1. Basic Authentication
- client request to server without req.headers.authorization
- server send 401 to refuse access, response with header contains 'WWW-authenticate': 'Basic'
- client request with auth contains user and password, encoded as base64 string, form as user:password, prefix with 'Basic '(note:one space character), such as Authorization: 'Basic Foooooobar=='
- Server check the user and password, if authorized, then process next middleware, if not, bypass directly to error handling middleware
Resources
Basic acccess authentication (Wikipedia)
Basic Access Authentication
2. Cookie-based Authentication
- client request to server without req.signedCookies.user
- server send 401 to refuse access, wait client to first basic authentication
- client first authorized, server response with signedCookie.user, using:
res.cookie('user', 'admin', {signed:true}) - client send this signed cookie key-value in every subsequent request
Resources
[HTTP Cookies](https://en.wikipedia.org/wiki/HTTP_cookie
cookie-parser
3. Cookie plus Session Authentication
- client request to server without req.session.user
- server send 401 to refuse access, wait client to first basic authentication
- client first authorized, server attach request with session.user using
req.session.user = 'admin'(note: attach to request) - client send a cookie contains session-id(modified by session name property) with client information, such as
user:'admin'here in every subsequent request
Resources
Sessions in Express.js
Express Session Management
Sessions in Express.js
Express Session Management
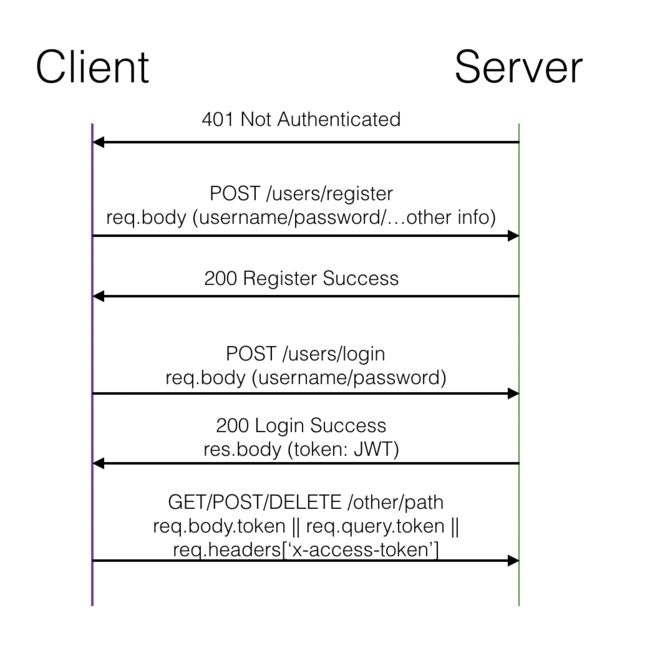
4. JSON web token Authentication
- client request to specified path on server without token provided
- server send 401 to refuse access, wait client to first authentication: POST specified path like /user/login, with
req.body.username, req.body.password - client first authorized, server sign user info to JWT
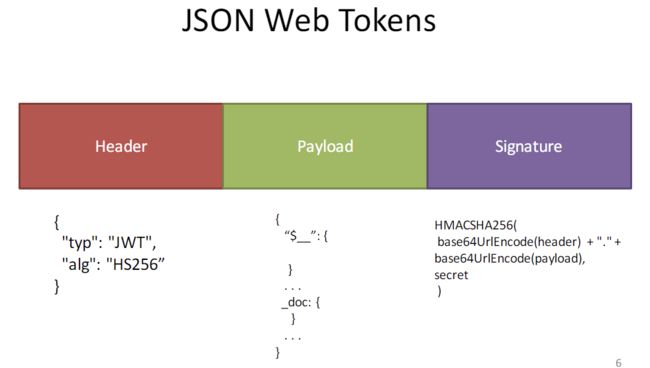
{'type':'JWT', 'alg': 'HS256'}and payloads with{ '$___': {foo}, '_doc': {foo} }to Signature asHMACSHA256(base64UrlEncode(header) + '.' + base64UrlEncode(payload),secret) - client request with signed token on every subsequent request:
req.body.token || req.query.token || req.headers['x-access-token']
JSON Resources
JSON Web Tokens
RFC 7519 (JSON Web Tokens)
jsonwebtoken (Node Module)
Other Resources
Authenticate a Node.js API with JSON Web Tokens
Using JSON Web Tokens with Node.js
Token Based Authentication for Single Page Apps (SPAs)
The Ins and Outs of Token Based Authentication
