2013微软校园招聘笔试题
1. You are managing the database of a book publichser, you currently store the book orders your company receives in the following BookOrders table. You manager has asked you to generate a report to list all the orders where the quantity ordered was greater than the average quantity per order for that book. Which of the following queries will satisfy the business requirements? (3Points)
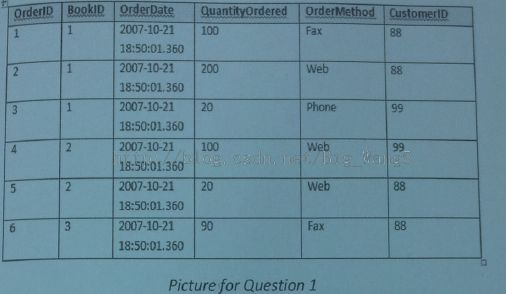
A. select BookID from BookOrders A where QuantityOrdered > (select avg(QuantityOrdered) from BookOrders B where B.BookID = B.BookID)
B. select OrderID from BookOrders A where QuantityOrdered > (select avg(QuantityOrdered) from BookOrders B where B.BookID = A.BookID)
C. select BookID from BookOrders A where QuantityOrdered > (select avg(QuantityOrdered) from BookOrders B where B.BookID = A.BookID)
D. select OrderID from BookOrders A where QuantityOrdered>(select avg(QuantityOrdered) from BookOrders B where A.BookID=A.BookID)
分析: 数据库
基于某个条件选出一个订单列表,考的是最基本的数据库语言select * from * where *
2.Which one CANNOT be used to communicate between 2 processes on Windows?
A. Named event B. Named Pipe C. Critical Section D. Shared Memory
分析:Linux线程间通信:互斥体,信号量,条件变量
Windows线程间通信:临界区(Critical Section)、互斥量(Mutex)、信号量(Semaphore)、事件(Event)
Windows 进程间通信:管道、内存共享、消息队列、信号量、socket
Windows 进程和线程共同之处:信号量和消息(事件)
3. Which of the following operation is NOT basic operation of stack?
A. Push an element to the stack B. Pop an element from the stack
C. Check if the stack is empty D. Sort the stack
4.Which of the following design patterns is(are) "creational" pattern(s)?
A. Facade B.Singleton C. Composite D.None of the above
分析:创建型模式
5. Which of the following TCP packets sequence is(are) correct for TCP handshake when setting up a connection?
A. SYN, SYN+ACK, SYN+ACK B. SYN+ACK, SYC + ACK, SYN
C. SYN, SYN+ACK, RST D. SYN, SYN, ACK
E. None of the above
分析:TCP三次握手应该是:SYN、SYN+ACK、ACK
6. The characteristics of functional programming are
A. Avoidance of changing state and mutable data
B. Referential transparency
C. Lambda calculus
D. Thread-safe
E. All of above
完全不了解functional programing
见http://www.ruanyifeng.com/blog/2012/04/functional_programming.html
考了”没有副作用”,“不修改状态”,“引用透明”引用透明的概念类似于可重入
Lisp语言《黑客与画家》很赞的一本书
7. The Hypertext Transfer Prorocol (HTTP) is an application protocol for distributed collaborative, hypermedia information systems. It is the foundation of data communication for the World Wide Web. Which of the following statment(s) is(are) correct:
A. It functions as a request-response protocol in the client-server computing model
B. It is a stateless protocol is that treats each request as an independent transaction
C. It is the protocol that major Internet applications such as the World Wide Web and email rely on
D. The HTTP response includes a numeric status code, and the status code "404" often stands for "Page Not Found"
E. None of the above
分析:E-MAIL使用SMTP协议。
8. Which is correct about shallow copy in C++?
A. Shallow copy only copy reference
B. Shallow copy will cause possible physical pointer duplication
C. Shallow copy may caue problems in case of assignment or parameter passing in function
D. Copy constructor may mitigate the risk of shallow copy
分析: shallow copying (浅拷贝)的特征
来总结一下关于 深拷贝与浅拷贝需要知道的基本概念和知识:
(1)什么时候用到拷贝函数?
a.一个对象以值传递的方式传入函数体;
b.一个对象以值传递的方式从函数返回;
c.一个对象需要通过另外一个对象进行初始化。
如果在类中没有显式地声明一个拷贝构造函数,那么,编译器将会自动生成一个默认的拷贝构造函数,该构造函数完成对象之间的位拷贝。位拷贝又称浅拷贝
(2)是否应该自定义拷贝函数?
