“为物联网提供分散的隐私保护医疗区块链”外文翻译——2019年5月份
原文链接:https://www.ncbi.nlm.nih.gov/pmc/articles/PMC6359727/
翻译人:FJTCM区块链开发学习小组 时间:2019/05/31
为物联网提供分散的隐私保护医疗区块链
原文链接:https://www.ncbi.nlm.nih.gov/pmc/articles/PMC6359727/
Abstract
Medical care has become one of the most indispensable parts of human lives, leading to a dramatic increase in medical big data. To streamline the diagnosis and treatment process, healthcare professionals are now adopting Internet of Things (IoT)-based wearable technology. Recent years have witnessed billions of sensors, devices, and vehicles being connected through the Internet. One such technology—remote patient monitoring—is common nowadays for the treatment and care of patients. However, these technologies also pose grave privacy risks and security concerns about the data transfer and the logging of data transactions. These security and privacy problems of medical data could result from a delay in treatment progress, even endangering the patient’s life. We propose the use of a blockchain to provide secure management and analysis of healthcare big data. However, blockchains are computationally expensive, demand high bandwidth and extra computational power, and are therefore not completely suitable for most resource-constrained IoT devices meant for smart cities. In this work, we try to resolve the above-mentioned issues of using blockchain with IoT devices. We propose a novel framework of modified blockchain models suitable for IoT devices that rely on their distributed nature and other additional privacy and security properties of the network. These additional privacy and security properties in our model are based on advanced cryptographic primitives. The solutions given here make IoT application data and transactions more secure and anonymous over a blockchain-based network.
摘要
医疗已经成为人类生活中最不可或缺的部分之一,医疗大数据也随之迅猛增长。为了简化诊断和治疗过程,医疗专业人员正在采用基于物联网(IoT)的可穿戴技术。近年来,数以十亿计的传感器、设备和车辆通过互联网连接起来。其中一项技术——远程病人监测——如今在病人的治疗和护理中很常见。然而,这些技术也对数据传输和记录数据事务带来了严重的隐私风险和安全问题。这些医疗数据的安全和隐私问题可能是由于治疗进展的延迟,甚至危及患者的生命。我们建议使用区块链来提供医疗大数据的安全管理和分析。然而,区块链计算成本高,需要高带宽和额外的计算能力,因此并不完全适合大多数面向智能城市的资源受限物联网设备。在这项工作中,我们试图解决上述问题,使用bb0与物联网设备。我们提出了一个新的框架,修改后的区块链模型适用于物联网设备,依赖于它们的分布式性质和其他额外的隐私和网络安全特性。我们模型中这些额外的隐私和安全属性是基于高级密码原语的。这里给出的解决方案使物联网应用程序数据和事务在基于区块链的网络上更加安全和匿名。
1. Introduction
Many countries are suffering from a dramatic increase in the number of medical patients, and it is becoming more difficult for patients to access primary doctors or caregivers. In recent years, the rise of IoT and wearable devices has improved the patient quality of care by remote patient monitoring. It also allows physicians to treat more patients. Remote patient monitoring (RPM) provides monitoring and care of patients outside of the conventional clinical setting (in the home as an example). Firstly, it allows patients an intrinsic convenience of service. Patients can stay connected with health providers as required. It also reduces medical costs and improves the quality of care. This is the main reason that healthcare providers are exploring means by which to provide RPM to the masses. The main component of a RPM system could be, a specially designed monitoring device to monitor and transmit health data to smart contracts, a smartphone with internet connectivity and an RPM application (Figure 1). Wearable devices and IoT play an important role in RPM and in the current push to develop Smart Cities. Wearable devices collect patient health data and transfer it to hospitals or medical institutions to facilitate health monitoring, disease diagnosis, and treatment. In doing so, we see a Big Data situation develop through all the patient data being analyzed and transferred.
1. 介绍
许多国家正在遭受医疗病人人数急剧增加的痛苦,病人越来越难以获得初级医生或护理人员。近年来,物联网和可穿戴设备的兴起,通过远程患者监测提高了患者的护理质量。它还允许医生治疗更多的病人。远程患者监测(RPM)提供常规临床环境之外的患者监测和护理(例如在家中)。首先,它给病人提供了一种内在的服务便利性。患者可以根据需要与卫生服务提供者保持联系。它还降低了医疗成本,提高了医疗质量。这是卫生保健提供者正在探索向大众提供RPM的方法的主要原因。RPM系统的重要组成部分,一个特别设计的监测装置监测和健康数据传输到智能合约,智能手机与互联网连接和一个RPM应用程序(图1)。可穿戴设备和物联网在RPM中发挥重要的作用,在当前大力发展智能城市。可穿戴设备收集患者的健康数据,并将其传输到医院或医疗机构,以方便健康监测、疾病诊断和治疗。在这样做的过程中,我们通过分析和传输所有的患者数据,看到了大数据的发展态势。
Wearable devices in healthcare are smart electronic devices with micro-controllers that can be embedded into clothing or worn on the body as accessories. They are unobtrusive, user-friendly, and connected with advanced features such as wireless data transmission, real-time feedback and alerting mechanisms built into the device. These devices can provide important information to healthcare providers such as blood pressure, blood glucose levels and breathing patterns just to name a few. Healthcare devices can be categorized into four types (Figure 2):
Stationary Medical Devices—devices can be used on a specific physical location (e.g., chemotherapy dispensing stations for home-based healthcare)
Medical Embedded Devices—devices which can be implanted inside the body (e.g., pacemakers)
Medical Wearable Devices—prescribed devices by doctors (e.g., insulin pump)
Wearable Health Monitoring Devices—consumer products (e.g., Fitbit, Fuelband, etc.)
医疗保健领域的可穿戴设备是带有微型控制器的智能电子设备,可以嵌入衣服或作为附件佩戴在身上。它们不引人注目,用户友好,并与先进的功能连接,如无线数据传输,实时反馈和警报机制内置设备。这些设备可以为医疗保健提供者提供重要的信息,例如血压、血糖水平和呼吸模式等等。医疗设备可以分为四种类型(图2):
固定医疗设备——设备可以用于特定的物理位置(例如,家庭医疗的化疗配药站)。
医学嵌入式设备——可以植入体内的设备(如起搏器)
医用可穿戴设备——医生指定的设备(如胰岛素泵)
可穿戴健康监测设备——消费品(如Fitbit、Fuelband等)
On 13 November 2017, the Food and Drug Administration (FDA) approved the first pill with a sensor inside of it (aripiprazole tablets with sensor) that can track if a patient has swallowed it. This pill’s sensor sends messages to a wearable patch, and the patch itself transmits the message to a mobile application on the smartphone. This technology could be a game changer for chronic disease and mental health disorders.
One of the facets of the Internet of Things (IoT) is the network of wearable devices, embedded with software, electronics, sensors, actuators, and connectivity which enables the wearable device to connect and exchange data (Figure 3). In a futuristic smart city, we will not only see these wearable devices transmitting healthcare data, but it is reasonable to assume that wearable devices can share a myriad of data as we interconnect these devices. Therefore, the reach of the ideas presented here regarding wearable healthcare devices and using blockchain technology are further reaching than we show or can imagine here.
2017年11月13日,美国食品和药物管理局(FDA)批准了第一种内置传感器的药片(阿立哌唑片内置传感器),这种药片可以追踪患者是否吞下了药片。这种药丸的传感器向可穿戴贴片发送信息,贴片本身将信息传输到智能手机上的移动应用程序。这项技术可能会改变慢性病和精神健康障碍的游戏规则。
的方面之一物联网的网络(物联网)是可穿戴设备、嵌入式软件、电子、传感器、执行器、和连通性使可穿戴设备连接和交换数据(图3)。在未来的智能城市,我们不仅能看到这些可穿戴设备传输医疗数据,但它是合理的假设可穿戴设备能够共享大量的数据,因为我们这些设备互连。因此,这里提出的关于可穿戴医疗设备和使用区块链技术的想法比我们在这里展示或想象的范围更广。
To handle such patient data with other institutions, such infrastructure demands secure data sharing. Health data is highly private and sharing of data may raise the risk of exposure. Furthermore, the current system of data sharing uses a centralized architecture which requires centralized trust.
The solution for data privacy and security could and should very well be blockchain technology. Initially proposed by Satoshi Nakamoto in Ref. [1], blockchain technology provides the robustness against failure and data exposure. The blockchain is a shared data structure responsible for storing all transactional history. The blocks relate to each other in the form of a chain. The first block of the chain is known as Genesis. Each block consists of a Block Header, Transaction Counter and Transaction. It acts as a decentralized architecture to record the data. The structure of blockchain is summarized in Table 1.
