热门威胁情报库深入分析(三)
第三部分:AlienVault-OTX
3.1 数据来源
1. AlienVault Labs threat research team:
This dedicated team spends countless hoursanalyzing the different types of attacks, emerging threats, suspiciousbehavior, vulnerabilities and exploits they uncover across the entire threatlandscape.
AlienVault Labs Threat Intelligence drivesthe USM platform’s threat assessment capabilities by identifying the latestthreats, resulting in the broadest view of threat vectors, attacker techniques andeffective defenses. AlienVault Labs regularly delivers eight coordinated ruleset updates to the USM platform.
2. 通过超过37000来自OTX社区的参与者,收集威胁数据
3.2 功能服务
包含的搜索信息有:
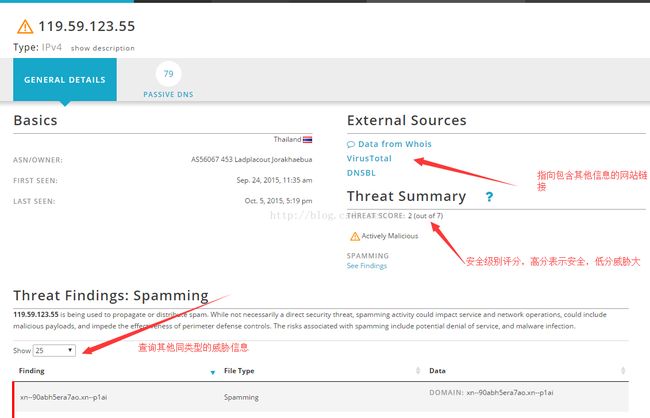
1. IP地址
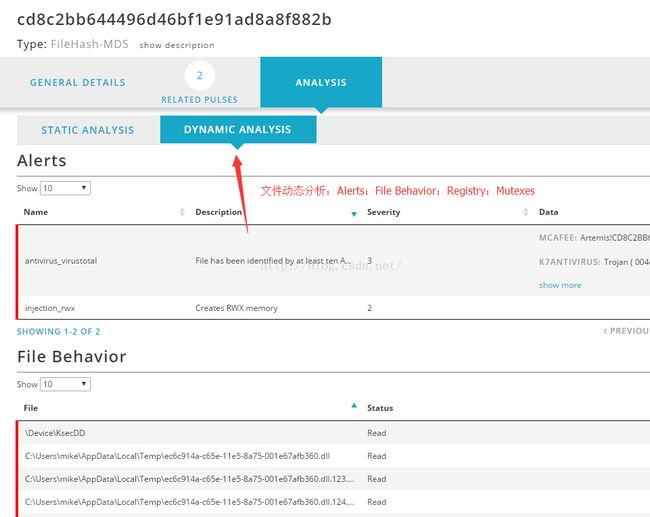
2. 文件校验:MD5,SHA1,SHA256,pehash,imphashdomain, Hostnames (subdomains), Email, URL, URI, CIDRrules, File paths,MUTEX name,CVEnumbers
3. 有公开的API接口可以使用
https://github.com/AlienVault-Labs/OTX-Python-SDK
4. 专门提供给公司的高级管理系统USM:Logs carry importantinformation such as what your users are doing, what data they are accessing,the performance of your systems and overall network health. They will alsocontain evidence of system compromise and data exfiltration, if you know whereto look.
USM automatically detects and linksbehavior patterns found in disparate yet related events generated acrossdifferent types of assets, telling you what are the most significant threatsfacing your network right now.