(3)什么叫深拷贝?什么是浅拷贝?两者异同?
自定义拷贝构造函数是一种良好的编程风格,它可以阻止编译器形成默认的拷贝构造函数,提高源码效率。
如果一个类拥有资源,当这个类的对象发生复制过程的时候,资源重新分配,这个过程就是深拷贝,反之,没有重新分配资源,就是浅拷贝。
(4)深拷贝好还是浅拷贝好?
如果实行位拷贝,也就是把对象里的值完全复制给另一个对象,如A=B。这时,如果B中有一个成员变量指针已经申请了内存,那A中的那个成员变量也指向同一块内存。这就出现了问题:当B把内存释放了(如:析构),这时A内的指针就是野指针了,出现运行错误。
9. There are 15 balls that are put into 4 bags. It is required that every bag has at least 1 ball but the number of balls in every bag should be different. How many different ways totally,can be used to put the balls into the 4 bags?
A. 4 B. 5 C. 6 D. 7 E. None of the above
分析:15个球放入4个袋子,每个袋子至少一个球,且每个袋子球数量不同:1,2,3,9; 1,2,4,8; 1,2,5,7; 1,3,4,7; 1,3,5,6; 2,3,4,6
10. What will be the output of this program?
class Base { public: char Value(){ return 'A'; } virtual char VirtualValue() { return 'V'; } }; class Derived : public Base { public: virtual char Value() { return 'D'; } }; class VirtualDerived:virtual public Base { public: char Value() { return 'Z'; } char VirtualValue() { return 'X'; } }; int main() { Base* b1 = new Derived(); Base* b2 = new VirtualDerived(); cout<<b1->Value() <<''<< b1->VirtualValue()<<''<< b2->Value() <<''<< b2->VirtualValue()<<endl; }
A. A V A X B. D V A X C. A V Z X D. A V Z V E. D V Z X
11. Tow 32 bit integer values A and B, are processed to give the 32 bit integers C and D as per the following rules. Which of the rule(s) is(are) reversible? i.e. is it possible to obtain A and B given c and D in all condition?
A. C = (int32)(A+B), D = (int32)(A-B)
B. C = (int32)(A+B), D= (int32)((A-B)>>1)
C. C = (int32)(A+B), D = B
D. C = (int32)(A+B), D = (int32)(A+2*B)
E. C = (int32)(A*B), D = (int32)(A/B)
分析:
对于A选项假设A>0,B>0;C可能越界使得C=A+B-2^32举个反例:A=B=2^31-1 C=-2,D=0;
A=B=-1,C=-2,D=0
对于C选项不管C是否越界总能得到A=C-D, B=D
对于B选项我们可以考虑Q=A+B, C=Q+B ,D=Q跟C的那个一样,就能求出Q与B Q=A+B,B又已知A可求
D选项:A=B=-1 A=B=2^31-1
E选项:A=B=2^15, A=B=2^31
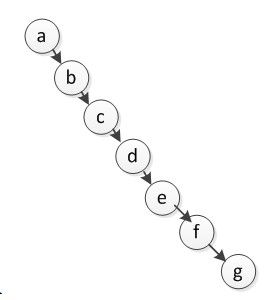
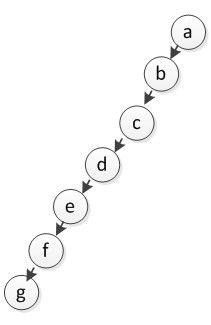
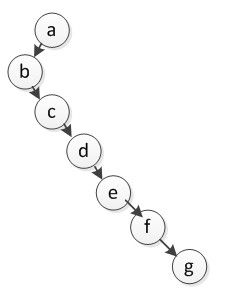
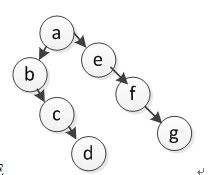
12. If a pre-order traversal sequence of a binary tree is abcdefg, which of the following(s) is(are) possible in-order traversal sequence?
A. abcdefg B. gfedcba C. bcdefga D. bceadfg E. bcdaefg
13. T(x) = 1(x<=1), T(n) = 25*T(n/5)+n^2 What is T(n)?
A. O(nlogn) B. O(n^2logn) C. O(n^2) D. O(n^3) E. O(n^3logn)
还是用主定理吧,直接推的话,好像比较麻烦。
主定理:
主要记住nlogba和f(n)的关系,即可,大于为情况1,等于为情况2,小于为情况3.