要与其他机构处理此类患者数据,此类基础设施需要安全的数据共享。健康数据高度隐私,共享数据可能会增加暴露的风险。此外,目前的数据共享系统采用集中式体系结构,需要集中式信任。
数据隐私和安全的解决方案可以而且应该是区块链技术。区块链技术最初是由中本聪在参考文献[1]中提出的,它提供了对故障和数据暴露的鲁棒性。区块链是负责存储所有事务历史的共享数据结构。这些块以链的形式相互联系。这条链的第一块被称为创世纪。每个块由一个块头、事务计数器和事务组成。它作为一个分散的架构来记录数据。表1总结了区块链的结构。
Table 1
Structure of the Blockchain.
| Field |
Size |
| Magic Number |
4 bytes |
| Block Size |
4 bytes |
| Header: Next 80 bytes |
|
| Version |
4 bytes |
| Previous Block Hash |
32 bytes |
| Merckle Root |
32 bytes |
| Timestamp |
4 bytes |
| Difficulty Target |
4 bytes |
| Nonce |
4 bytes |
| Rest of Blockchain |
|
| Transaction Counter |
Variable: 1 to 9 bytes |
| Transaction List |
Depends on the transaction size: Upto 1 MB |
Blockchain security is based on a proof of work concept, and a transaction is only considered valid once the system obtains proof that a enough computational work has been exerted by authorizing nodes. The miners (responsible for creating blocks) constantly try to solve cryptographic puzzles (named Proof of Work (PoW)) in the form of a hash computation. The process of adding a new block to the blockchain is called mining. Each block in the chain is identified by a hash in the header. The hash is unique and generated by the Secure Hash Algorithm (SHA-256). SHA takes any size plaintext and calculates a fixed size 256-bit cryptographic hash. Each header contains the address of the previous block in the chain. The inability to delete or change information from blocks makes the blockchain the best appropriate technology for the healthcare system. However, adopting blockchain in the context of IoT is not straightforward and entails several problems such as demands of high computational power to solve PoW, low scalability and long latency for transaction confirmation over the network.
We propose a novel model of blockchain and eliminate the concept of PoW to make it suitable for IoT devices. Our model relies on the distributed nature and other additional security properties to the network. Transactions in blockchain are broadcasted publicly in the blockchain network and contain additional information about both the sender and recipient. If we talk about the blockchain that underpins bitcoin, everyone has a public address, and anyone can see what funds they already have stored at that address. This way, users cannot be anonymous in the network. For anonymity and the authenticity of the user, we present a lightweight privacy-preserving ring signature scheme that is suitable for anonymous transactions by authentic users.
区块链安全性基于工作证明概念,只有当系统获得足够的计算工作由授权节点完成的证明时,事务才被认为是有效的。采掘者(负责创建块)不断尝试以哈希计算的形式解决密码难题(名为工作证明(Proof of Work, PoW))。向区块链添加新块的过程称为挖掘。链中的每个块由头中的散列标识。哈希是唯一的,由安全哈希算法(SHA-256)生成。SHA接受任何大小的明文,并计算一个固定大小的256位加密散列。每个头包含链中前一个块的地址。无法从块中删除或更改信息使区块链成为医疗系统的最佳合适技术。然而,在物联网环境下采用区块链并不简单,需要解决多个问题,如解决PoW需要高计算能力、低可伸缩性和长时间的网络事务确认延迟。
我们提出了一种新的区块链模型,消除了PoW的概念,使其适用于物联网设备。我们的模型依赖于网络的分布式特性和其他附加的安全属性。区块链中的事务在区块链网络中公开广播,并包含关于发送方和接收方的附加信息。如果我们讨论支撑比特币的区块链,每个人都有一个公共地址,任何人都可以看到他们已经在这个地址存储了哪些资金。这样,用户在网络中就不能是匿名的。为了提高用户的匿名性和真实性,提出了一种适用于真实用户进行匿名交易的轻量级保密环签名方案。
On the one hand, a lightweight digital signature guarantees that information has not been modified, as if it were protected by a tamper-proof seal that is broken if the contents were altered. On the other hand, a ring signature [2] allows a signer to sign a message anonymously. The signature is mixed with other groups (named ring) and no one (except actual signer) knows which member signed the message. We are not using heavy operations such as pairing and exponentiation in ring signature to make it more suitable for blockchain and IoT.
We also use double encryption of data using lightweight encryption algorithms (ARX ciphers) and public encryption schemes. Here double encryption means, we firstly encrypt the data using symmetric key encryption and then we encrypt the symmetric key itself using a public key. Please note that, here we are not encrypting the same data twice with different keys. ARX is a class of cryptographic algorithms which uses three simple arithmetic operations: namely modular addition, bitwise rotation, and exclusive-OR. In both industry and academia, ARX cipher has gained a lot of interest and attention in the last few years. For securely exchanging cryptographic keys over a public channel, we use the Diffie–Hellman key exchange technique. Using both these techniques together will guarantee the security, privacy and anonymity of user’s data using lightweight techniques suitable for small IoT devices.
一方面,一个轻量级的数字签名保证信息没有被修改,就好像它被一个防篡改的密封保护着,如果内容被修改,这个密封就会被破坏。另一方面,环形签名[2]允许签名者匿名签署消息。签名与其他组(名为ring)混合在一起,没有人(除了实际的签名者)知道哪个成员签署了消息。我们没有在环签名中使用大量的操作,例如配对和取幂,使其更适合区块链和物联网。
我们还使用轻量级加密算法(ARX密码)和公共加密方案对数据进行双重加密。这里的双重加密是指先用对称密钥加密数据,再用公钥加密对称密钥本身。请注意,这里我们不是用不同的密钥对相同的数据进行两次加密。ARX是一种密码算法,它使用三个简单的算术运算:模加法、位旋转和异或运算。近年来,ARX密码在业界和学术界都引起了广泛的关注。为了在公共通道上安全地交换密钥,我们使用Diffie-Hellman密钥交换技术。将这两种技术结合使用,将使用适用于小型物联网设备的轻量级技术,保证用户数据的安全性、隐私性和匿名性。
2. Related Work
In this paper, we pull some of our main motivation to explore blockchain in healthcare from Refs. [3,4,5,6,7,8], where the respective authors systematically mentioned some of the latest trends in blockchain research. Since the introduction of Bitcoin in Ref. [1], the possibilities are endless of how the underlying technology can be used in other ways outside of the financial realm. There have been numerous attempts at applying blockchain technology outside of the financial realm [9,10,11,12,13,14]. It is easy to imagine the far-reaching applicability of this technology specifically in healthcare, smart cities and IoT.
In Ref. [15], there was an introduction to methods for using blockchain to provide proof of pre-specified endpoints in clinical trials. Irving and Holden empirically tested such an approach using a clinical trial protocol where outcome switching had previously been reported. They confirmed the use of blockchain as a low cost, independently verifiable method to audit and confirmed the reliability of scientific studies. We use lightweight digital signature schemes in our model inspired by Ref. [2].
We have to date already heard of many data breaches or data losses with regards to medical data [16,17]. Health information is something hackers will seek out as it may contain pertinent information for identity theft. Medical record ownership is another key point when discussing health information. The records themselves come in many forms, reports, images, videos, and raw data. They could potentially also come in many different formats depending on the systems in use by the given provider. The integrity of these records then becomes paramount. There needs to be contingencies in place to ensure the integrity of the data is maintained to ensure the data has not been changed, destroyed, or removed. The access to the data should be controlled by the patients; however, they themselves should not be able to alter it either. The patient records should be consistent and available across institutional boundaries [18,19].
In the context of Smart cities and Big Data, we have seen some strong work recently by Wu and Ota in Refs. [20,21,22,23]. They have really been able to focus on how IoT, Smart Cities, and the resulting Big Data are all important factors going forward with Smart City design and implementation. We have contributed some work already in cryptanalysis of ARX ciphers and other security algorithms [24,25,26,27,28,29,30].
2. 相关工作
在本文中,我们从参考文献中提取了一些主要动机来探索区块链在医疗保健中的应用。[3,4,5,6,7,8],其中,各自的作者系统地提到了区块链研究的一些最新趋势。自从在Ref.[1]中引入比特币以来,如何在金融领域之外以其他方式使用基础技术的可能性是无穷无尽的。在金融领域之外应用区块链技术的尝试很多[9,10,11,12,13,14]。不难想象,这项技术在医疗、智能城市和物联网领域的广泛应用。
参考文献[15]中介绍了使用区块链在临床试验中提供预先指定终点的证明的方法。欧文和霍尔登使用之前报道过结果转换的临床试验方案对这种方法进行了经验检验。他们证实使用区块链作为一种低成本、独立可验证的审计方法,并证实了科学研究的可靠性。我们在模型中使用了轻量级数字签名方案,其灵感来自于Ref.[2]。
到目前为止,我们已经听说了许多关于医疗数据的数据泄露或数据丢失[16,17]。健康信息是黑客会寻找的东西,因为它可能包含有关身份盗窃的信息。病历所有权是讨论健康信息时的另一个关键点。这些记录本身有许多形式、报告、图像、视频和原始数据。根据给定提供者所使用的系统,它们也可能有许多不同的格式。因此,这些记录的完整性变得至关重要。需要有应急措施来确保数据的完整性得到维护,以确保数据没有被更改、销毁或删除。数据的获取应由患者控制;然而,他们自己也不应该改变它。患者记录应该是一致的,并且可以跨机构边界使用[18,19]。
在智慧城市和大数据的背景下,我们看到Wu和Ota最近在Refs方面进行了一些强有力的工作。(20、21、22、23)。他们真正关注的是物联网、智慧城市以及由此产生的大数据如何成为推动智慧城市设计和实现的重要因素。我们已经在ARX密码的密码分析和其他安全算法方面做了一些工作[24,25,26,27,28,29,30]。
3. Drawbacks and Security Issues
The main concern in RPM systems is the secure and efficient transmission of the medical data. Healthcare data is a lucrative target for hackers and therefore securing protected health information (PHI) is the primary motivation of healthcare providers. Healthcare has become the primary target for cybercriminals. For example, cyber-attacks on medical devices or health data have become more common in the last decade. However, the inability to delete or change information from blocks makes blockchain technology the best technology for the healthcare system and could prevent these issues. However, blockchain technology in its original form is not enough of a solution. In this section, we discuss the challenges for applying blockchain to the IoT and explain how to solve these problems in our model.
