Kubernetes-1.16部署之四 Istio
什么是Istio?
Istio是Service Mesh(服务网格)的主流实现方案。该方案降低了与微服务架构相关的复杂性,并提供了负载均衡、服务发现、流量管理、断路器、监控、故障注入和智能路由等功能特性。
其中,Sidecar模式是一种将应用功能从应用本身剥离出来作为单独进程的方式。该模式允许我们向应用无侵入添加多种功能,避免了为满足第三方组件需求而向应用添加额外的配置代码。从某种意义上来说,服务对于网络是无感知的,只知道所附加的sidecar代理,它将网络依赖抽象成了Sidecar。
在Service Mesh中,我们需要了解Data Plane和Control Plane两个概念:
- Data Plane:作用是处理网格内服务间的通信,并完成服务发现、负载均衡、流量管理、健康检查等功能;
- Control Plane:作用是管理和配置智能代理用于路由流量,同时配置Mixers来应用策略、收集指标。
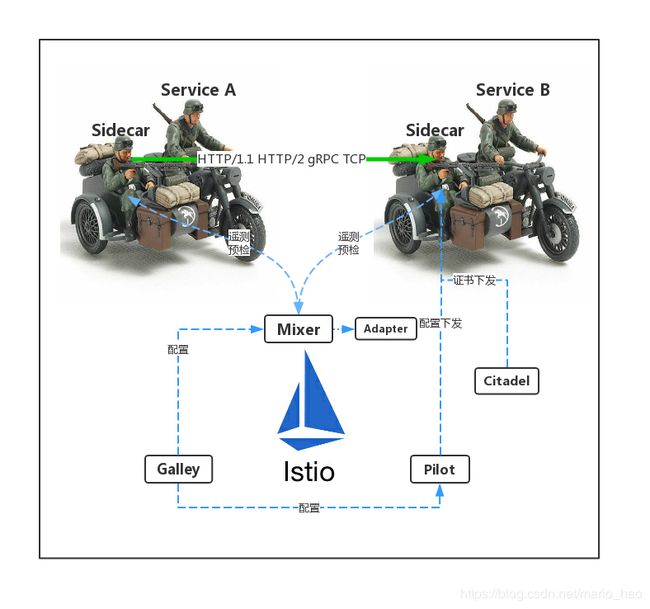
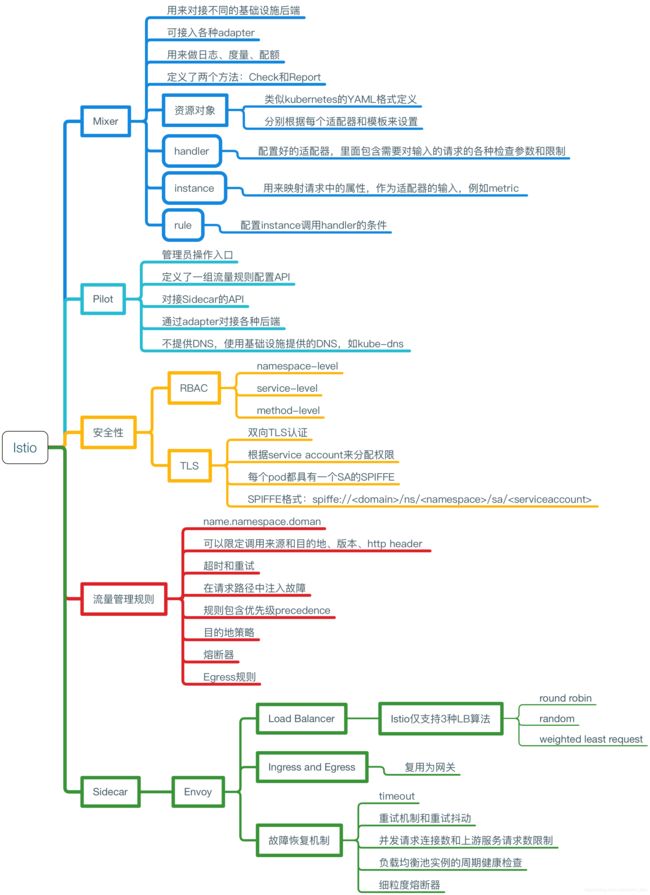
Istio核心组件
- Envoy:Istio 使用 Envoy调解服务网格中所有服务的入站和出站流量。属于数据平面。
- Mixer:负责在服务网格上执行访问控制和使用策略,以及收集从Envoy和其他服务自动监控到的数据。
- Pilot:为 Envoy sidecar 提供服务发现功能,为智能路由(例如 A/B 测试、金丝雀部署等)和弹性(超时、重试、熔断器等)提供流量管理功能。属于控制平面。
- Citadel:提供访问控制和用户身份认证功能。
Istio可视化管理组件
- Vistio:用于近乎实时地监控应用程序和集群之间的网络流量。
- Kiali:提供可视化服务网格拓扑、断路器和请求率等功能。Kiali还包括 Jaeger Tracing,可以提供开箱即用的分布式跟踪功能。
- jaeger:用于展示istio微服务调用链关系,以及微服务工作状态监测。注意,在生产环境中,应使用Elasticsearch或cassandra持久化存储jaeger数据。
Kiali、Jaeger、Prometheus、Grafana管理工具,将和Istio一并部署。
一、下载istio和helm(istio-1.4.2版不支持helm-3.x)
# mkdir /opt/kubernetes/istio
# ls /opt/software/
helm-v2.16.1-linux-amd64.tar.gz istio-1.4.2-linux.tar.gz
# tar -zxvf helm-v2.16.1-linux-amd64.tar.gz
# cp linux-amd64/helm /opt/kubernetes/bin/
# tar -zxvf istio-1.4.2-linux.tar.gz
# cp istio-1.4.2/bin/istioctl /opt/kubernetes/bin/
# istioctl verify-install //确认环境是否满足istio安装要求二、创建istio命名空间
# kubectl create namespace istio-system
namespace/istio-system created三、安装istio自定义资源CRDs
# cd /opt/software/istio-1.4.2
# for i in install/kubernetes/helm/istio-init/files/crd*yaml; do kubectl apply -f $i; done查看已安装信息,CRDs创建数必需满足23个
# kubectl get crds | grep 'istio.io' | wc -l
23
# kubectl get CustomResourceDefinition
NAME CREATED AT
adapters.config.istio.io 2019-12-23T07:46:08Z
attributemanifests.config.istio.io 2019-12-23T07:46:04Z
authorizationpolicies.security.istio.io 2019-12-23T07:46:10Z
certificates.certmanager.k8s.io 2019-12-23T07:46:12Z
challenges.certmanager.k8s.io 2019-12-23T07:46:13Z
clusterissuers.certmanager.k8s.io 2019-12-23T07:46:11Z
clusterrbacconfigs.rbac.istio.io 2019-12-23T07:46:04Z
destinationrules.networking.istio.io 2019-12-23T07:46:04Z
envoyfilters.networking.istio.io 2019-12-23T07:46:05Z
gateways.networking.istio.io 2019-12-23T07:46:05Z
handlers.config.istio.io 2019-12-23T07:46:09Z
httpapispecbindings.config.istio.io 2019-12-23T07:46:05Z
httpapispecs.config.istio.io 2019-12-23T07:46:05Z