USM:日志包含重要的信息:使用者在做什么,他们在获取什么数据,你的系统运行如何以及整个网络的健康状态。日志同样包括系统入侵和数据泄露的证据。
USM自动探测和联系被发现的在不同资产上的独立行为的行为模式,得到你的网络面临的最重要的威胁信息。
Network IDS signatures – detect the latest malicious traffic on your network
Host IDS signatures – identify the latest threats targeting your critical systems
Asset discovery signatures – detect the latest operating systems, applications, anddevice information
Vulnerability assessment signatures – uncover the latest vulnerabilities on your systems
Reporting modules – receive new views of critical data about your environment tomanagement and satisfy auditor requests
Dynamic incident response templates – customized guidance on how to respond to each alert
Newly supported data source plugins – expand your monitoring footprint by integrating data fromlegacy security devices and applications
网络IDS特征--检测最近你的网络中恶意通信。
主机IDS特征--识别关系到你关键系统的威胁。
发现资产的特征--探测最近的操作系统,应用,设备信息。
恶意评估特征--发现系统最近的破坏。
报道模块--获取环境中的关键数据的最新信息以管理和满足监听请求。
动态事件应激模范--为用户定制面对每个警告的指导。
新支持数据源插件--来自安全设备和应用的综合数据扩大监听脚步。
3.2.1 IP地址3.2.2文件校验:
MD5,SHA1,SHA256,pehash,imphashdomain, Hostnames (subdomains), Email, URL, URI, CIDRrules, File paths,MUTEX name,CVEnumbers
3.2.3 企业用户使用示例:
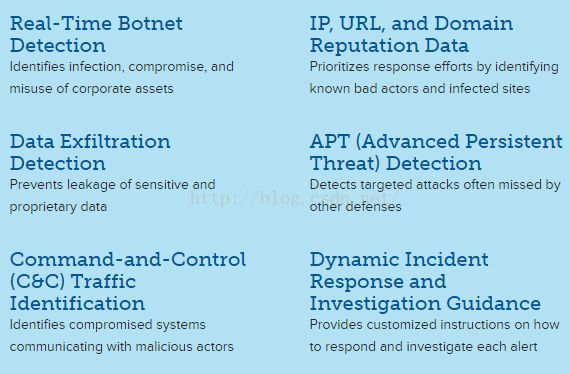
Real-time threat intelligence utilizes kill-chaintaxonomy to identify attackers, their victims, their methods and theirintents. 对攻击行为已组织的方式建立分析库

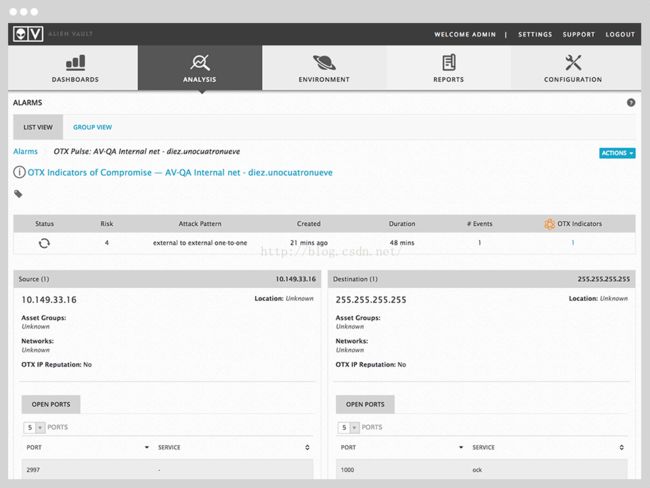
Each alarm provides detailed andcustomized instructions on how to investigate and respond to maliciousactivity. 通过alarm提醒与用户相关的威胁
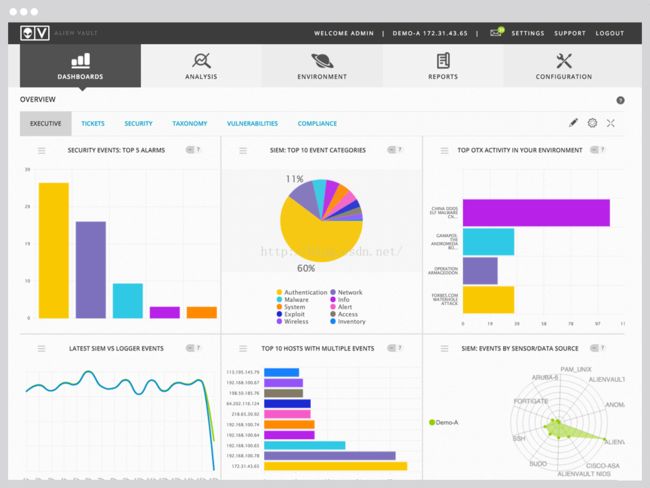
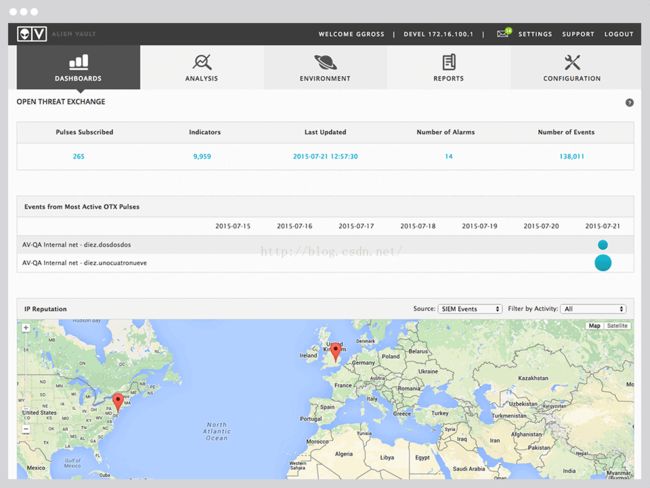
Customizable executive dashboardsprovide overviews and click-through details about your security and complianceposture. 对一段之间的结果进行图标分析
All you need to know about an asset forincident investigation and response – in one window. 与事件调查响应相关的资产
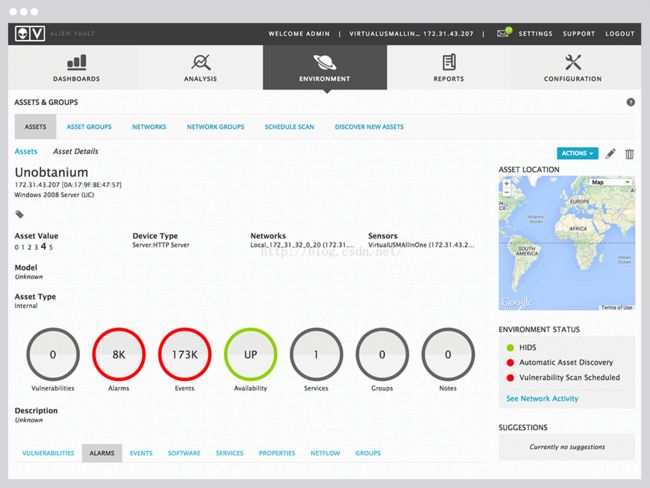
