Kubernetes---- 二进制集群部署(ETCD集群+Flannel网络)
文章目录
- 前言:
- 一、实验环境
- 二、ETCD集群部署
- 2.1 master 节点部署
- 2.1.1 定义两个脚本文件
- 2.1.2 创建证书
- 2.1.3 ETCD 部署
- 2.2 node节点部署
- 三、Flannel网络部署
- 3.1 Flannel 介绍
- 3.1.1 Flannel 网络概述
- 3.1.2 flannel网络架构图
- 3.2 flannel部署
- 3.2.1 flannel网络配置
- 3.2.2 测试容器间互通
- 总结
前言:
- 本篇博客主要介绍二进制集群之etcd+flannel组件部署~
一、实验环境
-
本实验需求为3个节点即可,配置2+4(2个CPU+4G内存)
-
主机角色分配为:
① master 节点IP:192.168.226.128
-
需安装的软件:
kube-apiserver
kube-controller-manager
kube-scheduler
etcd
② node1 节点IP:192.168.226.132
-
需安装的软件:
kubelet
kube-proxy
docker
flannel
etcd
③ node2 节点IP:192.168.226.133
- 需安装的软件与node1相同
-
-
官网源码包下载:https://github.com/kubernetes/kubernetes/releases?after=v1.13.1
-
ETCD 二进制包地址:https://github.com/etcd-io/etcd/releases
二、ETCD集群部署
2.1 master 节点部署
2.1.1 定义两个脚本文件
- 创建/k8s目录,在创建两个脚本
[root@master ~]# mkdir k8s
[root@master ~]# cd k8s
[root@master k8s]# ls
etcd-cert.sh etcd.sh
#etcd-cert.sh 是证书制作的脚本
#etcd.sh etcd启动脚本-
etcd-cert.sh 证书制作脚本详解
以下脚本书写的格式为:jason
[root@master k8s]# cat etcd-cert.sh
cat > ca-config.json <
{
"signing": { #键名称
"default": {
"expiry": "87600h" #证书有效期(10年)
},
"profiles": { #简介
"www": { #名称
"expiry": "87600h",
"usages": [ #使用方法
"signing", #键
"key encipherment", #密钥验证(密钥验证要设置在CA证书中)
"server auth", #服务器端验证
"client auth" #客户端验证
]
}
}
}
}
EOF
cat > ca-csr.json <
{
"CN": "etcd CA", #CA签名为etcd指定(三个节点均需要)
"key": {
"algo": "rsa", #使用rsa非对称密钥的形式
"size": 2048 #密钥长度为2048
},
"names": [ #在证书中定义信息(标准格式)
{
"C": "CN", #名称
"L": "Beijing",
"ST": "Beijing"
}
]
}
EOF
cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
#-----------------------
cat > server-csr.json <
{
"CN": "etcd",
"hosts": [ #定义三个节点的IP地址
"192.168.226.128",
"192.168.226.132",
"192.168.226.133"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server
#cfssl 为证书制作工具 - etcd.sh 启动脚本内容详解
[root@master k8s]# cat etcd.sh
#!/bin/bash
#以下为使用格式:etcd名称 当前etcd的IP地址+完整的集群名称和地址
# example: ./etcd.sh etcd01 192.168.1.10 etcd02=https://192.168.1.11:2380,etcd03=https://192.168.1.12:2380
ETCD_NAME=$1 #位置变量1:etcd节点名称
ETCD_IP=$2 #位置变量2:节点地址
ETCD_CLUSTER=$3 #位置变量3:集群
WORK_DIR=/opt/etcd #指定工作目录
cat <$WORK_DIR/cfg/etcd #在指定工作目录创建ETCD的配置文件
#[Member]
ETCD_NAME="$ {ETCD_NAME}" #etcd名称
ETCD_DATA_DIR="/var/lib/etcd/default.etcd"
ETCD_LISTEN_PEER_URLS="https://${ETCD_IP}:2380" #etcd IP地址:2380端口。用于集群之间通讯
ETCD_LISTEN_CLIENT_URLS="https://${ETCD_IP}:2379" #etcd IP地址:2379端口,用于开放给外部客户端通讯
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://${ETCD_IP}:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://${ETCD_IP}:2379" #对外提供的url使用https的协议进行访问
ETCD_INITIAL_CLUSTER="etcd01=https://${ETCD_IP}:2380,${ETCD_CLUSTER}" #多路访问
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster" #tokens 令牌环名称:etcd-cluster
ETCD_INITIAL_CLUSTER_STATE="new" #状态,重新创建
EOF
cat </usr/lib/systemd/system/etcd.service #定义ectd的启动脚本