3.缺点和安全性问题
RPM系统的主要关注点是医疗数据的安全和高效传输。医疗数据是黑客的一个有利可图的目标,因此保护受保护的医疗信息(PHI)是医疗服务提供商的主要动机。医疗保健已成为网络犯罪的首要目标。例如,对医疗设备或健康数据的网络攻击在过去十年变得更加普遍。然而,无法从块中删除或更改信息使得区块链技术成为医疗系统的最佳技术,并且可以防止这些问题。然而,区块链技术在其最初的形式是不够的解决方案。在本节中,我们将讨论将区块链应用于物联网的挑战,并解释如何在我们的模型中解决这些问题。
System Requirements and Our Solutions
Decentralization: To ensure robustness and scalability and to eliminate many-to-one traffic flows we need a decentralized system. Using such decentralized systems, we can also eliminate the single point of failure or information delay problems. In our model, we are using an overlay decentralized network.
Authentication of data: User’s computer or cloud services store unpreserved data that needs to be transferred to blockchain networks. During transmission, the data could be modified or lost. The preservation of such incorrect tampered data increases the burden to the system and can cause the loss of the patient (death). Therefore, to ensure that data is not modified, we use a lightweight digital signature [2] scheme. On the receiver side, data is verified with the user’s digital signature, and if received correctly, it sends a receipt of data to the patient.
Scalability: Solving PoW is computationally intensive; however, IoT devices are resource restricted. Also, the IoT network contains many nodes and blockchain scales poorly as the number of nodes in the network increases. We eliminate the concept of PoW in our overlay network and divide our overlay network into several clusters instead of a single chain of blocks, and therefore a single blockchain is not responsible for all nodes. Instead we spread the nodes over several clusters. Our model relies on the distributed nature and other additional security properties to the network.
Data Storage: Storing IoT big data over blockchain is not practical and therefore we use cloud servers to store encrypted data blocks. The data is safe over the cloud due to additional cryptographic security like the digital signature and high standard encryptions which will be discussed later. However, it may cause a problem about trusted third parties. For this purpose, we store all transactions in different blocks and create a combined hash of each block using Merkle Tree and transfer it to the distributed network. This way, any changes in cloud data can be easily detectable. Doing the storage in this manner also preserves the decentralization over some extents.
Anonymity of users: Medical data of a patient may contain sensitive information, and therefore data must be anonymized over the network. For anonymity, we are using lightweight Ring structure [2] along with digital signatures. Ring signature allow a signer to sign data anonymously, that is the signature is mixed with other groups (named ring), and no one (except actual signer) knows which member signed the message.
Security of data: Medical devices or health data must be accurate and cannot be changed by hackers. To save the data from hackers, we are using a double encryption scheme. Here double encryption does not refer to encrypting the same data using two keys but instead encryption of the data and again encryption of key which was used to encrypt data. We encrypt the data using lightweight ARX algorithms and then encrypt the key using the public key of the receiver. Also, we are using the Diffie–Hellman key exchange technique to transfer the public keys and therefore getting the keys is almost impossible for an attacker.
系统需求和我们的解决方案
1.分散化:为了确保健壮性和可伸缩性,并消除多对一的流量,我们需要一个分散化的系统。利用这种分散系统,还可以消除单点故障或信息延迟问题。在我们的模型中,我们使用了一个覆盖分散网络。
2.数据认证:用户的计算机或云服务存储需要传输到区块链网络的未保存数据。在传输过程中,数据可能被修改或丢失。保存这种不正确的篡改数据增加了系统的负担,并可能导致病人的损失(死亡)。因此,为了确保数据不被修改,我们使用了一个轻量级的数字签名[2]方案。在接收端,数据通过用户的数字签名进行验证,如果接收正确,它将向患者发送数据收据。
3.可伸缩性:解决PoW需要大量的计算;然而,物联网设备受到资源限制。此外,物联网网络包含很多节点,随着网络节点数量的增加,区块链的扩展性很差。我们在覆盖网络中消除了PoW的概念,将覆盖网络划分为多个集群,而不是单个块链,因此单个区块链并不负责所有节点。相反,我们将节点分散到几个集群中。我们的模型依赖于网络的分布式特性和其他附加的安全属性。
4.数据存储:在区块链上存储物联网大数据是不现实的,因此我们使用云服务器来存储加密的数据块。数据在云上是安全的,因为有额外的加密安全性,比如数字签名和高标准加密,这些将在后面讨论。然而,它可能会导致关于可信第三方的问题。为此,我们将所有事务存储在不同的块中,并使用Merkle树创建每个块的组合散列,并将其传输到分布式网络。这样,云数据中的任何变化都可以很容易地检测到。以这种方式进行存储也在一定程度上保留了分散化。
5.用户匿名:患者的医疗数据可能包含敏感信息,因此必须通过网络进行匿名。为了匿名,我们使用了轻量级的环形结构[2]和数字签名。Ring签名允许签名者匿名对数据签名,即签名与其他组(名为Ring)混合在一起,没有人(除了实际签名者)知道哪个成员签名了消息。
6.数据安全:医疗设备或健康数据必须准确,黑客不能更改。为了防止黑客窃取数据,我们采用了双重加密方案。这里的双重加密不是指使用两个密钥加密相同的数据,而是对数据进行加密,然后对用于加密数据的密钥进行加密。我们使用轻量级ARX算法加密数据,然后使用接收方的公钥加密密钥。此外,我们使用Diffie-Hellman密钥交换技术来传输公钥,因此攻击者几乎不可能获得密钥。
4. Our System
Our system consists of five parts: Overlay network, Cloud storage, Healthcare providers, Smart contracts and Patient equipped with healthcare wearable IoT devices.
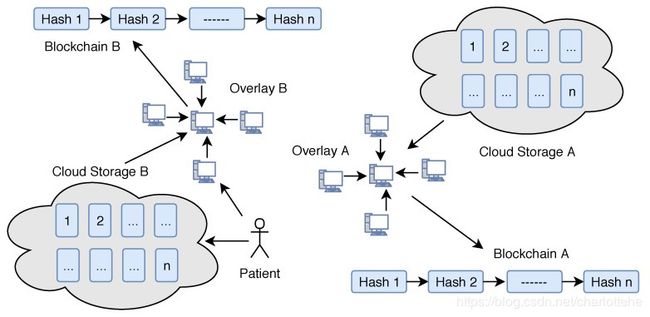
Cloud Storage: Instead of saving the IoT healthcare data over blockchain, we use cloud storage servers to save the patient data. The cloud storage groups user’s data in identical blocks associated with a unique block number. These clouds are connected to overlay networks, once the data stored in a block, the cloud server sends the hash of the data blocks to the overlay network. The hash of the data in the single block is calculated using Merkle Tree (Figure 4). If the overlay network accepts the root hash of the new block, it adds the new hash with the previous hash value and generates the new hash of the chain. In such cases, we do not need any third-party trust, because any changes in data could be easily traceable.