Automated asset discovery provides granulardetails on all devices in your network.发现所在网络中所有的资产
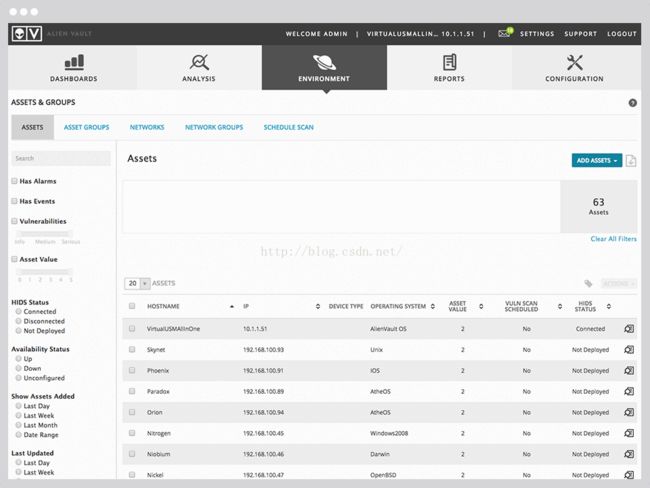
Targeted guidance eliminates the guessworkassociated with integrating data sources and provides precise suggestions forimproving visibility. 减少集成化的无效数据,提高可见度。
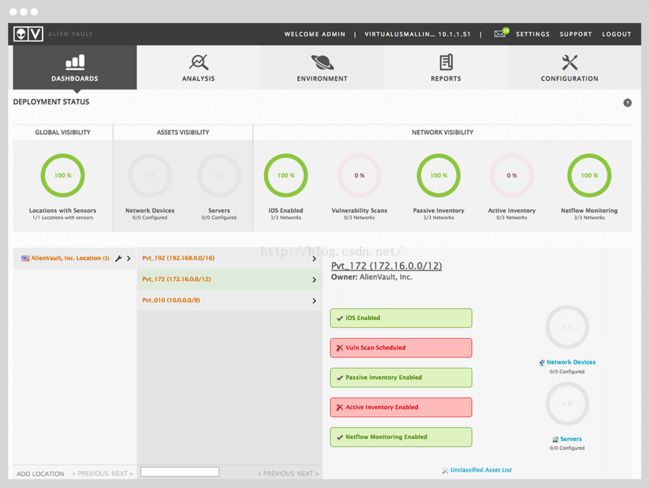
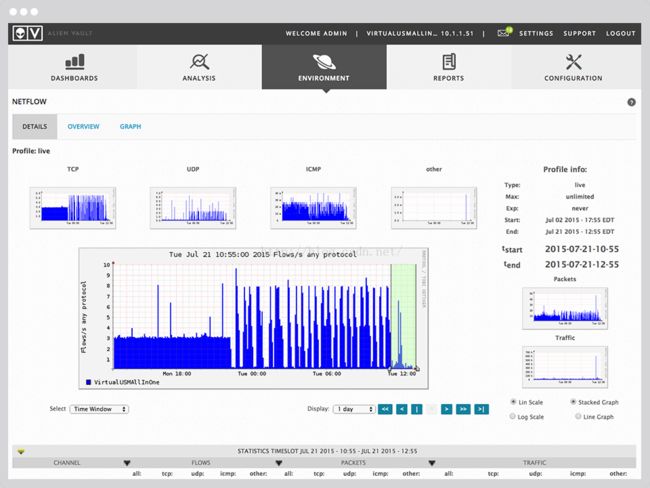
Built-in network flow analysis provides allthe data you need for in-depth investigations – including packet capture. 提供深度调查数据,包括抓包结果
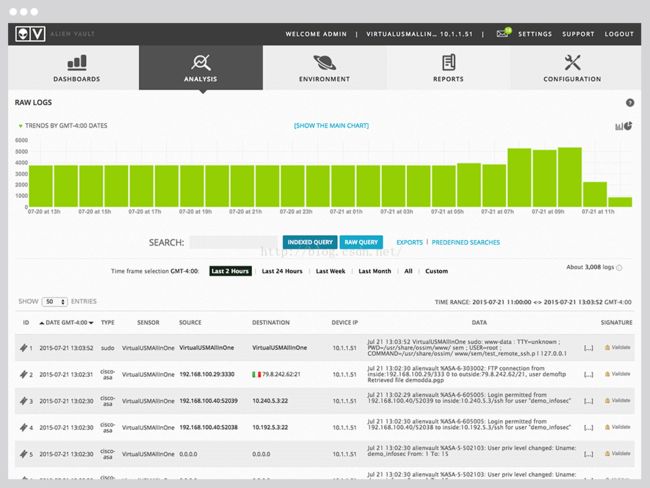
Secure storage of raw event data satisfiesregulatory compliance requirements while an easy-to-use interface allows forquick searches. 原始数据规范存储方便查找
Identify malicious actors attempting to interactwith your network using our dynamic IP reputation data. 使用动态库定位相关的恶意行为
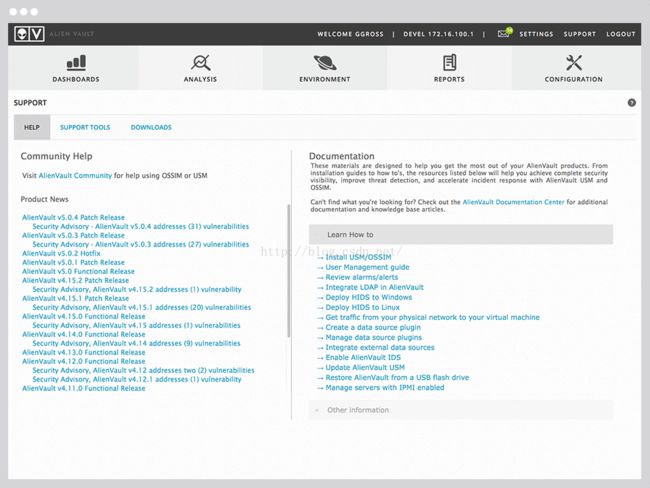
Centralized, integrated "how to"documentation for all you need to know about USM. 集中整合需要知道的文件