[Unit] #基本项
Description=Etcd Server #类似为 etcd 服务
After=network.target #vu癌症
After=network-online.target
Wants=network-online.target
[Service] #服务项
Type=notify
EnvironmentFile=$ {WORK_DIR}/cfg/etcd #etcd文件位置
ExecStart=${WORK_DIR}/bin/etcd \ #准启动状态及以下的参数
--name=\${ETCD_NAME} \
--data-dir=\${ETCD_DATA_DIR} \
--listen-peer-urls=\${ETCD_LISTEN_PEER_URLS} \
--listen-client-urls=\${ETCD_LISTEN_CLIENT_URLS},http://127.0.0.1:2379 \
--advertise-client-urls=\${ETCD_ADVERTISE_CLIENT_URLS} \ #以下为群集内部的设定
--initial-advertise-peer-urls=\${ETCD_INITIAL_ADVERTISE_PEER_URLS} \
--initial-cluster=\${ETCD_INITIAL_CLUSTER} \
--initial-cluster-token=\${ETCD_INITIAL_CLUSTER_TOKEN} \ #群集内部通信,也是使用的令牌,为了保证安全(防范中间人窃取)
--initial-cluster-state=new \
--cert-file=${WORK_DIR}/ssl/server.pem \ #证书相关参数
--key-file=${WORK_DIR}/ssl/server-key.pem \
--peer-cert-file=${WORK_DIR}/ssl/server.pem \
--peer-key-file=${WORK_DIR}/ssl/server-key.pem \
--trusted-ca-file=${WORK_DIR}/ssl/ca.pem \
--peer-trusted-ca-file=${WORK_DIR}/ssl/ca.pem
Restart=on-failure
LimitNOFILE=65536 #开放最多的端口号
[Install]
WantedBy=multi-user.target #进行启动
EOF
systemctl daemon-reload #参数重载
systemctl enable etcd
systemctl restart etcd
2.1.2 创建证书
- 首先,创建证书目录,复制k8s目录下的证书创建脚本
[root@master k8s]# mkdir etcd-cert
[root@master k8s]# ls
etcd-cert etcd-cert.sh etcd.sh
[root@master k8s]# cd etcd-cert/
[root@master etcd-cert]# mv ../etcd-cert.sh ./
[root@master etcd-cert]# ls
etcd-cert.sh
-
创建cfssl类型工具下载脚本
先从官网源中制作证书的工具下载下来
[root@master etcd-cert]# cat cfssl.sh
#先从官网源中制作证书的工具下载下来,(-o:导出)放在/usr/local/bin中便于系统识别
curl -L https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -o /usr/local/bin/cfssl
#从另一个站点源中下载cfssljson工具,用于识别json配置文件格式
curl -L https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -o /usr/local/bin/cfssljson
#下载cfssl-certinfo工具
curl -L https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -o /usr/local/bin/cfssl-certinfo
#给与权限
chmod +x /usr/local/bin/cfssl /usr/local/bin/cfssljson /usr/local/bin/cfssl-certinfo
[root@master etcd-cert]# bash cfssl.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 9.8M 100 9.8M 0 0 516k 0 0:00:19 0:00:19 --:--:-- 622k
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2224k 100 2224k 0 0 181k 0 0:00:12 0:00:12 --:--:-- 264k
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6440k 100 6440k 0 0 431k 0 0:00:14 0:00:14 --:--:-- 796k
[root@master etcd-cert]# ls /usr/local/bin
cfssl cfssl-certinfo cfssljson-
定义生成CA证书的配置文件
生成在etcd-cert目录下
[root@master etcd-cert]# cat > ca-config.json <
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"www": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
[root@master etcd-cert]# ls
ca-config.json cfssl.sh etcd-cert.sh
- 定义生成证书签名文件
[root@master etcd-cert]# cat > ca-csr.json <
{
"CN": "etcd CA", #证书名称 etcd CA