4. 我们的系统
我们的系统由五个部分组成:覆盖网络、云存储、医疗服务提供商、智能合同和配备医疗可穿戴物联网设备的患者。
云存储:我们使用云存储服务器来保存患者数据,而不是通过区块链保存物联网医疗数据。云存储将用户的数据分组到与惟一块号关联的相同块中。这些云连接到覆盖网络,一旦数据存储在一个块中,云服务器将数据块的哈希发送到覆盖网络。使用Merkle树计算单个块中数据的哈希值(图4),如果覆盖网络接受新块的根哈希值,则使用之前的哈希值添加新哈希值,生成链的新哈希值。在这种情况下,我们不需要任何第三方信任,因为数据中的任何更改都可以很容易地跟踪。
Overlay network: An overlay is a peer-to-peer network that is based on distributed architecture. The nodes connected to the network could be a computer, smartphone, tablet or any other IoT device as well (Figure 5). (Please note that, in the description of overlay networks we assume that readers have sufficient knowledge of standard cryptographic protocols and use of the hash function in bitcoin mining.) In our model, a network consists of specific nodes and they need to prove that they are certified with a valid certificate. Such a certificate can be uploaded or verified before making an account on the network. Once authorized, he/she will be able to sign data/transaction over the network digitally. To increase network scalability and avoid network delay, we group the nodes in the form of many clusters. Each cluster has one Cluster Head that takes care of public keys of the nodes. Any node attached with any cluster can change the cluster at any time in case of delay. Also, the nodes attached to a cluster can change the cluster head. Cluster head maintains the public keys of requesters (healthcare providers), who can access the data of a particular patient, and the public key of requestees (patient) that are allowed to be accessed
覆盖网络:覆盖是基于分布式架构的对等网络。连接到网络的节点也可以是计算机、智能手机、平板电脑或任何其他物联网设备(请注意,在描述覆盖网络时,我们假设读者对标准加密协议和比特币挖掘中的哈希函数有足够的了解)。在我们的模型中,网络由特定的节点组成,它们需要证明自己是通过有效证书认证的。这样的证书可以在网上注册帐户前上传或验证。一旦获得授权,他/她将能够通过网络数字签署数据/事务。为了提高网络的可伸缩性和避免网络延迟,我们将节点分组为多个集群的形式。每个集群都有一个集群头,负责处理节点的公钥。任何与任何集群连接的节点都可以在任何时候更改集群,以防出现延迟。此外,附加到集群的节点可以更改集群头。Cluster head维护可以访问特定患者数据的请求者(医疗保健提供者)的公钥,以及允许访问的请求者(患者)的公钥
· Consider the case where a patient wants to share his/her data with a particular doctor, then the node digitally signs the transaction and sends it to the network with a public address of the doctors’ node. The cluster head verifies the patient digital signature and patient public key, and if it is verified correctly, cluster head searches the public key of the doctor node in his own cluster. If the public key is available, then it will broadcast the transaction to its own cluster, and if doctor nodes public key is not available then cluster head will broadcast the transaction to other clusters. In the case where the digital signature or public key of any node is not verified then the cluster will not broadcast data in its cluster but transfer transaction to other cluster heads. Cluster heads are also responsible for storing the hash of the data block stored in the cloud. Each new block in the cluster contains the hash of the previous block also (Please note that each hash block says hashn is combined hash of all previous hashes such as hash1,hash2…hash(n−1)). A cluster head can independently decide whether to keep hash of new data block or not. Once a cluster head adds new hash it will broadcast this to all clusters. Other clusters also verify the new block using the hash value of the previous chain. To follow the distributed trust in the network, each cluster head maintains a trust rating for other cluster head based on Beta Reputation System [31]. For more details of overlay networks we suggest readers to reference the following papers [4,32].
· · Healthcare providers: Healthcare providers are appointed by insurance companies or by patients to perform medical tests or to provide medical treatments. Healthcare service providers deal with treatment of patients once they receive an alert from the network. They are also treated as a node in the network and authorized to receive particular patient data from the cloud.
· · Smart contracts: Smart contracts allow the creation of agreements in any IoT devices which is executed when given conditions are met. Consider we set the condition for the highest and lowest level of patient blood pressure. Once readings are received from the wearable device that do not follow the indicated range, the smart contract will send an alert message to the authorized person or healthcare provider and also store the abnormal data into the cloud so that healthcare providers can receive the patient blood pressure readings as well later on if needed.
· · Patient with wearable IoT devices: The IoT device will collect all health data from the patient. Such data could be heartbeats, sleeping conditions, or walking distance to name a few. Patients themselves are the owners of their personal data and responsible for granting, denying or revoking data access from any other parties, such as insurance companies or healthcare providers. If the patient needs medical treatment, he/she will share personal health data with the desired doctor. Once the treatment is finished the patient can deny further access to the doctor, healthcare provider or health insurance company.
考虑这样一种情况:患者希望与特定的医生共享他/她的数据,然后节点对事务进行数字签名,并使用医生节点的公共地址将其发送到网络。簇头验证患者数字签名和患者公钥,如果验证正确,簇头搜索自己簇中医生节点的公钥。如果公钥可用,那么它将把事务广播到它自己的集群,如果doctor nodes公钥不可用,那么cluster head将把事务广播到其他集群。如果没有验证任何节点的数字签名或公钥,则集群将不会在其集群中广播数据,而是将事务传输给其他集群头。集群头还负责存储存储在云中的数据块的散列。集群中的每个新块也包含前一个块的散列(请注意,每个散列块表示hashn是所有前一个散列的组合散列,如hash1、hash2……散列(n - 1))。集群头可以独立决定是否保留新数据块的散列。一旦一个集群头添加了新的散列,它将向所有集群广播这个散列。其他集群也使用前一个链的哈希值验证新块。为了跟踪网络中的分布式信任,每个簇头基于Beta信誉系统[31]为其他簇头维护一个信任等级。关于覆盖网络的更多细节,我们建议读者参考以下论文[4,32]。
医疗服务提供者:医疗服务提供者由保险公司或病人委任,进行医疗测试或提供医疗服务。医疗服务提供者一旦收到来自网络的警报,就会处理对患者的治疗。它们还被视为网络中的一个节点,并被授权从云接收特定的患者数据。
智能合同:智能合同允许在任何物联网设备中创建协议,这些协议在满足给定条件时执行。假设我们设置了患者血压的最高和最低水平。一旦收到可穿戴设备读数不遵守指定的范围,聪明的合同将发送警报信息授权人或医疗服务提供者和异常数据存储到云,医疗服务提供者也可以接收病人血压读数之后如果需要。
穿戴物联网设备的患者:物联网设备将收集患者的所有健康数据。这些数据可以是心跳、睡眠状况或步行距离等。病人本身是其个人资料的拥有人,并有责任准许、拒绝或撤销任何其他方面(例如保险公司或医疗服务提供者)查阅其个人资料。如果病人需要治疗,他/她将与所需医生分享个人健康数据。一旦治疗结束,患者可以拒绝医生、医疗保健提供者或健康保险公司的进一步访问。
5. Cryptographic Techniques Used in the Model
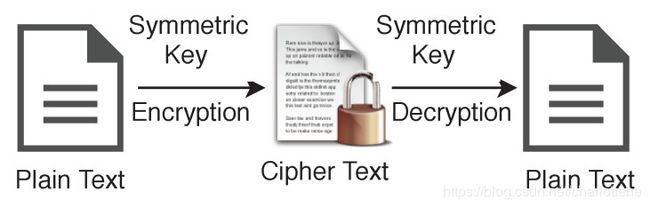
Instead of only one type of encryption technique, we use both encryption schemes, namely Symmetric and Asymmetric for different purposes. A symmetric algorithm (Private key encryption), as shown in Figure 6, uses the same key for both encryption of plaintext and decryption of ciphertext, whereas asymmetric algorithms (Public key encryption) use different keys for encryption of plaintext and decryption of ciphertext. We use the variable name ksym for the private key or symmetric key in our algorithms, and the same key will be used for encryption and decryption on both side of the transmission.
5. 模型中使用的加密技术
我们不是只使用一种加密技术,而是同时使用两种加密方案,即对称加密和非对称加密,用于不同的目的。对称算法(私钥加密),如图6所示,对明文加密和密文解密使用相同的密钥,而非对称算法(公钥加密)对明文加密和密文解密使用不同的密钥。在我们的算法中,私有密匙或对称密匙使用变量名称ksym,传输的两边将使用相同的密匙进行加密和解密。
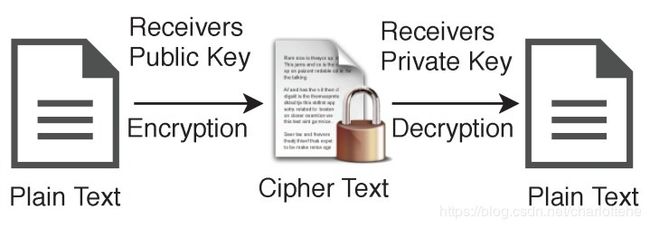
In the case of asymmetric encryption, sender will have one key pair skpriv,skpub, and receiver will have another key pair rkpriv,rkpub, shown in Figure 7. Data can be encrypted using receiver’s public key rkpub and can be decrypted using their private key rkpriv. Generally, we use abbreviations plaintext (P) for the unencrypted data and ciphertext (C) for the encrypted data.
在非对称加密的情况下,发送方将有一个密钥对skpriv,skpub,接收方将有另一个密钥对rkpriv,rkpub,如图7所示。数据可以使用接收方的公钥rkpub加密,也可以使用其私钥rkpriv解密。通常,未加密的数据使用缩写明文(P),加密的数据使用密文(C)。
5.1. ARX Encryption Algorithm
In our model, we are using a particular branch of Symmetric key encryption, called ARX algorithms to encrypt the data for blockchain. These algorithms are made of simple operations Addition, Rotation and XOR and support a lightweight encryption for small devices. Among a few well known examples, the one example of latest usage of ARX cipher is: SPECK [33], designed by the National Security Agency (NSA), of the United States of America (USA) in June 2013. However, SPECK itself has been severely criticized prior to ISO standardization rejection due to the possibility of the well known cipher backdoor issue, but still, we use it here because it is safe against key recovery attacks. Our model is specifically dedicated to securing the network against various attacks rather than to secure individual nodes. In the case where within the network a defaulter node is found, we can automatically block it. SPECK is a family of lightweight block ciphers with the Feistel-like structure in which each block is divided into two branches, and both branches are modified at every round. We show the round function of SPECK in Figure 8. Each block size is divided into two parts, the left half and right half.
