Nexus Repository Manager 2/3安全相关
出的代码只有执行只有两个。Nexus 3一个CVE-2019-7238,未授权RCE,Nexus 2一个CVE-2019-5475,内置插件不过需要admin权限的。
有一个需要登录之后的代码JEXL表达式代码执行:CVE-2018-16621
An attacker with administrative privileges can exploit this vulnerability to execute code on the server.
参考:
https://support.sonatype.com/hc/en-us/articles/360010789153-CVE-2018-16621-Nexus-Repository-Manager-Java-Injection-October-17-2018
Sonatype Nexus Repository Manager before 3.14 allows Java Expression Language Injection.
参考:https://nvd.nist.gov/vuln/detail/CVE-2018-16621
其他的是一些XSS。
还有两个不知道怎么弄到CVE的,一个是未授权可以访问一些图片等静态资源CVE-2019-9630,一个是CVE-2019-9629“默认密码是admin/admin123”
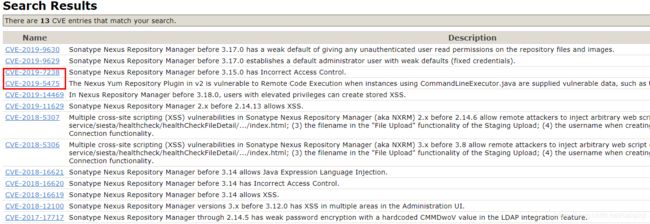
学习一下这几个XSS:
参考:
https://seclists.org/fulldisclosure/2018/Feb/23
CVE-2018-5306 - covers the XSS vulnerabilities in Nexus 3
官方公告:
https://support.sonatype.com/hc/en-us/articles/360000134968
修复版本:
3.8.0
CVE-2018-5307 - covers the XSS vulnerabilities in Nexus 2
修复版本:
2.14.6
官方公告:
https://support.sonatype.com/hc/en-us/articles/360000134928
[CVE-2019-16530][RCE] Nexus Repository Manager 2 & 3, and Nexus IQ Server
影响版本:<= 2.14.14;<= 3.18.1
修复版本:2.14.15;3.19.0
漏洞描述:
TLDR; 管理员权限的用户可以通过文件上传实现RCE。
An attacker with elevated privileges can upload a specially crafted file. That file can contain commands that will be executed on the system, with the same privileges as the user running the server.
触发点定位,
参考:https://help.sonatype.com/repomanager2/using-the-user-interface/uploading-components

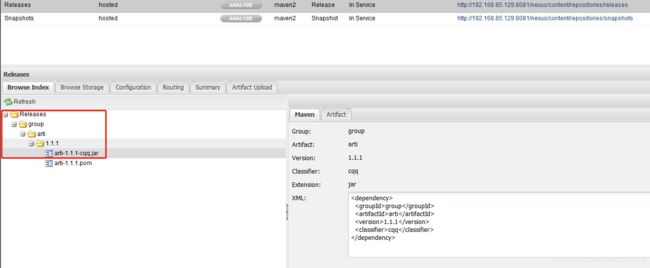
需要一个hosted repo(比如Releases、3rd party)
https://support.sonatype.com/hc/en-us/articles/360036132453-CVE-2019-16530-Nexus-Repository-Manager-2-3-and-Nexus-IQ-Server-Remote-Code-Execution-2019-09-19
[CVE-2019-15893][RCE] Nexus Repository Manager 2
影响版本:<= 2.14.15
修复版本: 2.14.16
漏洞描述:
TLDR; 管理员权限的攻击者可以创建repo,然后执行/读取系统数据。
an attacker with administrative access to NXRM to create repostories that can grant access to read/execute system data outside the scope of NXRM.
https://support.sonatype.com/hc/en-us/articles/360035055794-CVE-2019-15893-Nexus-Repository-Manager-2-Remote-Code-Execution-2019-09-03
杂
调试
高版本修改bin/nexus.vmoptions:
# for debug
-agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=12346
低版本2.14.14修改bin/jsw/conf/wrapper.conf:
#wrapper.java.additional.4=-Xdebug
#wrapper.java.additional.5=-Xnoagent
#wrapper.java.additional.6=-Djava.compiler=NONE
#wrapper.java.additional.7=-Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=8000
(注意:官方自带的是suspend=y,会阻塞等待调试,这里需要将其修改为suspend=n。)
将以上内容取消注释。
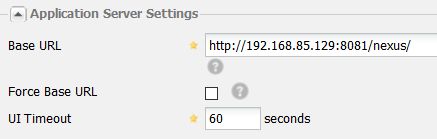
修改启动端口:
conf/nexus.properties
如果碰到下面的情况:
wrapper | OpenSCManager failed - 拒绝访问。 (0x5)
请按任意键继续. . .
则表示需要已管理员权限运行。
另外添加几个属性:
wrapper.startup.delay=30
wrapper.startup.timeout=30
(注意:Nexus2的启动要加上path:/nexus)
参考:
http://www.scmgalaxy.com/tutorials/the-nexus-webapp-service-is-not-installed-the-specified-service-does/
https://www.cnblogs.com/shannyn/archive/2012/07/04/2576875.html
https://support.sonatype.com/hc/en-us/articles/213464718-Windows-OpenSCManager-failed-Access-is-denied-0x5-errors-when-starting-Nexus