"key": {
"algo": "rsa", #algo:算法 rsa 非对称密钥
"size": 2048
},
"names": [ #项目标题
{
"C": "CN",
"L": "Beijing",
"ST": "Beijing"
}
]
}
EOF
[root@master etcd-cert]# ls
ca-config.json ca-csr.json cfssl.sh etcd-cert.sh
-
生成证书
需生成ca-key.pem 密钥证书和ca.pem证书
#命令、参数介绍:
#使用cfssl工具制作证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
#gencert-initca:初始化ca
#初始化对象为csr.json
#cfssljson -bare ca - 对照ca-config-json配置文件生成证书
#以下为过程
[root@master etcd-cert]# cfssl gencert -initca ca-csr.json | cfssljson -bare ca -
2020/04/28 22:23:51 [INFO] generating a new CA key and certificate from CSR
2020/04/28 22:23:51 [INFO] generate received request
2020/04/28 22:23:51 [INFO] received CSR
2020/04/28 22:23:51 [INFO] generating key: rsa-2048
2020/04/28 22:23:51 [INFO] encoded CSR
2020/04/28 22:23:51 [INFO] signed certificate with serial number 183162516941087785302161335460622789346733634483
[root@master etcd-cert]# ls
ca-config.json ca.csr ca-csr.json ca-key.pem ca.pem cfssl.sh etcd-cert.sh
-
指定etcd三个节点之间的通信验证
定义服务器端的json文件
[root@master etcd-cert]# cat > server-csr.json <
{
"CN": "etcd",
"hosts": [ #定义群集IP
"192.168.226.128",
"192.168.226.132",
"192.168.226.133"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [ #项目名称,内容需要与ca证书对应
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF
[root@master etcd-cert]# ls
ca-config.json ca-csr.json ca.pem etcd-cert.sh
ca.csr ca-key.pem cfssl.sh server-csr.json - 生成服务器端密钥证书:server-key.pem 和服务器端证书:server.pem
[root@master etcd-cert]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server
#命令参数简介:cfssl gencert 使用cfssl工具制作证书
#-ca=ca.pem 制作证书依赖于CA颁发的ca.pem
#-ca-key=ca-key.pem 制作证书同时依赖于CA的密钥证书
#-config=ca-config.json 制作证书需要使用到ca的配置文件
#-profile=www 文件名为www
#server-csr.json 使用之前制作的的签名文件
#| cfssljson -bare server 生成证书
#制作过程
[root@master etcd-cert]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server
2020/04/28 22:48:27 [INFO] generate received request
2020/04/28 22:48:27 [INFO] received CSR
2020/04/28 22:48:27 [INFO] generating key: rsa-2048
2020/04/28 22:48:27 [INFO] encoded CSR
2020/04/28 22:48:27 [INFO] signed certificate with serial number 355665838045981162128613702213192731340064915336
2020/04/28 22:48:27 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").- 以上证书制作已完成,现已产生的证书文件主要包含以下:
[root@master etcd-cert]# ls
ca-config.json ca-csr.json ca.pem etcd-cert.sh server-csr.json server.pem
ca.csr ca-key.pem cfssl.sh server.csr server-key.pem
#其中 ca.pem、ca-key.pem、server.pem、 server-key.pem 就是我们制作完成的服务端证书和客户端证书2.1.3 ETCD 部署
-
① 下载、解压软件包
本次实验软件包已下载完成,软件包下载地址在博客开头已给出
下载并将以下软件包,并放在k8s目录下
etcd-v3.3.10-linux-amd64.tar.gz
flannel-v0.10.0-linux-amd64.tar.gz
kubernetes-server-linux-amd64.tar.gz
[root@master k8s]# ls
etcd-cert etcd-v3.3.10-linux-amd64.tar.gz kubernetes-server-linux-amd64.tar.gz