5.1。ARX加密算法
在我们的模型中,我们使用对称密钥加密的一个特殊分支,称为ARX算法来加密区块链的数据。这些算法由简单的操作加法、旋转和XOR组成,支持小型设备的轻量级加密。在一些众所周知的例子中,最近使用ARX密码的一个例子是:SPECK[33],由美国国家安全局(NSA)于2013年6月设计。然而,由于众所周知的密码后门问题的可能性,SPECK本身在ISO标准化拒绝之前就受到了严厉的批评,但我们仍然在这里使用它,因为它对密钥恢复攻击是安全的。我们的模型专门用于保护网络免受各种攻击,而不是保护单个节点。在网络中找到一个defaulter节点的情况下,我们可以自动阻止它。SPECK是一种轻量级的块密码,它的结构类似于feistel,每个块被分成两个分支,每个分支在每一轮都被修改。我们在图8中显示了SPECK的圆形函数。每个块大小分为两部分,左半边和右半边。
SPECK Round Function
SPECK uses 3 basic operations on n-bit word for each round:
bitwise XOR, ⊕,
addition modulo 2n,⊞
left and right circular shifts by r2 and r1 bits, respectively.
The left half n-bit word is denoted by Xr−1,L and the right half n-bit word is denoted by Xr−1,R to the r-th round and n-bit round key applied in the r-th round is denoted by kr. Xr,L and Xr,R denotes output words from round r which are computed as follows:
Xr,L=((Xr−1,L⋙r1)⊞Xr−1,R)⊕kr
(1)
Xr,R=((Xr−1,R⋘r2)⊕Xr,L)
(2)
Different key sizes have been used by several instances of the SPECK family and the total number of rounds depends on the key size. The value of rotation constant r1 and r2 are specified as: r1=7, r2=2 or r1=8, r2=3 for various variants of SPECK.
小圆函数
SPECK每轮对n位单词使用3种基本运算:
位XOR,⊕
除了模2 n,⊞
左右圆分别移动了r2位和r1位。
左半边n位单词用Xr−1,L表示,右半边n位单词用Xr−1,R的R -第R轮表示,R -第R轮应用的n位圆键用kr表示。
Xr, L = ((Xr−1, L⋙r1)⊞Xr−1, R)⊕kr
(1)
Xr, R = ((Xr−1, R⋘r2)⊕Xr,左)
(2)
不同的钥匙大小已被使用的几个实例的SPECK家族和总轮数取决于钥匙大小。旋转常数r1和r2的值分别为:r1=7, r2=2或r1=8, r2=3,对于不同的SPECK变体。
5.2. Digital Signature
We add a digital signature to the data for authentication purposes. However, applying normal digital signatures is not suitable due to resources limit in IoT devices. Therefore, we suggest using lightweight digital signatures suitable for small devices as given in Ref. [2]. Digital signatures are the public key primitives of message authentication. Each user has a public-private key pair. Generally, the key pairs used for signing/verifying and the key pairs used for encryption/decryption are different. In our case here, sender will have one key pair skspriv,skspub, and receiver will have another key pair rkspriv,rkspub.
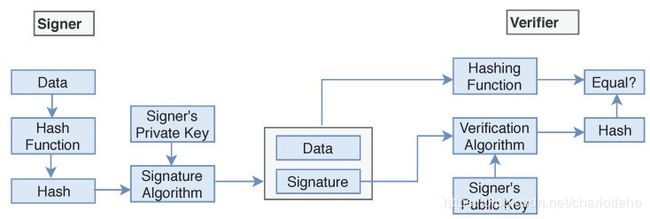
The senders private key skspriv is used to sign the data, and the key is referred to the signature key while senders public key skspub is used for verification on the receiver side of the transmission. Signer feeds the data or plaintext into the Hash Function and generates the hash value hashp. Hash value hashp of plaintext and signature key skspriv are then fed to the signature algorithm and sent along with the encrypted data (Figure 9). During the verification process, the verifier generates the hash value hashr of the received data from the same hash function. Using the Verification algorithm and signers public key, he/she also extracts the original hash value hashp of plaintext and if the value of hashp and hashr are the same then the data is verified and not changed during the transmission process.
5.2。数字签名
我们将数字签名添加到数据中以进行身份验证。然而,由于物联网设备的资源有限,应用普通数字签名并不合适。因此,我们建议使用轻量级数字签名,适用于小型设备,如参考文献[2]所示。数字签名是消息认证的公钥基元。每个用户都有一个公私密钥对。通常,用于签名/验证的密钥对和用于加密/解密的密钥对是不同的。在我们的示例中,发送方将有一个密钥对skspriv,即skspub,而接收方将有另一个密钥对rkspriv,即rkspub。
发送方私钥skspriv用于对数据进行签名,密钥引用签名密钥,而发送方公钥skspub用于在传输的接收端进行验证。签名者将数据或明文输入哈希函数并生成哈希值hashp。然后将明文的哈希值hashp和签名密钥skspriv提供给签名算法,并与加密的数据一起发送(图9),验证者在验证过程中,从相同的哈希函数生成接收数据的哈希值hashr。使用验证算法和签名者公钥,提取纯文本的原始散列值hashp,如果hashp和hashr的值相同,则在传输过程中对数据进行验证,不改变数据。
5.3. Digital Ring Signature
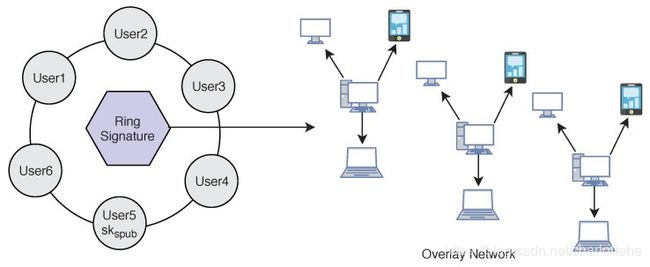
We use lightweight Ring signature technology [2] which allows a signer to sign data in an anonymous way (Figure 10). That is the signature is mixed with other groups (named ring) and no one (except the actual signer) knows which member signed the message. Ring Signature was originally proposed by Rivest in 2001 [34]. A user desiring to mix his transaction sends a request to the blockchain network. The request comprises the public key skspub. After receiving the request the network sends back a certain amount of public keys sk1spub,sk2spub,sk3spub,sk4spub which are collected from other users (u1,u2,…,uN) who also applied for mixing service, including skspub. Using ring signature in our model we can get two important security properties. We achieve both Signers Anonymity and Signature Correctness.
Signature Correctness: A valid signature is always accepted, and an invalid signature is always rejected.
Signers Anonymity: A signature is produced by one member from the set of public key holders. Therefore, the identity of the signer is always hidden in the network, and no one can find out who is the real signer from the signature.
5.3 数字环签名
我们使用轻量级的环形签名技术[2],它允许签名者以匿名的方式对数据签名(图10)。也就是说,签名与其他组(名为ring)混合在一起,没有人(除了实际的签名者)知道哪个成员签署了消息。环签名最初是由Rivest在2001年提出的[34]。希望混合事务的用户向区块链网络发送请求。该请求包括公钥skspub。接收到请求后,网络返回一定数量的公钥sk1spub、sk2spub、sk3spub、sk4spub,这些公钥是从其他申请混合服务的用户(u1、u2、…、uN)处收集的,其中包括skspub。在模型中使用环签名可以得到两个重要的安全属性。实现了签名者的匿名性和签名的正确性。
签名正确性:有效的签名总是被接受,无效的签名总是被拒绝。
签名者匿名性:签名由一组公钥持有者中的一名成员生成。因此,签名者的身份总是隐藏在网络中,没有人能从签名中发现谁是真正的签名者。
5.4. Diffie–Hellman Key Exchange
In all our previous techniques proposed, we need to transfer the public key through the network. To make data more secure, we also share the public key secretly. To share the public key skspub safely along the network we are using the Diffie–Hellman key exchange technique. A basic Diffie–Hellman exchange of a shared secret between Alice and Bob could take place in the following manner:
Alice and Bob generate their own private/public keys (kA;KA) and (kB;KB). Both publish or exchange their public keys and keep the private keys for themselves.
Clearly, it holds that
S=kA·KB=kA·kB·G=kB·kA·G=kB·KA
(3)
Alice could privately calculate S=kA·KB, and Bob S=kB·KA, allowing them to use this single value as a shared secret. For example, if Alice has a message m to send Bob, she could hash the shared secret h=H(S), compute x=m+h, and send x to Bob. Bob computes h′=H(S), calculates m=x−h′, and learns m.
An external observer would not be able to easily calculate the shared secret due to the DLP (discrete logarithm problem), which prevents them from ending kA or kB. Since the output of hash functions is ‘random’, the message m is information-theoretic secure from adversaries who know x, KA, and KB.
