centos安装LDAP即配置
1、安装ldap
(1)
#yum install -y openldap openldap-clients openldap-servers migrationtools
#cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
#chown ldap. /var/lib/ldap/DB_CONFIG
#systemctl start slapd 启动slapd
#systemctl enable slapd 设置开机启动
(2)查看是否已经安装 OpenLDAP:
# rpm -qa | grep openldap
显示如下:
openldap-2.4.40-13.el7.x86_64
openldap-servers-2.4.40-13.el7.x86_64
openldap-clients-2.4.40-13.el7.x86_64
(3)查看端口使用情况:
# netstat -tlnp | grep slapd
显示如下
Tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 227/slapd
tcp6 0 0 :::389 :::* LISTEN 227/slapd
默认情况下, slapd 用户会占用 389 端口。
2、配置ldap服务,设置openldap 的admin 密码。
# slappasswd
显示如下,需要输入两次密码
New password:
Re-enter new password:
显示如下,记下这个密码
{SSHA}XXXXXXXXXXXXXX
其中{SSHA}XXXXXXXXXXXXXX 就是加密处理后的明文密码,之后会用到这个密码。
之后再新建如下文件:
# vi chrootpw.ldif
输入如下内容,记得olcRootPW改为你生成的密码
# specify the password generated above for "olcRootPW" section
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}XXXXXXXXXXXXXX
然后导入该文件:
# ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif
输出如下:
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={0}config,cn=config"
3.导入基础的Schemas
(1)
# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
输出如下:
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=cosine,cn=schema,cn=config"
(2)
# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
输出如下:
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=nis,cn=schema,cn=config"
(3)
#ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
输出如下:
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=inetorgperson,cn=schema,cn=config"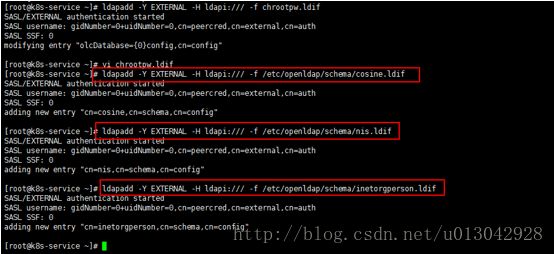
4.在LDAP DB设置domain name
(1)首先要生成经处理后的目录管理者明文密码:
# slappasswd
New password:
Re-enter new password:
{SSHA}XXXXXXXXXXXXXX
(2)之后,再新建如下文件:
vi chdomain.ldif文件内容如下,注意,要使用你自己的域名替换掉文件中所有的 "dc=***,dc=***",并且使用刚刚生成的密码,替换文中的 "olcRootPW" 部分:
# vi chdomain.ldif
输入一下内容
# replace to your own domain name for "dc=***,dc=***" section
# specify the password generated above for "olcRootPW" section
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth"
read by dn.base="cn=Manager,dc=nscc,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=nscc,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=nscc,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}XXXXXXXXXXXXXX
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by
dn="cn=Manager,dc=nscc,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=nscc,dc=com" write by * read
(4)之后再导入该文件:
# ldapmodify -Y EXTERNAL -H ldapi:/// -f chdomain.ldif
输出如下:
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={1}monitor,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
(5)然后再新建如下文件:文件内容如下,注意,要使用你自己的域名替换掉文件中所有的 "dc=***,dc=***":
# vi basedomain.ldif
输入以下内容:
# replace to your own domain name for "dc=***,dc=***" section
dn: dc=nscc,dc=com
objectClass: top
objectClass: dcObject
objectclass: organization
o: Server World
dc: nscc
dn: cn=Manager,dc=nscc,dc=com
objectClass: organizationalRole
cn: Manager
description: Directory Manager
dn: ou=People,dc=nscc,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=nscc,dc=com
objectClass: organizationalUnit
ou: Group
最后导入该文件:
# ldapadd -x -D cn=Manager,dc=nscc,dc=com -W -f basedomain.ldif
输出如下:
Enter LDAP Password: # directory manager's password
adding new entry "dc=nscc,dc=com"
adding new entry "cn=Manager,dc=nscc,dc=com"
adding new entry "ou=People,dc=nscc,dc=com"
adding new entry "ou=Group,dc=nscc,dc=com"
5、允许防火墙访问 LDAP 服务。开启 389/TCP 端口(根据你自己的防火墙进行设置):
若使用的是 firewall,修改方法如下:
# firewall-cmd --add-service=ldap --permanent
success
# firewall-cmd --reload
success
或者直接关闭防火墙:
systemctl stop firewalld
systemctl disable firewalld
setenforce 0
6、向 OpenLDAP Server 中添加用户
(1)首先要生成经处理后的明文密码:
# slappasswd
New password:
Re-enter new password:
{SSHA}XXXXXXXXXXXXX
(2)之后再新建如下文件: 文件内容如下,注意,要使用你自己的域名替换掉文件中所有的 "dc=***,dc=***",并且使用刚刚生成的密码,替换文中的 "userPassword" 部分:
# vi ldapuser.ldif
输入以下内容:
# create new
# replace to your own domain name for "dc=***,dc=***" section
dn: uid=cent,ou=People,dc=nscc,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
cn: Cent
sn: Linux
userPassword: {SSHA}XXXXXXXXXXXXXXXX
loginShell: /bin/bash
uidNumber: 1000
gidNumber: 1000
homeDirectory: /home/cent
dn: cn=cent,ou=Group,dc=nscc,dc=com
objectClass: posixGroup
cn: Cent
gidNumber: 1000
memberUid: cent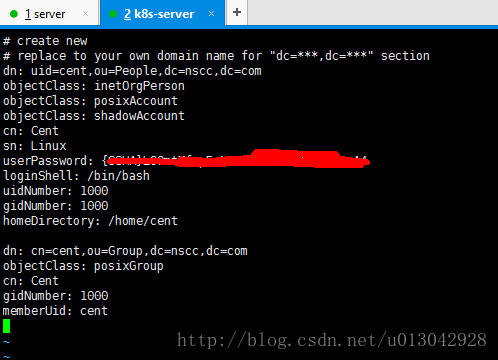
(3)最后导入该文件:
# ldapadd -x -D cn=Manager,dc=nscc,dc=com -W -f ldapuser.ldif
Enter LDAP Password:
adding new entry "uid=cent,ou=People,dc=nscc,dc=com"
adding new entry "cn=cent,ou=Group,dc=nscc,dc=com"