etcd.sh flannel-v0.10.0-linux-amd64.tar.gz- 解压etcd-v3.3.10-linux-amd64.tar.gz
[root@master k8s]# tar zxvf etcd-v3.3.10-linux-amd64.tar.gz
[root@master k8s]# ls etcd-v3.3.10-linux-amd64
Documentation etcd etcdctl README-etcdctl.md README.md READMEv2-etcdctl.md
-
创建ETCD工作目录
创建包括cfg:配置文件目录、bin:命令文件目录、ssl:证书文件目录
[root@master k8s]# mkdir /opt/etcd/{cfg,bin,ssl} -p
[root@master k8s]# ls /opt/etcd
bin cfg ssl
- 拷贝命令文件
[root@master k8s]# mv etcd-v3.3.10-linux-amd64/etcd etcd-v3.3.10-linux-amd64/etcdctl /opt/etcd/bin
[root@master k8s]# ls /opt/etcd/bin
etcd etcdctl- 拷贝证书文件
[root@master k8s]# cp etcd-cert/*.pem /opt/etcd/ssl
[root@master k8s]# ls /opt/etcd/ssl/
ca-key.pem ca.pem server-key.pem server.pem-
进入卡住状态等待其他节点加入
执行此命令会产生两个文件,一个是配置文件,一个是启动脚本
同时,等待加入的过程大约在5分钟左右,如果没有节点接入则会自动退出
[root@master k8s]# bash etcd.sh etcd01 192.168.226.128 etcd02=https://192.168.226.132:2380,etcd03=https://192.168.226.133:2380
Created symlink from /etc/systemd/system/multi-user.target.wants/etcd.service to /usr/lib/systemd/system/etcd.service.
- 另起终端,查看产生的配置文件
[root@master ~]# cd /opt/etcd/cfg
[root@master cfg]# ls
etcd
[root@master cfg]# cat etcd
#[Member]
ETCD_NAME="etcd01"
ETCD_DATA_DIR="/var/lib/etcd/default.etcd"
ETCD_LISTEN_PEER_URLS="https://192.168.226.128:2380"
ETCD_LISTEN_CLIENT_URLS="https://192.168.226.128:2379"
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.226.128:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://192.168.226.128:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://192.168.226.128:2380,etcd02=https://192.168.226.132:2380,etcd03=https://192.168.226.133:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
#以上则是群集信息和各节点信息,配置文件中的变量引用的则是我们之前在k8s目录中设置的启动脚本变量- 查看etcd 状态/进程
[root@master cfg]# ps -ef | grep etcd
root 80972 1 2 10:56 ? 00:00:00 /opt/etcd/bin/etcd --name=etcd01 --data-dir=/var/lib/etcd/default.etcd --listen-peer-urls=https://192.168.226.128:2380 --listen-client-urls=https://192.168.226.128:2379,http://127.0.0.1:2379 --advertise-client-urls=https://192.168.226.128:2379 --initial-advertise-peer-urls=https://192.168.226.128:2380 --initial-cluster=etcd01=https://192.168.226.128:2380,etcd02=https://192.168.226.132:2380,etcd03=https://192.168.226.133:2380 --initial-cluster-token=etcd-cluster --initial-cluster-state=new --cert-file=/opt/etcd/ssl/server.pem --key-file=/opt/etcd/ssl/server-key.pem --peer-cert-file=/opt/etcd/ssl/server.pem --peer-key-file=/opt/etcd/ssl/server-key.pem --trusted-ca-file=/opt/etcd/ssl/ca.pem --peer-trusted-ca-file=/opt/etcd/ssl/ca.pem
root 81895 71883 0 10:56 pts/2 00:00:00 grep --color=auto etcd
- 最后,将证书和启动脚本推送/复制到两台node节点中
#将etcd所有的配置文件、证书、脚本复制到两个节点
[root@master k8s]# scp -r /opt/etcd/ [email protected]:/opt
[root@master k8s]# scp -r /opt/etcd/ [email protected]:/opt
#将启动脚本复制到两个节点