T(n)=aT(n/b)+f(n)
1) e>0, F(n)=O(nlogba-e),复杂度为T(n)=theta(nlogba):例如T(n)=9T(n/3)+ n, theta(n2)
2) f(n)=theta(nlogba),复杂度为T(n)=theta(nlogba*lgn)。例如:T(n)=25T(n/5)+O(n2),theta(n2lgn)
3) e>0, F(n)=W(nlogba+e),复杂度为T(n)=theta(f(n)).例如T(n)=3T(n/4)+cn2,theta(n2)
14. There are two threads running on a dual-core machine. Their main body are listed as following c code snippet thread1: x=1; r1=y; thread2: y=1; r2 = x; x, y are two global variables initialized as zero. Which is(are)the possible value(s) of r1 and r2?
A. r1=1, r2 =1 B. r1=1,r2=0 C. r1=0, r2 =1 D r1=0, r2=0
考察临界区问题,没有设置临界区,所以可能:
A: x=1 => y=1 => r1=y=1 => r2=x=1
B: y=1 => r2=x=0 => x=1 => r1=y=1
C: x=1 => r1=y=0 => y=1 =>r2=x=1
15. The depth of a complete binary tree with n elements is
A. D(n) = log2(n) B. D(n) = 1+log2(n) C. D(n) = n * log2(n) D. D(n) = 1 + n*log2(n)
普遍来说,认为根结点深度为1,所以深度=1+ log2(n)
16. How many 0 appears in 1,2,3,...,999,1000?
A. 189 B. 191 C. 193 D. 195
这道题没有答案,正确应该是192,一种数的方法是:1-100有:9+2=11,101-200有:9+9+2=20,之后201-300,…,901-1000模式相同,但1000多1,所以公有11+20*9+1=192。也可以按照1个零有哪些,2个零有哪些,3个零有哪些这样数,总之有一个比较规律的数的方法,保证没有遗漏就可以了。
注:算出来结果是192
17. What is the probability for born on 2/28 vs born on 2/29? and what for born on 2012/2/28 vs born on 2012/2/29?
A: 1:1 and 1:1 B. 4:1 and 1:1 C. 1:1 and 4:1 D. 4:1 and 4:1
4:1(四年一次闰年)
1:1(如果闰年,则那年28日和29日出生概率相同,与在其他日期出生概率没有差别)
18. Which of the following use(s) greedy strategy?
A. Dijkstra algorithm in single-source shortest path
B. Prim's algorithm in minimum spanning tree
C. Kruskal's algorithm in minimum spanning tree
D. Floyd-Warshall algorithm in all-pairs shortest paths
E. KMP algorithm in string match
分析:D、E是使用动态规划算法
贪心:Dijkstra,Prim,Kruskal (算法导论中已明确说明)。
Kruskal:初始化每个顶点为只有一个根几点的树,将边的权值按从小到大排序,选择权值最小的边(u,v),如果u和v不在一颗树中,则将u和v所在两棵树合并,边(u,v)加入到集合中,直到所有的边都找完。
Prim:从任意顶点出发,维护一个树A,每一步,选择最小的边连接G(V,A),将结点V加入到树A中,直到所有的顶点都找完。
动态规划:Floyd-Warshall,KMP
19. Given the following code:
class A { public: int k1; int k2; }; int cmp(A x, A y) { return x.k1 - y.k1;} void exchange(A a[], int i, int j) { A t = a[i]; a[i] = a[j]; a[j] = t;} void f1(A a[], int l, int(*c)(A x, A y)) { for(int i = 0; i < l; ++i) { int min = i; for(int j = i+1; j < l; ++j) { if(c(a[j], a[min])<0) min = j; } exchange(a, i, min); } } void f2(A a[], int l, int(*c)(A x, A y)) { for(int i = 1; i < l; ++i) { A t = a[i]; int j = i-1; while(c(t, a[j])<0 && j >=0) { a[j+1] = a[j]; j = j-1; } a[j+1] = t; } } void f3(A a[], int l, int(*c)(A x, A y)) { for(int i = 0; i < l; ++i) { for(int j = l-1; j > i; --j) { if(c(a[j], a[j-1])< 0) exchange(a, j-1, j); } } } int _f41(A a[], int low, int high, int(*c)(A x, A y)) { int i = low; A t = a[low]; for(int j = low+1; j < high; ++j) { if(c(a[j], t)<= 0) { i++; if(i!