攻防世界misc高手进阶篇教程(2)
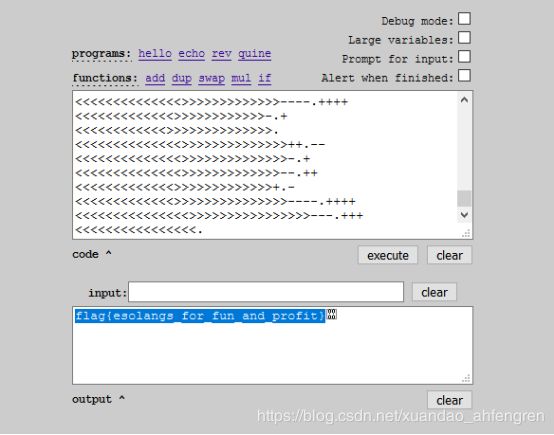
can_has_stdio?
通过brainfuck在线工具打开即可
http://esoteric.sange.fi/brainfuck/impl/interp/i.html
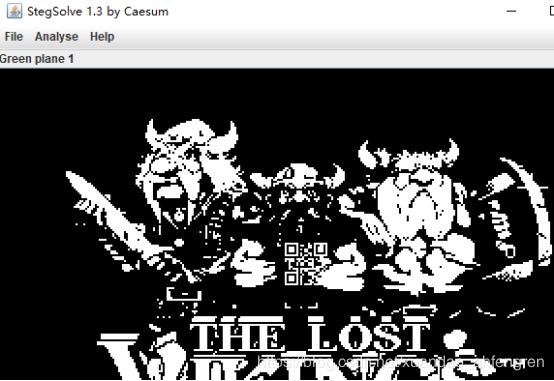
Erik-Baleog-and-Olaf
file发现是png格式,根据图片名字联想到使用Stegsolve工具
使用ps进行补全,扫描二维码得到flag
flag{#justdiffit}
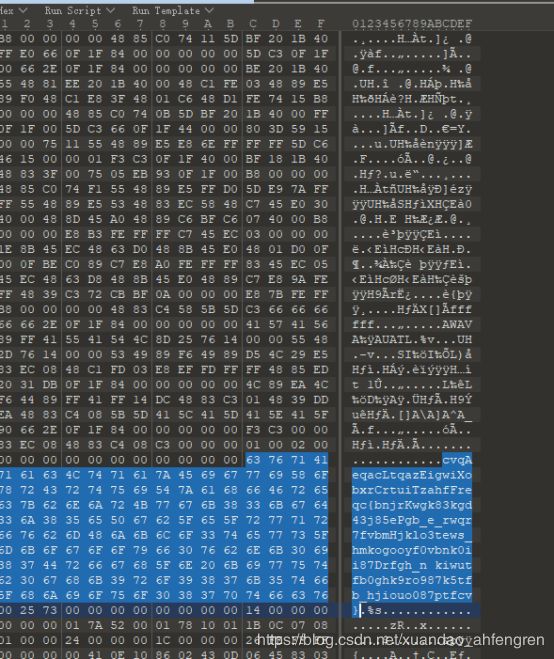
hit-the-core
用010editor打开,发现关键字符串
然后我们发现大写的XCTF每个字母之间只隔了四个字母,使用python提取一下,得到flag。
num='cvqAeqacLtqazEigwiXobxrCrtuiTzahfFreqc{bnjrKwgk83kgd43j85ePgb_e_rwqr7fvbmHjklo3tews_hmkogooyf0vbnk0ii87Drfgh_n kiwutfb0ghk9ro987k5tfb_hjiouo087ptfcv}'
flag = ''
for i in range(3,len(num),5):
flag += num[i]
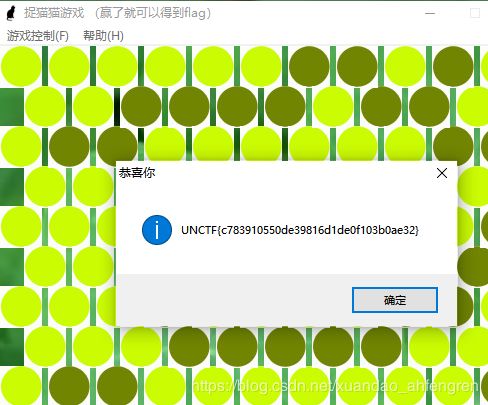
print(flag)快乐游戏题
直接通关就可以了
提示:flag是固定的可以直接提交,UNCTF{c783910550de39816d1de0f103b0ae32}
glance-50
用在线网站直接拼接
https://tu.sioe.cn/gj/fenjie/
TWCTF{Bliss by Charles O'Rear}
4-1
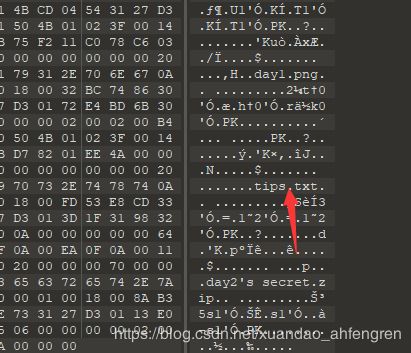
先用010editor编辑图片,发现txt文件,直接把后缀修改成zip把文件压缩出来
解压后txt中提示flag在day2.png中,猜想是盲水印
安装环境
sudo pip install matplotlib
pip install opencv-python
然后安装解密脚本
git clone https://github.com/chishaxie/BlindWaterMark
解密操作:
python bwm.py decode day1.png day2.png flag.png适合作为桌面
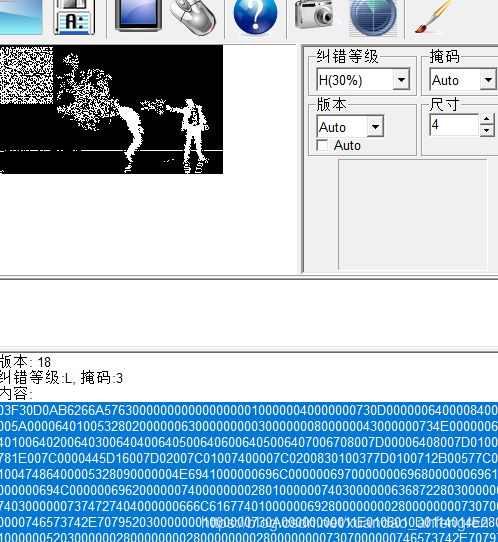
用Stegsolve打开左右调节即可出现二维码
再放在QR上面扫描二维码出现疑似十六进制的内容
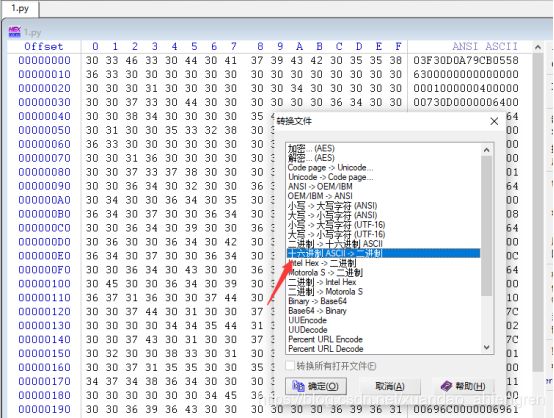
我们放在winhex里面,按Ctrl+r,转换成二进制,然后保存位1.pyc进行反编译python文件
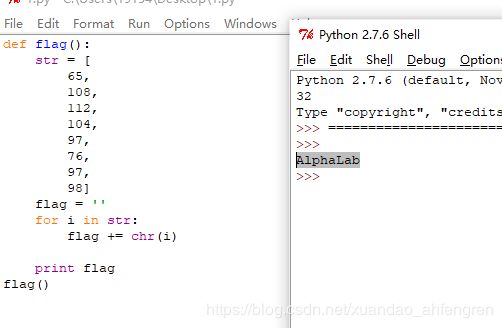
加多一个flag()即可运行得到flag
心仪的公司
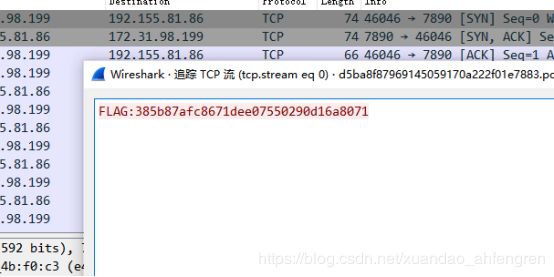
在tcp流中发现fl4g
stage1
放进Stegsolve里左右调整
保存再放在RQ分析二维码,然后放进winhex转换为二进制,保存为pyc进行反编译python文件后运行即可
Easycap
打开数据包,追踪tcp流即可
双色块