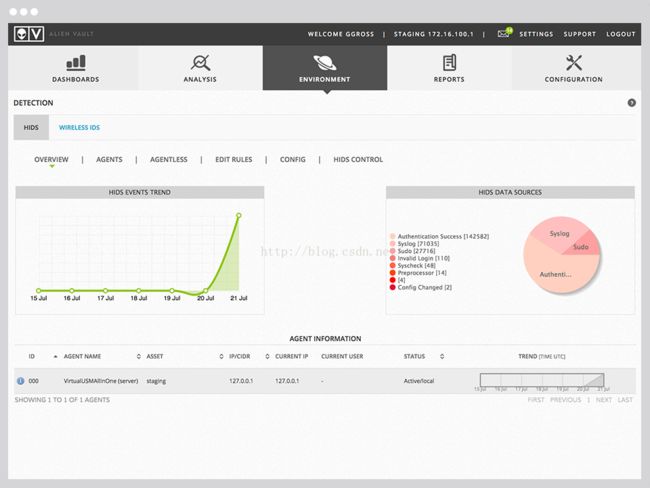
Built-in network IDS and host IDS resultsin more accurate threat detection and event correlation, faster deployment andsimpler management. 建立IDS库
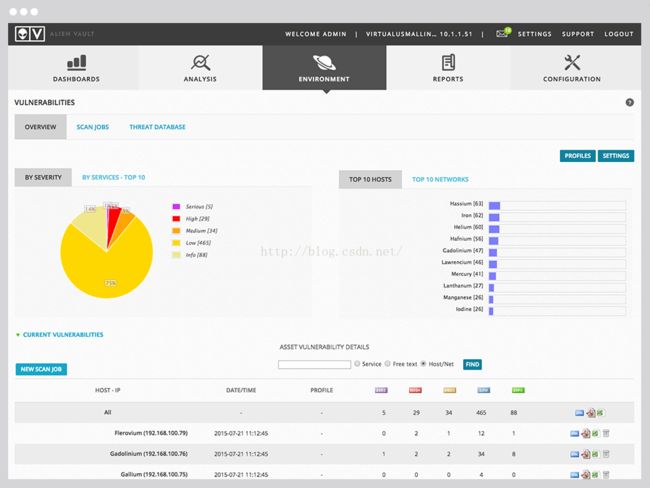
Built-in vulnerability assessmentsimplifies security monitoring and speeds remediation. 建立威胁评估,简化安全监控加快漏洞填补。
3.3 情报质&量
质:对于搜集到的信息进行比较和整合,同时部分进行人工分析和蜜罐监测分析,具有相对较高的质量;同时,提供给公司的针对性服务USM,具有更高的质量。
量:收集了超过26,000条涵盖140个国际的威胁数据,超过37000名的参与者可每日贡献了超过300万的威胁数据。

3.4 技术框架
提供公用的API https://github.com/AlienVault-Labs/OTX-Python-SDK
OTX在一个大数据平台基础上利用自然语言处理与机器学习,来比较数据和整合信息系统威胁。
Security Artifact Analysis(人工分析)
Honeypot Deployment and Analysis(蜜罐分析)
Attacker Profile Analysis(攻击者画像)
Open Collaboration with State Agencies,Academia, and Other Security Research Firms(与政府负责人,学术界,其他安全公司公开合作)
Powerful correlation engine.:over 2,000 pre-built correlation directives continuously analyzeevent data to identify potential security threats in network.