=j) exchange(a, i, j); } } exchange(a, low, i); return i; } void _f42(A a[], int low, int high, int(*c)(A x, A y)) { if(low < high) { int p = _f41(a, low, high, c); _f42(a, low, p, c); _f42(a, p+1, high, c); } } void f4(A a[], int l, int(*c)(A x, A y)) { _f42(a, 0, l, c); }
An array is declared as below:
A a[5] = {{3,4},{6,5},{2,7},{3,1},{1,2}};
Which of the function calls can transform it into:
{{1,2},{2,7},{3,1},{3,4},{6,5}}
A. f1(a,5,cmp) B. f2(a,5,cmp) C. f3(a,5,cmp) D. f4(a,5,cmp) E. None of the above
注: 排序算法稳定性问题
这道题出的很有意思,乍一看,题干这么大,可能会被唬住,其实冷静下来看一下,很简单,就是一个排序的稳定性非稳定性的分析。所谓稳定性,即:保证排序前2个相等的数其在序列的前后位置顺序和排序后它们两个的前后位置顺序相同,如果排序的结点仅仅是一个数,则稳定性意义不大,但是如果有多个键值,就需要考虑稳定性的分析。例如,对于本题,如果排序算法是稳定的,那么因为原数组{3,4}排在{3,1}前,根据稳定性的定义,排序的结果就一定不会出现{3,1}排在{3,4}前的情况。而如果算法是不稳定的,那么只能说,{3,1}有排在{3,4}前面的可能,需要根据具体的排序过程判断是否相等的值会变换位置。关于八种算法稳定性的分析,可以查看http://hi.baidu.com/shismbwb/item/404c94898cfd2855850fab24。选择排序、快速排序、希尔排序、堆排序不是稳定的排序算法,而冒泡排序、插入排序、归并排序和基数排序是稳定的排序算法。
所以,首先明确四个函数都采用了什么样的排序算法:
f1:选择排序;f2:直接插入排序;f3:冒泡,f4:快排
f2和f3是稳定的,直接pass掉。然后非稳定的再看是否变换了位置。A和D如果走一遍程序的话,会发现{3,4}和{3,1}这两个元素是变了顺序的。
对于A答案,a[5]={{3,4},{6,5},{2,7},{3,1},{1,2}}
第一遍排序:{{1,2},{6,5},{2,7},{3,1},{3,4}}
第二遍排序:{{1,2},{2,7},{6,5},{3,1},{3,4}}
第三遍排序:{{1,2},{2,7},{3,1},{6,5},{3,4}}
第四遍排序:{{1,2},{2,7},{3,1},{3,4},{6,5}}
所以正确
对于D答案,a[5]={{3,4},{6,5},{2,7},{3,1},{1,2}}
第一遍排序的运行过程是这样的。
初始:low=0,high=4,i=0,t={3,4}
For循环:
J=1, c({6,5},t)>0,i=0,没有交换(a[i],a[j]),{{3,4},{6,5},{2,7},{3,1},{1,2}}
J=2,c({2,7},t)<0,i=1,交换({6,5},{2,7}),{{3,4},{2,7},{6,5},{3,1},{1,2}}
J=3, c({3,1},t)=0,i=2,交换({6,5},{3,1}),{{3,4},{2,7},{3,1},{6,5},{1,2}}
J=4, c({1,2},t)<0,i=3,交换({6,5},{1,2}),{{3,4},{2,7},{3,1},{1,2},{6,5}}
最后,执行exchange(a,low,i), 交换({3,4},{1,2}),{{1,2},{2,7},{3,1},{3,4},{6,5}}
得到第一遍排序结果:{{1,2},{2,7},{3,1},{3,4},{6,5}},找到了{3,1}的位置,已经在{3,4}的前面,所以最后的结果一定与预期结果相同。这里需要非常注意的是在_f41函数中,if(c(a[j],t)<=0),如果写成c(a[j],t)<0的话,则该答案也不会选择。所以最终的答案是A和D
20. A particular BNF definition for a "word" is given by the following rules:

Which of the following lexical entieies can be derived from <word>? I. abcd II. bcdef III.d22
A. None B. I and II only C. I and III only D. II and III only E. I,II and III
算是一道考察形式自动机的题。关键是分析清楚每种模式本质上代表什么。<letter>表示单个字母;<digit>表示单个数字;<pairdig>是两个<digit>,或者递归<pairdig>和两个<digit>,其实表示的是偶数个<digit>,即偶数个数字;同理,<pairlet>是偶数个字母。所以<word>的可能是:1个字母,奇数个字母,或者一个字母和偶数个数字。所以第二个和第三个是正确的。