ingressroutes.traefik.containo.us 2019-12-19T13:25:45Z
ingressroutetcps.traefik.containo.us 2019-12-19T13:25:45Z
instances.config.istio.io 2019-12-23T07:46:08Z
issuers.certmanager.k8s.io 2019-12-23T07:46:11Z
meshpolicies.authentication.istio.io 2019-12-23T07:46:05Z
middlewares.traefik.containo.us 2019-12-19T13:25:46Z
orders.certmanager.k8s.io 2019-12-23T07:46:12Z
policies.authentication.istio.io 2019-12-23T07:46:05Z
quotaspecbindings.config.istio.io 2019-12-23T07:46:06Z
quotaspecs.config.istio.io 2019-12-23T07:46:06Z
rbacconfigs.rbac.istio.io 2019-12-23T07:46:06Z
rules.config.istio.io 2019-12-23T07:46:07Z
serviceentries.networking.istio.io 2019-12-23T07:46:07Z
servicerolebindings.rbac.istio.io 2019-12-23T07:46:07Z
serviceroles.rbac.istio.io 2019-12-23T07:46:07Z
sidecars.networking.istio.io 2019-12-23T07:46:09Z
templates.config.istio.io 2019-12-23T07:46:08Z
tlsoptions.traefik.containo.us 2019-12-19T13:25:46Z
virtualservices.networking.istio.io 2019-12-23T07:46:08Z四、部署istio核心组件(部署环境最低配置2cpn,4G memory)
# cd /opt/software/istio-1.4.2
# kubectl apply -f install/kubernetes/istio-demo.yaml查看创建的资源
# kubectl -n istio-system get pods
NAME READY STATUS RESTARTS AGE
grafana-7797c87688-2bzk5 1/1 Running 0 9m11s
istio-citadel-65c9f49c76-q2w5s 1/1 Running 0 9m8s
istio-egressgateway-5b6cbd4c96-7knwd 0/1 Running 0 9m12s
istio-galley-c5cb9c77d-58fws 1/1 Running 0 9m12s
istio-grafana-post-install-1.4.2-npkhx 0/1 Completed 0 9m15s
istio-ingressgateway-7b66b7c7c-2cq7z 0/1 Running 0 9m11s
istio-pilot-7d5c97cc67-ft78k 1/2 Running 2 9m9s
istio-policy-86775c9966-j9jq7 2/2 Running 6 9m10s
istio-security-post-install-1.4.2-whffb 0/1 Completed 0 9m14s
istio-sidecar-injector-59ccc94d59-82jwp 1/1 Running 0 9m8s
istio-telemetry-68c7b4f9b8-p6rxk 2/2 Running 6 9m10s
istio-tracing-55c965d5b6-snrs9 1/1 Running 0 9m7s
kiali-74fdc898b9-9tv67 1/1 Running 0 9m11s
prometheus-c8fdbd64f-qqs65 1/1 Running 0 9m9sistio pod功能注释:
- grafana-* //监控数据可视化工具
- istio-citadel-* //证书管理
- istio-egressgateway-* //出口流量网关
- istio-galley-* //配置检查
- istio-ingressgateway-* //入口流量网关
- istio-pilot-* //Envoy 服务发现,外部化配置
- istio-policy-* //Mixer 混合器策略检查
- istio-sidecar-injector-* //边车注入
- istio-telemetry-* //Mixer混合器指标收集
- kiali-* //Service Mesh可视化工具
- prometheus-* //监控报警
四、实现对外端口暴露
1)确认istio-ingressgateway是否有对外的IP