[root@master k8s]# scp -r /usr/lib/systemd/system/etcd.service [email protected]:/usr/lib/systemd/system/
[root@master k8s]# scp -r /usr/lib/systemd/system/etcd.service [email protected]:/usr/lib/systemd/system/
2.2 node节点部署
- 查看、修改配置文件
[root@node1 ~]# ls /usr/lib/systemd/system/ | grep etcd
etcd.service
[root@node1 ~]# vim /opt/etcd/cfg/etcd
#[Member]
ETCD_NAME="etcd02" #需修改节点名称
ETCD_DATA_DIR="/var/lib/etcd/default.etcd"
ETCD_LISTEN_PEER_URLS="https://192.168.226.132:2380" #将url:2380端口的IP地址改为132(本地节点IP)
ETCD_LISTEN_CLIENT_URLS="https://192.168.226.132:2379" #将url:2379端口的IP地址改为132(本地节点IP)
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.226.132:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://192.168.226.132:2379"
#以上两条选项的地址也改为本地IP
ETCD_INITIAL_CLUSTER="etcd01=https://192.168.226.128:2380,etcd02=https://192.168.226.132:2380,etcd03=https://192.168.226.133:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
#同理修改node2节点配置文件- 启动服务
- 先在master节点使用命令,开启等待节点加入
- 其他两个node节点启动etcd 服务
#master节点:
[root@localhost k8s]# bash etcd.sh etcd01 192.168.226.128 etcd02=https://192.168.226.132:2380,etcd03=https://192.168.226.133:2380
#node1、node2节点
[root@node1 cfg]# systemctl start etcd
[root@node2 cfg]# systemctl start etcd
- 检查集群状态
#master节点
#因为查看节点命令中要使用到ca证书,所以必须在包含ca证书文件的目执行
[root@localhost k8s]# cd etcd-cert/
[root@localhost etcd-cert]# ls
ca-config.json ca-csr.json ca.pem etcd-cert.sh server.csr server-key.pem
ca.csr ca-key.pem cfssl.sh etcd.sh server-csr.json server.pem
[root@localhost etcd-cert]# /opt/etcd/bin/etcdctl --ca-file=ca.pem --cert-file=server.pem --key-file=server-key.pem --endpoints="https://192.168.226.128:2379,https://192.168.226.132:2379,https://192.168.226.133:2379" cluster-health
member 71154e5294d6d635 is healthy: got healthy result from https://192.168.226.128:2379
member ea2eb7f7893afcb7 is healthy: got healthy result from https://192.168.226.132:2379
member fab550d1713e6ebd is healthy: got healthy result from https://192.168.226.133:2379
cluster is healthy
#截至目前状态,三个节点的通讯已完成三、Flannel网络部署
3.1 Flannel 介绍
3.1.1 Flannel 网络概述
- flannel是CoreOS提供用于解决Dokcer集群跨主机通讯的覆盖网络工具。
- 它的主要思路是:预先留出一个网段,每个主机使用其中一部分,然后每个容器被分配不同的ip;让所有的容器认为大家在同一个直连的网络,底层通过UDP/VxLAN等进行报文的封装和转发。
- Overlay Network:覆盖网络,在基础网络上叠加的一种虚拟网络技术模式,该网络中的主机通过虚拟链路连接起来
- 类似VPN隧道,原理为在物理网络上实现的逻辑网络
- VXLAN:将源数据包封装到UDP中,并使用基础网络的IP/MAC作为外层包头进行封装,然后在以太网上传输,到达目的地后由隧道断电解封并将数据发给目标地址
- Flannel:是Overlay网络的一种,也是将源数据包封装在另一种网络包中进行路由转发和通信,目前已支持UDP、VXLAN、AWS VPN和GCE路由等数据转发方式
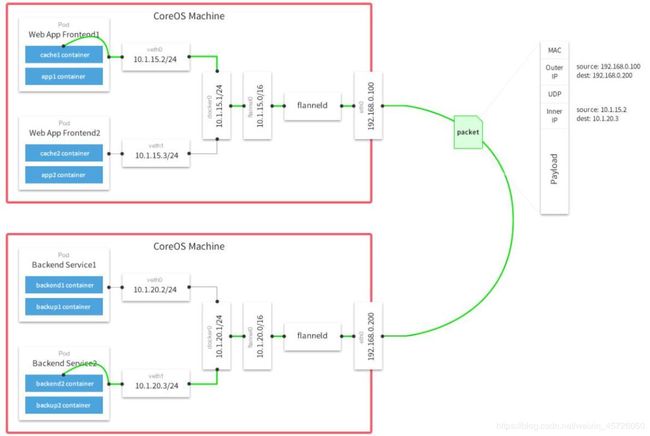
3.1.2 flannel网络架构图
- flannel原理简介:
- ① 数据从源容器中发出后,经由所在主机的docker0虚拟网卡转发到flannel0虚拟网卡,这是个P2P的虚拟网卡,flanneld服务监听在网卡的另外一端。
- ② Flannel通过Etcd服务维护了一张节点间的路由表,在稍后的配置部分我们会介绍其中的内容。
- ③ 源主机的flanneld服务将原本的数据内容UDP封装后根据自己的路由表投递给目的节点的flanneld服务,数据到达以后被解包,然后直接进入目的节点的flannel0虚拟网卡,然后被转发到目的主机的docker0虚拟网卡,最后就像本机容器通信一下的有docker0路由到达目标容器。