5.4。diffie - hellman密钥交换
在我们之前提出的所有技术中,我们都需要通过网络传输公钥。为了使数据更安全,我们还秘密共享公钥。为了在网络上安全地共享公钥skspub,我们使用了Diffie-Hellman密钥交换技术。Alice和Bob之间共享秘密的基本不同- hellman交换可以通过以下方式进行:
Alice和Bob生成自己的私有/公共密钥(kA; kA)和(kB; kB)。它们都发布或交换自己的公钥,并为自己保留私钥。
显然,它是成立的
S = kA ? KB = kA ? KB ? G = KB ? kA ? G = KB ? kA
(3)
Alice可以私下计算S=kA·KB, Bob S= KB·kA,允许他们使用这个值作为共享秘密。例如,如果Alice有一条消息m要发送给Bob,她可以哈希共享的秘密h= h (S),计算x=m+h,然后将x发送给Bob。Bob计算h ' = h (S),计算m=x - h ',并学习m。
由于DLP(离散对数问题)的存在,外部观察者将无法轻松地计算共享秘密,这将阻止它们结束kA或kB。由于哈希函数的输出是“随机的”,因此消息m从知道x、KA和KB的对手那里获得了理论上的信息安全。
6. Algorithms to Implement Cryptographic Techniques between Sender and Receiver in Our Model
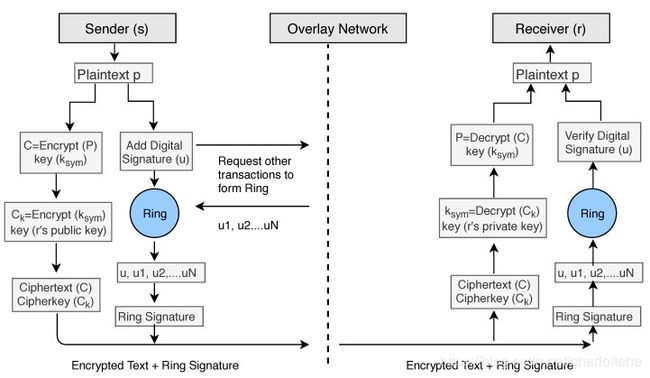
In our encryption Algorithm 1, we encrypt the data_file by using the symmetric key ksym and produce a ciphertext file C. After encryption, we use double encryption technique and encrypt the key ksym by using public key cryptography. We use the receivers public key rkpub to encrypt the symmetric key ksym and send the encrypted key along with the ciphertext C. We denote the encrypted symmetric key with Ck.
| Algorithm 1 Data Encryption. |
|
1:functionEncryption (data_file) 2: if user confirm data preservation over blockchain then 3: Generate a symmetric key ksym 4: C←Encryptsym (data_file,ksym) 5: Ck←Encryptasym(ksym,rkpub) 6: else 7: Do nothing 8: end if 9:end function
|
6. 在我们的模型中实现发送方和接收方之间的加密技术的算法
在我们的加密算法1中,我们使用对称密钥ksym加密data_file,生成密文文件c。加密后,我们使用双重加密技术,使用公钥加密对密钥ksym进行加密。我们使用接收方公钥rkpub加密对称密钥ksym,并将加密密钥与密文c一起发送。我们用Ck表示加密的对称密钥。
算法1数据加密。
1:functionEncryption (data_file)
2:如果用户确认在区块链上保存数据,则
3:生成对称密钥ksym
4:C←Encryptsym (data_file ksym)
5:Ck←Encryptasym (ksym rkpub)
6:其他的
7:什么都不做
8:如果
9:结束函数
For the digital signature senders can use two keys skspub,skspriv that is different from the encryption/decryption keys. To add the digital signature, the sender first passes the data file to the Hash Function and creates the hash value hashp of the data. Then he/she signs the data using his/her private key skspriv by passing the value of the private key and hash value hashp to the Signature Algorithm. The signers public key skspub can be used to verify data on the receiver’s side. To apply the Anonymity of the patient or user, we add ring signature in our Algorithm 2. The user will ask the network for other accounts who also want to add ring signature to their transactions. The network will provide him/her a set of users who also wish to apply ring signature. The sender’s transaction is then mixed with other users’ transactions and then send it over the network. No one will be able to identify the original signer of the ring group. The process is described in the block diagram (see Figure 11) of our model.
| Algorithm 2 Ring Signature and Public Key Sharing. |
|
1:functionSignature (data_file) 2. if user chose anonymity over blockchain then 3: Generate an asymmetric public-private key pair skspub,skspriv 4: hashp← calculate hash of the data_file 5: Create the Digital Signature using hashp and signers private key skspriv 6: Share the public key skspub to the receiver using Diffie–Hellman key exchange 7: Mix the signature with another network group to form a ring 8:end if 9:end function
|
对于数字签名发送者,可以使用两个密钥skspub,即与加密/解密密钥不同的skspriv。要添加数字签名,发送方首先将数据文件传递给Hash函数,并创建数据的Hash值hashp。然后,通过将私钥的值和散列值hashp传递给签名算法,使用私钥skspriv对数据进行签名。签名者公钥skspub可用于验证接收方的数据。为了应用患者或用户的匿名性,我们在算法2中添加了环签名。用户将向网络询问其他也想在其事务中添加戒指签名的帐户。网络将为他/她提供一组用户,他们也希望应用戒指签名。然后,发送方的事务与其他用户的事务混合,然后通过网络发送。没有人能够识别戒指组的原始签名者。这个过程在我们模型的框图(见图11)中进行了描述。
算法2环签名与公钥共享。
1:functionSignature (data_file)
2:如果用户选择匿名而不是区块链
3:生成非对称的公私密钥对skspub,skspriv
4:hashp←计算data_file的哈希值
5:使用hashp和签名者私有密钥skspriv创建数字签名
6:使用Diffie-Hellman密钥交换将公钥skspub共享给接收者
7:将签名与另一个网络组混合,形成一个环
8:如果
9:结束函数
7. Model Implementation
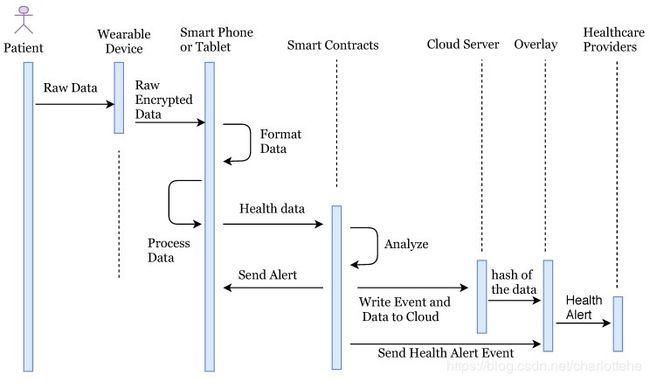
In our system, the patient is equipped with wearable devices such as a blood pressure monitor, insulin pump, or other known devices. Random patients are not allowed to connect with the network, they can only connect once they make an account and provide identity verification documents. Once account verifies the documents provided, users are allowed to access the network. The health information is sent to the smart devices such as a smartphone or tablet for the formatting and aggregation by the application (see Figure 1). Once complete, the formatted information is sent to the relevant smart contract for full analysis along with the threshold values as required. The threshold value decides whether the health reading is NORMAL as per standard readings or not. If the health reading is ABNORMAL, then the smart contract will create an event and send an alert to the overlay network and to the patient. Also, it stores the abnormal readings to cloud servers and cloud server can then transfer the hash of the stored data to the overlay network. When health data is transferred to the cloud server, the sender adds a digital signature to the data. Overlay network then sends an alert to the health providers. Here, we are not storing the health readings to the overlay network, but we only store the transaction alert to the overlay network.
Health Alert Event should also be anonymous, and privacy preserved to the overlay network. We treat this alert as a transaction of the specific user and apply all advanced cryptographic techniques according to the algorithm explained in Section 6. Here the entity who is sending the information could be treated as a sender and who is receiving the information could be treated as a receiver. Here we only describe the flow of data in our system and do not describe all encryption/decryption technical details as we have already explained the cryptographic techniques in above sections by taking a general model of the sender, receiver, and network. An overlay network contains the public key information of all connected nodes and hash index of the stored data over the cloud. Once the healthcare provider node gets an alert, he/she access the full health reading of patient for which he/she is authorized over the network. We summarize the logical flow execution of the system in Figure 12.
7. 模型实现
在我们的系统中,患者配备了可穿戴设备,如血压监测器、胰岛素泵或其他已知设备。随机抽取的患者不允许连接网络,他们只能在开立账户并提供身份验证文件后才能连接。一旦account验证了所提供的文档,就允许用户访问网络。健康信息由应用程序发送到智能手机或平板电脑等智能设备进行格式化和聚合(见图1),完成后将格式化信息发送到相关智能契约进行全面分析,并根据需要设置阈值。阈值决定健康读数是否与标准读数正常。如果健康读数不正常,那么智能契约将创建一个事件,并向覆盖网络和患者发送警报。此外,它将异常读数存储到云服务器,然后云服务器可以将存储的数据哈希传输到覆盖网络。当健康数据传输到云服务器时,发送方向数据添加一个数字签名。然后Overlay network向健康提供者发送警报。在这里,我们没有将健康读数存储到覆盖网络,但是我们只将事务警报存储到覆盖网络。
健康警报事件也应该是匿名的,隐私保护到覆盖网络。我们将此警报视为特定用户的事务,并根据第6节中解释的算法应用所有高级加密技术。在这里,发送信息的实体可以被视为发送者,接收信息的实体可以被视为接收者。在这里,我们只描述系统中的数据流,而不描述所有加密/解密技术细节,因为我们已经在上面几节中通过使用发送方、接收方和网络的一般模型解释了加密技术。覆盖网络包含所有连接节点的公钥信息和云上存储数据的哈希索引。一旦医疗保健提供者节点收到警报,他/她将访问通过网络授权的患者的完整健康读数。我们在图12中总结了系统的逻辑流执行。
8. Security Evaluation
In any model, there are three main security requirements that need to be addressed by model designers: Confidentiality, Integrity, and Availability. Confidentiality makes sure that only authorized users can access the system. Integrity is responsible for messages sent to the destination without any change, and Availability means data is always available to the users when needed. We evaluate the security margin of the model under various threats. In this model, the adversary can be a home device, the cluster head, or any other node in the network or part of the cloud storage. These adversaries can discard transactions, sniff communications, create false transactions, or change or delete information from the storage. However, our models’ basic aim is to save the network from the adversary, and we focus on this rather than individual nodes. If a node is connected to the network and he verifies proof of authority and registered by the network, then we assume that he is an honest node. In the case where the network detects some malicious activity by the given node, we can block the malicious node from the network. We summarize the security requirement evaluation in Table 2.
