StrongSwan IKEv2 搭建Linux 与 Cisco的 GRE Tunnel over IPsec IKEv2
目录
- StrongSwan IKEv2 搭建Linux 与 Cisco的 GRE Tunnel over IPsec IKEv2
- 环境
- 效果图
- 安装
- 配置
- 应用
StrongSwan IKEv2 搭建Linux 与 Cisco的 GRE Tunnel over IPsec IKEv2
环境
Linux:
cat /proc/version
Linux version 4.15.0-73-generic (buildd@lcy01-amd64-006) (gcc version 7.4.0 (Ubuntu 7.4.0-1ubuntu1~18.04.1)) #82-Ubuntu SMP Tue Dec 3 00:04:14 UTC 2019
Cisco:
show version
Cisco IOS Software, C880 Software (C880DATA-UNIVERSALK9-M), Version 15.6(3)M3, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2017 by Cisco Systems, Inc.
Compiled Wed 26-Jul-17 02:21 by prod_rel_team
StrongSwan:
ipsec version
Linux strongSwan U5.6.2/K4.15.0-73-generic
Institute for Internet Technologies and Applications
University of Applied Sciences Rapperswil, Switzerland
See 'ipsec --copyright' for copyright information.
vlan1(192.168.1.1/24) = = = = = = = = = loopback0(192.168.2.1/24)
Linux:enp2s0(10.207.238.11/24)------(10.207.238.21/24)F4:Cisco
Tunnel100 = = = = = = = = = = = = = = = = = = Tunnel1
ip addr 192.168.100.1/24#################ip addr 192.168.100.2/24
tunnel local 192.168.1.1##################tunnel source 192.168.2.1
tunnel remote 192.168.2.1################tunnel destination 192.168.1.1
效果图
安装
apt-get install openssl libssl-dev strongswan libstrongswan
ipsec --help
ipsec command [arguments]
Commands:
start|restart [arguments]
update|reload|stop
up|down|route|unroute <connectionname>
down-srcip <start> [<end>]
status|statusall [<connectionname>]
listalgs|listpubkeys|listcerts [--utc]
listcacerts|listaacerts|listocspcerts [--utc]
listacerts|listgroups|listcainfos [--utc]
listcrls|listocsp|listplugins|listall [--utc]
listcounters|resetcounters [name]
leases [<poolname> [<address>]]
rereadsecrets|rereadcacerts|rereadaacerts
rereadocspcerts|rereadacerts|rereadcrls|rereadall
purgecerts|purgecrls|purgeike|purgeocsp
scepclient|pki
stroke
version
Refer to the ipsec(8) man page for details.
Some commands have their own man pages, e.g. pki(1) or scepclient(8).
配置
- Linux #####################################################################
/etc/ipsec.conf
conn %default
ikelifetime=1440m
keylife=60m
rekeymargin=3m
keyingtries=3
keyexchange=ikev1
authby=secret
conn cisco
#本地公网IP
left=10.207.238.11
#本地内网IP(段)
leftsubnet=192.168.1.0/24
#本地IKE ID,Cisco的会默认设定ID为IP,所以这里直接写本地IP。
leftid=10.207.238.11
leftfirewall=yes
#对端公网IP
right=10.207.238.21
对端内网IP(段)
rightsubnet=192.168.2.0/24
#对端IKE ID
rightid=10.207.238.21
auto=add
ike=aes128-sha1-modp1536
esp=aes128-sha1
#启用IKEv2
keyexchange=ikev2
/etc/ipsec.secrets
10.207.238.11 : PSK "cisco"
10.207.238.21 : PSK "cisco"
ipsec restart
ipsec status
//创建GRE Tunnel100
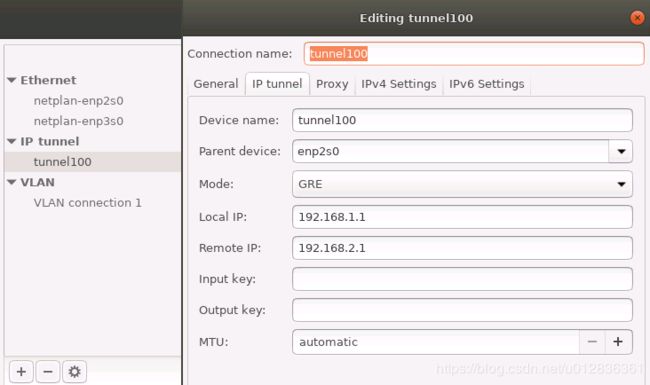
ip tunnel add tunnel100 mode gre local 192.168.1.1 remote 192.168.2.1 ttl 255 dev enp2s0
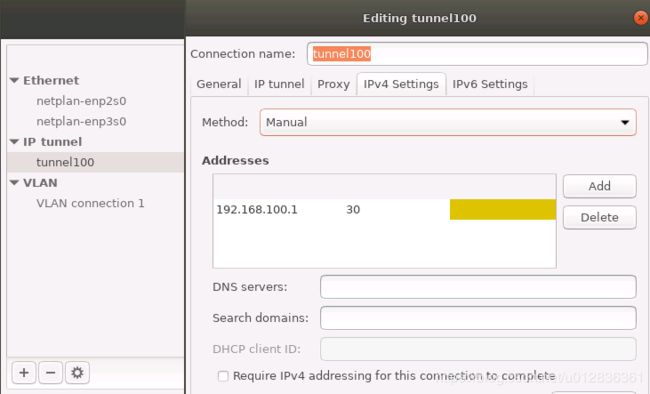
ip addr add 192.168.100.1/30 dev tunnel100 peer 192.168.100.2/30
ip link set dev tunnel100 up
- Cisco ########################################################################
interface FastEthernet4
mtu 1600
ip address 10.207.237.21 255.255.255.0
no ip route-cache
duplex auto
speed auto
no cdp enable
!