The Anatomy of a JSON Web Token
5. Secure communication on HTTPS
- The first user authentication should not be transformed on insecure way like http
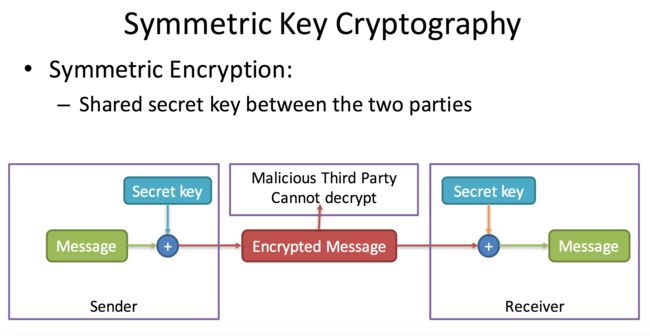
Symmetric Key Cryptography
- Server/Client side has one symmetric key to encrypted and decrypted messages
-
Once the distributed key leaked, communication no longer safe
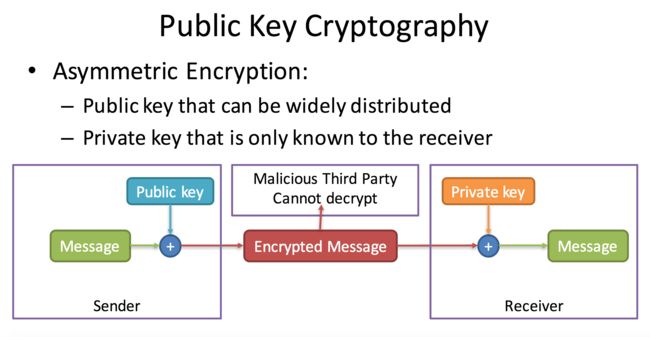
Public Key Cryptography
- Public/Private Key pair
- Public key can be distributed everywhere
- Private key should be only known by Server side
-
Message encrypted by public key can only be decrypted by private key
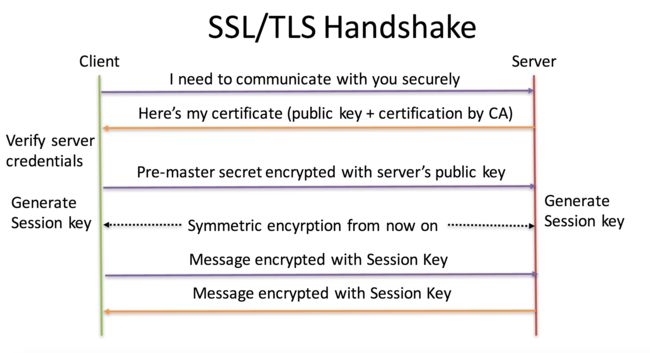
HTTPS
- Server send public key to client (distributed)
- Client verify server credentials to ensure it from exactly the server
- Client use public key to generate a Pre-masted secret encrypted key (called session key), then send to server
- Since only server have private key to decode the session key, ensure the security
-
Both side have session key, communication now based on symmetric key cryptography (Public key cryptograph is so expensive)
Generate self-signed SSL key
openssl genrsa 1024 > private.key
openssl req -new -keyprivate.key -out cert.csr
openssl x509 -req -in cert.csr -signkey private.key -out certificate.pem
Note for Windows Users
If you are using a Windows machine, you may need to install openssl. You can find some openssl binary distributions here. Also, this article gives the steps for generating the certificates in Windows. Another article provides similar instructions. Here's an online service to generate self-signed certificates.
Resources
HTTPS
HTTPS (Wikipedia)
Public Key Cryptography
Transport Layer Security
Node's HTTPS Server
Node HTTPS Server
Book
Kurose, James F., and Keith W. Ross. Computer networking: a top-down approach. Pearson, 2017, ISBN-10: 0134522206 • ISBN-13: 9780134522203.
Other Resources
Howto: Make Your Own Cert With OpenSSL on Windows
OpenSSL for Windows
How to Use SSL/TLS with Node.js
Adding HTTPS (SSL) to Express 4.X Applications
How does HTTPS actually work?
OAuth 2
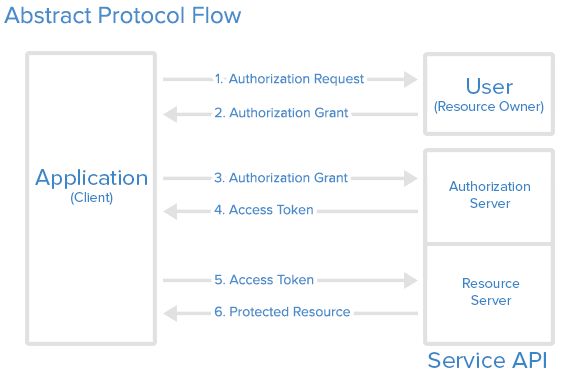
OAuth Role
- Resource Owner
- Client
- Resource Server
- Authorization Server
Flow
OAuth Resources
OAuth 2.0
OAuth
OAuth (Wikipedia)
Facebook Resources
https://developers.facebook.com/apps/
Passport Resources
passport-facebook
passport-google-oauth
passport-twitter
Other Resources
Social Authentication With Passport.js
Easy Node Authentication: Facebook
An Introduction to OAuth 2
Understanding OAuth2
The OAuth Bible