Table 2
Security Requirement Evaluation.
| Requirement |
Model Solution |
Reference |
| Confidentiality |
Proof of Authority, Public Key |
Section 6 |
| Authorization |
Using Public Key and Lightweight Digital Signature |
Section 5.2 |
| User control |
Proof of Authority |
Section 7 |
| Integrity |
Hashing of data blocks |
Section 4 |
| Availability |
Achieved by limiting acceptable transactions |
Section 4 |
| Anonymity |
Lightweight Ring Signature |
Section 5.3 |
8. 安全评估
在任何模型中,都有三个主要的安全需求需要模型设计人员处理:机密性、完整性和可用性。机密性确保只有授权用户才能访问系统。完整性负责将消息发送到目的地而不做任何更改,可用性意味着在需要时数据总是对用户可用。我们评估了模型在各种威胁下的安全裕度。在这个模型中,竞争对手可以是家庭设备、集群头或网络中的任何其他节点或云存储的一部分。这些对手可以丢弃事务、嗅探通信、创建假事务或更改或删除存储中的信息。然而,我们的模型的基本目标是将网络从竞争对手那里拯救出来,我们关注的是这一点,而不是单个节点。如果一个节点连接到网络,并且他验证了权限证明并被网络注册,那么我们假设他是一个诚实的节点。在网络检测到给定节点有恶意活动的情况下,可以从网络中屏蔽恶意节点。我们在表2中总结了安全性需求评估。
We considered a few attacks that could be possible in this model and find a security margin against them in our model:
Denial of Service (DoS) Attack: In such an attack, the attacker tries to prevent the authentic user from accessing the service in the network. In such cases, the adversary can launch fraudulent transactions and can increase traffic in the network. However, in our system, random users cannot join the network without proof of authority. Regardless, consider an adversary attacked the network and started sending fake transactions to the network. In such a case, cluster head will check his/her public address and if it is not available or registered with cluster head then it will not broadcast the transaction to the network and forward the request to other clusters. If the public address is not available or is a registered public address, no cluster will accept the request and after many attempts, cluster head will finally block him/her in the network, and therefore our system is safe against this attack. However, a particular attacker can attack many times with a different public address.
Mining Attack: Consider an adversary hacked a few cluster heads and started controlling multiple cluster heads. In such a situation, fake mining is possible but once it is detected by other cluster heads or nodes, they can easily trace the fake cluster heads. This is because in our model if any cluster head approves a block then it will add a digital signature over that block and without the digital signature other cluster heads will not accept a new block in the network. Once a fake cluster head is detected by the network it can be modified by the nodes in that cluster.
Storage Attack: If an adversary attacked the cloud storage, he/she can remove, change, or add data in the cloud. However, in our model we are using a hash of the data block stored in the cloud, therefore changes in the data can easily be detected. However, in our model, if any user wants to store or manage data over the cloud, he needs to digitally sign the data and can only access his/her data or others’ data with permission. In such cases, if someone else modifies the data, the cluster heads can block them from the network.
Dropping Attack: For such an attack, the adversary should have to control cluster heads. The cluster heads under the attacker’s control will not be able to do anything in the network. They will drop all received blocks and they will not be connected to other nodes or clusters. As a solution here the nodes in the network can elect another node as a cluster head.
我们考虑了在这个模型中可能发生的一些攻击,并在我们的模型中找到了针对这些攻击的安全裕度:
拒绝服务攻击:在这种攻击中,攻击者试图阻止真实用户访问网络中的服务。在这种情况下,对手可以发起欺诈性交易,增加网络流量。但是,在我们的系统中,没有权限证明,随机用户不能加入网络。无论如何,假设一个对手攻击了网络并开始向网络发送假事务。在这种情况下,集群负责人将检查他/她的公共地址,如果该地址不可用或没有在集群负责人处注册,那么它将不会将事务广播到网络并将请求转发给其他集群。如果公共地址不可用或者是注册的公共地址,没有集群会接受请求,经过多次尝试,集群头最终会在网络中阻塞他/她,因此我们的系统不会受到这种攻击。然而,特定的攻击者可以使用不同的公共地址进行多次攻击。
挖掘攻击:假设一个对手攻击了几个集群头并开始控制多个集群头。在这种情况下,可以进行伪挖掘,但是一旦被其他集群头或节点检测到,它们就可以很容易地跟踪伪集群头。这是因为在我们的模型中,如果任何集群头批准了一个块,那么它将在该块上添加一个数字签名,如果没有数字签名,其他集群头将不会接受网络中的新块。一旦网络检测到一个伪集群头,它就可以被该集群中的节点修改。
存储攻击:如果对手攻击云存储,他/她可以删除、更改或添加云中的数据。然而,在我们的模型中,我们使用了存储在云中的数据块的散列,因此可以很容易地检测到数据中的更改。然而,在我们的模型中,如果任何用户想要通过云存储或管理数据,他需要对数据进行数字签名,并且只有在获得许可的情况下才能访问他/她的数据或其他人的数据。在这种情况下,如果其他人修改了数据,集群头可以将它们从网络中屏蔽。
下降攻击:这样的攻击,对手必须控制簇头。在攻击者控制下的集群头将无法在网络中执行任何操作。它们将删除所有接收到的块,并且不会连接到其他节点或集群。作为一种解决方案,网络中的节点可以选择另一个节点作为集群头。
9. Future Work
This paper takes an initial look at a blockchain-based IoT model glimpsing into an advanced security and privacy model to be used in any current IoT-based remote monitoring system. Our main future direction for this work or any researchers who wish to further this work is to implement the system in a testable system to provide some real work security guarantees apart from what has already been established for all the individual cryptographic components used. We also hope to find an industrial partner to help bring some of the novel ideas mentioned in this work to become commercially available.
- 未来的工作
本文对基于区块链的物联网模型进行了初步研究,并对目前任何基于IoT的远程监控系统中使用的先进安全和隐私模型进行了初步探讨。对于这项工作,或者任何希望进一步开展这项工作的研究人员,我们未来的主要方向是在一个可测试的系统中实现该系统,以提供一些真正的工作安全保障,而不是为所使用的所有单独的加密组件提供已经建立的安全保障。我们也希望找到一个工业伙伴,以帮助把一些在这项工作中提到的新奇的想法商业化。
10. Conclusions
IoT privacy and security is one of the most significant issues nowadays in academia and industry. Due to resource constraint factor of IoT, existing security solutions are not well suited. Our proposed architecture provides a solution to most of the security and privacy threats while considering the resource constraint factor of IoT. In this paper, we introduced a novel hybrid approach that combines the advantages of the private key, public key, blockchain and many other lightweight cryptographic primitives to develop a patient-centric access control for electronic medical records, capable of providing security and privacy. We also raise open questions to reduce various attacks such as DoS, modification attacks etc. However, resource-constraints of IoT are key challenges towards answering such problems or seizures.
