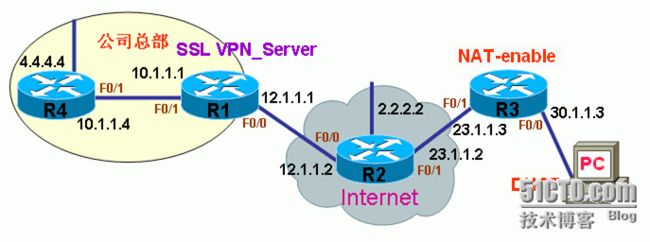
(1)将SSL ××× client模块传至路由器:
R1#dir
R1#
说明:本实验已经将SSL ××× client模块(sslclient-win-1.1.0.154.pkg)上传至路由器,如果需要,可以通过以下地址进行下载:
http://www.china-ccie.com/download/sslclient/sslclient.rar
(2)安装SSL ××× client模块:
R1(config)#web*** install svc disk0:sslclient-win-1.1.0.154.pkg
SSL××× Package SSL-×××-Client : installed successfully
(3)配置自动分配给用户的地址池:
R1(config)#ip local pool ccie 100.1.1.100 100.1.1.200
说明:自动分配给用户的地址范围是100.1.1.100 -100.1.1.200。
(4)为地址池网段创建loopback:
R1(config)#int loopback 100
R1(config-if)#ip add 100.1.1.1 255.255.255.0
R1(config-if)#exit
说明:当地址池不是自身直连网段时,必须创建同网段的loopback接口。
(5)配置SSL ×××参数:
R1(config)#web*** gateway chinaccie
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
R1(config-web***-gateway)#
*Nov 7 22:44:58.159: %SSH-5-ENABLED: SSH 1.99 has been enabled
*Nov 7 22:44:59.315: %PKI-4-NOAUTOSAVE: Configuration was modified. Issue "write memory" to save new certificate
R1(config-web***-gateway)#ip address 12.1.1.1 port 443
R1(config-web***-gateway)#inservice
R1(config-web***-gateway)#exit
说明:定义标识名字,开启的地址,端口等等。
(6)定义其它参数,以及组策略:
R1(config)#web*** context cisco
R1(config-web***-context)#gateway chinaccie domain cisco
R1(config-web***-context)#inservice
*Nov 7 22:46:41.651: %SSL×××-5-UPDOWN: ssl*** context : cisco changed state to UP
R1(config-web***-context)#policy group mygroup
R1(config-web***-group)#functions svc-enabled
R1(config-web***-group)#svc address-pool ccie
R1(config-web***-group)#exit
R1(config-web***-context)#default-group-policy mygroup
R1(config-web***-context)#exit
说明:定义用户组策略,地址池等等。
(7)定义用来认证的账户:
R1(config)#username chinaccie password chinaccie
1.配置基础网络环境(1)配置ASA:
ciscoasa(config)# int e0/0
ciscoasa(config-if)# ip add 12.1.1.1 255.255.255.0
ciscoasa(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# exit
ciscoasa(config)# int e0/1
ciscoasa(config-if)# ip add 10.1.1.1 255.255.255.0
ciscoasa(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# exit
ciscoasa(config)# route inside 4.4.4.4 255.255.255.255 10.1.1.4
ciscoasa(config)# route outside 0 0 12.1.1.2
ciscoasa(config)#
说明:配置ASA的接口地址,并写指向R4的Loopback地址4.4.4.4的路由,同时写默认路由指向Internet(路由器R2),地址12.1.1.2
说明:本实验已经将SSL ××× client模块(anyconnect-win-2.3.0185-k9.pkg)上传至ASA,如果需要,可以通过以下地址进行下载:
http://www.china-ccie.com/download/sslclient/anyconnect-win-2.3.0185-k9.rar
(2)开启SSL ×××并安装client模块:
ciscoasa(config)# web***
ciscoasa(config-web***)# enable outside
INFO: Web××× and DTLS are enabled on 'outside'.
ciscoasa(config-web***)# svc p_w_picpath disk0:/anyconnect-win-2.3.0185-k9.pkg
ciscoasa(config-web***)# svc enable
ciscoasa(config-web***)# tunnel-group-list enable
ciscoasa(config-web***)# exit
(3)配置自动分配给用户的地址池:
ciscoasa(config)# ip local pool ccie 100.1.1.100-100.1.1.200 mask 255.255.255.0
(4)定义隧道分离网段:
ciscoasa(config)# access-list split-ssl extended permit ip 10.1.1.0 255.255.255.0 any ciscoasa(config)# access-list split-ssl extended permit ip 4.4.4.4 255.255.255.255 any
(5)定义组策略属性:
ciscoasa(config)# group-policy SSLCLientPolicy internal
ciscoasa(config)# group-policy SSLCLientPolicy attributes
ciscoasa(config-group-policy)# address-pools value ccie
ciscoasa(config-group-policy)# dns-server value 202.96.209.133
ciscoasa(config-group-policy)# default-domain value cisco.com
ciscoasa(config-group-policy)# ***-tunnel-protocol svc
ciscoasa(config-group-policy)# split-tunnel-policy tunnelspecified
ciscoasa(config-group-policy)# split-tunnel-network-list value split-ssl
ciscoasa(config-group-policy)# exit
(6)定义隧道策略属性:
ciscoasa(config)# tunnel-group mygroup type remote-access
ciscoasa(config)# tunnel-group mygroup general-attributes
ciscoasa(config-tunnel-general)# default-group-policy SSLCLientPolicy
ciscoasa(config-tunnel-general)# tunnel-group mygroup web***-attributes
ciscoasa(config-tunnel-web***)# group-alias mygroup enable
ciscoasa(config-tunnel-web***)# exit
(7)定义用来认证的账户:
ciscoasa(config)# username chinaccie password chinaccie