interface Tunnel1
ip address 192.168.100.2 255.255.255.252
tunnel source 192.168.2.1
tunnel destination 192.168.1.1
!
crypto ikev2 proposal ikev2Proposal
encryption aes-cbc-128
integrity sha1
group 5
!
crypto ikev2 policy ikev2policy
match fvrf any
proposal ikev2Proposal
!
crypto ikev2 keyring keys
peer strongswan
address 10.207.238.11
pre-shared-key local cisco
pre-shared-key remote cisco
!
crypto ikev2 profile ikev2profile
match identity remote address 0.0.0.0
match identity remote address 10.207.238.11 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local keys
!
crypto ipsec transform-set TS esp-aes esp-sha-hmac
mode tunnel
!
ip route 192.168.1.0 255.255.255.0 10.207.238.11 name IPSec
!
ip access-list extended cryptoacl
permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
!
crypto map cmap 10 ipsec-isakmp
set peer 10.207.238.11
set transform-set TS
set ikev2-profile ikev2profile
match address cryptoacl
!
interface FastEthernet4
crypto map cmap
!
#建立Track去定时触发 IPSec
!
ip sla 1
icmp-echo 192.168.1.1 source-ip 192.168.2.1
tos 224
threshold 3000
timeout 3000
frequency 3
ip sla schedule 1 life forever start-time now
!
track 1 ip sla 1 reachability
delay down 25 up 9
// 查看会话是否建立
R-test#show crypto session
Crypto session current status
Interface: FastEthernet4
Profile: ikev2profile
Session status: UP-ACTIVE
Peer: 10.207.238.11 port 500
Session ID: 1
IKEv2 SA: local 10.207.238.21/500 remote 10.207.238.11/500 Active
IPSEC FLOW: permit ip 192.168.2.0/255.255.255.0 192.168.1.0/255.255.255.0
Active SAs: 2, origin: crypto map
// 测试Cisco Lookback 0 与 Linux Vlan1的连通性
R-test#ping 192.168.1.1 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
R-test#show track
Track 1
IP SLA 1 reachability
Reachability is Up
1 change, last change 02:23:53
Delay up 9 secs, down 25 secs
Latest operation return code: OK
Latest RTT (millisecs) 1
!
interface Tunnel1
ip address 192.168.100.2 255.255.255.252
tunnel source 192.168.2.1
tunnel destination 192.168.1.1
!
应用
Linux 与 Cisco 互写静态路由
interface Vlan1
ip address 10.1.1.1 255.255.255.0
pppoe enable group global
!
ip dhcp excluded-address 192.168.1.1
!
ip dhcp pool test
network 10.1.1.0 255.255.255.0
dns-server 114.114.114.114
domain-name test.gogo.org
- Linux
写入静态路由,到Cisco Vlan1(10.1.1.0/24)的路由出口为Tunnel00
```bash
ip route add 10.1.1.0/24 dev tunnel100
ip route
10.1.1.0/24 dev tunnel100 scope link
10.207.238.0/24 dev enp2s0 proto kernel scope link src 10.207.238.11 metric 100
172.16.1.0/24 dev vlanif2 proto kernel scope link src 172.16.1.1 metric 401
192.168.1.0/24 dev vlanif1 proto kernel scope link src 192.168.1.1 metric 400
192.168.100.0/30 dev tunnel100 proto kernel scope link src 192.168.100.1
- Cisco
写入静态路由,到Linux Vlan2(172.16.1.0/24)的路由下出口为Tunnel1,下一跳为192.168.100.2
ip route 172.16.1.0 255.255.255.0 Tunnel1 192.168.100.1 name ToLinuxSubnet
show ip route 172.16.1.0
Routing entry for 172.16.1.0/24
Known via "static", distance 1, metric 0
Routing Descriptor Blocks:
* 192.168.100.1, via Tunnel1
Route metric is 0, traffic share count is 1
- Linux Vlan2— Cisco Vlan1 互相Ping && Tracert
ping 10.1.1.1
PING 10.1.1.1 (10.1.1.1) 56(84) bytes of data.
64 bytes from 10.1.1.1: icmp_seq=1 ttl=255 time=10.0 ms
64 bytes from 10.1.1.1: icmp_seq=2 ttl=255 time=1.38 ms
64 bytes from 10.1.1.1: icmp_seq=3 ttl=255 time=1.37 ms
64 bytes from 10.1.1.1: icmp_seq=4 ttl=255 time=1.38 ms
^C
--- 10.1.1.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 1.372/3.550/10.052/3.754 ms
traceroute 10.1.1.1
traceroute to 10.1.1.1 (10.1.1.1), 30 hops max, 60 byte packets
1 192.168.100.2 (192.168.100.2) 8.519 ms * *
ping 172.16.1.1 source vlan 1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
traceroute 172.16.1.1 source vlan 1
Type escape sequence to abort.
Tracing the route to 172.16.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 172.16.1.1 0 msec 0 msec 0 msec
ip route 0.0.0.0 0.0.0.0 Tunnel1