网鼎杯朱雀组逆向 tree
找到main函数
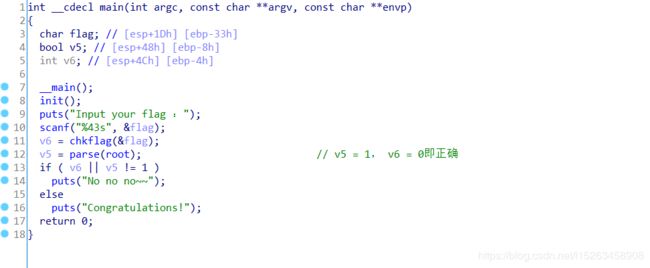
进入到chkflag函数,发现其是将输入的flag中的xxx每一个x都换成2进制的形式,每一个4位,然后存在glockflag中
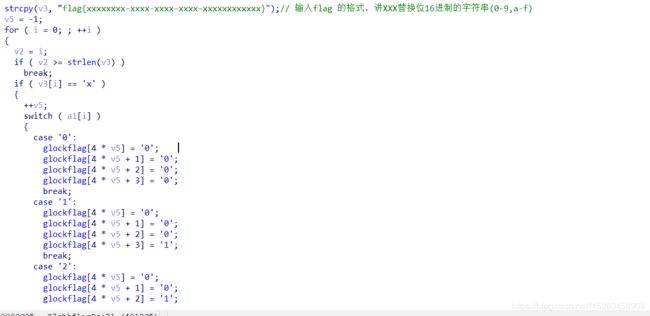
parse函数是将glockflag中的二进制拿出来,0代表左,1代表右,开始遍历叶子节点,如果找到的叶子节点是zvzjyvosgnzkbjjjypjbjdvmsjjyvsjx,就正确
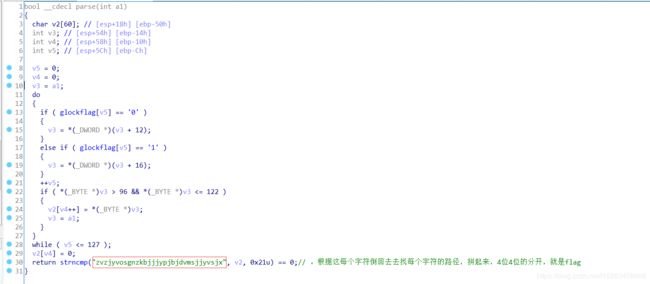
我们先将 每个节点及其路径打印出来
def traverse_leaf(pnode):
if pnode != 0:
if Dword(pnode + 12) == 0 and Dword(pnode + 16) == 0:
print(chr(Byte(pnode)))
print("".join(a))
lujing.append([chr(Byte(pnode)), "".join(a)])
a.append('0')
traverse_leaf(Dword(pnode + 12))
a.append('1')
traverse_leaf(Dword(pnode + 16))
if pnode != 0X0406530:
a.pop()
traverse_leaf(0X0406530)
print(lujing)
[[‘y’, ‘0000’], [‘b’, ‘00010’], [‘q’, ‘00011’], [‘g’, ‘0010’], [‘f’, ‘0011’], [‘j’, ‘010’], [‘w’, ‘01100’], [‘p’, ‘01101’], [‘x’, ‘011100’], [‘d’, ‘0111010’], [‘i’, ‘0111011’], [‘k’, ‘01111’], [‘s’, ‘100’], [‘z’, ‘1010’], [‘n’, ‘1011’], [‘c’, ‘11000’], [‘t’, ‘110010’], [‘e’, ‘110011’], [‘h’, ‘1101’], [‘o’, ‘11100’], [‘l’, ‘1110100’], [‘u’, ‘11101010’], [‘r’, ‘111010110’], [‘a’, ‘111010111’], [‘m’, ‘111011’], [‘v’, ‘1111’]]
然后在开始写脚本,将 zvzjyvosgnzkbjjjypjbjdvmsjjyvsjx 转成路径,然后拼起来,4位4位的分开就是flag中的xxxx
lujing = [['y', '0000'], ['b', '00010'], ['q', '00011'], ['g', '0010'], ['f', '0011'], ['j', '010'], ['w', '01100'], ['p', '01101'], ['x', '011100'], ['d', '0111010'], ['i', '0111011'], ['k', '01111'], ['s', '100'], ['z', '1010'], ['n', '1011'], ['c', '11000'], ['t', '110010'], ['e', '110011'], ['h', '1101'], ['o', '11100'], ['l', '1110100'], ['u', '11101010'], ['r', '111010110'], ['a', '111010111'], ['m', '111011'], ['v', '1111']]
res = "zvzjyvosgnzkbjjjypjbjdvmsjjyvsjx"
flag01 = ""
flagx = ""
for i in res:
for j in lujing:
if i in j[0]:
flag01 += j[1]
print(flag01)
for i in range(0, len(flag01), 4):
tmp = "%x" % int(flag01[i:i+4], 2)
flagx += tmp
print(flagx)
最终打印出flagx是afa41fc8574f12481a849d7f7120f89c
将flag{xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}替换掉,即
flag为flag{afa41fc8-574f-1248-1a84-9d7f7120f89c}
原文我发在吾爱破解了,欢迎大佬们关注我的吾爱号: https://www.52pojie.cn/thread-1181476-1-1.html