2020网鼎杯青龙组部分题目WP
0x00 Crypto之boom
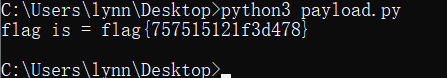
下载下来是个exe文件,拖到cmd运行(切记一定不要双击,用cmd打开)
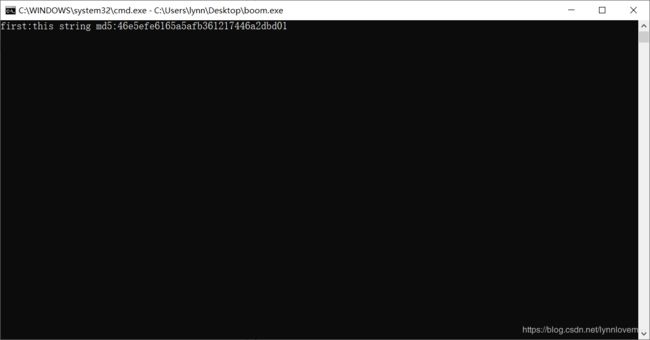
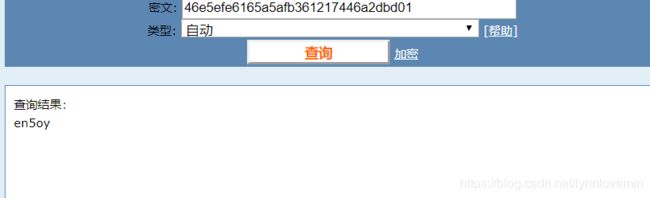
找个md5网站解密,得到明文
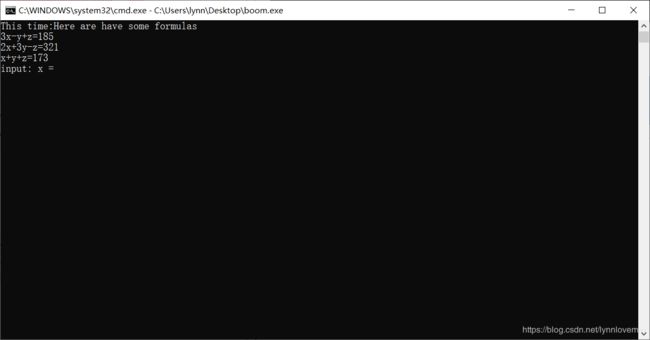
输入后得到一个方程组,解方程组(找个就不用说了,初中知识)
输入有又出现一个方程:
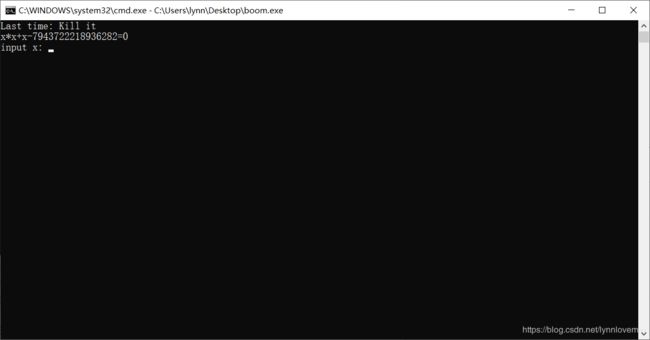
解出来输入x可得flag:

0x01 Reverse之signal
用IDA逆向后,可得关键算法:
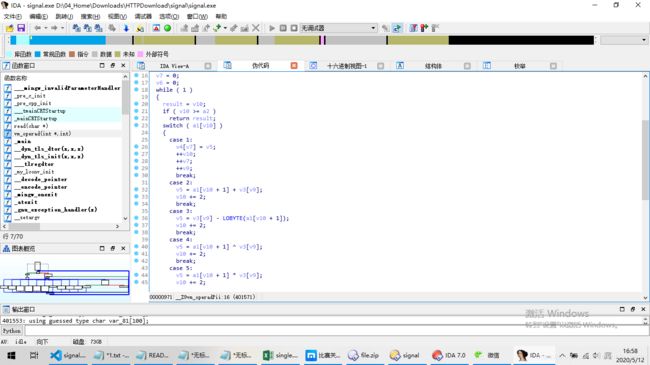
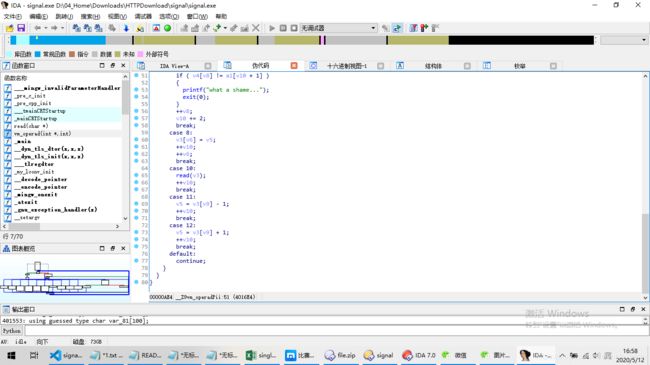
他是将一串数字做了不同操作符运算,得到一个ascii码,即为flag,于是写出爆破payload如下:
# -*- coding: UTF-8 -*-
code = [10,4,16,8,3,5,1,4,32,8,5,3,1,3,2,8,11,1,12,8,4,4,1,5,3,8,3,33,1,11,8,11,1,4,9,8,3,32,1,2,81,8,4,36,1,12,8,11,1,5,2,8,2,37,1,2,54,8,4,65,1,2,32,8,5,1,1,5,3,8,2,37,1,4,9,8,3,32,1,2,65,8,12,1,7,34,7,63,7,52,7,50,7,114,7,51,7,24,7,167,7,49,7,241,7,40,7,132,7,193,7,30,7,122]
result = [34,63,52,50,114,51,24,167,49,241,40,132,193,30,122]
flag = []
def encode(x,code):
i=0
achar=0
while(i