Kerberos 服务部署
Kerberos服务部署
系统版本:CentOS Linux release 7.2.1511
Kerberos简介
首先,我们了解下kerberos是个什么东西?
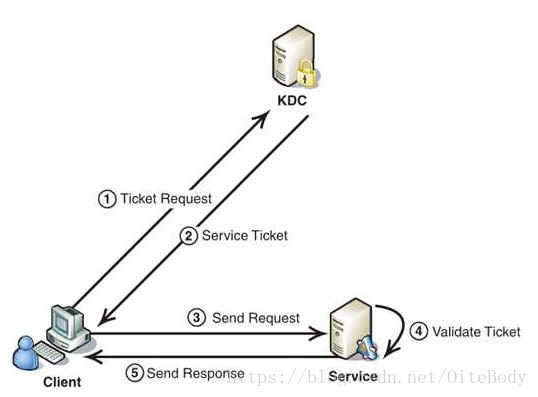
Kerberos协议主要用于计算机网络的身份鉴别(Authentication), 其特点是用户只需输入一次身份验证信息就可以凭借此验证获得的票据(ticket-granting ticket)访问多个服务,即SSO(Single Sign On)。由于在每个Client和Service之间建立了共享密钥,使得该协议具有相当的安全性。Kerberos协议分为两个部分
1.Client向KDC发送自己的身份信息,KDC从Ticket Granting Service得到TGT(ticket-granting ticket), 并用协议开始前Client与KDC之间的密钥将TGT加密回复给Client。
此时只有真正的Client才能利用它与KDC之间的密钥将加密后的TGT解密,从而获得TGT。
(此过程避免了Client直接向KDC发送密码,以求通过验证的不安全方式)
2.Client利用之前获得的TGT向KDC请求其他Service的Ticket,从而通过其他Service的身份鉴别。
Kerberos简易流程说明:
- Client将之前获得TGT和要请求的服务信息(服务名等)发送给KDC,KDC中的Ticket Granting Service将为Client和Service之间生成一个Session Key用于Service对Client的身份鉴别。然后KDC将这个Session Key和用户名,用户地址(IP),服务名,有效期, 时间戳一起包装成一个Ticket(这些信息最终用于Service对Client的身份鉴别)发送给Service, 不过Kerberos协议并没有直接将Ticket发送给Service,而是通过Client转发给Service.所以有了第二步。
- 此时KDC将刚才的Ticket转发给Client。由于这个Ticket是要给Service的,不能让Client看到,所以KDC用协议开始前KDC与Service之间的密钥将Ticket加密后再发送给Client。同时为了让Client和Service之间共享那个秘密(KDC在第一步为它们创建的Session Key), KDC用Client与它之间的密钥将Session Key加密随加密的Ticket一起返回给Client。
- 为了完成Ticket的传递,Client将刚才收到的Ticket转发到Service. 由于Client不知道KDC与Service之间的密钥,所以它无法算改Ticket中的信息。同时Client将收到的Session Key解密出来,然后将自己的用户名,用户地址(IP)打包成Authenticator用Session Key加密也发送给Service。
- Service 收到Ticket后利用它与KDC之间的密钥将Ticket中的信息解密出来,从而获得Session Key和用户名,用户地址(IP),服务名,有效期。然后再用Session Key将Authenticator解密从而获得用户名,用户地址(IP)将其与之前Ticket中解密出来的用户名,用户地址(IP)做比较从而验证Client的身份。
- 如果Service有返回结果,将其返回给Client。
Kerberos server 搭建
注:以下搭建环境基于centos7 1511 minimal版本,内网各个主机添加了dns内部解析及ntp时间同步。
1、kerberos服务端软件包安装
yum install krb5-server krb5-libs krb5-workstation -y
2、修改/etc/krb5.conf# Configuration snippets may be placed in this directory as well
#includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = TEST.COM
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
clockskew = 600
[realms]
TEST.COM = {
kdc = bigdatademo
admin_server = bigdatademo
}
[domain_realm]
.test.com = TEST.COM
test.com = TEST.COM主要修改realm为TEST.COM
配置样例:
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
TEST.COM = {
#master_key_type = aes256-cts
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
max_life = 1d
max_renewable_life = 7d
supported_enctypes = aes256-cts:normal aes128-cts:normal arcfour-hmac:normal
default_principal_flags = +renewable, +forwardable
}
4、修改/var/kerberos/krb5kdc/kadm5.acl,设置database administrator的ACL权限
*/[email protected] *5、创建数据库,/user/sbin/kdb5_util create -s 需要输入database master的密码
路径保存为:/var/kerberos/krb5kdc,如果需要重新建立数据库,把principal下相关文件删除即可
6、开启kerberos
systemctl restart krb5kdc
systemctl restart kadmin
systemctl enable krb5kdc
systemctl enable kadmin
现在KDC已经在工作了,两个daemons将会在后台运行,可以查看他们的日志文件/var/log/krb5kdc.log、/var/log/kadmind.log
7、使用本地方式添加admin权限用户
# kadmin.local -q "addprinc oiteboy/admin"
Authenticating as principal root/[email protected] with password.
WARNING: no policy specified for oiteboy/[email protected]; defaulting to no policy
Enter password for principal "oiteboy/[email protected]":
Re-enter password for principal "oiteboy/[email protected]":
Principal "oiteboy/[email protected]" created.
8、检查kdc是否OK
kinit 获取票据到缓存中
# kinit oiteboy/admin
Password for oiteboy/[email protected]:
klist 查看缓存中的内容
# klist -e
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: oiteboy/[email protected]
Valid starting Expires Service principal
07/06/2018 10:11:58 07/07/2018 10:11:58 krbtgt/[email protected]
renew until 07/13/2018 10:11:58, Etype (skey, tkt): aes128-cts-hmac-sha1-96, aes128-cts-hmac-sha1-96
Kerberos client搭建
1、客户端安装
yum install krb5-workstation
2、复制Kerberos server的/etc/krb.conf到client的/etc/krb.conf
在kerberos server/client添加主机名映射到 /etc/hosts
3、authenticate the admin user with kerberos
# kinit oiteboy/admin
Password for oiteboy/[email protected]:
# kadmin
Authenticating as principal oiteboy/[email protected] with password.
Password for oiteboy/[email protected]:
kadmin: listprincs
管理kerberos principal
- kerberos server管理kerberos principal
- 创建service principal
- 创建普通principal
- 改变principal
- 改密码
- 查看principal
创建principal和生成keytab文件
创建principal
addprinc -randkey hadoop/[email protected]创建keytab文件
# ktadd -norandkey -k /root/hadoop.keytab hadoop/[email protected]验证keytab文件是否生效
# klist -kt /root/hadoop.keytab
将kerberos server主机下的/root/hadoop.keytab拷贝到主机test上。
根据keytab获取KDC的ticket
# kinit -kt /root/hadoop.keytab host/[email protected]
查看kerberos服务端对应日志,确认鉴权成功