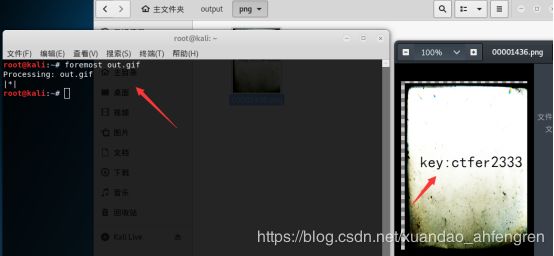
binwalk分析发现尾部有png,用foremost分离出来
拿出来是⼀个密码
gif轮播之后发现是⼀个2424的像素点,每个像素为1010,每个点颜⾊为00ff00或是ff00ff 先把gif分离成单帧
#! /usr/bin/env python2
# -*- coding: utf-8 -*-
import os
from PIL import Image
def main(gif_file):
png_dir = 'frame/'
img = Image.open(gif_file)
while True:
current = img.tell()
img.save(png_dir + str(current + 1) + '.png')
img.seek(current + 1)
if __name__ == '__main__':
gif_file = 'out.gif'
main(gif_file)会出先很多图片
然后读取每个png中的对应点的信息,并按照8bit转换为ascii
#! /usr/bin/env python2
# -*- coding: utf-8 -*-
import os
from PIL import Image
def main():
png_dir = 'frame/'
ret = ""
for i in range(0,24):
line = ""
for j in range(0,24):
file_name = "frame/" + str(i * 24 + j + 1) + ".png"
x = j * 10 + 5
y = i * 10 + 5
img = Image.open(file_name)
img = img.convert("RGB")
img_array = img.load()
r, g, b = p = img_array[x, y]
if g == 255:
line += "0"
if r == 255 and b == 255:
line += "1"
if len(line) == 8:
ret += chr(int(line, 2))
line = ""
print ret
if __name__ == '__main__':
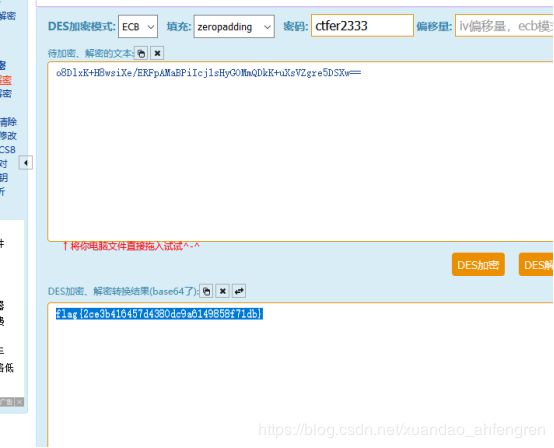
main()两个等会后面的hhh去除掉然后进⾏DES解密即可得到flag
很普通的数独
将有数字的格子写成0,没有的写成1
111111101010101000101000001111110000101111111
100000101100111101010011101100011001001000001
101110101110011111010011111101000101001011101
101110101101100010001010000011110001101011101
101110100011100100001111101111111011101011101
100000101100100000011000100001110100001000001
111111101010101010101010101010101011101111111
000000000011001101001000110100110011100000000
110011100100100001111111100100101000000101111
101001001011111111101110101011110101101001100