10. 结论
物联网的隐私和安全是当今学术界和工业界最重要的问题之一。由于物联网的资源约束因素,现有的安全解决方案并不适用。我们提出的架构在考虑物联网资源约束因素的同时,为大部分安全和隐私威胁提供了一种解决方案。在本文中,我们引入了一种新的混合方法,它结合了私钥、公钥、区块链和其他轻量级密码原语的优点,开发了一种以病人为中心的电子病历访问控制,能够提供安全和隐私。我们也提出了开放的问题,以减少各种攻击,如DoS,修改攻击等。然而,物联网的资源约束是解决此类问题或癫痫发作的关键挑战。
参考文献
1. Nakamoto S. Bitcoin: A Peer-to-Peer Electronic Cash System. BN Publishing; La Vergne, TN, USA: 2008. [Google Scholar]
2. Malina L., Hajny J., Dzurenda P., Ricci S. Lightweight Ring Signatures for Decentralized Privacy-preserving Transactions; Proceedings of the 15th International Joint Conference on e-Business and Telecommunications; Porto, Portugal. 26–28 July 2018; pp. 526–531. [CrossRef] [Google Scholar]
3. Mettler M. Blockchain technology in healthcare: The revolution starts here; Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom); Munich, Germany. 14–17 September 2016; [CrossRef] [Google Scholar]
4. Dorri A., Kanhere S.S., Jurdak R., Gauravaram P. Blockchain for IoT security and privacy: The case study of a smart home; Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops); Kona, HI, USA. 13–17 March 2017; pp. 618–623. [CrossRef] [Google Scholar]
5. Zhang J., Xue N., Huang X. A Secure System For Pervasive Social Network-Based Healthcare. IEEE Access. 2016;4:9239–9250. doi: 10.1109/ACCESS.2016.2645904. [CrossRef] [Google Scholar]
6. Zhu X., Badr Y. Identity Management Systems for the Internet of Things: A Survey Towards Blockchain Solutions. Sensors. 2018;18:4215. doi: 10.3390/s18124215. [PMC free article] [PubMed] [CrossRef] [Google Scholar]
7. Yue X., Wang H., Jin D., Li M., Jiang W. Healthcare Data Gateways: Found Healthcare Intelligence on Blockchain with Novel Privacy Risk Control. J. Med. Syst. 2016;40:218. doi: 10.1007/s10916-016-0574-6. [PubMed] [CrossRef] [Google Scholar]
8. Panarello A., Tapas N., Merlino G., Longo F., Puliafito A. Blockchain and IoT Integration: A Systematic Survey. Sensors. 2018;18:2575. doi: 10.3390/s18082575. [PMC free article] [PubMed] [CrossRef] [Google Scholar]
9. Srivastava G., Dwivedi A.D., Singh R. PHANTOM Protocol as the New Crypto-Democracy. In: Saeed K., Homenda W., editors. Computer Information Systems and Industrial Management. Springer International Publishing; Cham, Switzerland: 2018. pp. 499–509. [Google Scholar]
10. Srivastava G., Dwivedi A.D., Singh R. Crypto-democracy: A Decentralized Voting Scheme using Blockchain Technology; Proceedings of the 15th International Joint Conference on e-Business and Telecommunications; Porto, Portugal. 26–28 July 2018; pp. 508–513. [CrossRef] [Google Scholar]
11. Buccafurri F., Fotia L., Lax G. Social Signature: Signing by Tweeting. In: Kő A., Francesconi E., editors. Electronic Government and the Information Systems Perspective. Springer International Publishing; Cham, Switzerland: 2014. pp. 1–14. [Google Scholar]
12. Buccafurri F., Fotia L., Lax G. A privacy-preserving e-participation framework allowing citizen opinion analysis. Electron. Gov. Int. J. 2015;11:185–206. doi: 10.1504/EG.2015.070131. [CrossRef] [Google Scholar]
13. Christidis K., Devetsikiotis M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access. 2016;4:2292–2303. doi: 10.1109/ACCESS.2016.2566339. [CrossRef] [Google Scholar]
14. Qu C., Tao M., Yuan R. A Hypergraph-Based Blockchain Model and Application in Internet of Things-Enabled Smart Homes. Sensors. 2018;18:2784. doi: 10.3390/s18092784. [PMC free article] [PubMed] [CrossRef] [Google Scholar]
15. Irving G., Holden J. How blockchain-timestamped protocols could improve the trustworthiness of medical science. F1000Research. 2016;5 doi: 10.12688/f1000research.8114.1. [PMC free article] [PubMed] [CrossRef] [Google Scholar] Retracted
16. He W., Liu X., Nguyen H., Nahrstedt K., Abdelzaher T. PDA: Privacy-Preserving Data Aggregation in Wireless Sensor Networks; Proceedings of the IEEE INFOCOM 2007—26th IEEE International Conference on Computer Communications; Anchorage, AK, USA. 6–12 May 2007; pp. 2045–2053. [CrossRef] [Google Scholar]
17. Li N., Zhang N., Das S.K., Thuraisingham B. Privacy preservation in wireless sensor networks: A state-of-the-art survey. Ad Hoc Netw. 2009;7:1501–1514. doi: 10.1016/j.adhoc.2009.04.009. [CrossRef] [Google Scholar]
18. Li M., Yu S., Ren K., Lou W. Securing Personal Health Records in Cloud Computing: Patient-Centric and Fine-Grained Data Access Control in Multi-owner Settings. In: Jajodia S., Zhou J., editors. Security and Privacy in Communication Networks. Springer Berlin Heidelberg; Berlin/Heidelberg, Germany: 2010. pp. 89–106. [Google Scholar]
19. Mandl K.D., Markwell D., MacDonald R., Szolovits P., Kohane I.S. Public standards and patients’ control: how to keep electronic medical records accessible but private. BMJ. 2001;322:283–287. doi: 10.1136/bmj.322.7281.283. [PMC free article] [PubMed] [CrossRef] [Google Scholar]
20. Wu J., Dong M., Ota K., Li J., Guan Z. Big Data Analysis-Based Secure Cluster Management for Optimized Control Plane in Software-Defined Networks. IEEE Trans. Netw. Serv. Manag. 2018;15:27–38. doi: 10.1109/TNSM.2018.2799000. [CrossRef] [Google Scholar]
21. Wu J., Dong M., Ota K., Li J., Guan Z. FCSS: Fog Computing based Content-Aware Filtering for Security Services in Information Centric Social Networks. IEEE Trans. Emerg. Top. Comput. 2018 doi: 10.1109/TETC.2017.2747158. [CrossRef] [Google Scholar]
22. Guo L., Dong M., Ota K., Li Q., Ye T., Wu J., Li J. A Secure Mechanism for Big Data Collection in Large Scale Internet of Vehicle. IEEE Internet Things J. 2017;4:601–610. doi: 10.1109/JIOT.2017.2686451. [CrossRef] [Google Scholar]
23. Wu J., Ota K., Dong M., Li C. A Hierarchical Security Framework for Defending Against Sophisticated Attacks on Wireless Sensor Networks in Smart Cities. IEEE Access. 2016;4:416–424. doi: 10.1109/ACCESS.2016.2517321. [CrossRef] [Google Scholar]
24. Dwivedi A.D., Morawiecki P., Wójtowicz S. Finding Differential Paths in ARX Ciphers through Nested Monte-Carlo Search. Int. J. Electron. Telecommun. 2018;64:147–150. [Google Scholar]
25. Dwivedi A.D., Morawiecki P., Singh R., Dhar S. Differential-linear and related key cryptanalysis of round-reduced scream. Inf. Process. Lett. 2018;136:5–8. doi: 10.1016/j.ipl.2018.03.010. [CrossRef] [Google Scholar]
26. Dwivedi A.D., Srivastava G. Differential Cryptanalysis of Round-Reduced LEA. IEEE Access. 2018 doi: 10.1109/ACCESS.2018.2881130. [CrossRef] [Google Scholar]
27. Dhar Dwivedi A., Morawiecki P., Wójtowicz S. Differential and Rotational Cryptanalysis of Round-reduced MORUS; Proceedings of the 14th International Joint Conference on e-Business and Telecommunications; Madrid, Spain. 24–26 July 2017; pp. 275–284. [CrossRef] [Google Scholar]
28. Dwivedi A.D., Morawiecki P. Differential Cryptanalysis in ARX Ciphers, Application to SPECK. [(accessed on 9 January 2019)];2018 Cryptology ePrint Archive: Report 2018/899. Available online: https://eprint.iacr.org/2018/899.
29. Dwivedi A.D., Morawiecki P., Wójtowicz S. Differential-linear and Impossible Differential Cryptanalysis of Round-reduced Scream; Proceedings of the 14th International Joint Conference on e-Business and Telecommunications; Madrid, Spain. 24–26 July 2017; pp. 501–506. [CrossRef] [Google Scholar]
30. Dwivedi A.D., Klouček M., Morawiecki P., Nikolić I., Pieprzyk J., Wójtowicz S. SAT-based Cryptanalysis of Authenticated Ciphers from the CAESAR Competition; Proceedings of the 14th International Joint Conference on e-Business and Telecommunications; Madrid, Spain. 24–26 July 2017; pp. 237–246. [CrossRef] [Google Scholar]
31. Josang A., Haller J. Dirichlet Reputation Systems; Proceedings of the Second International Conference on Availability, Reliability and Security (ARES’07); Vienna, Austria. 10–13 April 2007; pp. 112–119. [CrossRef] [Google Scholar]
32. Chu Y., Rao S., Seshan S., Zhang H. Enabling Conferencing Applications on the Internet Using an Overlay Muilticast Architecture. SIGCOMM Comput. Commun. Rev. 2001;31:55–67. doi: 10.1145/964723.383064. [CrossRef] [Google Scholar]
33. Beaulieu R., Treatman-Clark S., Shors D., Weeks B., Smith J., Wingers L. The SIMON and SPECK lightweight block ciphers; Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC); San Francisco, CA, USA. 8–12 June 2015; [CrossRef] [Google Scholar]
34. Rivest R.L., Shamir A., Tauman Y. How to Leak a Secret. In: Boyd C., editor. Advances in Cryptology—ASIACRYPT 2001. Springer Berlin Heidelberg; Berlin/Heidelberg, Germany: 2001. pp. 552–565. [Google Scholar]