(强大的合作机制:超过2,000持续性的预见性的相关性指导分析事件数据来辨别网络中可能的安全隐患)
Correlation directives – USM shipswith over 2,000 pre-defined rules that translate raw events into specific,actionable threat information by linking disparate events from across yournetwork
(相关性指导规则---USM定义超过2,000预定义的规则,通过连接网络中的独立事件将突兀的事件解释为特定的,有控告的威胁信息。)
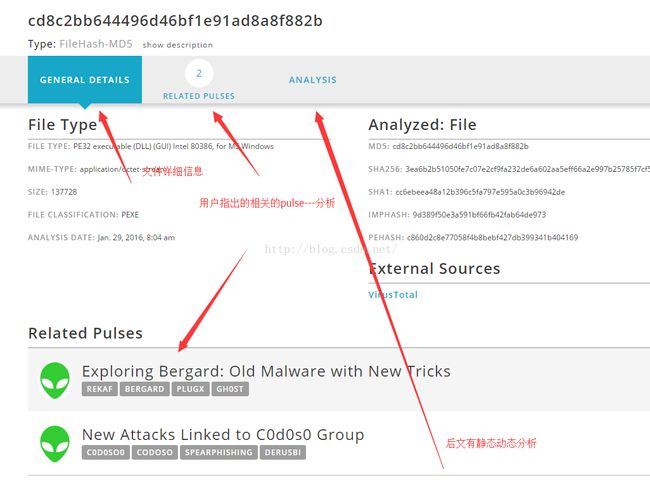
OTX社区的威胁情报以pulse的形式提交和报告。一个pulse包含一个或多个形成威胁,行动或底层恶意行为的威胁信息(indicators of compromise IOCs)。 IOCs 对于活跃于网络和电脑的威胁来说就像是一个标志。
l 基础设施(分布式计算;分级存储):
l 数据汇聚与存储层(数据采集;数据存储;数据管理):已pulse形式存储报告;人工分析;蜜罐分析;攻击者画像;
l 信息分析处理层(算法实验;数据挖掘;流处理;批处理):自然语言处理;机器学习;相关性分析
l 情报输出层(WEB服务器;WEB应用;WEB前端):js, .net server:nginx/1.4.6
3.5 优势
USM:拥有内嵌的数据源和管理平台,对于提供的可预测的信息源可以更好的收集关联和分析。
公用平台具有较为优越的数据整合分析技术,具有较高的预测能力。
提供丰富的可视化分析资料
Ownership of both the built-in data sourcesand the management platform that make up the USM platform gives AlienVault aunique advantage over other security point products. Providing predictable datasources enables our threat research team to have a comprehensive understandingof the interactions between the different data types being collected,correlated and analyzed. This in-depth knowledge enables us to engineer the USMplatform to provide effective security controls and seamlessly integratedthreat intelligence for any environment.
3.6 不足
优秀的分析功能和可视化分析只提供给付费用户