100000111100100100000110001101001101010001010
001100010011010001010011000100000010110010000
010110101010001111110100011101001110101101111
100011000100011100111011101101100101101110001
001100110100000000010010000111100101101011010
101000001011010111110011011111101001110100011
110111110111011001101100010100001110000100000
110101000010101000011101101101110101101001100
010011111110001011111010001000011011101101100
011001011001010101100011110101001100001010010
010111111111101011111111101101101111111111100
011110001100000100001000101000100100100011110
111110101110011100111010110100110100101010010
110010001011101011101000111100000011100010000
101011111011100111101111111100001010111110010
110100011000111000100111101101111101000100010
111101111110001001000011010110001111110111110
011001010101000110010100010001000101101010001
011101110101101101100100001101101000111101001
110110001001101100010101101111110100101100110
000011100111000000000100001010101111100010010
111010010011110011101110010100001011111010010
101001100010111111110100000100001010101010100
000010011001001101110101001111100101111101101
000010111101110001101011000001000101110100110
011110011010100010100000011011000001110010000
100110100100001101111111101100101110111110011
000000001111110101101000101011100100100011010
111111100011111011011010101101110011101011110
100000101110101101101000111110010001100010001
101110101011100001111111101101001000111111011
101110100110111101101000001001101100011101101
101110100000011101100001101010110010010010001