3.2 flannel部署
- 首先两个node节点需要先安装docker引擎,具体流程可见:Docker安装
3.2.1 flannel网络配置
- ① 写入分配的子网段到ETCD中,供flannel使用(master主机)
[root@localhost etcd-cert]# /opt/etcd/bin/etcdctl --ca-file=ca.pem --cert-file=server.pem --key-file=server-key.pem --endpoints="https://192.168.226.128:2379,https://192.168.226.132:2379,https://192.168.226.133:2379" set /coreos.com/network/config '{ "Network": "172.17.0.0/16", "Backend": {"Type": "vxlan"}}'
{ "Network": "172.17.0.0/16", "Backend": {"Type": "vxlan"}}‘
#命令简介:
#使用etcdctl命令,借助ca证书,目标断点为三个ETCD节点IP,端口为2379
#set /coreos.com/network/config 设置网段信息
#"Network": "172.17.0.0/16" 此网段必须是集合网段(B类地址),而Pod分配的资源必须在此网段中的子网段(C类地址)
#"Backend": {"Type": "vxlan"}} 外部通讯的类型是VXLAN- ② 查看写入的信息
[root@localhost etcd-cert]# /opt/etcd/bin/etcdctl --ca-file=ca.pem --cert-file=server.pem --key-file=server-key.pem --endpoints="https://192.168.226.128:2379,https://192.168.226.132:2379,https://192.168.226.133:2379" get /coreos.com/network/config
{ "Network": "172.17.0.0/16", "Backend": {"Type": "vxlan"}}
- ③ 上传flannel软件包到所有的 node 节点并解压
#node1
[root@node1 ~]# ls
anaconda-ks.cfg initial-setup-ks.cfg 公共 文档 模板 音乐
flannel-v0.10.0-linux-amd64.tar.gz 下载 图片 桌面 视频
[root@node1 ~]# tar zxvf flannel-v0.10.0-linux-amd64.tar.gz
flanneld
mk-docker-opts.sh
README.md
#node2同node1- ④ 创建k8s工作目录(所有node节点)
[root@node1 ~]# mkdir /opt/kubernetes/{cfg,bin,ssl} -p
[root@node1 ~]# mv mk-docker-opts.sh flanneld /opt/kubernetes/bin/
[root@node1 ~]# ls /opt/kubernetes/bin/
flanneld mk-docker-opts.sh
- ⑤ 创建启动脚本(两个node节点)
[root@node1 ~]# vim flannel.sh
#!/bin/bash
ETCD_ENDPOINTS=${1:-"http://127.0.0.1:2379"}
cat </opt/kubernetes/cfg/flanneld #创建配置文件
FLANNEL_OPTIONS="--etcd-endpoints=$ {ETCD_ENDPOINTS} \ #flannel在使用的时候需要参照CA证书
-etcd-cafile=/opt/etcd/ssl/ca.pem \
-etcd-certfile=/opt/etcd/ssl/server.pem \
-etcd-keyfile=/opt/etcd/ssl/server-key.pem"
EOF
cat </usr/lib/systemd/system/flanneld.service #创建启动脚本
[Unit]
Description=Flanneld overlay address etcd agent
After=network-online.target network.target
Before=docker.service
[Service]
Type=notify
EnvironmentFile=/opt/kubernetes/cfg/flanneld
ExecStart=/opt/kubernetes/bin/flanneld --ip-masq \$FLANNEL_OPTIONS
ExecStartPost=/opt/kubernetes/bin/mk-docker-opts.sh -k DOCKER_NETWORK_OPTIONS -d /run/flannel/subnet.env #Docker使用的网络是flannel提供的
Restart=on-failure
[Install]
WantedBy=multi-user.target #多用户模式
EOF
systemctl daemon-reload
systemctl enable flanneld
systemctl restart flanneld
-------》wq
#node2与node1相同 - ⑥ 开启flannel网络功能(两个node节点)
[root@node1 ~]# bash flannel.sh https://192.168.226.128:2379,https://192.168.226.132:2379,https://192.168.226.133:2379
Created symlink from /etc/systemd/system/multi-user.target.wants/flanneld.service to /usr/lib/systemd/system/flanneld.service.
