一、实验拓扑: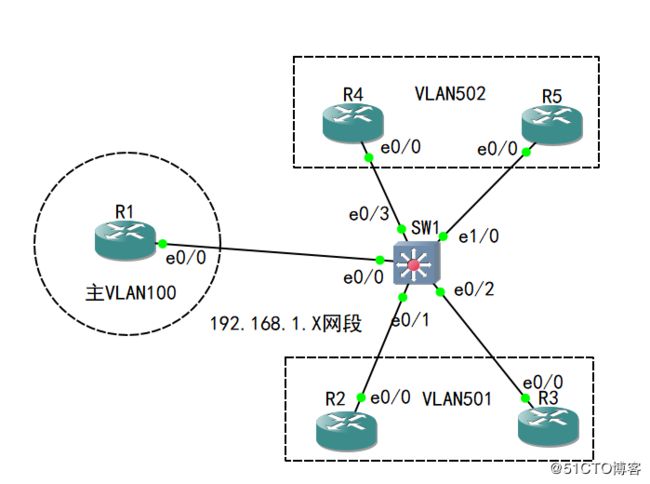
二、实验要求:
某一个VLAN中会划分多个子VLAN,子VLAN可以和主VLAN之间通信,但是子VLAN和子VLAN之间通不了。
一般在IDC机房比较常见,CCIE有很多方向,比如:RS、ISP等共8个方向。这里会涉及到Q in Q技术,可以百度了解下。一共就4000多个VLAN,根本不够用,所以二层通信数量不够用。
隔离VLAN:相同VLAN 通不了;
杂合端口:可以通信VLAN200、VLAN201,多个VLAN都能通就是杂合端口;
1、R1为主VLAN,R2、R3为一个子VLAN并为团体属性;R4、R5为一个子VLAN并设置为隔离属性;
2、效果:R1可以和R2、R3、R4、R5通信;
R2、R3相互可以通信;
R4、R5相互不通;
R2、R3和R4、R5不通
3、R2、R3连接交换机的端口做switch protect的,查看R2、R3是否还可以正常通信?
4、如不能,怎么解决?利用三层设备来解决。
注意:如果用VTP一定要透明模式,不然所有交换机都会相互学习到VLAN;
先部署501、502才可以继续部署association 501-502;
现在工程环境中很少见到私有VLAN技术,因为这是一个很旧的技术;
比如百度服务器,自己拉电缆、自己维护,运行BGP连接整个互联网;
三、命令部署:
实验一部署:
1、设置VTP为透明模式:
SW1(config)#vtp mode transparent
2、设置主VLAN:
SW1(config)#vlan 100
SW1(config-vlan)#private-vlan primary 私有VLAN模式为主VLAN
3、设置二级子VLAN:
SW1(config)#vlan 501
SW1(config-vlan)#private-vlan community 私有VLAN:设为联盟VLAN
SW1(config)#vlan 502
SW1(config-vlan)#private-vlan isolated 私有VLAN:设为隔离VLAN
4、将子VLAN划入主VLAN中,建立关联:
SW1(config)#vlan 100
SW1(config-vlan)#private-vlan association 501,502
SW1(config-vlan)#private-vlan association 501-502 私有VLAN:子VLAN划入主VLAN中
5、将端口设定一个模式,并划入相应的VLAN:
SW1(config)#int e0/0
SW1(config-if)#switchport mode private-vlan promiscuous //设置混杂端口
SW1(config-if)#switchport private-vlan mapping 100 501-502 //设定混杂端口所能管理的子VLAN
SW1(config)#int range e0/1-2
SW1(config-if-range)#switchport mode private-vlan host // 端口模式:私有VLAN主机模式
SW1(config-if-range)#switchport private-vlan host-association 100 501 //端口私有VLAN:主机联合 100 501(主VLAN、子VLAN)
SW1(config)#int range e0/3,e1/0
SW1(config-if-range)#switchport mode private-vlan host
SW1(config-if-range)#switchport private-vlan host-association 100 502
实验二部署:
SW1(config-if)#switchport protected
四、验证:
1、R1可以和R2、R3、R4、R5通信
R1#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R1#ping 192.168.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R1#ping 192.168.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R1#ping 192.168.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.5, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
2、R2 ping R3:可以Ping通
R2#ping 192.168.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
3、R4 ping R5:不通
R4#ping 192.168.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.5, timeout is 2 seconds:.....
Success rate is 0 percent (0/5)
4、R2、R3和R4、R5不通
R2#ping 192.168.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.4, timeout is 2 seconds:.....
Success rate is 0 percent (0/5)
R2#ping 192.168.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.5, timeout is 2 seconds:.....
Success rate is 0 percent (0/5)
R3#ping 192.168.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.4, timeout is 2 seconds:.....
Success rate is 0 percent (0/5)
R3#ping 192.168.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.5, timeout is 2 seconds:.....
Success rate is 0 percent (0/5)
5、SW1连接R2的端口e0/1开启端口保护:
SW1#ping 192.168.1.3
% Unrecognized host or address, or protocol not running.