Kerberos安装以及使用ambari开启HDP集群Kerberos认证
文章目录
- 环境准备
- 安装KDC MASTER
- 安装KDC SLAVER
- 安装客户端:
- 使用ambari
环境准备
- 安装jdk
- 下载Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy File。解压下载后的zip包,将得到的jar包放到所有服务器上的$JAVA_HOME/jre/lib/security/目录下。
安装KDC MASTER
yum install krb5-server krb5-libs krb5-workstation openldap-clients
kdc服务器包含三个配置文件:
# 集群上所有节点都有这个文件而且内容同步
/etc/krb5.conf
# 主服务器上的kdc配置
/var/kerberos/krb5kdc/kdc.conf
# 能够不直接访问 KDC 控制台而从 Kerberos 数据库添加和删除主体,需要添加配置
/var/kerberos/krb5kdc/kadm5.acl
vi /etc/krb5.conf
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
# 日志输出设置
[logging]
default = FILE:/var/log/krb5/krb5libs.log
kdc = FILE:/var/log/krb5/krb5kdc.log
admin_server = FILE:/var/log/krb5/kadmind.log
# 连接的默认配置
[libdefaults]
dns_lookup_realm = false
# 表明凭证生效的时限,一般为24小时
ticket_lifetime = 24h
# 表明凭证最长可以被延期的时限,一般为一个礼拜。
#当凭证过期之后,对安全认证的服务的后续访问则会失败
renew_lifetime = 7d
forwardable = true
rdns = false
# Kerberos应用程序的默认领域,所有的principal都将带有这个领域标志
default_realm = xxxxT.COM
# clockskew:时钟偏差是不完全符合主机系统时钟的票据时戳的容差,超过此容差将不接受此票据。
# 通常,将时钟扭斜设置为 300 秒(5 分钟)。这意味着从服务器的角度看,票证的时间戳与它的偏差可以是在前后 5 分钟内
# clockskew = 300
# credential缓存名,默认值为
default_ccache_name = KEYRING:persistent:%{uid}
# :禁止使用 udp 可以防止一个 Hadoop 中的错误
udp_preference_limit= 1
[realms]
xxxxT.COM = {
# 代表要 kdc 的位置。格式是 机器:端口
kdc = cn-bji-t-f205ab.novalocal:88
# 代表 admin 的位置。格式是 机器:端口
admin_server = cn-bji-t-f205ab.novalocal
}
# 域名到realm的关系 (可选)
[domain_realm]
# .example.com = EXAMPLE.COM
# example.com = EXAMPLE.COM
cd /var/kerberos/krb5kdc
vim /var/kerberos/krb5kdc/kdc.conf
# kdc相关配置,这里只设置了端口信息
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
# realms的配置
[realms]
# 设定的realms领域
xxxxT.COM = {
# 和 supported_enctypes 默认使用 aes256-cts。JAVA 使用 aes256-cts 验证方式需要安装 JCE包(推荐不使用)
#master_key_type = aes256-cts
# 标注了 admin 的用户权限,文件格式是:Kerberos_principal permissions [target_principal] [restrictions]
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
# KDC 进行校验的 keytab
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
# 支持的校验方式
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
- 创建Kerberos数据库
[root@cn-bji-t-f205ab krb5kdc]# kdb5_util create -r xxxxT.com -s
Loading random data
Initializing database '/var/kerberos/krb5kdc/principal' for realm 'xxxxT.com',
master key name 'K/[email protected]'
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key: xxxx
Re-enter KDC database master key to verify: xxxx
- 添加database administrator
[root@cn-bji-t-f205ab krb5kdc]# kadmin.local
Authenticating as principal root/[email protected] with password.
kadmin.local: Can not fetch master key (error: No such file or directory). while initializing kadmin.local interface
出错:注意第4步kdb5_util create -r xxxxT.com -s 中的com是小写改成大写。
[root@cn-bji-t-f205ab krb5kdc]# kdb5_util create -r xxxxT.COM -s
Loading random data
Initializing database '/var/kerberos/krb5kdc/principal' for realm 'xxxxT.COM',
master key name 'K/[email protected]'
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key: xxxx
Re-enter KDC database master key to verify: xxxx
[root@cn-bji-t-f205ab krb5kdc]# kadmin.local
Authenticating as principal root/[email protected] with password.
kadmin.local: addprinc admin/[email protected]
WARNING: no policy specified for admin/[email protected]; defaulting to no policy
Enter password for principal "admin/[email protected]": admin
Re-enter password for principal "admin/[email protected]": admin
Principal "admin/[email protected]" created.
- 启动
systemctl start krb5kdc
systemctl start kadmin
或:
[root@cn-bji-t-f205ab krb5kdc]# service krb5kdc start
Redirecting to /bin/systemctl start krb5kdc.service
[root@cn-bji-t-f205ab krb5kdc]# service kadmin start
Redirecting to /bin/systemctl start kadmin.service
[root@cn-bji-t-f205ab krb5kdc]# systemctl status krb5kdc.service
● krb5kdc.service - Kerberos 5 KDC
Loaded: loaded (/usr/lib/systemd/system/krb5kdc.service; disabled; vendor preset: disabled)
Active: active (running) since Wed 2019-01-09 17:35:52 CST; 35s ago
Process: 8268 ExecStart=/usr/sbin/krb5kdc -P /var/run/krb5kdc.pid $KRB5KDC_ARGS (code=exited, status=0/SUCCESS)
Main PID: 8269 (krb5kdc)
CGroup: /system.slice/krb5kdc.service
└─8269 /usr/sbin/krb5kdc -P /var/run/krb5kdc.pid
Jan 09 17:35:52 cn-bji-t-f205ab.novalocal systemd[1]: Starting Kerberos 5 KDC...