#node2与node1相同- ⑦ 配置 docker 连接 flannel(两个node节点)
[root@node1 ~]# vim /usr/lib/systemd/system/docker.service
#在13行向下插入以下内容:
#想要docker可以使用flannel网络,需要设置env指向flannal的运行文件
EnvironmentFile=/run/flannel/subnet.env
#原14行在dockerd 添加一个参数$DOCKER_NETWORK_OPTIONS
#此参数作用为 让docker使用的网络组件为flannel,而不是自身的组件
ExecStart=/usr/bin/dockerd $DOCKER_NETWORK_OPTIONS -H fd:// --containerd=/run/containerd/containerd.sock
-----》wq- 查看flannel分配的子网段
#node1
[root@node1 ~]# cat /run/flannel/subnet.env
DOCKER_OPT_BIP="--bip=172.17.6.1/24" #bip:指定启动时的子网IP/网段
DOCKER_OPT_IPMASQ="--ip-masq=false"
DOCKER_OPT_MTU="--mtu=1450"
DOCKER_NETWORK_OPTIONS=" --bip=172.17.6.1/24 --ip-masq=false --mtu=1450"
#node2
[root@node2 ~]# cat /run/flannel/subnet.env
DOCKER_OPT_BIP="--bip=172.17.25.1/24"
DOCKER_OPT_IPMASQ="--ip-masq=false"
DOCKER_OPT_MTU="--mtu=1450"
DOCKER_NETWORK_OPTIONS=" --bip=172.17.25.1/24 --ip-masq=false --mtu=1450"
#也可以直接使用ifconfig查看flannel1信息- ⑧ 重载进程、重启docker
[root@node1 ~]# systemctl daemon-reload
[root@node1 ~]# systemctl restart docker3.2.2 测试容器间互通
- 在两个node节点下载centos:7 ,并直接进入容器
[root@node2 ~]# docker run -it centos:7 /bin/bash
Unable to find image 'centos:7' locally
7: Pulling from library/centos
ab5ef0e58194: Pull complete
Digest: sha256:4a701376d03f6b39b8c2a8f4a8e499441b0d567f9ab9d58e4991de4472fb813c
Status: Downloaded newer image for centos:7
[root@557a12dfadec /]# - 下载net-tools工具
yum install net-tools -y- 查看地址,使用ping 测试是否可以跨容器互通
#node1
[root@b3546847c994 /]# ifconfig
eth0: flags=4163 mtu 1450
inet 172.17.6.2 netmask 255.255.255.0 broadcast 172.17.6.255
ether 02:42:ac:11:06:02 txqueuelen 0 (Ethernet)
RX packets 9815 bytes 7594496 (7.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4498 bytes 246084 (240.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73 mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#node2
[root@557a12dfadec /]# ifconfig
eth0: flags=4163 mtu 1450
inet 172.17.25.2 netmask 255.255.255.0 broadcast 172.17.25.255
ether 02:42:ac:11:19:02 txqueuelen 0 (Ethernet)
RX packets 9812 bytes 7594774 (7.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4011 bytes 219965 (214.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73 mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- 测试互联
- flannel在其中做了路由的角色
总结
- 因为整个集群内部间的通信都需要ca证书支持,所以简单罗列出个组件/服务需要的证书:
- ① etcd (所有节点)
- ca.pem,server.pem,server-key.pem
- ② flannel(node节点)
- ca.pem,server.pem,server-key.pem
- ③ kube-apiserver(master节点)
- ca.pem,server.pem,server-key.pem
- ④ kubelet(node节点)
- ca.pem,server.pem
- ⑤ kube-proxy(node节点)
- ca.pem,kube-proxy.pem,kube-proxy-key.pem
- ⑥ kubectl (master节点)
- ca.pem,admin-pem,admin-key.pem