100000101011001011111011001011000011010110000
111111101010101001111011110101101110000101101然后使用python写个脚本来生成图片。
from PIL import Image
x = 45
y = 45
im = Image.new('RGB', (x, y))
white = (255, 255, 255)
black = (0, 0, 0)
with open('ss.txt') as f:
for i in range(x):
ff = f.readline()
for j in range(y):
if ff[j] == '1':
im.putpixel((i, j), black)
else:
im.putpixel((i, j), white)
im.show()扫出来是:Vm0xd1NtUXlWa1pPVldoVFlUSlNjRlJVVGtOamJGWnlWMjFHVlUxV1ZqTldNakZIWVcxS1IxTnNhRmhoTVZweVdWUkdXbVZHWkhOWGJGcHBWa1paZWxaclpEUmhNVXBYVW14V2FHVnFRVGs9
是多个base64加密的,解密出来是flag{y0ud1any1s1}
很普通的Disco
峰值高的点为1,峰值低的点为0。抠出来,是105个二进制数,每7个数为一组,刚好15组,也就是15个字母,最后用python跑出来即可
flag{W0W*funny}
就在其中
打开数据包发现,找到了key
还有一些文件,果断用foremost分离出来
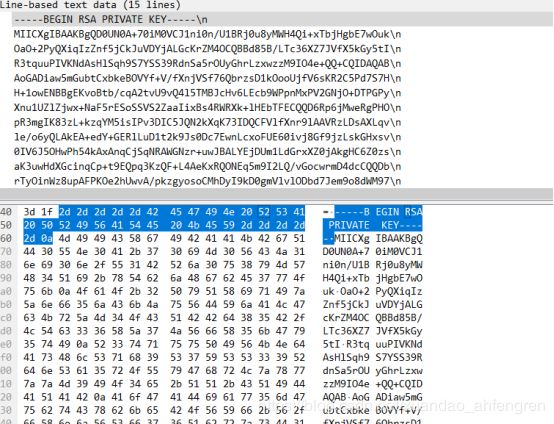
有个压缩包,里面的key.txt文件被加密过了,我们有密码就可以直接解密
openssl rsautl -decrypt -in key.txt -inkey 1.key -out flag.txt
in为要解密的加密文档-inkey为密钥-out为输出文档
再见李华
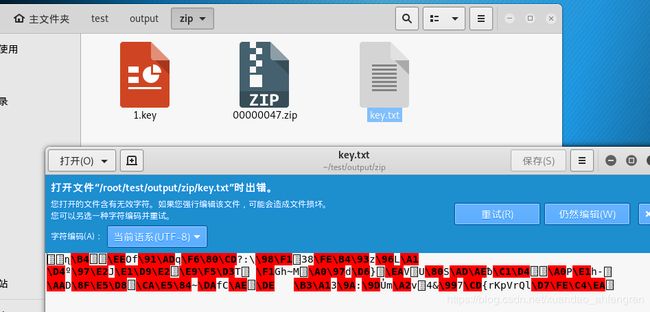
用winhex打开看到key.txt,把后缀改成zip
打开需要密码。
没有特殊字符,是指密码中没有特殊字符。而不少于1000个字,这个1000是8的二进制,所以密码是9位或9位以上,最后署名,意思是密码中后面5位数是Lihua,最后用Advanced ZIP Password Recovery_4.0进行破解。 最后密码为15CCLiHua
import string
from hashlib import md5
a = string.ascii_letters + string.digits
for a1 in a:
for a2 in a:
for a3 in a:
for a4 in a:
if '1a4fb3fb5ee' in md5(bytes(a1 + a2 + a3 + a4 + 'LiHua').encode('ascii')).hexdigest():
print a1+ a2 + a3 + a4 + 'LiHua'
break肥宅快乐题
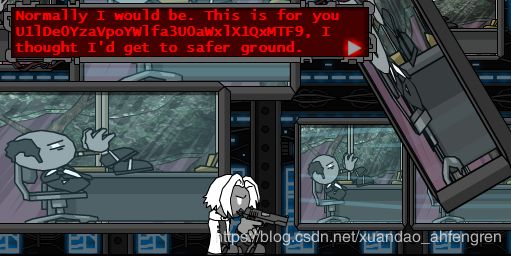
打通关后获取base64加密后的falg,解密即可
warmup
先将 open_forum.png 压缩为 open_forum.zip,然后明文破解
python bwm.py encode fuli.png fuli2.png res.png
flag{bWm_Are_W0nderfu1}