# kubectl get service istio-ingressgateway -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-ingressgateway LoadBalancer 10.1.64.214 15020:39304/TCP,80:31380/TCP,443:31390/TCP,31400:31400/TCP,15029:43062/TCP,15030:49735/TCP,15031:43992/TCP,15032:48291/TCP,15443:46926/TCP 10m 注:如果 EXTERNAL-IP 有值(IP 地址或主机名),则说明环境中具有可用于Ingress网关的外部负载均衡器,如果 EXTERNAL-IP 值是
2)编译istio-ingressgateway添加外部IP
# kubectl edit service istio-ingressgateway -n istio-system
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
kind: Service
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
creationTimestamp: "2019-12-18T04:09:40Z"
labels:
app: istio-ingressgateway
chart: gateways
heritage: Helm
istio: ingressgateway
release: RELEASE-NAME
name: istio-ingressgateway
namespace: istio-system
resourceVersion: "120335"
selfLink: /api/v1/namespaces/istio-system/services/istio-ingressgateway
uid: 165c8aa1-3210-4b62-bba2-94c196bedfd8
spec:
clusterIP: 10.1.163.208
externalTrafficPolicy: Cluster //在此行下添加如下两行内容
externalIPs: //需添加内容
- 192.168.168.3 //设置一个nodeIP或k8s-master IP
ports:
- name: status-port
nodePort: 42858
port: 15020
protocol: TCP
targetPort: 15020查看配置后信息
# kubectl get service istio-ingressgateway -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-ingressgateway LoadBalancer 10.1.163.208 192.168.168.3 15020:42858/TCP,80:31380/TCP,443:31390/TCP,31400:31400/TCP,15029:32548/TCP,15030:35183/TCP,15031:34070/TCP,15032:45177/TCP,15443:44470/TCP 135m五、对default namespace使用自动注入sidecar功能
# kubectl label namespace default istio-injection=enable
namespace/default labeled
如要禁止defaule namespace自动注入sidecar功能,则使用
# kubectl label namespace default istio-injection-说明:disabled - Sidecar 注入器缺省不会向 Pod 进行注入。在 Pod 模板中加入 sidecar.istio.io/inject 注解并赋值为 true 才能启用注入。
enabled - Sidecar 注入器缺省会对 Pod 进行注入。在 Pod 模板中加入 sidecar.istio.io/inject 注解并赋值为 false 就会阻止对这一 Pod 的注入。
查看添加istio注入后namespace信息
# kubectl get namespace -L istio-injection
NAME STATUS AGE ISTIO-INJECTION
default Active 11d enable
istio-system Active 15m
kube-node-lease Active 11d
kube-public Active 11d
kube-system Active 11d 六、创建名为kiali的secret
# echo -n 'admin' | base64
YWRtaW4=
# echo -n 'admin@123' | base64
YWRtaW5AMTIz
# cat > /opt/kubernetes/istio/kiali-secret.yaml << EOF
apiVersion: v1
kind: Secret
metadata:
name: kiali
namespace: istio-system
labels:
app: kiali
type: Opaque
data:
username: YWRtaW4=
passphrase: YWRtaW5AMTIz
EOF
# kubectl apply -f /opt/kubernetes/istio/kiali-secret.yaml
secret/kiali created