Jan 09 17:35:52 cn-bji-t-f205ab.novalocal systemd[1]: Started Kerberos 5 KDC.
安装KDC SLAVER
前提:
- 主从服务器的/etc/hosts文件已经配置
- slave服务器的JCE已经安装
例:
主KDC hostname:namenode01
从KDC hostname: namenode02
- 修改
/etc/krb5.conf
[realms]
xxxxT.COM = {
kdc = namemode01
kdc = namenode02
admin_server = namenode01
}
kerberos认证时是按照/etc/krb5.conf中主机顺序访问kdc服务器,kdc认证只会读取本地数据库
- 在slave kdc 上安装kdc
yum install krb5-server krb5-libs krb5-workstation openldap-clients
- 从master KDC服务器上拷贝一下文件到 slave KDC
/etc/krb5.conf
/var/kerberos/krb5kdc/kadm5.acl
/var/kerberos/krb5kdc/kdc.conf
## master key stash file
/var/kerberos/krb5kdc/.k5.xxxxT.COM
- 为主从KDC服务器创建host keytabs
在master上执行:
kadmin.local
addprinc -randkey host/namenode01
addprinc -randkey host/namenode02
ktadd host/namenode01
ktadd host/namenode02
会生成/etc/krb5.keytab文件,将此文件拷贝到slave服务器的/etc目录下
- 在slave服务器上创建
kpropd.acl文件,内容如下
host/[email protected]
host/[email protected]
- 将kpropd作为独立守护程序启动
在slave上运行
kpropd
- 执行以下命令同步数据库
kdb5_util dump /usr/kerberos/krb5kdc/replica_datatrans
kprop -r xxxx.COM -f /var/kerberos/krb5kdc/replica_datatrans namenode02
同步成功后在namenode02的/var/kerberos/krb5kdc目录下会多出以下文件:
-rw------- 1 root root 16384 Feb 15 10:35 principal
-rw------- 1 root root 8192 Feb 15 10:35 principal.kadm5
-rw------- 1 root root 0 Feb 15 10:35 principal.kadm5.lock
-rw------- 1 root root 0 Feb 15 10:35 principal.ok
安装客户端:
yum install krb5-workstation krb5-libs krb5-auth-dialog
使用ambari
确保已经安装好了KDC并且在所有集群都安装了JCE。
-
打开并登陆ambari web。并在浏览器选择Admin > Kerberos。
-
点击 “Enable Kerberos”进入安装向导。
-
选择正在使用的KDC类型,并确认已满足先决条件。
-
根据环境修改高级Kerberos设置。
- 手动管理Kerberos客户端krb5.conf(而不是Ambari
管理krb5.conf),展开Advanced krb5-conf部分并取消选中
“Manage Kerberos client krb5.conf”选项。必须在每台主机上配置krb5.conf。
注意:
- 手动管理Kerberos客户端krb5.conf(而不是Ambari
手动管理krb5.conf时,建议确保DNS不用于查找KDC和REALM条目。 依赖DNS可能会导致负面性能和功能影响。 要确保不使用DNS,请确保在配置的libdefaults部分中设置以下条目。
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
Ambari将服务器上安装Kerberos客户端,并通过测试Ambari可以创建principal,生成keytab并分发该keytab来测试对KDC的访问。
- 自定义Hadoop使用的Kerberos标识,然后继续对集群进行kerberize。
重要:
在Configure Identities步骤中,务必确认principal名称。尤其是Ambari Principals部分。默认情况下,会将集群名称附加到每个Principals。可以将其保留为默认值,或者通过从主体名称字符串中删除“ - $ {clustername}”来调整它们。 例如,如果集群名为HDP且realm是EXAMPLE.COM,则hdfs主体将创建为[email protected]。
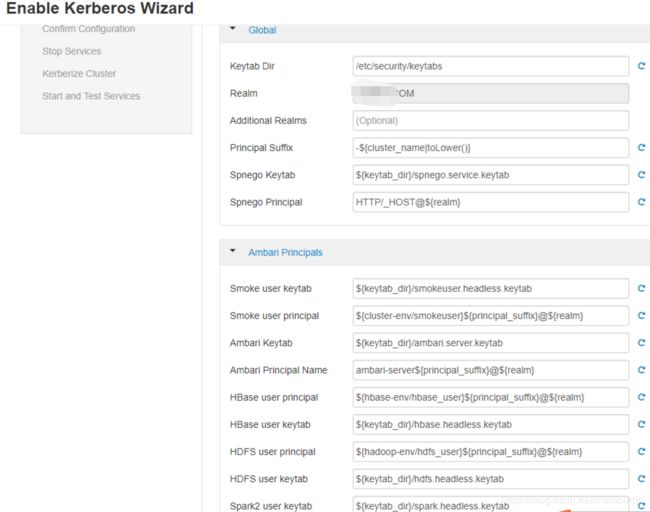
8. 点击下一步,可以选择下载ambari自动创建的principals和keytabs。
- 点击下一步开始安装
- 等到principals已经创建并且keytabs已经初始化并分发之后。ambari更新集群配置,并且启动和测试集群的服务。



